Report: Over 300k Residents in the Philippines Exposed in Covid-19 Relief Portal Leak
Led by Noam Rotem, vpnMentor's research team discovered a data breach related to a website from the government of Makati Philippines called Proud Makatizen.
Proud Makatizen is an official website from the city of Makati, Philippines. It began as an online portal for providing Covid-19 relief services, such as signing up for vaccinations, financial support, and more.
Proud Makatizen had misconfigured an Amazon Web Services S3 bucket, exposing just over 620,000 files stored within. The files included photos of ID cards, as well as private medical and financial information.
The Proud Makatizen data breach totaled 39.7GB and exposed around 300,000 Makati residents to potentially devastating online attacks, like identity theft and privacy violations.
Data Breach Summary
| Company/Org. | Makati city’s government, specifically the website ProudMakatizen.com |
|---|---|
| Headquarters | Makati, Philippines |
| Industry | Public Sector |
| Size of data in gigabytes | 39.7 GB |
| Suspected no. of files | Over 620,000 |
| No. of people exposed | Around 300,000 |
| Date range/timeline | May 2020 - April, 2022 |
| Geographical scope | Residents of Makati, Philippines |
| Types of data exposed | ID cards; personal medical and financial information |
| Potential impact | Phishing, privacy violation, and identity theft |
| Data storage format | AWS S3 bucket |
What is Proud Makatizen?
The Proud Makatizen website and service began in April of 2020 while the Covid-19 pandemic was still in its early stages.
When the site first started, it was primarily used to provide information on how to receive Covid-19 financial relief, according to news articles and the site’s FAQ section. More recently, the site also started providing information about, and forms to sign up for vaccinations.
Makatizen eWallet and GCash were two terms we saw come up often in files from the data breach. Neither of these programs were responsible for the breach, but they were payment methods regularly used for services on the Proud Makatizen website.
Makatizen eWallet is a digital wallet system which Makati city encourages residents to use. GCash is the service often used to make payments to and from this Makatizen eWallet.
Timeline of Discovery and Owner Reaction
- Date discovered: March 30, 2022
- Date Philippines CERT contacted: March 31, 2022
- Date of CERT response: March 31, 2022
- Date CERT report sent to City of Makati: April 4, 2022
- Date bucket was found secured: April 7, 2022
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue is quickly resolved. But rare are these times. We often need days of investigation before we understand what’s at stake or who’s exposing the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, Proud Makatizen was using an Amazon Web Services (AWS) S3 bucket to store data collected from the public through its various activities. S3 buckets are a popular enterprise cloud storage solution. However, it is up to the users to properly define the security settings to protect any data stored therein.
Proud Makatizen failed to implement appropriate security measures on its S3 bucket, leaving the contents totally exposed and easily accessible to anyone with a web browser and technical skills.
We quickly identified Proud Makatizen as the owner of the data largely because the names of folders in the bucket matched the names of services offered on the Proud Makatizen website.
Once we confirmed that Proud Makatizen was responsible for the data breach, we contacted Philippines CERT (Computer Emergancy Response Team) to notify them and offer our assistance. They replied quickly and asked us to provide more information. We disclosed the URL leading to the unsecured server and provided further detail about what it contained.
We received regular communication with Philippines CERT until they were able to complete their report and send it to the City of Makati. The AWS S3 bucket was secured shortly after.
Examples of Entries in the S3 Bucket
In order to confirm registration for vaccinations and Covid-19 relief funds, the Proud Makatizen website required residents to upload identity documents as well as medical and financial information depending on the service they were trying to use.
However, the Makati government did not properly configure the AWS S3 bucket in order to secure this personal information.
Identity Documents
In order for residents to confirm their identity for vaccination and relief fund registration, residents uploaded ID documents such as passport pages, driver’s licenses, senior citizen cards, health licenses, and so on.
The data bucket contained approximately 300,000 unique identity document files exposing details such as:
- Full name
- Photo
- Place of residence
- Nationality
In addition, it revealed information such as ID numbers and expiration dates. This could expose users to identity theft and fraud.
 Leaked image of a US citizen’s passport, a resident of The Philippines
Leaked image of a US citizen’s passport, a resident of The Philippines
 Leaked image of a resident’s passport page.
Leaked image of a resident’s passport page.
Medical Documents
For some services, Proud Makatizen asks residents to upload medical information to prove preexisting conditions.
The documents seen in the breach included prescriptions and physician’s letters explaining the details of the user’s medical condition. The bucket contained roughly 200,000 of these files.
 Leaked image of personal medical information.
Leaked image of personal medical information.
Financial Documents from Companies
The bucket contained several files showing financial documents from companies in Makati. These were probably uploaded to the website in order to take part in the Makati Assistance and Support to Businesses (MASB) program.
The documents showed some of the impact which the pandemic has had on the companies. They also showed information such as transaction dates, account numbers, and names of accounts.
