Auto Insurance Customers' Personal Data and Documents Exposed Online

Cybersecurity researcher, Jeremiah Fowler, discovered and reported to vpnMentor a non-password protected database containing over 250k documents related to auto insurance policies. The publicly exposed documents contained highly sensitive personal identifiable information (PII).
The unsecure database contained scans and images of vehicle registrations, division of motor vehicle registration applications, certificate of insurance cards, vehicle titles, driver’s licenses, state medicaid health coverage cards, and more. Upon further research all of the policies I saw listed USA Underwriters as the primary insurer. I immediately sent a responsible disclosure notice by email to USA Underwriters regarding my findings. After multiple email notices went unanswered, I was able to reach someone at USA Underwriters by phone and express the severity of the data exposure. The database was secured and restricted from public access in less than 2 hours after my call; however, it was exposed for at least 2 weeks from the time I discovered it until it was finally closed.
The story took a strange turn when I woke up the next morning with a voicemail from someone claiming to be a detective with the Detroit Police wanting to ask me a few questions. As an ethical security researcher, I have provided information on my findings to government agencies and law enforcement agencies many times in the past. I searched the name and phone number of the alleged detective and a LinkedIn account matched the same unique and uncommon name of a USA Underwriters employee. I returned the call and asked if the individual was an employee or affiliated with USA Underwriters and each time the answer was, “No”.
During the call, this person mentioned a third-party vendor named RateForce as the owner of the database. This also matched the name of the database which was listed as “RF******Prod”(redacted for security reasons). RateForce provides a platform to compare car insurance quotes online and, according to their website, they have provided nearly 11 million quotes since 2014. In 2021, RateForce, LLC ranked #2 on the Inc. 5000 list of fastest-growing private companies in the insurance industry.
The records also indicated what appeared to be a large number of independent insurance agents who sold the policies. The majority of the documents appeared to come from agencies and car dealerships obtaining insurance for their customers. In a limited sampling of records, I saw identification documents belonging to thousands of individuals. Although a majority of