A Cybersecurity Guide for Small to Medium Businesses in 2025
Cybersecurity threats are growing every day, and not a day passes when there isn’t a story about some kind of breach or data theft in the news. Those of us who own or manage small and medium businesses know that cybersecurity is crucial and that we should be paying close attention to these issues. The problem comes in figuring out where to start.
Cybersecurity can feel overwhelming and terribly complicated. Not every manager or small business owner has a technical background, so wading through all of the technical jargon and conflicting information can put off even the most careful and security-oriented among us.
We’ve put together this guide just for this type of person. If you’re a busy manager, and your plate is full with the actual day-to-day running of your business, you don’t have time to become an advanced technical expert in all aspects of cybersecurity. But, if you read through this guide, and work with your team (including the people who you employ or outsource to set up your computer hardware, software, and networks) to implement the security measures we have outlined, you will sleep better at night. Securing your business is really not as difficult as many experts make it out to be. With a bit of patience and guidance, you can implement world-class security measures for even the smallest of companies.
1. Determine your vulnerabilities

The first step in protecting yourself from cybersecurity threats is to determine your vulnerabilities. If you don’t know what your weaknesses are, how will you be able to fix them? If you don’t know what kind of data your company stores, how will you protect it?
Start by identifying the “crown jewels” of your company data. What are the most crucial pieces of data that your company holds?
These could be anything, from your intellectual property to customer and client details, inventory, financial information, etc. Where do you store all of this data? Once you have the answers to these questions, you can start thinking about the risks that your data is open to.
Carefully map all of the processes that you and your staff members move through to collect, store, and dispose of this data. Think about all the transit points along the way through which this data could leak out or get stolen. And consider the consequences of a cybersecurity breach for you, your employees, and your customer, client, and partner relationships. After doing so, you can start to put precautions in place.
2. Protect your computers and devices
Your computers and other devices are the portals through which just about all of the work that makes your business tick are done. But, because these devices are connected to the internet and to a local network, they are vulnerable to attack. These are our guidelines for boosting your security across the spectrum of your company’s computer systems.
A. Update your software
The very first step (and probably the easiest one) to ensure that your systems are not vulnerable to attack is to make sure that you always use the most up-to-date version of the software that your business relies on. Criminal hackers spend their time searching for bugs in popular software, exploiting loopholes to get into the system. They do it for all manner of reasons: to make money, to make a political statement, or simply because they can. This kind of intrusion can cause untold damage to your business. Hackers could steal your customer’s credit card numbers from your website, or steal passwords from your computer. Your business could be in real trouble if this happens.
Microsoft and other software companies are always on the lookout for vulnerabilities in their software. When they find one, they release an update for users to download. Making sure you download these updates as soon as they are released is so easy, one wonders why so many businesses are not careful about this.
In 2017, a global ransomware attack called “WannaCry” hit thousands of victims, including huge organizations like FedEx and the UK’s National Health Service (more on ransomware below). Before the attack, Microsoft released a patch, a software update that fixes the problem, but many system administrators failed to install it, leading to the massive attack. Luckily the attack was stopped, but this is not always the case. The easiest way to avoid becoming the hackers’ next victim is to conscientiously update your software.
- If your system is managed by a system administrator, make sure they are aware of software updates as soon as they come out and are on top of updating your system.
- If you have a small business where you manage your computers yourself, simply enable Windows update. Once you update your system, reboot your computers.
B. Protect against viruses
Viruses are malicious programs that infect your computer without any warning. Viruses can do many things, but, usually, they gain access to your files and delete or change them. Viruses spread quickly by replicating and sending themselves to the people in your contacts list. If one computer in your network gets a virus, it can quickly spread across your company, causing significant data loss. If you communicate with your clients and customers via email (which just about all of us do), you run the risk of infecting them as well.
Malware and ransomware are the two most dangerous types of virus in circulation today. There are a few differences between malware and ransomware. Malware stands for “malicious software”. It works by tricking the victim into downloading certain software, thereby gaining access to that victim’s computer. It can trace what you access on your computer, steal sensitive information, or spread spam via email.
