Report: Online Fashion App Exposes Financial Records of Top European Influencers
vpnMentor’s cybersecurity research team, led by Noam Rotem, recently discovered that e-commerce app 21 Buttons was exposing private data for 100s of influencers across Europe.
21 Buttons mixes online shopping with social media. Users post photos of their favorite outfits with links to the brands they’re wearing. Their followers can then purchase their favorite items directly from the relevant brands from within the app.
Users on 21 Buttons’ Rewards program earn a commission for any purchases made via their profiles.
The company was storing over 50 million pieces of data from the app on a misconfigured AWS cloud storage bucket. Buried amongst all this data, we discovered invoices for commissions paid by 21 Buttons to 100s of influencers all around Europe, based on the value of sales made through their profiles.
The invoices exposed a massive amount of information about how much individual influencers earn on 21 Buttons, along with incredibly sensitive personal information.
Had these records fallen into the hands of criminal hackers, the consequences for those exposed would be profound.
Data Breach Summary
| Company | 21 Buttons |
|---|---|
| Headquarters | Barcelona, Spain |
| Industry | Social Media; e-Commerce |
| Suspected no. of files | Over 50 million; includes 400+ invoices |
| No. of people exposed | Potentially millions had already-public data exposed; private data for hundreds of people also exposed. |
| Date range/timeline | Aug 2016 - Oct 2020 |
| Geographical scope | Worldwide/Europe |
| Types of data exposed | Social media posts and profiles; invoices; PII data and financial information |
| Potential impact | Phishing; fraud and identity theft; stalking, harassment, loss of privacy |
| Data storage format | Misconfigured AWS S3 bucket |
Company Profile
21 Buttons is a Spanish ‘social commerce’ company founded in Barcelona in 2015.
The company’s flagship app combines fashion, social media, and e-commerce. Influencers upload photos with their favorite wardrobe pieces to 21 Buttons and link to the stores where they’re available.
Their followers can then save these pieces, combine them with other outfits, and purchase them directly from the respective stores.
Influencers earn a commission for any purchases made via their profile. Their followers enjoy a seamless and convenient shopping experience, easily replicating the looks of their favorite influencers.
21 Buttons has quickly grown popular in Europe, with an estimated 2 million monthly active users in 2018, and partnerships with the biggest brands and influencers on the continent.
The same year, it secured USD$17 million in private investment to expand to the US. 21 Buttons has raised USD$30 million in funding since it launched.
Timeline of Discovery and Owner Reaction
- Date discovered: 2nd Nov. 2020
- Dates vendors contacted: 5th Nov., 12th Nov., 8th Dec. 2020
- Dates Amazon Contacted: 10th Nov., 8th Dec. 2020
- Date of Response: 22nd Dec. 2020
- Date of Action:
Sometimes, the extent of a data breach and the data’s owner are obvious, and the issue is quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s exposing the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, 21 Buttons was using an AWS S3 bucket to store user uploads and data from its app. S3 buckets are a popular cloud-based storage solution for app developers across the globe.
However, 21 Buttons has not followed AWS security protocols, leaving the bucket (and all data stored within) publicly accessible.
Our team discovered the bucket and quickly identified 21 Buttons as its owner. After confirming the company owned the data and other aspects of the breach, we reached out to 21 Buttons and presented our findings.
After several attempts to make contact with 21 Buttons, we finally received an answer from their customer support (over a month and a half since our first contact attempt). They informed us that they forwarded our "message immediately to the correspondent department”, who would contact us after reviewing our disclosure.
At the time of publication, we are still waiting to be contacted.
Example of Entries in the S3 Bucket
One unique aspect of 21 Buttons is that anyone can connect their public profile with any retailer available through the app to become an influencer.
And it appears the bucket contained media files from every single user on the 21 Button app.
In total, over 50 million files were stored in a single S3 bucket, most of them photos and videos uploaded to the app.
As there is no clear organization of the information, it's impossible to know how many people were exposed and if any other types of files were exposed.
However, 21 Buttons has over 5 million downloads just on Android and boasts millions of monthly active users. We believe the bucket contained media files from every single user on the app.
It appears that all this data was already publicly available on the app and 21 Buttons’ website.
While the exposure of all its user-generated content is problematic for 21 Buttons, there is no threat to users from this aspect of the breach.
