Remote Access VPN vs Site-to-Site VPN — Full Guide 2025
- What Is a Remote Access VPN and How Does It Work?
- The Best Remote Access VPNs for 2025
- What Is a Site-To-Site VPN and How Does It Work?
- Remote Access VPN vs Site-To-Site VPN: Pros and Cons
- The Differences Between a Remote Access VPN and Site-To-Site VPN
- FAQs on Remote Access VPNs vs Site-To-Site VPNs
- Conclusion
Whether you’re new to VPNs or an experienced user, understanding the different types of VPNs available for business use can be daunting.
Businesses first used VPNs to extend private networks over the public internet, allowing remote workers to connect to a company’s LAN (local area network).
Initially, two basic VPN types were used to achieve this networking solution: remote access VPNs and site-to-site VPNs. In this article, I break down the VPN types and show you how to pick the right one for your needs.
What Is a Remote Access VPN and How Does It Work?
Remote access VPNs (also known as client-to-site VPNs) let off-site employees connect to their organization's network (LAN) or a remote server using personal devices. These VPNs enable you to access secure resources on your company's LAN as if you were physically connected to it.
These VPNs are more closely related to consumer VPNs, which are used to protect your online identity and activity, like ExpressVPN. Their main aim, like all VPNs, is to secure your data. In this setup, the remote user's device handles data encryption and decryption that’s either sent or received.
A remote access VPN relies on a network access server (NAS), or VPN gateway to function, which authenticates any device attempting to connect. It’s the NAS that you, as a teleworker, interface with when using a remote access VPN.
With this configuration, the client software must also be installed on the off-site worker’s device. This software communicates with the VPN gateway, which authenticates you as a remote user and creates a secured "virtual” tunnel between the LAN and the gateway.
Once the tunnel is created, any data sent from an off-premise employee’s device is encapsulated and encrypted by the remote access VPN. It’s then transmitted to the VPN gateway that sits just outside the remote LAN. Upon receipt, the VPN gateway decrypts the traffic and relays it to the LAN.
All traffic, whether sent or received through the virtual tunnel, is secured as it travels. The VPN gateway encrypts the incoming traffic (to you), which is then received by your VPN client.
Today, remote access VPNs are not only tools for connecting employees to company networks; they’re also used by individuals to secure their online activities and traffic, thanks to various VPN providers.
The Best Remote Access VPNs for 2025
1. ExpressVPN — Excellent Speeds for Real-Time Collaboration

Tested June 2025
| Best Feature | Consistently high-speeds and stable connections to work remotely without interruptions |
|---|---|
| Server Network | 3,000 servers in 105 countries to avoid delays due to overcrowding |
| Works With | Netflix, Disney+, BBC iPlayer, Amazon Prime Video, Max, Hulu, Vudu, and more |
| Compatible With | Windows, Mac, Android, iOs, Linux, smart TVs, Fire TV Stick, routers, and more |
ExpressVPN stands out with its proprietary Lightway protocol, which uses less code and won't cause noticeable delays. It is ideal for seamless access to shared files, real-time editing, and smooth video calls. During tests on local servers, my 118.1Mbps base speed was only slightly reduced to 114.03Mbps — a 3% drop.
Your online privacy is protected, thanks to the VPN's military-grade (AES 256-bit) encryption. Perfect Forward Secrecy regularly assigns you a new encryption key, so even in the rare event one is compromised, your past and future sessions are kept private. ExpressVPN's kill switch (Network Lock) also protects you from accidental data exposure by instantly cutting your internet connection if the VPN drops, for example, when your laptop goes into sleep mode.
