PII, ID Numbers, & SSNs Exposed in Tax Credit Consultancy Data Breach

Cybersecurity researcher Jeremiah Fowler discovered and reported to vpnMentor an unencrypted and non-password-protected database that contained 245,949 records. The database, which presumably belonged to a tax credit consulting agency, held PII, driver’s licenses, military discharge forms, documents containing Social Security numbers (SSNs), and other internal, potentially sensitive information.
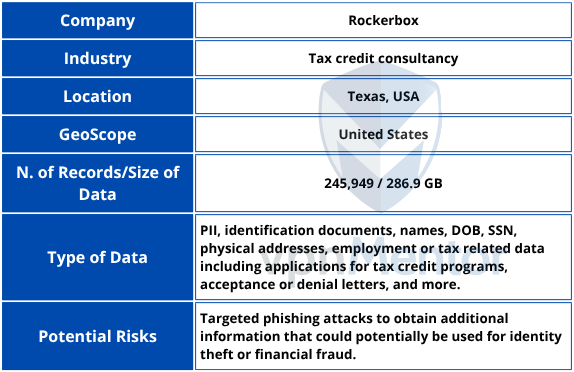
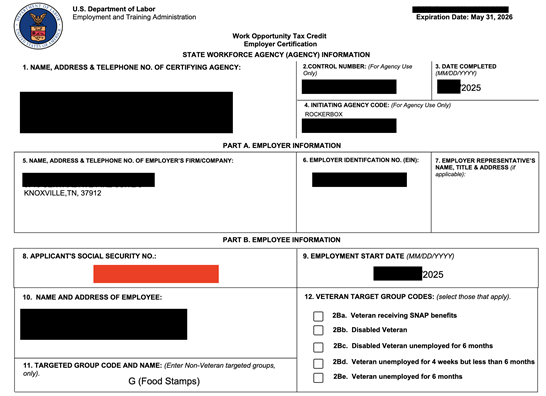
The publicly exposed database was not password-protected or encrypted. It contained 245,949 records with a total size of 286.9 GB. In a limited sampling of the exposed documents, I saw files that detailed PII such as names, physical addresses, email addresses, DOB, and SSN in plain text. There were also driver’s licenses, identification cards, SSN cards, work opportunity tax credit documents that included employment and salary information, and determination letters with acceptance or denials of eligibility.
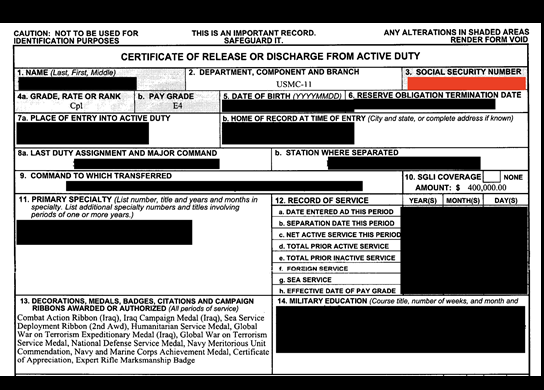
The database also contained DD214 forms, which are Certificates of Release or Discharge from Active Duty issued by the U.S. Department of Defense. These records serve as an official documentation of a veteran's military service. In addition to these publicly accessible documents, the database contained a large number of password-protected.PDF files marked as “forms”. The file names of these documents contained PII such as the employer’s name, applicant’s first and last name, a numeric code, and document number.
Information contained in the internal files indicated the records appeared to belong to a Texas-based company called Rockerbox. This is a tax credit consulting company that helps businesses to increase their cash flow by identifying and managing employer-focused tax incentives through programs like the Work Opportunity Tax Credit (WOTC), Employee Retention Tax Credit (ERTC), R&D credits, and Empowerment Zone credits. Based in Dallas, with clients from all over the United States.
I immediately sent a responsible disclosure notice to Rockerbox, and the database was restricted from public access several days later and no longer accessible. I did not receive any reply to my responsible disclosure notice. Although the records appeared to belong to Rockerbox, it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
According to their website, Rockerbox provides services to a range of industries including restaurant and hospitality, healthcare, healthcare staffing, temporary staffing, trucking, manufacturing, warehouse, food processing, skilled trades, and golf courses.
While some files in the database were not publicly accessible or returned an “access denied” error, many other documents were available to anyone with an internet connection and a web browser. Inconsistent security measures are a potentially serious risk to any organization that uses cloud storage for sensitive data. When access controls are not properly configured, these inconsistencies can make it difficult to audit or enforce compliance measures. Moreover, since the storage location and file path are known, they could lead to a data breach or other forms of unauthorized access.
