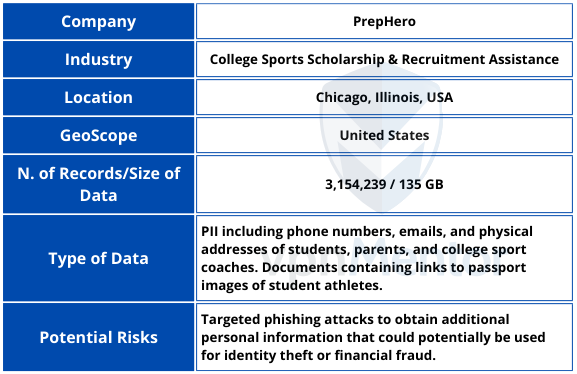
Over 3 Million Records, Including PII of Student-Athletes and College Coaches Exposed in a Data Breach

Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to vpnMentor about an unencrypted and non-password-protected database that contained 3,154,239 records presumably belonging to a platform designed to assist high school athletes in securing college sports scholarships.
The publicly exposed database was not password-protected or encrypted. It contained 3,154,239 records with a total size of 135 GB. In a limited sampling of the exposed documents, I saw names, phone numbers, emails, physical addresses, and passport data of students, as well as contacts of parents and college sport coaches. The database also contained unprotected.CSV documents with links to passport images of student athletes.
The internal files and database name indicated the records appeared to belong to a Chicago-based company called PrepHero, operated by EXACT Sports. PrepHero offers a platform designed to help high school athletes build recruiting résumés. It also allows for direct communication with coaches at some of the most prestigious and well-known colleges and universities with the goal of obtaining college sports scholarships.
I immediately sent a responsible disclosure notice to PrepHero, and the database was restricted from public access the same day and no longer accessible. Although the records appeared to belong to PrepHero, it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
According to their website, PrepHero provides recruiting assistance, mental training resources, and prospect evaluations to support student athletes' development and performance. PrepHero aims to streamline the recruiting process and increase athletes' visibility to improve their chances of being recruited by college sports programs.
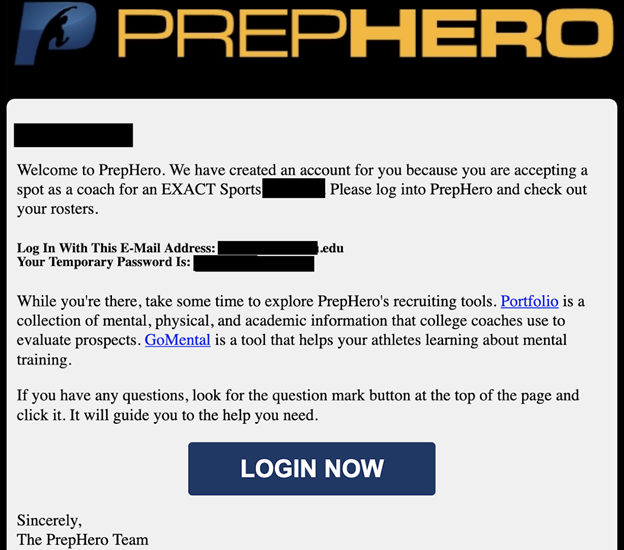
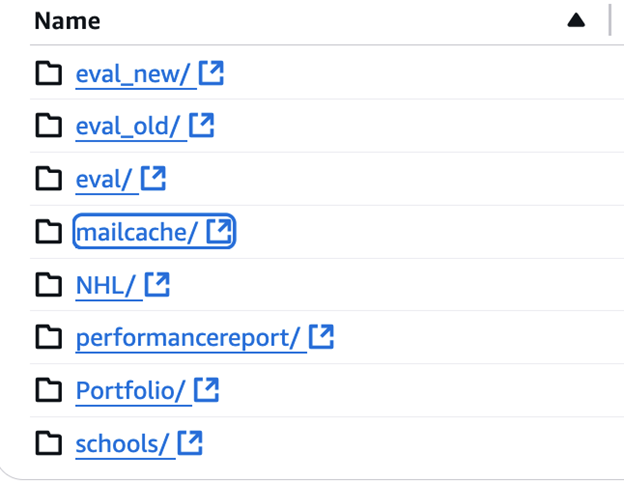
The database also contained a folder named “mail cache” that had 10 GB of email messages that range from 2017 to 2025. In a limited sample, I saw numerous messages to coaches with unique personalized links to publicly accessible pages that contain names, dates of birth, emails, physical addresses, and details about compensation or reimbursement. Some emails also contained welcome messages with account emails and login credentials marked as temporary passwords that could pose additional potential privacy risks. I also saw numerous audio files of coaches stating their names, the college they are affiliated with, and their individual summaries or evaluations of the student’s strengths and weaknesses.