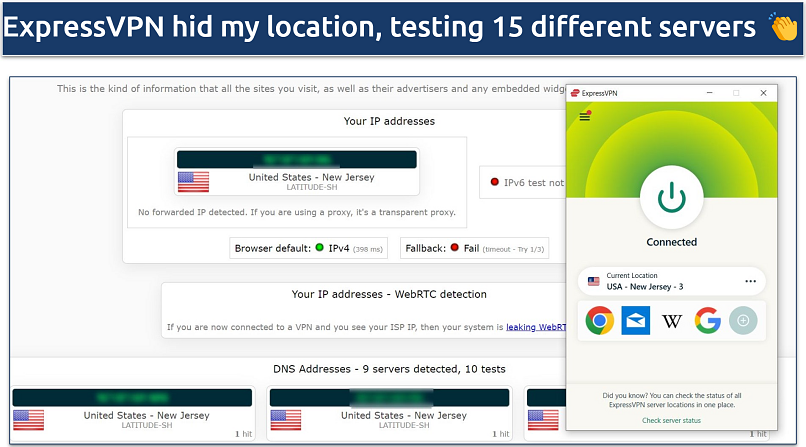 ExpressVPN's IP/DNS leak protection works as advertised
ExpressVPN's IP/DNS leak protection works as advertised
Apps are user-friendly and intuitively designed for all major devices, including computers, smartphones, tablets, and even smart TVs. However, if your device isn't VPN compatible, you can install ExpressVPN on your router using its custom firmware and secure all devices on your network.
On the downside, plans are expensive starting at $4.99/month, but you can save up to 61% and get 3 months of service free with ExpressVPN's regular deals. Plus, all plans have a 30-day money-back guarantee*, and getting a refund is easy when requesting via 24/7 live chat.
Useful Features
- Privacy features. ExpressVPN follows a verified no-logs policy, meaning none of your data is collected or shared. Plus, all its servers are RAM-based — your data gets erased with every reboot.
- Simultaneous connections. You can use one ExpressVPN subscription on up to 8 devices at the same time without any noticeable effect on your devices' performance.
- Smart Location. When you click this feature, you're automatically connected to the fastest server based on your network and location.
2. CyberGhost — Optimized-Torrenting Servers for Fast and Secure Downloads
| Best Feature | Optimized servers are regularly tested and updated for the best performance |
|---|---|
| Server Network | 11,690 servers in 100 countries, with ones optimized for gaming and streaming |
| Works With | Netflix, Disney+, Amazon Prime Video, BBC iPlayer, Max, Hulu, Vudu, and more |
| Compatible With | Windows, Mac, Android, iOs, Linux, smart TVs, Fire TV Stick, routers, and more |
Dedicated P2P servers make CyberGhost an excellent choice for fast file transfers and downloads. You can use the search bar to find a torrenting-optimized server in your country. While testing the CyberGhost UK-torrenting server, I could download large files without delays.
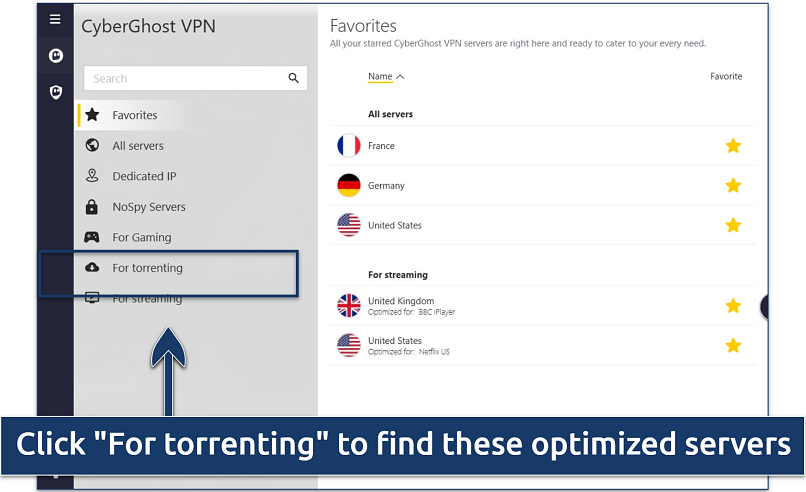 If security is your top concern, you can upgrade to CyberGost's NoSpy servers
If security is your top concern, you can upgrade to CyberGost's NoSpy servers
Advanced security features keep your data safe from snoops and hackers. AES-256 encryption, a kill switch, and leak protection are built into apps for every major platform, making your devices secure. I never ran into any DNS/IP leaks testing CyberGhost's servers. The VPN also uses RAM-only servers and an audited no-logs policy to protect your information against online surveillance.