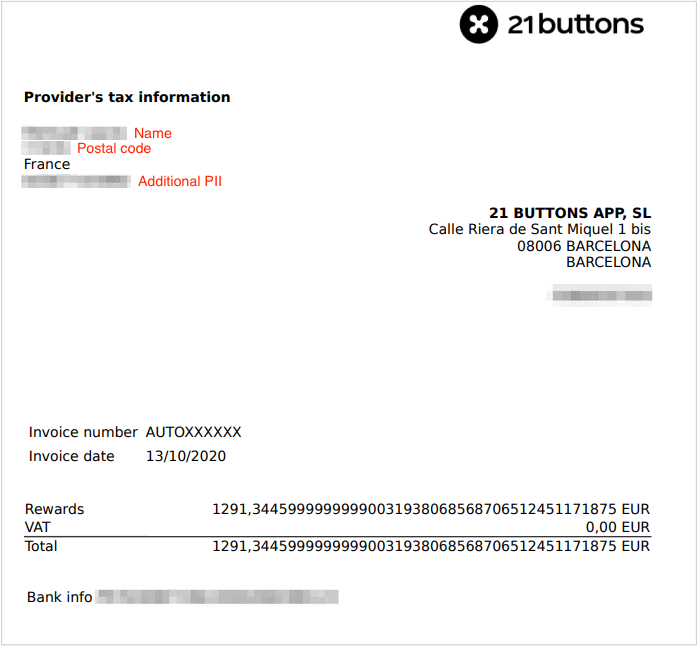
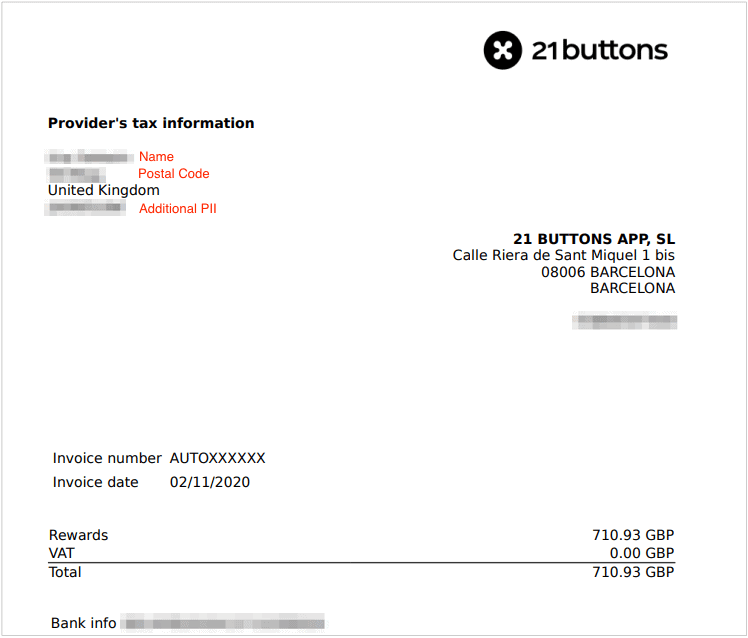
Influencer Invoices
Unfortunately, that’s not all 21 Buttons was storing on the S3 bucket.
Among the millions of photos and videos, we also viewed hundreds of invoices detailing payments to users in the 21 Buttons Rewards program, covering the last few months. Some of these invoices appear to be test data, but many of them were definitely legitimate invoices detailing real records of payments made.
Any 21 Buttons user can join the Rewards program. After joining, they can post an outfit and connect individual items to an online retailer like Zara or H&M. Any time someone purchases an item via their profile, Rewards program users earn a commission.
Most of the invoices exposed in 21 Buttons’ bucket relate to commissions earned by well-known European influencers on the app.
Each invoice contained different forms of personally identifiable information (PII) data and financial information for each influencer, including:
- Full names
- Countries of residence
- Zip and postal codes
- Bank details
- National ID number
- Value of sales commissions earned through 21 Buttons (in various currencies)
- PayPal email address
Big-name influencers whose data we viewed on the bucket include:
While most of the media stored in the bucket was relatively harmless, the invoices represent a massive risk to the privacy and wellbeing of the individuals affected.
Data Breach Impact
If criminal hackers had accessed the invoices in 21 Buttons’ AWS S3 bucket, they could have pursued numerous illegal activities targeting the influencers affected.
Phishing Campaigns, Scams, and Malware
Using the PII data and email addresses included on the invoices, along with publicly available information on an influencer’s profile, hackers could create incredibly effective phishing campaigns.
In a phishing campaign, hackers and cybercriminals send victims fraudulent emails imitating real businesses. The emails trick victims into providing sensitive data like bank account and credit card details. They may also be asked to click a link that embeds their device with malware, spyware, ransomware, etc.
