Report: Online Fashion Retailer Exposes European Customers in Massive Data Leak
Led by Noam Rotem and Ran Locar, vpnMentor’s research team recently discovered a leak in a database belonging to Polish online fashion retail company, BrandBQ.
BrandBQ owns several retail and fashion brands operating in Eastern Europe. It appears the exposed database belonged to at least one of these brands’ websites, Answear. The database also included entries from another BrandBQ website, WearMedicine.com.
The database contained an enormous amount of data, over 1 terabyte, and was leaking incredibly sensitive personal and financial data belonging to online shoppers visiting the websites.
By leaking this data, BrandBQ compromised the safety and security of millions of people across Eastern Europe, exposing them to fraud, financial scams, and wholesale identity theft.
Data Breach Summary
| Company | BrandBQ |
|---|---|
| Headquarters | Krakow, Poland |
| Industry | Fashion Retail |
| Size of data in gigabytes | 1 Terabyte |
| No. of records | Over 1 billion |
| No. of records exposing people | Up to 6.7 million |
| Date range/timeline | June 2020 |
| Geographical scope | Poland, Romania, Hungary, Bulgaria, Slovakia, Czech Republic |
| Types of data exposed | Full name, phone number, email, DOB, IP address, home address, gender, product searches, payment records |
| Potential impact | Identity theft and fraud; phishing and malware; Corporate espionage; hacking and attacks |
| Data storage format | Open & unencrypted Elasticsearch |
Company Profile
Founded in 2010, BrandBQ is currently based in Krakow, Poland, and operates in seven countries across Eastern Europe: Poland, Romania, Hungary, Bulgaria, Slovakia, Ukraine, and the Czech Republic.
The company owns a selection of fashion and clothing retail brands that are also a mix of online and physical stores.
While Answear stocks and sells well-known international brands, such as Adidas, Levis, and Calvin Klein, WearMedicine.com exclusively sells its own name-brand products.
BrandBQ is a fast-growing company, with over 700 employees and US$61.21 million in sales across its brands.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue is quickly resolved. But rare are these times. Most often, we need days of investigation before understanding what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, we discovered the database stored on an unencrypted Elasticsearch server. Entries in the database contained the names of at least two BrandBQ companies: Wear Medicine and Answear. Furthermore, the server was hosted by a company in Poland, where BrandBQ is headquartered.
Through additional investigation, we decided BrandBQ was the most likely owner of the database, using it to store records from at least two of its brands.
To confirm the validity of the entries and ensure they belonged to real people, we verified a sample of email addresses exposed in the database.
Upon confirming the various details of the leak, we reached out to Answear and WearMedicine to present our findings. After some delay, BrandBQ (the parent company) reached out to us to confirm that the leak had been closed and the data was secure.
The company was proactive and responsible in its response to the leak and ensuring that there was no longer a threat to its customers. Unfortunately, this is often not the case, as most companies don’t take responsibility for the leaks we report.
- Date discovered: June 28, 2020
- Date Answear contacted: June 30, 2020
- Date of 2nd contact attempt (WearMedicine): July 21, 2020
- Date of 3rd contact attempt (BrandBQ): August 5, 2020
- Date of Action (leak secured): August 20, 2020
- Date of Response from BrandBQ: August 20, 2020
Example of Entries in the Database
BrandBQ’s database contained over 1 billion entries, including up to 6.7 million records related to the data of people using its websites.
Most of the database's entries were activity logs from customer actions on the affected websites, including newsletter registrations, purchases (and related checkout details), user agreements, and more.
New activity logs were uploaded every hour throughout July 2020, creating new records every time, explaining the volume of data stored.
Every one of these entries contained a wide range of Personally Identifiable Information (PII) data for potentially millions of people. These included:
- Full names
- Phone numbers
- Email addresses
- Dates of birth
- Home addresses
- Gender
- Product searches
- Payment records (excluding credit card details)
Such detailed PII data is incredibly valuable to hackers and cybercriminals, who would consider BrandBQ’s exposed database an absolute goldmine.
Aside from activity logs detailing customers' actions and exposing their PII data, the database also appeared to contain approximately 50,000 entries relating to what seemed to be BrandBQ’s local contractors in various countries. We believe the contractors affected were local companies who receive and handle online purchases from BrandBQ websites in their respective countries.