One minor con is the price of short-term plans with a limited refund period. However, you can try CyberGhost free for 45 days using its extended money-back guarantee on long-term subscriptions, which only cost $2.19/month. Getting a refund is easy if it’s not for you. I submitted my request via its 24/7 live chat and it took only 4 days for the money to reflect in my bank account.
Useful Features
- Fast speed. Like ExpressVPN, CyberGhost is fast — I only had a 5% drop from a base connection of 123.31Mbps. The best VPNs decrease speeds by 10-20% on nearby servers, so CyberGhost's results are great.
- Easy to use. The apps are straightforward and look and work the same on different devices. It took me less than 5 minutes to install CyberGhost on my Windows laptop and connect to a server.
3. Private Internet Access (PIA) — Unlimited Connections To Protect All Your Devices Simultaneously
| Best Feature | Secure all your devices with one subscription at no additional cost |
|---|---|
| Server Network | 29,650 servers in 91 countries, including ones optimized for streaming |
| Works With | Netflix, Disney+, Amazon Prime Video, BBC iPlayer, Max, Hulu, Vudu, and more |
| Compatible With | Windows, Mac, Android, iOs, Linux, smart TVs, Fire TV Stick, routers, and more |
With PIA, you can secure all devices for only $2.19/month, which is ideal for a business. During my tests, I connected PIA to 8 devices at once, including an Android tablet, 3 Windows laptops, and several smartphones. I averaged 114.71 Mbps (only a 7% speed loss) testing a UK server from Camden, London.
Its choice of encryption level and protocols lets you balance speed with security. AES 256-bit with OpenVPN is my go-to for online banking as it offers the best protection. However, WireGuard was always the fastest during my tests. Like ExpressVPN, there's also a kill switch, leak protection, and it follows a court-proven no-logs policy. While these customization options might be overwhelming to beginners, everything is pre-configured for online security.
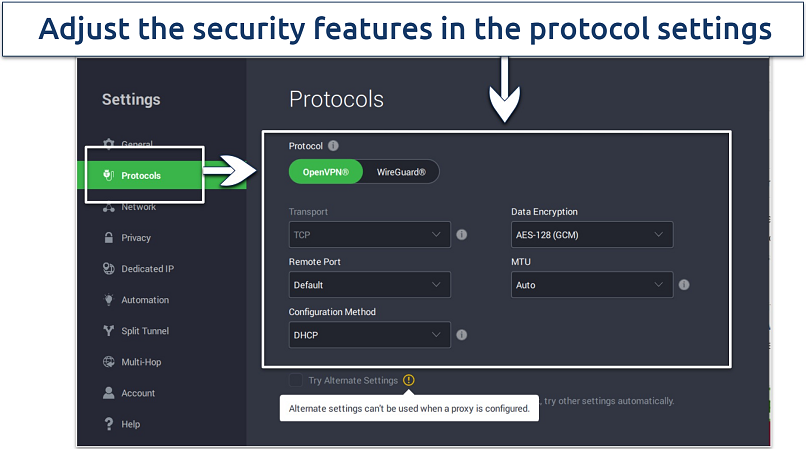 If your network is slow, you can adjust your MTU size for small packets
If your network is slow, you can adjust your MTU size for small packets
You can add a layer of anonymity by paying for your subscription using cryptocurrencies. All PIA plans are backed by a trustworthy 30-day money-back guarantee.
Useful Features
- 24/7 Customer support. PIA's support is on standby round the clock to assist you with more advanced configurations, such as split tunneling and SOCKS5 proxy.
What Is a Site-To-Site VPN and How Does It Work?
Whereas remote access VPNs safely connect individual devices to a remote LAN, site-to-site VPNs securely link two or more LANs in different physical locations. They use the public internet to extend your company’s network across multiple office locations.
There are two common types of site-to-site VPNs: intranet-based and extranet-based. The best choice depends on your organization's specific operational needs. Intranet-based site-to-site VPNs combine the LANs of multiple office locations into one single private network, creating a WAN (Wide Area Network).
Extranet-based site-to-site VPNs, on the other hand, allow your company to use the public internet to connect its LAN with those of other companies, customers, or communities. This allows your company to share information with its partners, while still securing its LAN (intranet).