Any data breach exposing potentially sensitive information of student-athletes could have serious privacy risks. The PII of students and young individuals are particularly vulnerable to identity theft because they often don’t have an established credit history or debt. Hypothetically, this could make it easier for criminals to open fraudulent accounts using their names, identities, and personal data without suspicion or immediate detection.
Most young people have never had a credit check, and they may not actively monitor their financial profiles, making it possible that identity theft attempts could go undetected for a very long time. The worst-case scenario would probably be discovering years later – when applying for credit cards or jobs – that criminals have used their personal information and damaged their credit without their knowledge. I am not saying any student athlete or individuals affiliated with PrepHero are at risk of identity theft or the misuse of their personal information. I am only highlighting a hypothetical real world risk scenario of how criminals could use this type of exposed data.
Additionally, the exposure of direct contact information of students, parents, and coaches could potentially be used for targeted phishing attacks, scams, and social engineering tactics designed to trick students or their families into sharing additional sensitive personal information or making additional financial payments under false pretenses.
Coaches could also potentially be targeted with spear-phishing attacks that impersonate trusted sports organizations, colleges, or even pretending to be affiliated with PrepHero or a similar organization. This could potentially compromise personal and professional relationships or recruiting activities or expose additional data. I am not saying any of PrepHero’s users are at risk of social engineering or phishing, I am only providing a risk scenario of a well known and common tactic used by criminals.
My advice to anyone who believes that their personal information was leaked in a data breach is to be vigilant and know the signs of a spear-phishing and social engineering attempt. Young people (or their parents) should obtain a credit report annually to make sure there are no unauthorized accounts in the child’s name. Always verify the identity of any unexpected requests for personal information, payments, or login credentials. Sometimes criminals can create messages that appear to come from a legitimate source. Always verify that any communications are only through an official channel — never provide additional personal or financial information if the request seems suspicious.
Organizations that collect and store potentially sensitive information should use a secure content management system as opposed to keeping all business files in a single cloud storage repository. Using individual spreadsheet documents may be convenient but could pose a potential security threat. A password-protected CRM or CMS offers structured access control, encryption, and audit logs, making it much harder for unauthorized users to access or manipulate sensitive data compared to spreadsheet files or similar documents that are stored in a cloud database. Spreadsheet files lack built-in security features like role-based permissions and are more prone to accidental sharing or exposure if a data breach occurs.
Additionally, sending emails with unique web links to surveys or open webpages that contain PII should be restricted and only accessible with login credentials to prevent unauthorized or accidental access. I would recommend that companies require multi-factor authentication (MFA) on all accounts — internally, for employees or coaches, and externally for users, student athletes, and parents. Using MFA combined with a strong password is a bare-minimum step that can make it harder for cybercriminals or unauthorized individuals to gain access. Encrypting all documents and removing or deleting old records that are no longer in use is also a good idea that can minimize the impact of a data exposure.
I imply no wrongdoing by PrepHero, EXACT Sports, or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download the data I discover. I only take a limited number of screenshots as necessary and solely for verification and documentation purposes. I do not conduct any activities beyond identifying the security vulnerability and notifying the relevant parties. I disclaim any and all liability for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.





Please, comment on how to improve this article. Your feedback matters!