Are Blockchain and Bitcoin Really Immutable?
We take a deep look at the concept of blockchain, how it applies to Bitcoin, and if they are immutable or not. Share
Whenever we talk about blockchain, immutability is the next thing that comes up. There are different views on the topic, but when it comes down to it, everyone is looking for an answer to a single question – are blockchain and Bitcoin immutable? The short answer is – Yes, blockchains and Bitcoins cannot be changed. The long answer is that you still need to know the reasons behind that answer in order to understand the implications.
Before diving into the topic, it is important to understand the basics of blockchain. However, we will not get into core technical details, since it is a topic in itself. So, what is blockchain? Many people interchangeably use the term blockchain and Bitcoin, but they are not the same. Blockchain is a concept, an idea. Bitcoin is the first and major implementation of that idea. There can be other different implementations on top of blockchain which are nowhere related to Bitcoin. In fact, there has been decent progress in other areas such as smart contracts, inter-bank settlements, etc. which are more interesting than Bitcoin.
In its essence, blockchain is just a distributed ledger. As opposed to common paradigms where there is a central trusted authority to control things, blockchain provides a network where there is no single point of power. There is no need to “trust” anyone because the system itself makes it almost impossible for anyone to take control. This decentralization is what makes it so powerful and appealing to the common people.
Bitcoin is a crypto-currency based on blockchain that is not regulated by anyone. The transactions are instantaneous and there is a minor fee associated with a transaction, which makes it very popular for worldwide payments. However, there is no intrinsic value of the currency, since it is not backed by anything. Its value is dependent purely on how much people are willing to pay (check Bitcoin Price using this tool) and directly correlates with the trust people have in the system. That’s why you see the price of Bitcoin go down whenever a negative news associated with the blockchain comes out. (You can read more about Bitcoin here.)
Now, what is immutability and why should you care? In general terms, immutability refers to something that cannot be altered after creation. Those who are from the software programming world know the importance of immutable objects. In the context of blockchain, immutability has a similar meaning but a far greater importance. To explain why it is so important, let’s talk in concrete terms taking the example of Bitcoin.
Bitcoin transactions, occurring globally, are stored in a decentralized manner across the network, ensuring multiple copies of the data are dispersed. Essentially, this forms a connected chain of blocks. However, if these blocks were susceptible to modifications, it would present an opportunity for malicious individuals to manipulate the transaction history, enabling them to amass significant wealth by altering the records. Consequently, the immutability of the blocks holds paramount significance. Now, let us delve into the specifics:
To start a new transaction, you broadcast a message with the transaction details, like “pay Bob 9 BTC.” But how does the world know that it is you and not someone else who is the originator of the transaction? For that, the Bitcoin software/wallet you use creates a digital signature from your private key, which is only known to you (your system) and is unique per transaction. Others will use a corresponding public key to decrypt the message. The below diagram explains the flow at a high level:

However since the transaction goes via networks and computers, which cannot be trusted, how do you ensure that the message is immutable and someone doesn’t change the details? The way a digital signature works is if the message is altered, it invalidates the whole signature and hence everybody knows that it was tampered with. Next, your transaction goes to a pool of unconfirmed transactions. People who are participating in the Bitcoin network pick some of these transactions and try to add them in the existing block. However, in order to add the transaction, a mathematical puzzle has to be solved (SHA256 Hash, to be precise). Finding the solution to this puzzle takes time, which marks a very important feature in the Bitcoin infrastructure as we will see later. Now, multiple people will try to solve that puzzle. Whoever is able to solve it first gets to add the transaction to the existing block, and they receive a small percentage of Bitcoin as the reward. Below is the diagram to explain it. Note that the last transaction has a pointer to the older transaction forming a block.
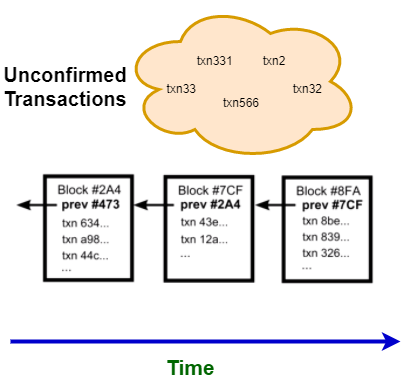
Due to the nature of Bitcoin infrastructure, there can be multiple branches of the blockchain containing conflicting information. How do you know which one to trust? The rule is that the longer branch is the one that should be trusted and the shorter branch goes back to the pool of unconfirmed transactions. That is why there is a cooling period after you do a transaction, and for the initial period, it is generally risky and unconfirmed. Some wallets mark the transaction in red to denote the same.
Now, our question comes again. Is the block really immutable? Is it possible for a malicious attacker to change the block in his/her favor? The answer is that it is not 100% immutable, but the mathematical puzzle approach we discussed earlier makes it nearly impossible to do so. For an attacker to succeed, he needs to create a chain of blocks which is longer than the existing ones. The distribution and time-consuming nature of the process make it practically impossible for someone to do that.
But what about the already accepted block? Is it prone to modifications? Yes, but again, since the nodes are distributed, it would require an attacker to take control of a large number of computers in the network. Percentage wise, it would require the attacker to takes control of 51% of the computers and hence the name “51% attack”. But then, a logical argument would be that if someone has control of so many computers, it would be more beneficial to earn Bitcoin by mining and play a fair game rather than cheating the system.
So, in all, it would be wise to say that blockchain is nearly immutable, as long as there are a huge number of participants. But it is also important to understand the reason because some people are paranoid about it and may be correctly so.




Please, comment on how to improve this article. Your feedback matters!