Report: French Postal Service App Exposes Small Business Owners in Data Leak
Led by Noam Rotem and Ran Locar, vpnMentor's research team discovered a breach on a database belonging to Genius, an Android app built by French postal service La Poste. Genius is an app-based cash register that integrates many different processes to help small shop owners. The database in question is mostly related to payments made via the app. With over 23 million records, this is a huge breach in data security and makes Genius users across France vulnerable. If malicious hackers had discovered this database, the consequences could be devastating for those exposed.
La Poste Company Profile
La Poste is the main postal service in France, majority-owned by the French government, and also operating in overseas territories traditionally linked with the country. It's the second-largest employer in France, and like many postal services around the world, has expanded beyond mail delivery. Their operations include insurance, banking, webmail hosting, and many more services for private citizens. The company also offers services for small-to-medium businesses (SMBs) in France. These include Genius, the cash register app. Aside from processing payments from customers, Genius assists SMBs with inventory management, data reporting and analytics, accounting, and many more key processes. Genius is billed to SMBs as "A modular solution that adapts to all your needs... And your budget!"
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what's at stake or who's leaking the data. Understanding a breach and what's at stake takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness. Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and true. In this case, upon identifying La Poste as the database's owner, we reached out to them with our findings. While we waited for a reply from La Poste, on November 18th we also reached out to their hosting company and The Commission nationale de l'informatique et des libertés (CNIL), France's independent regulatory body for data privacy. The database was closed almost three weeks after our first contact with the French CNIL.
- Date discovered: 11/11
- Date vendors contacted: 13/11
- Date of contact with CNIL: 18/11
- Date of action: Approx. 8/12
Example of Entries in the Database
According to the Terms of Service for Genius, La Poste is committed to: "implement[ing] the necessary measures to protect Personal Data against accidental or unlawful destruction, accidental loss, alteration, disclosure or unauthorized access;" "notify[ing] the Customer, within 48 hours from the time it becomes aware of it, any violation of Personal Data." (Translated from French) However, based on our research, the exposed database had not been sufficiently protected. It was leaking sensitive information that would be a goldmine for criminals and malicious hackers. Our team found over 15GB of sensitive information, with 23 million records originating from SMBs across France, Belgium, Switzerland, Italy, Spain, and maybe more. Entries into the database were linked to payments made by customers via Genius, as well as other functions carried out on the app. Each entry contained different forms of data, depending on the action being taken by the user. These included Personally Identifiable Information (PII) data of both the Genius users and their customers, along with sensitive information about the businesses’ finances and operations. Examples of the user data viewable of the database included:
- Full names, Email addresses, phone numbers, and Dates Of Birth, of people using the app
- City of business residence and zip codes of users
- Information about products sold (label, price, barcode, etc) and transactions made via Genius
- Information about sellers (name, email, phone number)
- Bills sent to customers and suppliers
- Business' Stock inventory
- Both the test and genuine values of products on Genius
- Email addresses of customers who received a bill via Genius
- Total values of the business' transactions made via Genius
- Business' Siret number (for French business registration)
- Much more
Below is an example of a Genius user doing their end of day reconciliation on the app (currency values are listed as totals in cents. For example, "10150" = €101.50). This is just one example of how a business’s sensitive data and financial records were being leaked: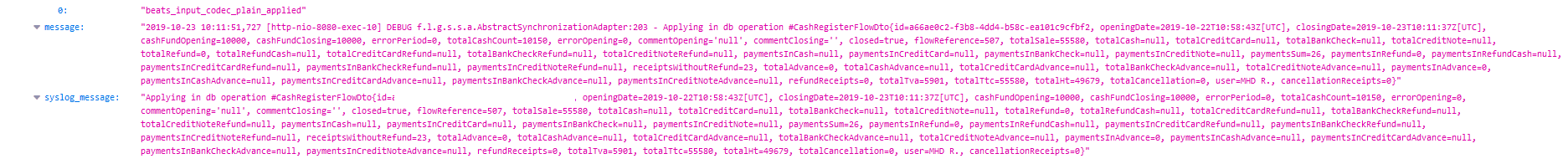 In the following example, data belonging to a business and one of its employees is exposed while performing another action on the Genius app:
In the following example, data belonging to a business and one of its employees is exposed while performing another action on the Genius app:  In this final example, the PII of a customer is exposed:
In this final example, the PII of a customer is exposed: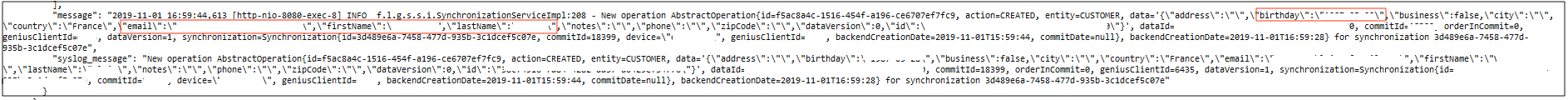 Genius is used by SMBs across France, as well as other European countries including France, Belgium, Switzerland, Italy, and Spain. As such, the database contained records from Genius' user base in many different industries across each of these countries, and many more. Some examples of the businesses exposed include:
Genius is used by SMBs across France, as well as other European countries including France, Belgium, Switzerland, Italy, and Spain. As such, the database contained records from Genius' user base in many different industries across each of these countries, and many more. Some examples of the businesses exposed include:
- Nilaï - A jewelry store in Paris
- By164 - A jewelry store in Paris
- Lovat&Green - A unisex fashion retailer based in Bilbao, Spain
- Manta - A French gift store with shipping to numerous European countries
- Louisette - A French family gift store
- MHD Restauration - A small, independent restaurant
*Note: Lousiette and MHD were users of Genius cited on its website, offering positive testimonials for the service. Aside from exposing client users of their app, the database also inadvertently made employees of La Poste vulnerable. During their research, our team also viewed PII data of La Poste employees, such as their names, email addresses, and phone numbers, alongside 'test values' of products on the app. This was most likely due to the affected employees testing the app in-house.