These entries included even more PII data, such as:
- Purchase information from orders
- Product prices
- Full names of the package receivers
- Email addresses
- Home addresses
- Phone numbers
- Payment methods
- VAT numbers
In addition to BrandBQ’s proprietary websites, the database also contained logs of API calls from Answear’s mobile app on iOS and Android. These revealed any actions taken by a user on the app, along with their PII data.
The Answear app has been downloaded over 500,000 times on Android alone, with all those users potentially exposed by this leak. The number of iOS downloads is unknown.
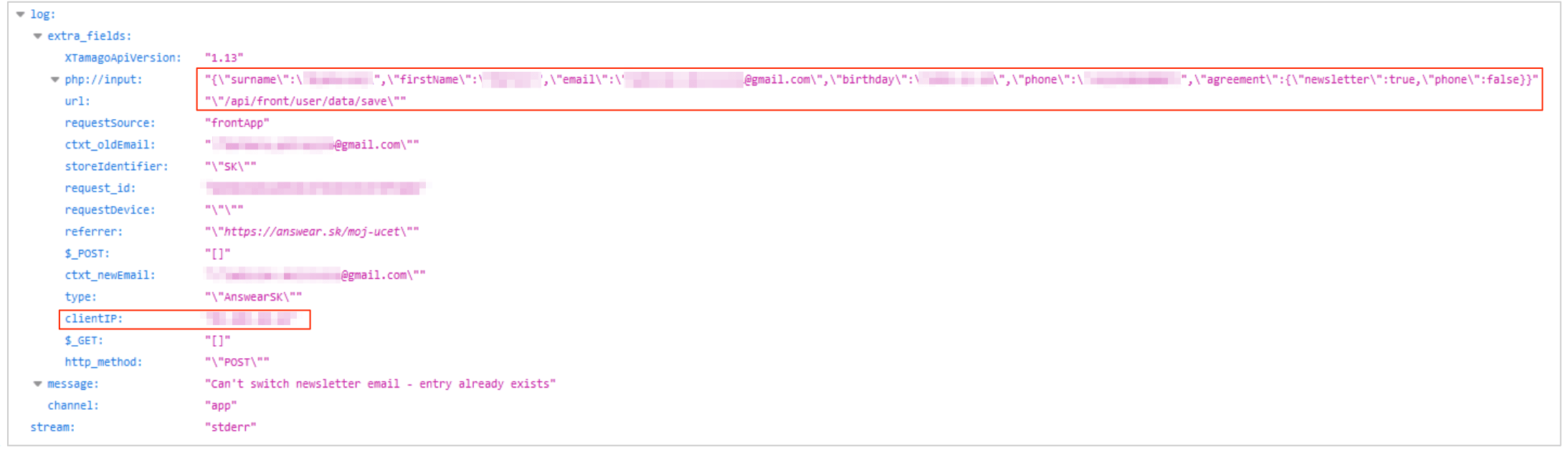
Example #1: entry from a website newsletter section
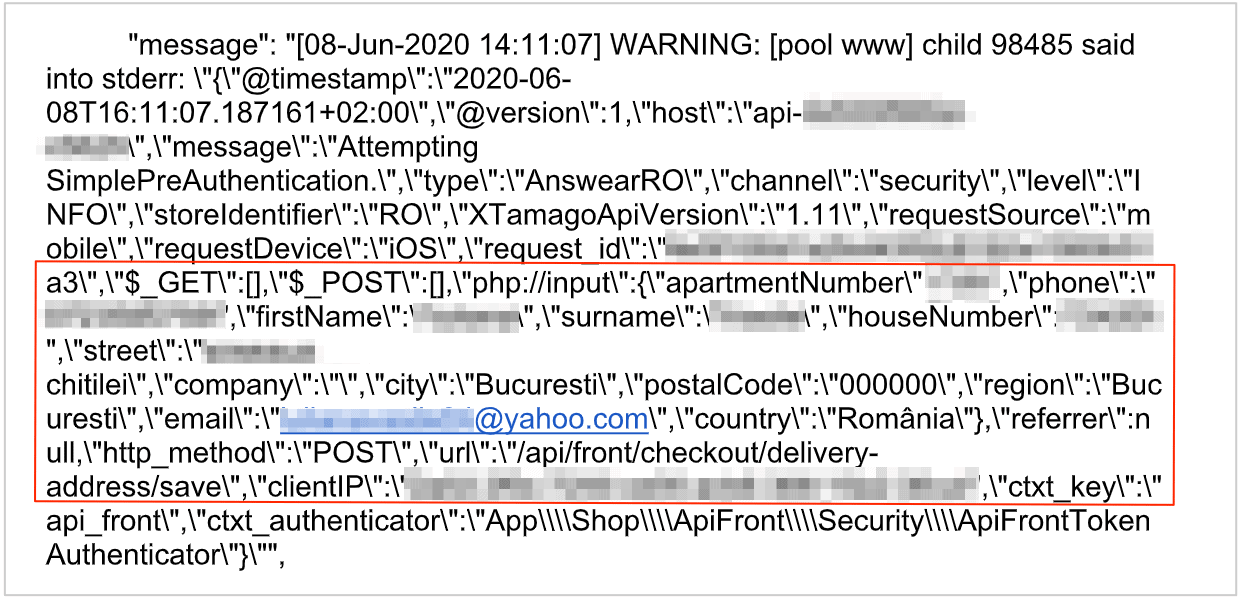
Example #2: entry from iOS app
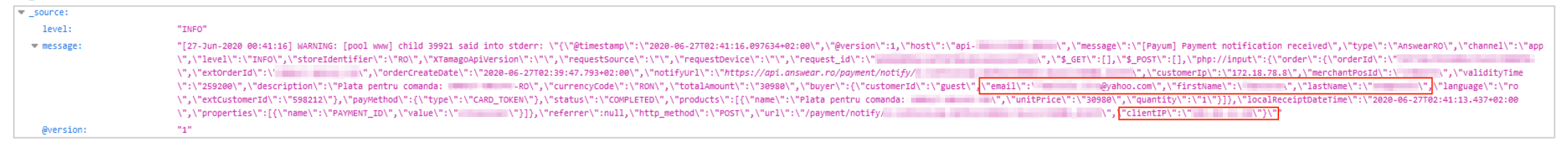
Example #3: payment record from an online purchase
Finally, BrandBQ’s database inadvertently revealed sensitive technical information about its structure and security setup.
This included roughly 49 million entries that exposed how websites using the database responded to system errors and blacklisted emails (if an email address used on a website becomes associated with fraud or spam). They also showed internal logs and other resources within the database.
Combined, this all amounts to an incredible quantity of data, compromising the safety and security of BrandBQ, its subsidiary companies, and its customers.
Had malicious or criminal hackers gained access to the database before we reported it to BrandBQ, the consequences for all those affected could have been devastating.
Data Breach Impact
The data exposed in this leak could be used in many different criminal schemes, targeting both shoppers on BrandBQ’s online stores and the company itself.
Online Fraud and Identity Theft
Cybercriminals could take the exposed PII data and use it to commit various forms of consumer and financial fraud against BrandBQ’s customers, including complete identity theft.
These criminal schemes could occur anywhere on the internet, and even in physical businesses and commercial establishments of different kinds.
It would be incredibly difficult to trace the potential frauds back to BrandBQ’s database, especially if the exposed PII data was shared on the Dark Web.
Phishing and Malware
The PII data and contact details contained in entries on BrandBQ’s database could also be exploited for even more criminal activities. Using this information, hackers and criminal groups could create incredibly convincing phishing emails targeting shoppers on BrandBQ’s websites.
With detailed knowledge about the shoppers and their activities on the websites, the email could easily convince victims to provide additional data, such as credit card details, or click a link embedded with malicious software like malware or ransomware.
The same tactics could be used against the contractors exposed in the leak, and BrandBQ itself. A successful phishing campaign against a business can be absolutely devastating and challenging to overcome. Furthermore, it only takes a single employee with no education on cybercrime to click a link in an email that could infect a company's entire network.
With over 700 employees, this is a real risk for BrandBQ.
