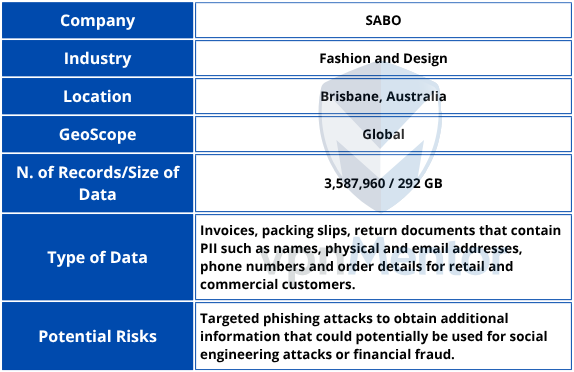
3.5 Million Records Exposed in Australian Global Fashion Brand Data Breach

Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to vpnMentor about an unencrypted and non-password-protected database that contained 3,587,960 records. The database, which presumably belongs to an Australian fashion brand, held invoices, shipping information, and return details. The documents contained names, physical and email addresses, phone numbers, and other potentially sensitive information.
The publicly exposed database was not password-protected or encrypted. It contained 3,587,960.pdf documents with a total size of 292 GB. In a limited sampling of the exposed documents, I saw personally identifiable information (PII) (including names, physical addresses, email addresses, phone numbers, and more) corresponding to what appeared to be retail and corporate customers. In one single PDF file, there were 50 separate order pages, indicating that the total number of potential customers is higher than the total number of PDF files in the database. The records appeared to belong to an internal document management storage system that is used to track sales and returns, as well as the corresponding domestic and international shipping documents. The file dates ranged from 2015 to 2025.
Given the information in the internal files, the records appeared to belong to a Brisbane, Australia-based fashion company called SABO. It designs and sells an exclusive collection of clothing, shoes, swimwear, sleepwear and formal wear. SABO sells their products at physical locations across Australia, but it also does online sales with worldwide shipments.
I immediately sent a responsible disclosure notice to SABO, and the database was restricted from public access within hours and no longer accessible. I did not receive any reply to my responsible disclosure notice. Although the records appeared to belong to SABO, it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
Any data breach that exposes customer invoices (which contain names, delivery addresses, and email addresses) poses potential privacy and security risks. When years of transaction history are compromised, criminals could potentially have access to a large amount of PII that could be exploited for a range of malicious purposes.
Knowing purchase details and the companies that customers have had a business relationship with could provide quality data for targeted phishing campaigns or social engineering attempts. Criminals could create convincing emails that appear to come from the company, quoting real order numbers, items ordered, dates, purchase totals, and more. Being familiarized with internal information that, theoretically, only the customer and the company could know could potentially increase the chances of a successful phishing or social engineering attack.
While a majority of cyber-crime is conducted for financial gain, there are also other potential risks of exposed contact details. As of 2025, it is estimated that email accounts for up to 91% of cyberattacks, and that nearly 92% of all malware is distributed via emails. The same report also indicates that approximately 30% of phishing emails are opened by the recipients.
Just a few years ago, it was fairly easy to spot poorly written emails that were clearly a scam, but now, with the global access to AI writing tools, it has become much more difficult to rely on grammar-based detection. My advice to anyone who believes their email or other contact information may have been potentially exposed would be to take steps to avoid falling victim to phishing attempts.
Always verify the sender’s email address and make sure it matches the company or organization. Make sure you only use official communication channels. Never click on suspicious links and beware of those that could be cloaked using a link shortener. Never download attachments from non-trusted or unverified senders. Remember: Criminals know that having insider information increases their chance of success, so being suspicious or cautious is warranted. Always validate that the person contacting you or requesting additional information is who they say they are.
Another potential new risk is called a brushing scam, which is when criminals use personal information (like names and addresses) that is often obtained from leaked data and used without their knowledge. Sellers send unsolicited packages to seemingly random people and then use their names and identities to post fake positive reviews in an attempt to boost product ratings. The U.S. Postal Service issued a warning about this growing scam stating “It may look like a harmless delivery, like a keychain, some socks, a random kitchen gadget, but it’s often a red flag that cybercriminals have gotten hold of your name and address”. I am not claiming that SABO’s clients are at risk of these types of threats. I am only identifying hypothetical real-world scenarios of how this information could be potentially used by criminals.
Companies that collect and store customer and internal data should ensure that the cloud storage services they use are properly configured to prevent public access. Implementing access controls and authentication measures is a good first step to protect data, but there’s more that you can do. For instance:
- When possible, use multi-factor authentication (MFA) to access potentially sensitive information or documents.
- Encrypt your documents. PDF files can be password-protected individually, which can create an additional layer of protection. Many cloud storage providers offer built-in encryption tools that can be configured to the organization's specific needs.
- Applying security configurations such as firewall rules and network segmentation can also help to reduce potential vulnerabilities.
- Do not store years’ worth of data all in one place — keep your backups and store some of that data in a different location.
- Monitoring and auditing can help detect unusual or unauthorized activity and close access if anything suspicious is identified.
- Just like customers it is important to train employees to recognize phishing attempts, how to secure their credentials, and proper data handling practices.
I imply no wrongdoing by SABO or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I disclaim any and all liability from the use, interpretation or reliance on this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.
vpnMentor Recent Publications
Cybersecurity Expert Jeremiah Fowler has discovered and disclosed some of the most impactful data breaches in recent years. This includes, for instance, a data breach exposing over 3.6 million records, which included PII and other sensitive data apparently linked to Passion.io users — a no-coding app-building platform—. Another report covered the exposure of over 3 million records presumably belonging to RockerBox a tax credit consulting agency.






Please, comment on how to improve this article. Your feedback matters!