Report: Data Breach Reveals Private Emails of International Manufacturing Firm
Led by Noam Rotem and Ran Locar, vpnMentor’s research team has found a data breach in the email platform used by a South Korean company, DKLOK.
DKLOK is an industrial pipe, valve, and fittings manufacturer with clients located across the globe. The vulnerability found in the database of their email platform gave our team access to their internal & external communications. The team was able to view email communications between DKLOK staff, as well as with their clients, and some personal emails.
Many of the emails were marked private & confidential, revealing highly sensitive information about DKLOK operations, products, and client relations.
The breach affected DKLOK branches in various countries and their international clients.
We made several attempts to contact DKLOK but have not yet received their response. As DKLOK's communications are leaking, we can see records of our own emails to the company - so we know they have received our attempts to contact them. The most absurd part is that we not only know that they received an email from one of the journalists we work with, alerting them to the leak in this report, but we know they trashed it.
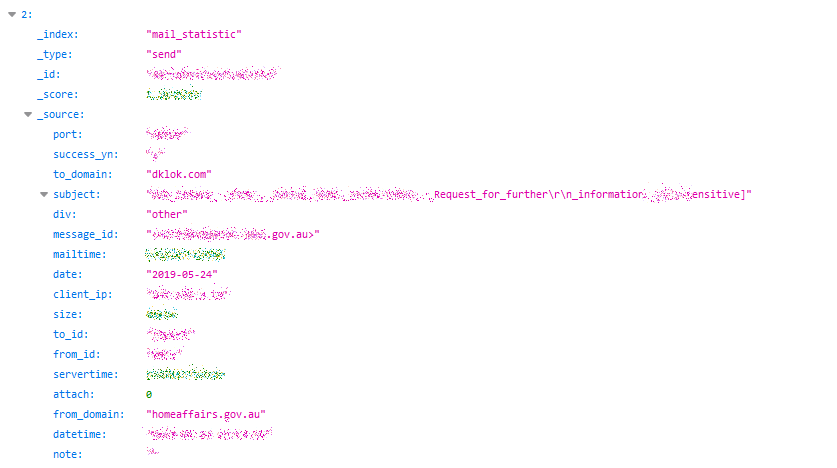
Example of Entries in the Database
The information our team was able to view in private emails between DKLOK employees and their clients included the following:
- Product prices and quotes
- Project bids
- Travel arrangements
- Private conversations
- Discussions on suppliers, clients, projects, internal operations
These involved numerous international offices of DKLOK and customers from around the world. In our research, we viewed communication relating to DKLOK operations in the following countries:
- Iran
- Germany
- Australia
- Israel
- Russia
- South Korea
- USA
- France
- Turkey
- New Zealand
- Italy
- Canada
- Egypt
- Portugal
- Jordan
- South Africa
- Brazil
This list is incomplete, and the final tally would probably be much longer.
Aside from the content of the emails, the beach in DKLOK’s email database gave access to the personal details of their employees and clients. This included:
- Full names of employees and clients
- Internal email addresses from various international DKLOK branches
- Employee/User IDs
- External/client email addresses, full names, phone numbers
- Personal emails received on work email addresses (Alibaba orders, newsletters, Starwood hotels, spam/junk mail for viagra and hair growth products)
- Professional events and conventions attended by DKLOK employees
This leak doesn’t just compromise the security and privacy of DKLOK, but also its clients. Confidential discussions of a highly sensitive nature have been made public in this leak. They give a great deal of insight into DKLOK’s business around the world and compromise the privacy of DKLOK clients.
Data Breach Impact
This data breach has many negative implications for DKLOK. The most obvious is the reputational damage caused to the company. Aside from the internal emails found in the leak, DKLOK clients will not be happy to learn their emails were also viewable.
Privacy and internet security are two of the biggest concerns for businesses in the 21st century. Executives at the companies on DKLOK’s client roster will understandably be concerned that their private communications have been made public - along with confidential insights into their respective businesses.
DKLOK will be under a great deal of pressure to resolve these concerns.
The data leaked in this breach could also be used by criminals, malicious hackers, and dishonest competitors of DKLOK in many illegal schemes.
Once stolen, the data could be sold to competitors and used to undercut DKLOK. The same tactic can also be used to target their clients.
Hackers can use the knowledge gained by reading these emails for use in further corporate fraud. In any cyber-crime, information is crucial. The more private information you can gather about a company, the better you can target them for fraud or malicious attacks.
This data breach gives cyber-criminals a solid foundation on which to start building a profile of DKLOK for future criminal use.
Finally, with access to the personal details and private emails of DKLOK employees, hackers can target individuals for attacks like phishing campaigns.
A phishing campaign involves creating imitation emails of legitimate businesses and organizations, to trick victims into providing private information that can be used to steal from them or plant malware within their network.
The breach gives hackers plenty of options for crafting effective phishing emails to targeting DKLOK employees.
A bigger risk is embedding a link into an email that plants malware or ransomware into the DKLOK network. This could have huge security implications for DKLOK and its clients.
Advice from the Experts
This data leak could have easily been avoided if DKLOK and the email platform it uses had taken some basic security measures. These can be replicated by any company, no matter its size:
- Secure your servers.
- Implement proper access rules.
- Never leave a system that doesn’t require authentication open to the internet.
For a more in-depth guide on how to protect your business, check out how to secure your website and online database from hackers.
For DKLOK
Review your security protocols internally and those of any 3rd party apps and contractors you use. Make sure that any online platform you integrate into your operations follows the strictest data security guidelines.
For DKLOK Clients
If you’re concerned that you have been affected by this data breach, contact DKLOK directly. They will be able to provide an update and explain the steps they’re taking to resolve this issue.
To learn more about your internet privacy in general, and how to avoid data breaches like this one, read our complete guide to online privacy.
How and Why We Discovered the Breach
As part of an expansive web mapping project, the vpnMentor research team found out that DKLOK's email databases were left without protection and encryption. Our cybersecurity experts utilize port scanning techniques to analyze specific IP blocks and assess the vulnerabilities of open spots in systems. Every identified weak point is carefully investigated for any evidence of data leakage.
When they find a data breach, they use expert techniques to verify the database’s identity. We then alert the company to the breach. If possible, we will also alert those affected by the breach.
Our team was able to access this database through a vulnerability in a peripheral system linked to their email hosting service, which has left its entire email database unsecured and unencrypted.
The company uses an Elasticsearch database, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing schemata from a single index at any time.
The purpose of this web mapping project is to help make the internet safer for all users.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. This is especially true when the company's data breach affects outside parties across the globe. In this case, DKLOK’s international clients and partners.
However, these ethics also mean we carry a responsibility to the public. DKLOK customers and clients must be aware of a data breach that impacts them also.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
We recently discovered a huge data breach impacting 80 million US households. We also revealed that Gearbest experienced a massive data breach. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
[Publication date: 05.09.2019]





Please, comment on how to improve this article. Your feedback matters!