Report: Inmates’ Prescriptions & PII Leaked in Breach Spanning Multiple Jailhouses
The vpnMentor cybersecurity research team, led by Noam Rotem and Ran Locar, have uncovered a leaking S3 Bucket with 36,077 files of visible data on an Amazon server, belonging to JailCore.
JailCore Company Profile
JailCore is a correctional facility management and compliance cloud-based application, evidently started by the same people behind the insurance consultancy Correctional Risk Services, Inc. Its official parent company is CRS Technologies, LLC, and JailCore is listed as being based in Brentwood, Tennessee, and founded in 2017.
For a technology company, our research team found it odd that there was no available privacy policy nor terms of service for JailCore, and their site is being served unencrypted without a SSL certificate.
Timeline of Discovery and Owner Reaction
Sometimes the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and true.
Date discovered: January 3, 2020
Date company notified: January 5, 2020
Date the Pentagon was notified: January 15, 2020
Date bucket was closed: between January 15 and January 16, 2020
Our team reached out initially to Jailcore directly. They refused to accept the disclosure of our findings. We then reached out to The Pentagon to bring this leak to their attention, and the S3 Bucket leak was subsequently closed.
Examples of Entries in the Database
In an attempt - according to their marketing - for Jailcore to help ensure better compliance with insurance standards by creating their app, their plans have backfired. They have created more of a risk and additional threats to the well-being of those at the nerve-end of the system.
Each detainee that was checked into a detention center, from what we could see, has a number of PII about themselves and their mugshots logged into the system. A portion of this is shared in an online, publicly-accessible roster of current inmates when it comes to county jails, for example. What’s not meant to be available to all is individual specific medication information and additional sensitive data. Also included were the full names of correctional officers (and occasionally their signature), associated with personally-filled out observation reports and the like.
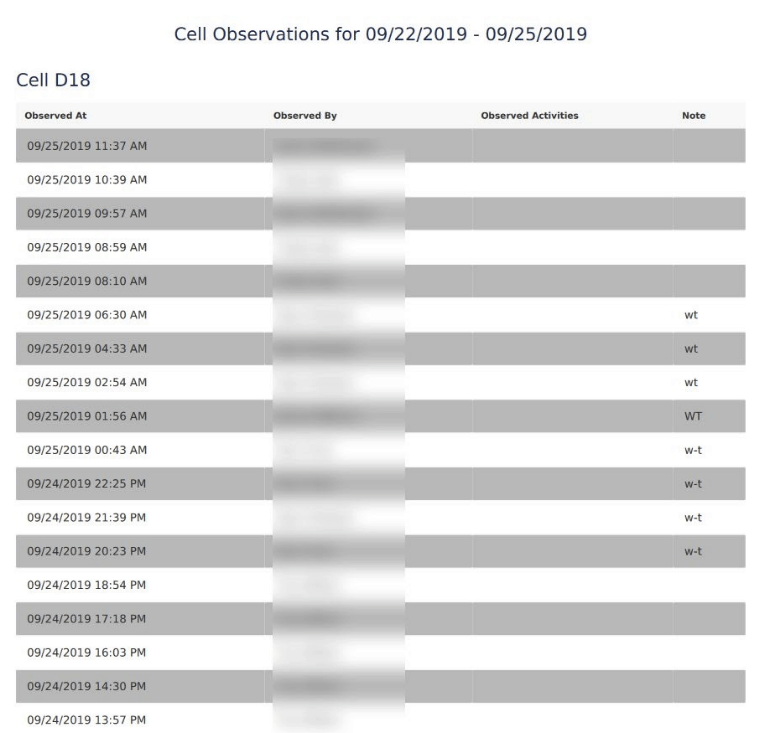
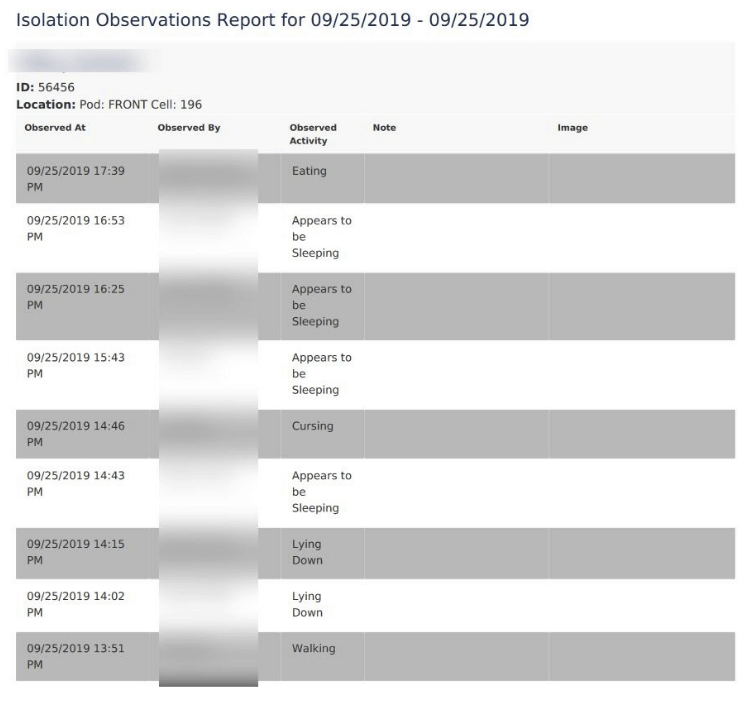
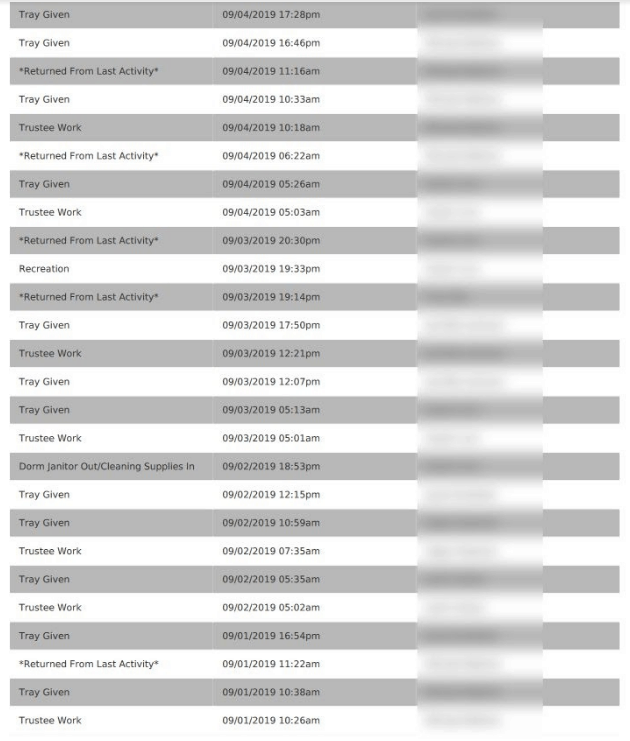
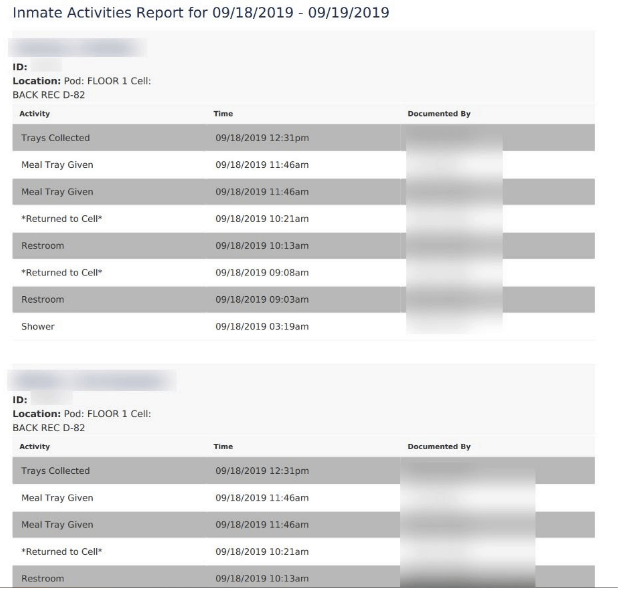
It’s important to note that a portion of the entries were of ‘dummy-data,’ but we were still able to find a sizable amount of actual user-end data as well.
