Report: X-Rated Social Media App Exposes Users in Massive Data Breach
vpnMentor’s research team, led by cybersecurity analyst Noam Rotem, recently uncovered a data breach originating from the Fleek social media app.
While it appears Fleek ceased operating in 2019, it failed to secure a huge amount of sensitive data collected from users since it launched in 2016.
Fleek was marketed as an ‘x-rated’ alternative to Snapchat’s “Campus Stories”, with similar photo-sharing functions but almost no censorship or moderation of content. As a result, much of the data exposed in this breach contained explicit content, ranging from drug use to sexual imagery.
Furthermore, the discovery exposed a potential scam by the app's operators, who appeared to be monetizing it by targeting users with fake chatbot accounts.
Data Breach Summary
| Company | Fleek App, owned by Squid Inc |
|---|---|
| Industry | Social network |
| Size of data in gigabytes | 32 GB |
| Suspected no. of files | ~377,000 |
| Date range/timeline | 2016-2019 |
| Geographical scope | Primarily US, some global users affected |
| Types of data exposed | Photos; Bot chat scripts |
| Potential impact | Blackmail, extortion |
| Data storage format | Misconfigured AWS S3 bucket |
Company Profile
Fleek was launched in 2016 by developers Squid Inc.
It was marketed as an uncensored alternative to Snapchat “Campus Stories” with the same basic photo-sharing features, including automatic deletion after a specific time.
The app quickly became popular across US college campuses, with students often sharing photos that may otherwise be banned on more ‘family-friendly’ social media apps.
Fleek seems to have been briefly rebranded as Mojo - College Stories before being deleted from all app stores in 2019.
Timeline of Discovery and Owner Reaction
- Date discovered: 13th October 2020
- Date AWS contacted: 19th October 2020
- Date of Action: 21st October 2020
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue is quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s exposing the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, the data was stored on an Amazon Web Services (AWS) S3 bucket - a popular form of cloud storage for app developers.
We quickly identified Fleek as the party likely most responsible for the breach. However, we always conduct a thorough investigation to confirm a database or S3 bucket’s owner.
Because we couldn’t find a lot of information about Fleek or Squid Inc online, our investigation took longer than expected.
Also, since the app was deleted from most online databases, we could not directly contact the developers.
Instead, we reached out to AWS directly, so they could review the S3 bucket account and inform the owners of the breach.
Eventually, we also found the contact details of Squid Inc’s founder and contacted them directly. However, despite reaching out twice, we didn’t receive a reply.
One week after we discovered Fleek’s S3 bucket, it was secured.
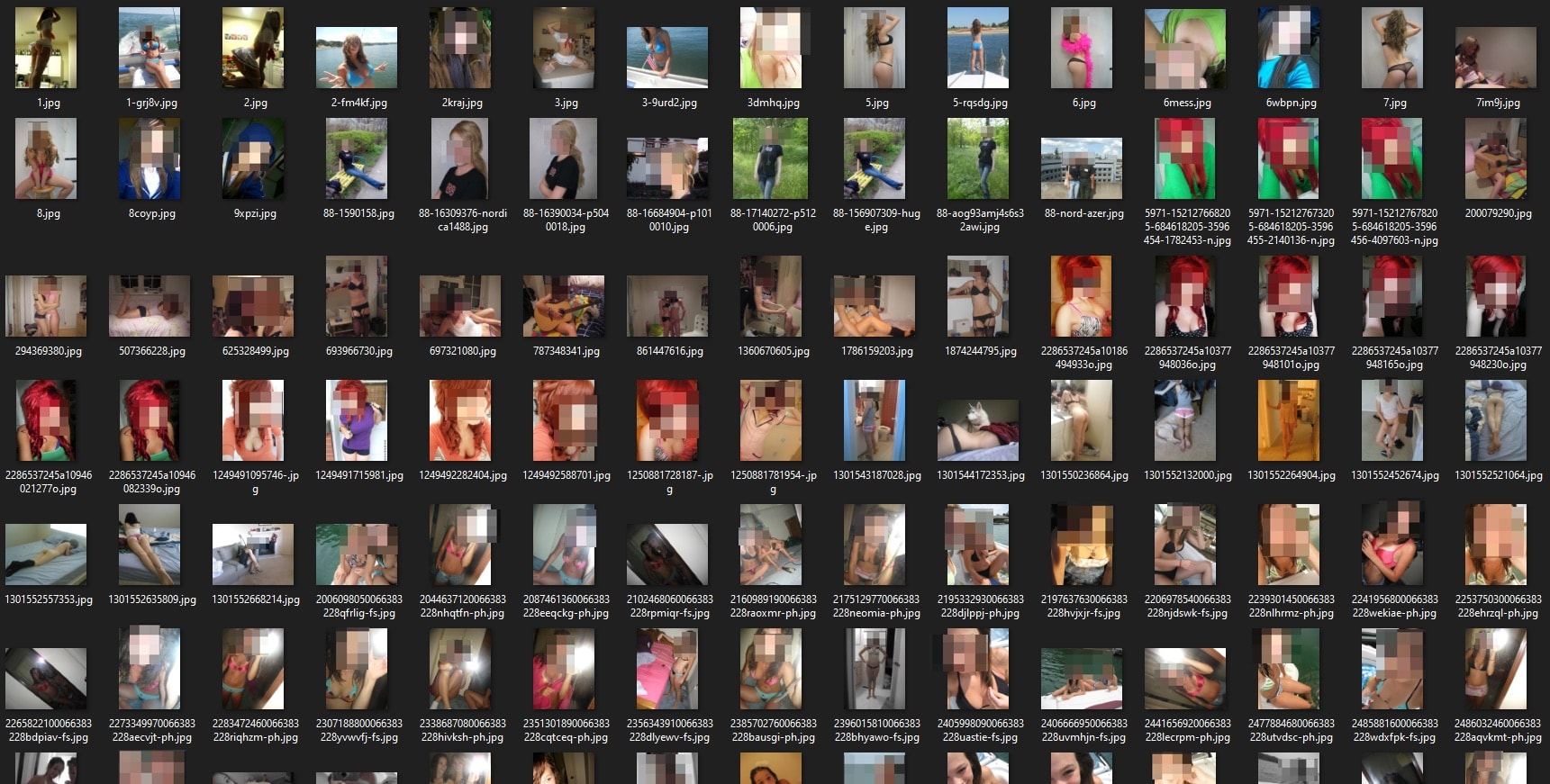
Example of Entries in the S3 Bucket
Like Snapchat, any images uploaded to Fleek were meant to be automatically deleted after a short time.