Hackers could take the information exposed in the invoices and appear as 21 Buttons querying transactions, requesting updated financial information, and much more. Access to each invoice’s monetary values would allow them to create convincing emails, quickly establishing trust and deceiving countless victims.
Identity Theft and Fraud
Hackers could combine the information obtained through 21 Buttons’ data breach, users’ public posts, and successful criminal phishing campaigns to pursue various forms of financial fraud.
This could include anything from credit card fraud and bank account takeover to wholesale identity theft.
By the time someone realizes they’ve been defrauded, it may be too late. It would also be almost impossible to trace the origins of any fraud scheme back to 21 Buttons.
Loss of Privacy, Stalking, and Harassment
Most social media influencers try to keep their PII data secret and completely hidden. However, by exposing their contact details, home addresses, and national ID numbers, 21 Buttons has compromised the privacy of everyone affected.
If somebody shared the invoices publicly, bad actors would have plenty of material to identify any private accounts held by influencers, as well as their homes and workplaces.
This doesn’t just make the people affected vulnerable to phishing and fraud, as detailed above. They’re also at risk from an invasion of privacy, doxing, stalking, and harassment - both online and offline.
Risks for 21 Buttons
21 Buttons may also face negative backlash and other consequences as a result of this data breach.
Fines and Legal Action
21 Buttons is based in Spain, with most of its users living within the European Union. As a result, the company operates within the jurisdiction of GDPR. It will need to take swift action to resolve the data breach or face potential fines or legal action from the regulatory body.
Loss of Customers and Partners
While this breach represented a small aspect of 21 Buttons’ growing business, people may question its broader data privacy practices as a result.
Regular users, influencers, and companies may be reluctant to use an app discovered to be exposing such detailed financial and PII data.
While innovative, 21 Buttons’ business model isn’t unique. There are plenty of other platforms that offer similar mixes of e-commerce and social media, such as Instagram.
By revealing how much (or how little) big influencers make on its app, 21 Buttons could damage its perceived value as a way to earn money online.
This is significant for a company in its early ‘growth’ stage, where the ability to attract new users is based largely on what they believe they can earn on the app.
Negative Publicity
As the ‘social commerce’ industry is such a competitive space, rivals of 21 Buttons may exploit the data breach to entice users over to their platforms and apps.
Big companies like Instagram and its parent, Facebook, could seize the opportunity to catch up with 21 Buttons and offer their social commerce features as a safer alternative.
All of these outcomes could have a significant negative impact on 21 Buttons’ short term revenue and long term growth.
Advice From the Experts
21 Buttons could have easily avoided exposing its users’ data if it had taken some basic security measures. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
- Always store user data and operations data separately.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online data from hackers.
Securing an Open S3 Bucket
It’s important to note that open, publicly viewable S3 buckets are not a flaw of AWS. They’re usually the result of an error by the owner of the bucket. Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
In the case of 21 Buttons, the quickest way to fix this error would be to:
- Make the bucket private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to their S3 bucket to further restrict who can access it from every point of entry.
For 21 Buttons Users
If you’re concerned about how this breach might impact you, contact the company directly to determine what steps it's taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy. It shows you the many ways cybercriminals target internet users and the steps you can take to stay safe.
How and Why We Discovered the Breach
As part of an extensive web mapping project, the research team at vpnMentor identified a breach in 21 Button's data security. Our investigators utilize port scanning to inspect specific IP blocks and assess different systems for any weaknesses or vulnerabilities. Each detected weakness is thoroughly evaluated for potential data exposure.
Our team was able to access this S3 bucket because it was completely unsecured and unencrypted.
Whenever we find a data breach, we use expert techniques to verify the data’s owner, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to 21 Buttons, not only to let them know about the vulnerability but also to suggest ways to make their system secure.
These ethics also mean we carry a responsibility to the public. 21 Buttons users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We have no evidence - and no way of knowing - whether the data in our reports have been accessed or leaked by anyone else; only the database owner can know that.
We do our best to prevent this from happening by reaching out to the companies and ensuring they secure their leaking database as soon as possible.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included an enormous data leak exposing millions of Indian COVID-19 patients. We also revealed that global pharmaceutical company Pfizer compromised the privacy and security of 100s of US cancer patients and Viagra users. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to anonymously report any data breach they find online. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.
[Publication date: 23.12.2020]



Please, comment on how to improve this article. Your feedback matters!