the identification documents were from Michigan, I also saw licenses from Georgia, Arizona, and Virginia. It is unclear if residents from other states were also affected by the exposure as I did not analyze the over 255k documents.
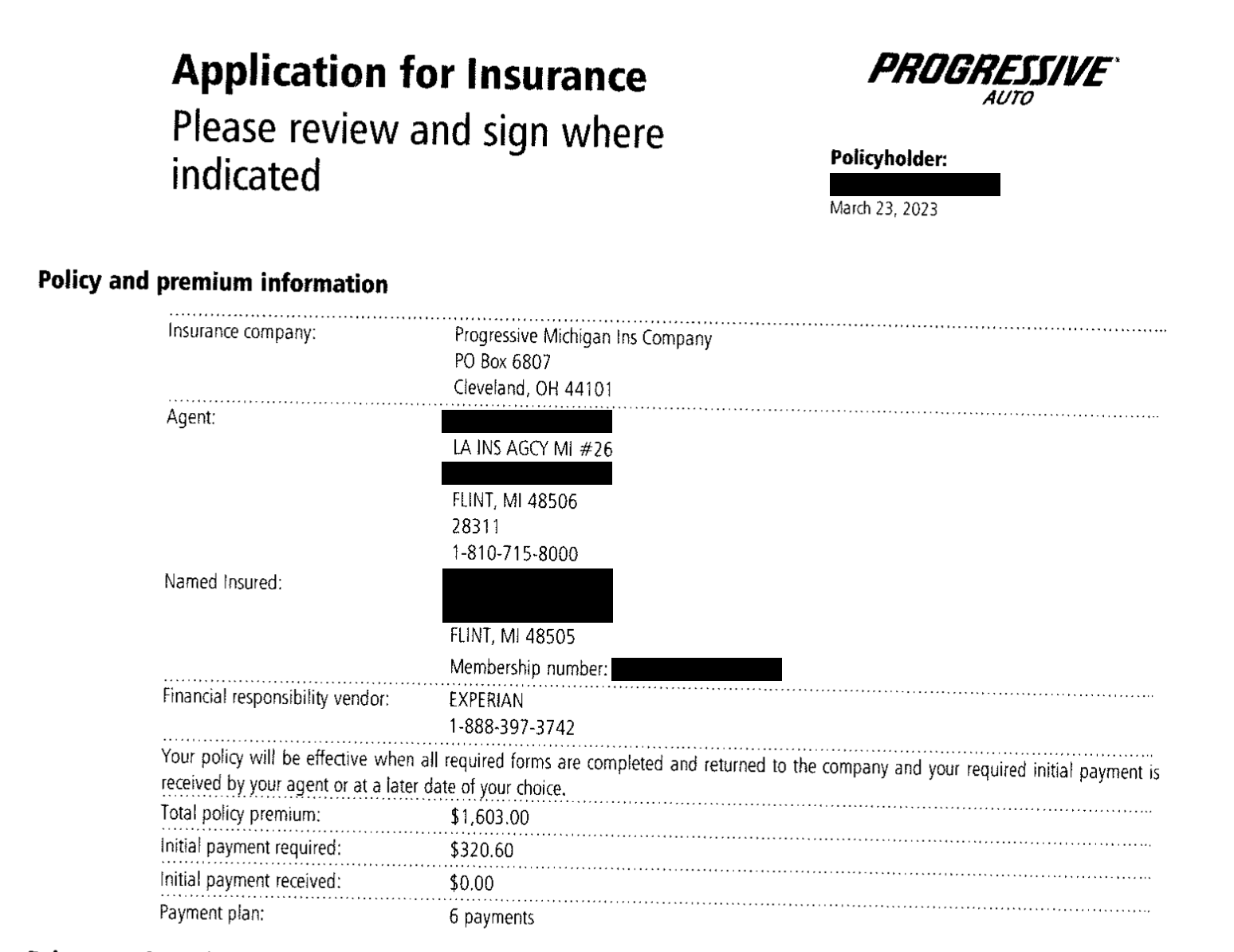
There were a large number of insurance companies listed in the documents, including Gainsco Insurance (owned by State Farm), Progressive, Excepsure, Cimarron, L.A. Insurance, and others. The one common factor is that all of the policies were underwritten by USA Underwriters and this is why I initially believed they owned the exposed database. However, it was later confirmed that the database was owned by RateForce. I am not implying that any of these companies are responsible for the data exposure and only identify that I saw references to them in the documents. In the insurance industry, it is common for independent agents to sell insurance products from many insurance companies, whereas captive agents only sell insurance for one company.
Details of what the database contained
- 96,175 folders that contained a total of 255,756 records with a size of 93.93 GB.
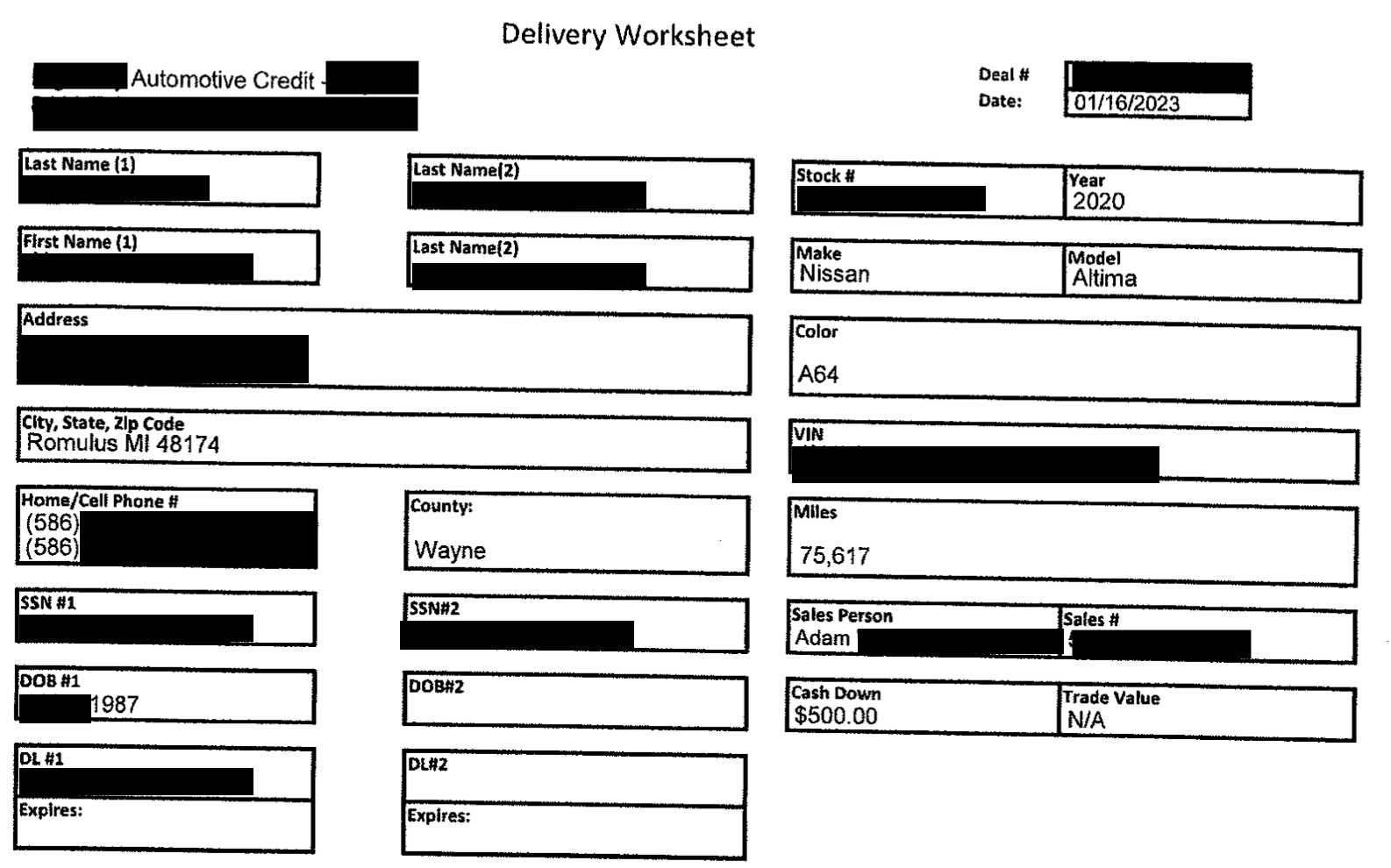
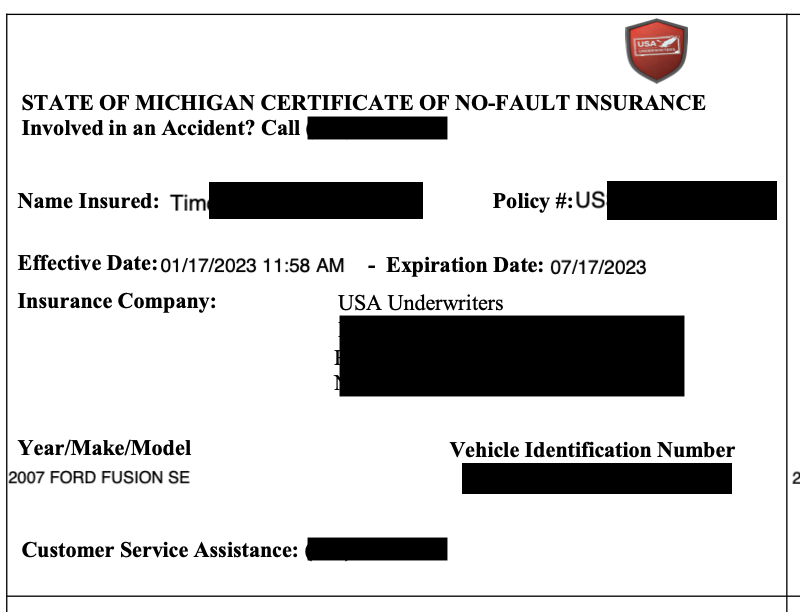
- Folders contained insurance policy cards and driver’s licenses (front and back sides).