However, it appears that Fleek’s developers were storing some images uploaded to the app by users - and continued to store them even after they shut the app down.
Since Fleek has been removed from app stores by its developers, there isn’t much information about the app online.
However, we still learned a lot about how people used the app before it disappeared, based on what we found in the S3 bucket.
Most of the data in the S3 bucket consisted of images uploaded by users, including their account avatars.
During our investigation, we reviewed many images of users engaging in embarrassing and illegal activities and sharing sexually explicit photos of themselves.
Many of these were shared in folders given offensive and derogatory names like “asianAss” by the app’s developers.
User Uploaded Images





User Account Avatar Images
Chat Bot Data
We believe the developers were trying to monetize Fleek by promoting a paid chat room between users.
To entice male users into paying for the chat room, Fleek seems to have created fake bot accounts, using photos of young women scraped from the internet and sending messages to men inviting them to chat.
However, the only way users could view the accounts sending them messages - and ensure they weren’t fake - was to pay Fleek a small fee, according to the scripts we found in the bucket.
Unfortunately, most of the accounts were still fake. In fact, it appears they'd been created by Fleek to trick users.
The S3 bucket contained both the fake accounts' images and examples of automated text message scripts sent by the bot accounts.
Bot Account Avatar Images
 Avatar images for fake Fleek bot accounts
Avatar images for fake Fleek bot accounts
Data Breach Impact
For Users
Fleek users were mostly college students naive of the implications of uploading images that show them engaging in embarrassing and criminal activities, such as drug use.
If cybercriminals obtained these images and knew how to find the people exposed, they could easily target them and blackmail them for large sums of money.
For Fleek
While the app closed down in 2019, the person or company paying for the storage of the exposed data could still face legal action or fines from the US government.
Advice from the Experts
Fleek could have easily avoided exposing its users’ data if it had taken some basic security measures. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online data from hackers.
Securing an Open S3 Bucket
It’s important to note that open, publicly viewable S3 buckets are not a flaw of AWS. They’re usually the result of an error by the owner of the bucket. Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
In the case of Fleek, the quickest way to fix this error would be to:
- Make the bucket private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to their S3 bucket to further restrict who can access it from every point of entry.
For Fleek Users
Unfortunately, it's incredibly difficult to contact the people behind Fleek directly and find out if they’re taking any steps to delete or better protect user data.
In the future, never share anything you’d be embarrassed about online - few systems are 100% secure from hacking, leaks, or dishonest people saving incriminating images to hurt you in the future.
It's equally crucial to be aware of the fate of your data if a company that has gathered it either goes bankrupt or ceases operations. In many cases, especially with smaller firms, the owner retains the data, and there are scarce checks and balances in place to prevent potential misuse or future sharing of this information.
There are many examples over the years of companies closing down, not taking measures to destroy or protect user data, and that data eventually leaking out into the public.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered Fleek’s data breach as part of a huge web mapping project. Our researchers use port scanning to examine particular IP blocks and test different systems for weaknesses or vulnerabilities. They examine each weakness for any data being exposed.
Our team was able to access this S3 bucket because it was completely unsecured and unencrypted.
Whenever we find a data breach, we use expert techniques to verify the owner of the data, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in its online security. We reached out to Fleek, not only to let them know about the vulnerability but also to suggest ways to make their system secure.
These ethics also mean we carry a responsibility to the public. Fleek users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We have no evidence - and no way of knowing - whether the data in our reports have been accessed or leaked by anyone else; only the database owner can know that.
We do our best to prevent this from happening by reaching out to the companies and ensuring they secure their leaking database as soon as possible.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included an enormous data breach exposing the data of 1,000s of American cancer patients and Viagra users. We also revealed that the government of the most populous state in India leaked the data of millions of COVID-19 patients. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to anonymously report any data breach they find online. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.
[Publication date: 19.01.2021]




Please, comment on how to improve this article. Your feedback matters!