In this exposure, the document name and URL (or file path) of the password protected.PDF files included several identifiers such as the name of the business, first and last names of individuals, numeric characters, and the document form number. It is theoretically possible that the numeric part of the file name could have contained the password to unlock the individual file.
As an ethical security researcher, I never bypass authentication credentials or test assumed passwords under any circumstances and only view publicly accessible data or files. I recommend that developers avoid embedding things like names or passwords in the file name or as a file identifier. Never rely on security through obscurity. Web-accessible files that contain identifiable information in the file path or name could potentially expose sensitive data through browser histories, logs, analytics tools, or even copy-pasted links. I am not asserting that these password-protected PDFs were at risk of being unlocked or accessed by unauthorized individuals, I am only highlighting a hypothetical risk scenario and recommending best practices for general file name and file path security.
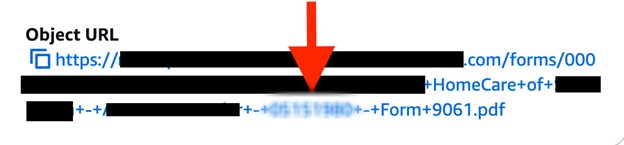 This image shows the web url that includes the name of the individual and a suspected password to the protected PDF file.
This image shows the web url that includes the name of the individual and a suspected password to the protected PDF file.
Exposed PII like SSNs, dates of birth, full names, and driver’s license numbers (when combined with employment information) may be targeted by criminals seeking to use this information for financial crimes or identity theft. In such scenarios, criminals could theoretically obtain sufficient personal information to impersonate individuals and attempt to obtain fraudulent credit accounts, apply for loans, or even file false tax returns.
According to a report by the credit rating agency Experian, in 2024, the FTC recorded over 1.1 million claims of identity theft. Additionally, the agency handled approximately 2.6 million fraud cases tied to these incidents, with reported losses exceeding $12.7 billion. For clarity, I am not stating nor implying that Rockerbox’s clients or their employees are at risk of any type of fraudulent activities or that their personal data was ever at risk. I am only providing general, hypothetical risk scenarios of how exposed personal data could potentially be used.
Individuals who believe their personal information has been exposed in a data breach should take proactive steps to minimize the potential risks associated with identity-related crimes. For instance, it is always a good idea to monitor your bank and credit accounts’ activity. If attempts have been made to open new accounts in your name or suspicious charges appear, we recommend you place a fraud alert or credit freeze with the three major credit bureaus (Experian, Equifax, and TransUnion).
There are many companies that offer identity theft protection services that can help identify new accounts as they appear. The Federal Trade Commission (FTC) offers a valuable resource for reporting and recovery by visiting IdentityTheft.gov. Again, I am not asserting nor implying that Rockerbox’s customers, users, or clients are at risk of any misuse of their identity or financial information. I only offer this content for general advice and for educational purposes.
For companies and organizations that collect and store potentially sensitive personal data in cloud storage repositories, it is important to implement the proper security measures to protect that information. This starts with access controls and limiting who (from both inside and outside of the organization) can see and manipulate which pieces of information. It is always a good idea to use encryption for files that contain PII or valuable internal data. This way, if they are ever exposed, the data is not accessible.
In addition, I recommend regular audits of the organization’s overall security practices. Monitoring access logs to detect unauthorized or suspicious activity can also identify potential security vulnerabilities. Ensure that cloud storage configurations and firewall settings are accurate and up to date. Finally, when it comes to internal storage systems, implement a zero-trust policy. This means configuring the system so it never allows access to any internal systems or data without verifying it is an authorized user.
It should be noted that Screen Technologies LLC, DBA Rockerbox.tech is a tax credit consulting firm not affiliated in any way with Rockerbox.com, a marketing analytics platform (which, based on publicly available information, was acquired by DoubleVerify in 2025). Despite sharing the same name, there seems to be no apparent connection, and they operate in different industries.
I imply no wrongdoing by Rockerbox, or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively intended for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a definitive assessment of any organization’s specific practices, systems, or security measures, and I expressly disclaim liability for how this information is used or understood by a reader.
As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I disclaim any and all liability for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.
vpnMentor Recent Publications
Cybersecurity Expert Jeremiah Fowler has discovered and disclosed some of the most impactful data breaches in recent years.
This includes a data breach exposing over 3 million records, presumably belonging to PrepHero, a platform designed to assist high school athletes in securing college sports scholarships and a most recent report, which exposed over 3.6 million records presumably belonging to Passion.io, including users PII and other sensitive data.




Please, comment on how to improve this article. Your feedback matters!