Here’s the list of data that our research team found and was able to identify:
Data Impacted
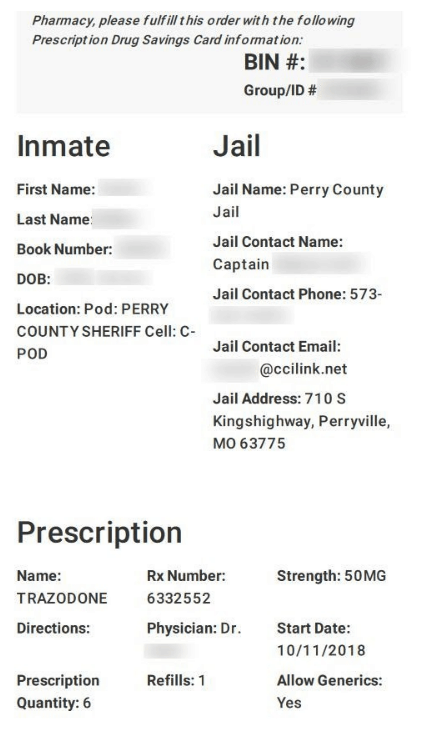
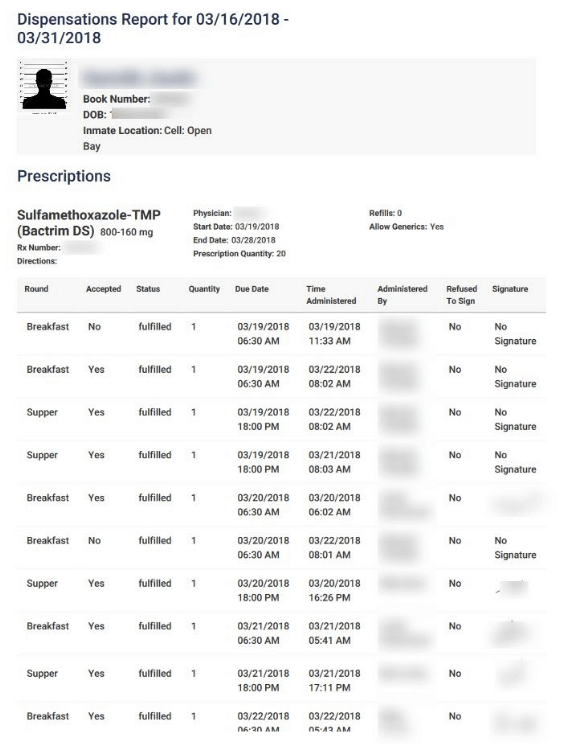
- Prescription records for inmates (PHI)
- Medicine name
- Dosage amount
- Start and end date
- Prescription quantity & refills remaining
- Time/date administered
- Full name of correctional officer who administered (and, in some cases, their signature)
- If the inmate took the prescription or refused
- PII of inmates
- Full name
- Booking number
- Date of birth
- Cell location
- Mugshot
- Headcount report
- Date
- Name of inmate
- Inmate ID
- Inmate date of birth
- Inmate cell location (including ‘detox’ facilities)
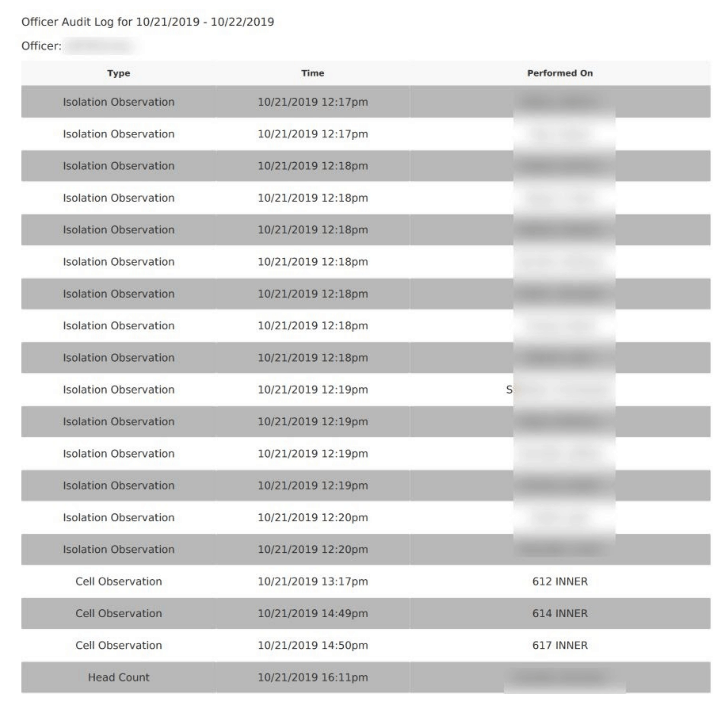
- Officer Audit Log
- Type of observation (eg: isolation, cell, head count)
- Date/time of observation
- Which inmate and/or cell observed
- Inmate activity (time meal served, time returned to cell, etc.)
- Inmate Mugshots
- Inmate Activities Report
- Restroom
- Shower
- Meals
- Return to cell
- Visits
- Recreation
- Packages
- Cleaning

States Affected
These are the states where we found detention centers included in the leak, but we did not open each file and it is possible that there are more correctional facilities in additional states that were impacted.
- Florida
- Kentucky
- Missouri
- Tennessee
- West Virginia
Data Breach Impact
This leak represents a potentially severe threat to those whose data has been exposed. It has many implications, all of which could very well ruin the lives of those involved. For many of the app’s customers, there is a current inmate roster on their Detention Center’s website. However, this roster does not include their medicine, their behavior, and their punishments - all of which were potentially made available in this data leak.