Ransomware is a specific type of malware. It locks your computer and blocks you from accessing your important files until you pay the ransom. Ransomware works by encrypting your files using a private key accessible only to its creators. The WannaCry attack mentioned above was a type of ransomware. Paying the ransom doesn’t necessarily help: there is no guarantee that the hackers will actually unlock your files.
There are a number of basic steps you can take to avoid infecting your computer with viruses. First, install antivirus software on all office computers. Antivirus software scans incoming email messages, as well as files currently on your computer, and then deletes or quarantines any viruses it finds. Hackers are always putting out new viruses, so you should update your antivirus software regularly. The best software providers will include a feature that commands your computer to download the updates automatically. You should make sure your staff know not to open suspicious files, and to delete any email attachments from a source that they do not recognize as trustworthy.
Using a VPN to access the internet can also give you an extra security boost. Because VPNs allow you to access the internet anonymously, and because they encrypt all of your data, they make tracking your computer very difficult for hackers. Good VPN providers send you a security warning when you try to access suspicious URLs.
If you’re already the victim of a ransomware attack, it’s not too late. This step-by-step guide will help you beat an attack.
-
- Update your antivirus software, or if you don’t have any, install one now.
- Educate your staff not to open suspicious attachments.
- Browse the internet using a VPN.
- Read up on how to foil a ransomware attack in case you need to refer to it.
C. Set up a firewall
Like most businesses today, all of the devices in your office are probably connected to a broadband internet connection that is always on. If this is the case, then there is a strong likelihood that criminal hackers have probed your computer network at least once. Hackers do this randomly, but when they find a valid computer address, they will exploit any and all vulnerabilities to get access to your network and to individual computers on that network.
Installing a firewall is the best way to prevent this kind of attack from happening. Firewalls work by separating different parts of the network from each other, allowing only authorized traffic to pass through the protected part of the network. If you run a small business, your firewall will fence off your local private network from the wider Internet. A good firewall examines each packet of data that flows into your network to make sure it is legitimate and filters out packets that it deems suspicious. In order to prevent hackers from targeting individual computers on your network, the firewall obscures the individual identity of each computer.
Installing a firewall is complicated and should only be done by a trained professional. That makes your job easy: all you have to do is speak to your system administrator, and make sure your network is protected.
- Call your system administrator, ask if your local network has a firewall, and if not, ask him or her to install one.
D. Special precautions for laptops and other mobile devices
Because they are portable and can, therefore, leave the office, laptops are at particular risk for security breaches. They are a target for thieves because they are easy to steal and then sell. Employees can also be careless with their work laptops since most companies will simply replace the machine if it is lost or stolen. However, replacing a laptop is a significant financial outlay, especially for a small business. But this isn’t even the biggest problem. Staff laptops, especially those of more senior staff, more than likely contain sensitive information that could be damaging to your business if it falls into the wrong hands.
There are a few precautions you and your staff should take to both prevent laptop theft, and to mitigate the most serious consequences if a company laptop is stolen. First, when an employee uses a laptop in a public area, or even at a meeting or conference, he or she should always make sure to keep the laptop within sight. Laptops should be kept in carry-on luggage, and not left in baggage storage areas in hotels or airports.
Hackers can also easily access data on a laptop or mobile device if the connection is not on a secure network. There are a number of measures we recommend to protect your data, like using a strong password, backing up all the work you’ve done on your laptop before a trip, and encrypting your data. These guidelines are especially pertinent in regard to laptops. We explore them further in section 3, “Protect your data”.
It pays to plan ahead for the eventuality that one of your company devices will get stolen. If you use a cloud solution for any of your software needs, look into your provider’s mobile device management features. The major cloud computing providers allow you to wipe an account from any device that goes missing.
All of this advice applies equally to company smartphones. There are a number of steps you can take to secure company smartphones, and this guide specifically for iPhones will take you through this process. There are a number of security apps we recommend using, as well as ways to change your phone’s settings to make it more secure.