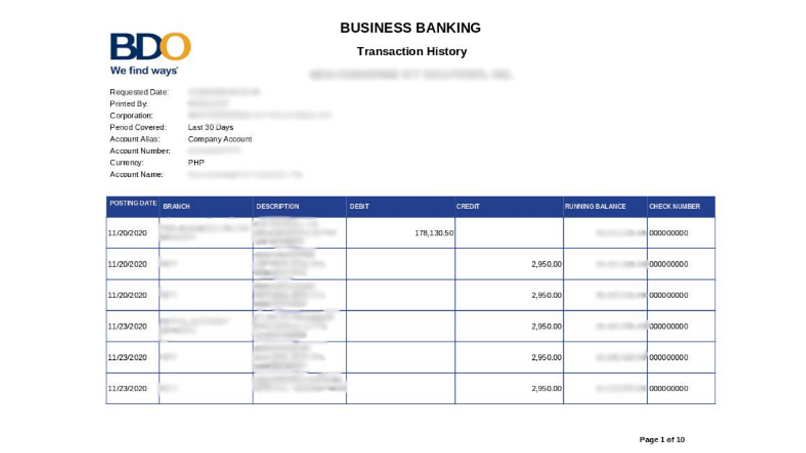 Leaked billing document from a Makati business.
Leaked billing document from a Makati business.
Financial Documents from Residents
The bucket contained about 12,000 files showing financial information from residents of Makati. Most of these were screenshots of GCash payment confirmation messages which citizens uploaded to Proud Makatizen’s website as proof of payment for their vaccination registration.
Information from these files included:
- Payment amount
- Transaction date
- Account balance
- Transaction reference number
- Transaction tracing number
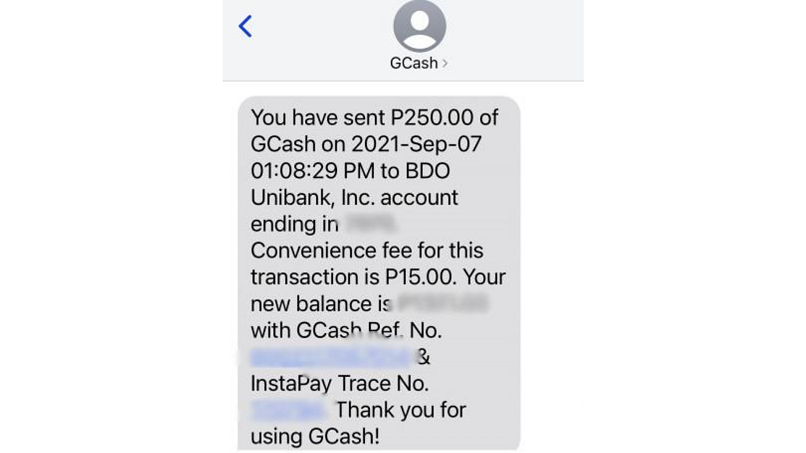 Leaked pay confirmation text message with confidential information.
Leaked pay confirmation text message with confidential information.
Data Breach Impact
When data from a breach like this gets out, there is a chance that it can damage the individuals or the government agencies who that data came from. Below, we’ll explain some of the most likely and impactful types of damage that we have seen occur from data breaches like this.
Impact for Users of Proud Makatizen
Based on the data we saw in this particular data breach, the potential risks to Proud Makatizen users include:
- Identity theft
- Tax fraud
- Insurance fraud
- Mail fraud
- And many more...
In addition, the exposed data leaves Proud Makatizen users vulnerable to phishing attacks.
In a phishing campaign, criminals send victims fake emails and text messages imitating real businesses and organizations. By building the victim’s trust, they hope to trick them into any of the following actions:
- Providing additional Personally Identifiable Information (PII) data (i.e., social security numbers) or private information (i.e., bank account details) that can be used in the fraudulent activities listed above.
- Inputting debit or credit card details into a fake payment portal, so they can be scraped and used by criminals or sold on the dark web.
- Clicking a link embedded with malicious software that infects a user’s device, such as malware, spyware, and ransomware.
Depending on the skill and ruthlessness of the bad actor, a phishing attack could wipe out a victim’s livelihood. This is a story that happens far too often.
Impact for the Makati Government
After the Covid-19 pandemic began, we saw governments across the world rapidly set up online services to provide relief for their citizens. Unfortunately, some of these services were set up in haste and were released without the necessary security precautions.
Failures like this erode public trust in the government and their services, which directly results in fewer people wanting to access these valuable services.
Advice from Experts
The City of Makati could have easily avoided exposing its participants’ data if it had taken some basic security measures. These include, but are not limited to:
- Secure its servers.
- Implement proper access rules.
- Never leave a system that doesn’t require authentication open to the internet.
- Any company or public agency can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online data from hackers.
Securing an Open S3 Bucket
It is crucial to acknowledge that open and publicly accessible S3 buckets are not a vulnerability inherent to AWS. Rather, they typically occur due to mistakes made by the bucket owners themselves. Amazon offers comprehensive guidance to AWS users, providing them with detailed instructions on how to secure S3 buckets effectively and maintain their privacy.
In this case, the quickest way to fix this error would be to:
- Make the bucket private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to the S3 bucket to further restrict who can access it from every point of entry.
For Users of Proud Makatizen
If you have used Proud Makatizen and are concerned about how this breach might impact you, contact the department directly to find out what steps it's taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included a major report on how millions of people were exposed by a data leak from the vulnerability of a Covid-19 surveillance tool in India. We also revealed how the Indonesian government failed to secure a Covid-19 app, exposing over 1 million people in a data leak. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to anonymously report any data breach they find online. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.




Please, comment on how to improve this article. Your feedback matters!