With a site-to-site VPN, the VPN gateway of one remote LAN communicates with the gateway of another LAN (or HQ network) to create a secure tunnel. Unlike remote access VPNs, the remote devices don’t need a VPN client, but rather send normal traffic through the VPN gateways.
In the absence of VPN clients, the VPN gateways are in charge of authentication of the user and the network, encryption, and data integrity. The gateway receives the encrypted data, decrypts it, and then sends the data to the target device in the network.
The tunnel created by the site-to-site VPN allows your company to share its network and resources between its main and remote branches – no matter the distance. Devices on one LAN can communicate with devices on the other LAN as though they are part of the same network.
There are two main methods for creating a site-to-site VPN: Internet-based VPN and MPLS (Multiprotocol Label Switching) VPN. Below, I’ll briefly walk you through the basics of these two VPN techniques.
Internet-Based VPN
The internet VPN method combines the company’s existing network with public internet infrastructure. As described above, a VPN gateway (a router, switch, VPN-enabled firewall, or VPN concentrator) is required at both LAN locations attempting to establish a secure site-to-site tunnel.
Most internet-based site-to-site VPNs use IPSec (Internet Protocol Security) to secure traffic across the WAN. If both LANs are already connected to the internet, why not use this connection? Well, IPSec leverages the preexisting internet as the backbone of its encrypted communication.
IPSec secures IP packets one at a time. In doing so, it reliably provides WAN traffic with confidentiality (all bits are encrypted), integrity (no bits were tampered with during transmission), and authentication.
Because IPSec encrypts packets at the outgoing router, the final addresses of packets remain hidden until the receiving router decrypts it.
Additionally, because the packets are encrypted during travel over the internet, the data would appear as illegible ciphertext in the event that it was captured.
MPLS-Based VPN
With MPLS, the VPN connection is created using a service-provided MPLS cloud rather than public internet infrastructure.
Unlike internet-based site-to-site VPNs where a company uses its own infrastructure, MPLS VPN uses proprietary infrastructure owned by the VPN. This MPLS network, including its cloud, functions as the tunnel by which a company creates virtual connections between office sites.
MPLS VPNs stand out in regards to the quality of service and ease of set-up. Using labels for data forwarding prevents the need for extra header info that most VPNs use for encryption. This results in peak network performance, ideal for delay-sensitive applications like VoIP (Voice over IP).
MPLS providers will guarantee that the security and performance demands of your business are met. Furthermore, MPLS offers interface independence, meaning that each of your sites can have different connections (i.e. T1, Fiber Optic, DSL) to the MPLS infrastructure.
The downside of an MPLS VPN is the price. These VPNs, like other private WAN technologies, are very costly — particularly if your WAN has hundreds of locations or international connections.
Remote Access VPN vs Site-To-Site VPN: Pros and Cons
Benefits of a Remote Access VPN
Remote access VPNs offer a powerful toolkit for both businesses and individuals seeking secure and flexible connections. Here are some of the key benefits:
- Enhanced Security. A VPN encrypts data traveling between a remote device and the company network, creating a secure tunnel. This safeguards sensitive information from interception by hackers or prying eyes, especially on public WiFi connections.
- Simple setup and management. Compared to site-to-site VPNs, remote access VPNs typically require less complex configuration and ongoing management, thanks to user-friendly apps that automate the setup.
- Business continuity. Maintains business operations by supporting constant access to necessary resources, which is critical during unexpected disruptions like natural disasters.
- Cost-effective. Remote access VPNs offer a cost-effective alternative to establishing dedicated leased lines for remote access.
- Mobility and flexibility. Employees can securely access their work network from anywhere with an internet connection. This allows for true remote work, giving them the flexibility to work from home, while traveling, or anywhere else that suits them.
Drawbacks of a Remote Access VPN
While remote access VPNs offer a wealth of benefits, there are also some limitations to consider:
- Limited control for businesses. Compared to site-to-site VPNs, remote access VPNs offer less granular control over user access to specific resources within the network. This might be a concern for businesses with highly sensitive data.