Identity Theft
Knowing the full name, birthdate, and, yes, even the incarceration record of an individual can provide criminals with enough information to steal that person’s identity. Considering that the person whose identity is stolen is in jail, cut off from normal access to a cellphone or their email, the damage could be even greater, as it will take longer to discover.
Identity theft does not always mean that the thief will claim that they are a particular individual in real life; it also allows them to engage in credit fraud, drain your bank account, and engage in scams to family, friends, and other associates of the identity theft victim.
Advice from the Experts
Jailcore could have easily avoided this leak if they had taken some basic security measures to protect the S3 Bucket. These include, but are not limited to:
- Secure your servers.
- Implement proper access rules.
- Never leave a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size. For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For Inmates and Correctional Officers Everywhere
You can contact Jailcore directly and find out how they are resolving this issue and plan on protecting your data better in the future. Whether you’re an inmate or correctional officer who may have your personal information on the Jailcore platform - and are concerned about how this breach might impact you or other data vulnerabilities in general, read our complete guide to online privacy to help better protect yourself online in the future. It shows you the many ways cyber criminals target internet users, and the steps you can take to stay safe. You can also use a VPN to hide some of the data collected by Jailcore. A VPN will mask your IP address and country of residence, giving you an added layer of protection even if your data is leaked.
For anyone working in the correctional industry, it is imperative that you take it upon yourself, going above and beyond in safeguarding your personally identifying information.
How and Why We Discovered the Breach
As part of an extensive web mapping operation, the breach in Jailcore's database was detected by the research team at vpnMentor. Our research experts apply port scanning to scrutinize specific IP blocks, testing uncovered gaps in systems for potential vulnerabilities. Each of these exposed gaps is closely inspected for any data leakage.
When they find a data breach, they use expert techniques to verify the database’s identity. We then alert the company to the breach. If possible, we will also alert those affected by the breach.
We were able to access Jailcore’s S3 bucket because it was completely unsecured and unencrypted. Using a web browser, the team could access all files hosted on the database.
The purpose of this web mapping project is to help make the internet safer for all users. As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security.
However, these ethics also mean we also carry a responsibility to the public. This is especially true when the companies data breach contains such a huge amount of private and sensitive information.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
In the past, we’ve discovered a breach in LightInTheBox that compromised the data of its customers. We also recently revealed that a company owned by major hotel chain AccorHotels exposed over 1TB of guests’ data. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
JailCore Comment: "1. We are a startup company that currently works with 6 jails totaling 1,200 inmates. Not the 36,000 mentioned in an earlier email.
2. Of those 6 jails, only 1 is using the application to track medication compliance is a 35 inmate jail and only 5 of those 35 inmates in that jail has a prescribed medication. Meaning all other reports with any mention of medication were all used for demonstration purposes only.
3. These are incarcerated individuals, not free citizens. Meaning, the same privacy laws that you and I enjoy, they do not.
I would implore you to get all facts straight before writing/publishing anything. You cannot look at this like an example of a private citizen getting certain private information hacked from the cloud. These are incarcerated individuals who are PROPERTY OF THE COUNTY (this is even printed on their uniforms)….they don’t enjoy our same liberties.
Having said all of this, the safety and security of all our data, whether at rest, in transit or in a report are extremely important to us. We have rectified the situation of the data held within a report. Below is a description of how our data at rest and in transit is secured:
Data Security is of utmost importance here at JailCore. We ensure all of our data is encrypted end to end as well as when it is at rest. Here are a few things we use to ensure the security of our client’s data:
SSL
We use a SHA-256 SSL Certificate to protect all data while in transit to our server. That means all the data being sent to our servers is encrypted while in transit and if intercepted by a hacker they would only see a garbled mess. The digital security industry now recommends SHA-256 as the standard signature hash algorithm for SSL certificates. The signature hash algorithm generates a digital fingerprint - also known as a "hash", "digest", or "checksum" - of information transferred during an SSL session.
This fingerprint verifies that the information was not tampered with or corrupted between the server and client.
The data we request from a facilities JMS is also encrypted using SSL even though we do not ask for any information from a JMS that isn't already public information.
Google Cloud SQL
All of our data is stored in the Google Cloud Platform which uses several layers of encryption to protect customer data at rest. Data for storage is split into chunks, and each chunk is encrypted with a unique data encryption key. These data encryption keys
are stored with the data, encrypted with key encryption keys that are exclusively stored and used inside Google's central Key Management Service. The data is encrypted when stored in database tables, temporary files, and backups. Data stored in Google
Cloud Platform is encrypted at the storage level using either AES256 or AES128."



Please, comment on how to improve this article. Your feedback matters!