Virtual Attacks Against BrandBQ
Aside from phishing emails targeting the company, hackers could use BrandBQ’s database to identify how its online systems and data storage work.
Such information would be a huge asset for anyone trying to attack BrandBQ or find vulnerabilities in its network to exploit.
The result would be highly targeted, devastating attacks that could cripple the company for years.
Corporate Espionage and Legal Issues
Competitors could also exploit the exposed database and use it against BrandBQ.
By monitoring customer and business activity on BrandBQ’s websites, a rival could tweak its offering to be more appealing to shoppers and effectively convert them into customers.
Rival retailers could also target the company with negative publicity over the leak, further enticing customers away from its businesses and impacting its revenue.
Finally, as BrandBQ is based in the European Union, it may face regulatory action from the trade bloc’s GDPR agencies.
Advice From the Experts
BrandBQ could have easily avoided this leak if it had taken some basic security measures to protect the database. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
- Refrain from logging sensitive, personal data unless absolutely necessary. If logging this data is required, it should be encrypted and masked.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For BrandBQ Customers
If you’re a customer of a BrandBQ website and are concerned about how this breach might impact you, contact the company directly to find out what steps it's taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the breach in BrandBQ’s database as part of a huge web mapping project. Our researchers use port scanning to examine particular IP blocks and test different systems for weaknesses or vulnerabilities. They examine each weakness for any data being leaked.
Our team was able to access this database because it was completely unsecured and unencrypted.
BrandBQ was utilizing an Elasticsearch database. By adhering to standard authentication procedures, Elasticsearch can be configured securely without much hassle, ensuring all data remains safe and encrypted.
However, BrandBQ failed to follow these practices. As a result, we were able to access its database via a web browser and manipulate the URL search criteria into exposing schemata from a single index at any time.
Whenever we find a data breach, we use expert techniques to verify the database owner, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to BrandBQ, not only to let it know about the vulnerability but also to suggest ways in which it could make its system secure.
These ethics also mean we carry a responsibility to the public. BrandBQ users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data leaks in recent years.
This includes an enormous leak exposing the data of over 1 million American students. We also revealed that a domestic violence prevention app backed TV personality Dr. Phil compromised the privacy and security of abuse victims in the US. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect the Internet!
Introducing the Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to anonymously report any data breach they find online. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.
Company’s Reply
We also received the following reply from Answear on the 24th of August:
"We are currently working on:
- Review of all security procedures of our data and systems.
- Introducing new procedures and processes that can protect us against mistakes and carelessness of people's work.
- Conducting additional security audits and penetration tests by external companies.
- Train our employees so they can capture all important information flowing to our company through all channels.
We want to draw conclusions from the incident so we can be one of the safest stores operating on the market in the future, where all customer data is safe so that a similar situation cannot happen again in the future.
Regarding the data contained in the Report;
We are impressed with the effectiveness of your internet scanning service in terms of detecting possible leaks and the risk of data leakage. However, we must indicate a few inconsistencies in the report sent to the actual state;
- There have never been 6 million 700 thousand of our customers in this database. We would like to, but we don’t have that many customers yet. As I mentioned, the database stores the basic data of customers who have placed orders, subscribed to the newsletter, registered or logged into the stores within 14 days of the event. In the period from March to August 20, the data of about 500,000 customers appeared in the database and was stored for a period of 14 days. This set of data does not include Answear customers from Poland and Ukraine.
- There were no 50,000 BrandBQ B2B contractors in this database. The number of contractors of this company is several times smaller, and there is no data of business partners there, after the tax identification numbers that some customers leave when they ask for an invoice when making a purchase.
- There were no data of employees in this database, except for those who during this period made a purchase, registered or logged into one of the above-mentioned stores and therefore acted as customers of stores, not employees.
- A large content of the database is a fact, but a large amount of data concerned communication between systems, communication errors and other system errors, and the personal data collected in the log database was multiplied (the same data for the customer registration event, placing an order, registration, etc.) Probably only samples were taken from this database and after the number of events alone, you estimated the number of people whose data could be included in this set, if each event related to the personal data of another client."
[Publication date: 7th July 2020]




Please, comment on how to improve this article. Your feedback matters!