- Reliance on the public internet. Since VPNs rely on the public internet, performance can be unpredictable due to factors like latency, jitter, and packet loss. Internet outages can also disrupt remote access.
- Potential performance impact. Remote access VPNs encrypt your data, which might slow down your internet. However, selecting a provider with fast servers can help prevent noticeable speed decreases.
- Performance and scalability Issues. Remote access VPNs were not designed for continuous, large-scale use. As more users connect, VPN servers can become overloaded, leading to performance degradation and scalability challenges.
- Require extra software components. This can create compatibility issues, increase management overhead for IT, and introduce potential security risks if the client software is not kept updated
Benefits of a Site-To-Site VPN
Site-to-site VPNs are favored by many organizations for securely linking different office locations. Here's why they're so valuable:
- Secure data transmission. The core advantage of site-to-site VPNs is their ability to encrypt traffic between multiple sites. This protects sensitive data from snoops and hackers during transmission.
- Scalability. As your business grows, so does your site-to-site VPN, allowing you to add new office locations to the network without major changes or disruptions.
- Organized network. Imagine dividing your network into secure sections. Site-to-site VPNs can do this, giving specific departments or offices access only to what they need. This keeps things organized and strengthens security.
- Seamless collaboration. Site-to-site VPNs allow for effortless collaboration and file sharing, no matter how far apart your teams are. Working on a project together feels like everyone's in the same room, even if they're in different cities or countries.
- Simplified access and network control. These VPNs treat all network users as internal, making it easy to manage who can access specific resources. It's like having a VIP pass for your company network. You can even control settings and access rights from one central location for all your connected offices, saving time and effort.
- No extra apps. Employees don't have to install any special software on their devices. They just connect to the office network, and the VPN takes care of the rest.
- Backup connections. Site-to-site VPNs can act as backups. They can keep your offices connected even if there's a problem with one connection to keep communication flowing.
Drawbacks of a Site-To-Site VPN
Site-to-site VPNs also come with some challenges:
- Not Ideal for remote workers. This type of VPN secures traffic within a company's network, and they don’t extend that protection to employees working remotely. If your business has a significant remote workforce, a remote access VPN is a better choice.
- Complex configuration and management. Each office pair needs its own VPN setup. If your business has many locations, keeping an eye on these connections can also become complex and challenging. This is especially true for smaller companies with limited IT support.
- Limited security features. The main function of this VPN is to encrypt data between offices. It doesn't include more advanced security features, which means you might need extra security tools for full protection.
- Internal network vulnerabilities. While they protect data moving between different office networks, site-to-site VPNs don’t secure the data or devices within each network from internal security risks.
An Example of a Company That Can Use a Remote Access VPN
Think about a Boston-based food truck business that expands to Los Angeles and New York. While each truck will have a handful of employees, and each city will have a few trucks, only one device per truck needs secure access to HQ's LAN to record transactions, orders, etc.
Whereas a site-to-site VPN would be overkill, and no VPN at all would be unwise, a remote access VPN would be a cost-effective and ideal solution for this company’s needs. Any compromises in speed and performance will largely go unnoticed.
An Example of a Company That Needs a Site-to-Site VPN
How about a Shanghai-based pharmaceutical company that chooses to open labs in Tel Aviv and Austin? The number of employees at each lab could range from the tens to the hundreds, and each worker will need access to shared servers on the main network.
Site-to-site VPNs allow multiple users’ traffic to flow through each VPN tunnel. Remote access VPNs also support multiple users' traffic through each tunnel, but they are optimized for individual user connections.
Thus, it’ll be easier and more efficient for both the company and its employees to use a site-to-site VPN. While a dedicated connection could be used for each lab, the network demands (i.e. fast upstream speeds) of each lab don’t necessarily justify the very high cost of operating these connections. Rather, the company can use existing internet connections to set up an internet-based site-to-site VPN that connects the labs.
Despite the VPN’s substantial set-up and maintenance costs, it will save the company hundreds of thousands of dollars per year when compared to the cost of dedicated connections for all locations.