Data Breach Impact
This data leak is a serious breach of data security protocols for La Poste and the developers of the Genius app. While La Poste may be commended for their transparency regarding the protection of their users' data, our team's discovery indicates that they did not take sufficient steps to protect said data. Had criminals or malicious hackers accessed this data, there would be serious implications for the privacy and security of all those affected.
For La Poste and Genius
A leak of this nature will raise questions over La Poste's overall data security practices - not just in the Genius app, but across their wider operations and network of subsidiary businesses. While we're working to resolve this leak, future customers to Genius may be reluctant to adopt the app into their business operations. La Poste may struggle to maintain the trust of SMBs after our discovery, along with their reputation in France's business communities. As France's largest postal service, with customers across Europe, La Poste is within the jurisdiction of the European Union and GDPR. La Poste even acknowledges GDPR, though not by name, in their Terms of Service. By not protecting the personal data of Genius users and their customers, La Poste may be liable for legal action or fines by the appropriate regulatory bodies.
For Genius Users
The confidential information revealed on this database places Genius users and their respective businesses at risk of numerous forms of attacks and fraud strategies. For instance, with the exposed personal, business, and financial data, wrongdoers could orchestrate convincing phishing campaigns. Such a campaign entails fabricating deceptive emails that mimic genuine businesses or governmental entities, with the intent to deceive recipients into carrying out any of the following actions:
- Reveal additional information like passwords and usernames to private online accounts and email hosting
- Give access to financial accounts like credit cards or online banking
- Click a link that will embed malicious software, such as malware, ransomware, spyware, and viruses
If a hacker viewing the exposed data was able to calculate the average values of transactions on Genius, they could devise methods to steal money in small, incremental amounts from a user - or entire lump sums. Recovering these stolen funds could be a long, difficult, and unsuccessful process - beyond the abilities of many SMB owners. The leak also created a potentially more traumatic physical danger for the shop owners. End of day reconciliations done by users via Genius revealed the amounts of physical cash on their premises close of business. This gives potential thieves an insight into the best time to burgle or break into an exposed store and steal the cash directly from the premises. As with all currency totals listed, in the following code snippet, the value "10150" is equal to 101.50 in the user's currency.
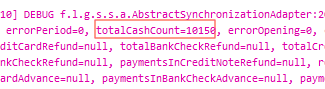
Furthermore, as the leaked data also exposed customers of these businesses, their owners could face a loss of customers who no longer trust the businesses using Genius to keep their data safe. Lastly, Genius users could be vulnerable to dishonest actions by competitors. With access to sales and pricing data analytics, a competitor could undermine the user with competing offers. This may further drive customers away from an exposed Genus user.
Advice from the Experts
La Poste and the developers of Genius could have easily avoided this leak if they had taken some basic security measures to protect the database. These include, but are not limited to:
- Secure your servers.
- Implement proper access rules.
- Never leave a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size. For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For Genius Users
As per their terms of service, La Poste is obligated to notify users of "any violation of Personal Data" within 48 hours: "In this context, [we] will communicate to the Customer all the information [we have] regarding the conditions surrounding this violation of Personal Data." Hopefully, they will fulfill this obligation and inform any party affected by the leak. If you're a customer of La Poste Genius and concerned about how this breach might impact you, La Poste also offers directions for raising your concerns with outside parties: "As part of La Poste's personal data protection policy, you can contact the Data Protection Officer, CP C703, 9 Rue Colonel Pierre Avia, 75015 PARIS. In case of difficulty in the management of your personal data, you can file a complaint with the CNIL."
For SMB Owners
If you own a SMB and are concerned about how data vulnerabilities and theft could impact your business and customers, read our complete guide to online privacy for SMBs. It shows you the many ways cybercriminals target small businesses, and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the breach in La Poste’s databases as part of a huge web mapping project. Our researchers use port scanning to examine particular IP blocks and test open holes in systems for weaknesses. They examine each hole for data being leaked. When they find a data breach, they use expert techniques to verify the database's identity, as well as its owner. We then alert the company to the breach. If possible, we will also alert any other parties affected by the breach. Our team was able to access this database because it was completely unsecured and unencrypted. La Poste uses an Elasticsearch database, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing schemata. The purpose of this web mapping project is to help make the internet safer for all users. As ethical hackers, we're obliged to inform a company when we discover flaws in their online security. This is especially true when the companies data breach contains such private information. These ethics also mean we carry a responsibility to the public. Genius users must be aware of how a data leak impacts them also.
About Us and Previous Reports
vpnMentor is the world's largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data. In the past, we've discovered a huge breach exposing the data of customers to a French hotel group owned by AccorHotels. We also revealed a data leak by French flight booking platform Option Way, compromising the privacy of their customers. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
[Publication date: 11.12.2019]




Please, comment on how to improve this article. Your feedback matters!