- Some folders also included additional documents such as auto loan information that contained PII and social security numbers, vehicle titles, applications for titles, state registrations, Medicaid or health insurance cards, utility bills showing proof of residence, letters from banks showing active accounts, and partial account numbers.
- The breach included customer and applicant names, home addresses, phone numbers, driver's license numbers, vehicle identification numbers (VINs), and insurance policy details.
- Sales records with auto dealer information that included EIN tax identification numbers and other sales or vehicle data. Some included the buyer’s social security number (SSN) in plain text.
Third-Party Vendor Risks
USA Underwriters is a company that provides insurance to high-risk drivers. Although each policy I saw lists them as the insurer, the database was not under their management and did not belong to them. Often vendors and third-party partners who serve as brokers will collect and store the necessary documents to secure an insurance policy. USA Underwriters employs a separate IT company to manage their infrastructure and a representative of this company confirmed this database did not belong to USA Underwriters and although these were USA Underwriters policies the database was not under their management.
I then called RateForce and spoke with their leadership as well as with the head of Samarpan Infotech, the company who manages RateForce’s network and infrastructure. During the call, RateForce did not admit or deny that they were responsible for the exposed records despite the name of the dataset and the call with the individual claiming to be a Detroit Police detective who indicated the database belonged to RateForce and later another USA Underwriters employee confirmed this. I am not implying any wrongdoing by USA Underwriters, RateForce, or Samarpan Infotech, nor am I implying that the individuals whose data was exposed were ever at risk. However, I do want to raise awareness of my discovery and how this information could be hypothetically used by criminals or scammers. It is important to notify the insurance customers who had their PII exposed online. I am only stating the facts of my discovery in an attempt to ensure individuals who may have been affected by the data leak are aware of the exposure and be on the lookout for any suspicious activity or unauthorized attempts to use their identity.
The most important part of this discovery is identifying the real world risks associated with the data leak of highly sensitive PII. Data breaches involving customer auto insurance information can potentially put the affected individuals at risk of identity theft and fraud. The type of information that is required for an auto insurance policy would provide criminals with all of the personal information they would need to commit a range of nefarious activities. An auto insurance policy contains information about the individual's vehicle, including the make and model, year, and VIN. This information can be used by fraudsters to commit auto insurance fraud or other types of criminal activities.
Another potential risk would be selling the information on the dark web, where it could be exploited by criminals from around the world. Exposed auto insurance policy information also raises the risk of fraudulent claims and can cause the victim’s car insurance rates to increase. It is estimated that insurance scams cause $29 billion of damage to auto insurers every year. This type of fraud can cause significant harm to both insurers and the insured.
Exposed images of driver's licenses could cause a variety of issues for the affected individuals. This document contains sensitive personal information such as the individual's full name, date of birth, address, and state issued license number. This information can be used by identity thieves to steal the individual's identity, open fraudulent accounts, and conduct other types of illegal activities.
Images of Medicaid and health insurance cards can also pose a risk of misuse. Criminals could potentially receive benefits through the exposed number or receive medical care, prescriptions, and other services that the victim did not not authorize. This can lead to fraudulent medical charges or debt-collection disputes that could negatively impact the victim’s credit scores.
Auto insurance companies have a responsibility to safeguard their customers' personal information and to notify them in the event of a data breach. For individuals who have had their personal information exposed in an auto insurance data breach, I highly recommend that they monitor their credit reports regularly for any suspicious activity and consider placing a fraud alert with one of the credit reporting agencies. Another option is using an identity theft protection service to monitor personal information.
It is unclear how long the database was publicly exposed before I discovered and reported my findings. It is also unclear if anyone else had gained access to these records. As a security researcher, my primary goal is data protection no matter who is affected or who the database ultimately belonged to. I highly recommend that any organization that collects and stores sensitive customer data take steps to ensure that data is not publicly accessible and use encryption whenever possible. It is also important that companies have an internal communication channel for data incidents to ensure that outside responsible disclosure notices get the proper attention they deserve without being ignored by customer support agents. This can drastically reduce the exposure time and help secure sensitive information fast when it is relayed to the correct person or team within an organization.






Please, comment on how to improve this article. Your feedback matters!