The Differences Between a Remote Access VPN and Site-To-Site VPN
Choosing between a remote access VPN and a site-to-site VPN hinges on your needs. For example, consider whether you need to support individual users or connect networks securely across the internet. The table below outlines the key differences between remote-access VPNs and site-to-site VPNs to help you make informed decisions:
| Feature | Remote Access VPN | Site-to-Site VPN |
| Purpose | Connects individual devices to a remote network | Connects entire Local Area Networks (LANs) across locations |
| Client setup | Required on user devices | No client software is needed on individual devices |
| User access | Provides access for individual users | Provides access for all users on connected networks (treated as internal) |
| Scalability | Easier to scale for individual remote users | Can become complex to manage with many locations |
| Connection | Temporary | Permanent |
| Security focus | Encrypts data traffic between the user’s device and remote network | Secures data transmission between networks |
| Internal network security | May require extra security measures within the LAN | Doesn't directly address security within each LAN |
| Typical setup | Client-server model | Gateway-to-gateway model |
| Management | Less complex and managed by IT for the central network. | More complex and requires the configuration of VPN gateways at each location |
| Performance | May experience performance impact due to encryption overhead | Generally offers better performance as traffic is not routed through individual user devices |
| Multiple user support | Each user connects individually through separate tunnels | Multiple users across connected LANs share the same network resources |
| Cost | Cost-effective for individual users or small teams | Can be costly due to equipment and setup for multiple locations, but cost-efficient for large-scale operations |
| Best suited to | Remote workers, business travelers, and occasional access users | Connecting geographically dispersed offices |
We recommend consulting a technology expert for guidance, especially for site-to-site VPN setups for optimal configuration. Most companies that use site-to-site VPNs have the service set up and maintained by an IT security company like Cisco, Bynet, or Checkpoint. Perimeter 81 offers both remote access VPN and site-to-site VPN options, allowing you to test them and see which works best for you.
FAQs on Remote Access VPNs vs Site-To-Site VPNs
What protocol to use for remote access VPN vs site-to-site VPN?
Remote access VPNs and site-to-site VPNs use different security protocols, and the choice to use one depends on your organization's needs. Well-known VPN security protocols include OpenVPN, WireGuard, and IKEv2/IPsec.
There are several protocols that play critical roles in securing data transmissions. Some providers are even offering in-house protocols. If you prefer these, we advise caution and recommend giving more preference to the open-source options, as they are constantly checked for vulnerabilities by experts.
What is the difference between a VPN, remote access VPN, and a site-to-site VPN?
A remote access VPN lets individual users securely connect to a central network, such as a company's, from anywhere. A site-to-site VPN securely connects entire office networks, enabling seamless collaboration across locations. Each type has pros and cons to consider before making a purchase.
What key aspects should organizations analyze to determine the most suitable VPN solution for them?
Deciding between remote access and site-to-site VPNs involves multiple factors. First, you need to assess your business needs and then understand the difference between these two options to choose the most appropriate one. This comprehension will help you determine whether to prioritize accessibility for individual users or connections between entire networks. You should also assess if the current network setup will work with various VPN models.
Conclusion
Remote access VPNs and site-to-site VPNs offer unique benefits for securing business networks. Ultimately, the best choice depends on your specific requirements.
Remote access VPNs empower teleworkers and enable them to connect confidently to a central network. Their user-friendliness and scalability make them ideal for today's geographically distributed teams.
On the other hand, site-to-site VPNs excel at creating secure bridges between geographically separated offices, allowing effortless collaboration and resource sharing across locations. By understanding the strengths and limitations of each, you can choose the VPN solution for your organization's security and connectivity needs.
Your online activity may be visible to the sites you visit
Your IP Address:
216.73.216.112
Your Location:
US, Ohio, Columbus
Your Internet Provider:
Some sites might use these details for advertising, analytics, or tracking your online preferences.
To protect your data from the websites you visit, one of the most effective steps is to hide your IP address, which can reveal your location, identity, and browsing habits. Using a virtual private network (VPN) masks your real IP by routing your internet traffic through a secure server, making it appear as though you're browsing from a different location. A VPN also encrypts your connection, keeping your data safe from surveillance and unauthorized access.




Please, comment on how to improve this article. Your feedback matters!