One of the best ways to protect devices – whether laptops, smartphones, Amazon’s Alexa device, or even your office PS4 (if you’re the fun type of office that has a gaming device!) – is by installing a VPN to encrypt all of the data moving through these devices. You don’t necessarily need to install a VPN on each and every device; instead, you can install it directly on your office router. That way, all of the devices that use the office internet connection will be protected.
It’s also important to formulate a policy on which devices you allow staff members to bring with them to work. Many companies encourage their workers to bring their own laptops and other devices to the office because doing so is far cheaper than providing each employee with company equipment. We recommend you require all personal devices that are used for any work purpose to install antivirus software and receive regular updates.

- Update all company laptops and smartphones with the latest anti-virus software and operating system updates.
- Formulate a policy for which devices can be used at work and the security features they must contain.
- Contact any cloud computing providers and ask them how they can help you with mobile device management.
3. Protect your data
No matter what type of business you run, your data is at the very core of what you do. Without your customer contact information, your inventory, your proprietary data, and everything in between, you simply would not be able to function as a business. Your data can get lost in all manner of ways. Your hardware can get damaged or break down, hackers can get into your system and take it, or you could be hit by a natural disaster. Your goal, therefore, should be to insure yourself against data loss by taking precautions against its worst effects.
A. Implement a procedure to back up critical data
There are two different types of backups. When you do a full backup, you make a copy of the entirety of the data you selected and put it on another device or transfer it to a different medium. With an incremental backup, by contrast, you simply add the data that has been created since the last time you backed up your system.
The easiest and most efficient method is to combine the two. Perform a full backup periodically and an incremental backup every day in between. Or, you can perform a full backup every night after work hours. It’s crucial to actually test that your backups are working: losing all of your data and finding that your backup systems do not work would be a tragedy. You can do this by restoring a test portion of your data to a new location. This will reassure you that your backup systems are working and help you identify any issues in the backup process.
There are many different ways to backup your data. You can put it on a physical device, like a USB stick or a second hard drive, or place it in a shared folder on your network. You can also keep backups at a secure offsite location. However, backing up your data to one specific physical location won’t help you if natural disaster or theft strikes. We strongly recommend that all companies invest in a cloud-based backup system – see the next section for further details.
- Evaluate your company’s data retention policy. Is all your crucial data backed up? If so, where do you keep that data?
- Work with your system administrator or IT staff to implement a weekly backup plan.
- Test your backup system to ensure that it’s working.
B. Encrypt sensitive company data kept in the cloud
Today, many companies keep most – if not all – of their data on a cloud-based platform. This could be a cloud-based storage system, like Dropbox, or a SaaS (software as a service) platform like Salesforce. Because we refer to these systems as the “cloud”, we tend to imagine that our data is kept safe in some abstract, virtual space. In reality, all it means is that your data is not stored on your hard drive or your local network, but rather on remote computing facilities provided by your cloud-based service. It is therefore essential to carefully look into what kinds of security measures your cloud provider has put in place and whether your data is protected at an appropriate level.
There are a number of approaches you can take to make sure your files in the cloud are secure. The simplest and most secure approach is to encrypt your files manually, and there are a number of programs that can help you do so. This means you don’t have to rely on your cloud provider’s security, and you can use it without worry. Just make sure not to upload your encryption keys.
That being said, you should investigate your cloud storage options carefully. There are more and more providers on the market, and some of the smaller and less-known ones actually have more robust security features than the big names. Some of these services will automatically encrypt your files before they are uploaded to the cloud.
Another option entirely is to use BitTorrent Sync, which is a totally free service. BitTorrent Sync was designed as a replacement for cloud-based systems but does not actually store files in the cloud. Instead, it enables you to collaborate on documents through a peer-to-peer (P2P) file-sharing platform. These services tend to use the highest-grade AES-256 encryption and enable two-factor authentication, which adds an extra layer of security.
This ultimate guide to online privacy explains it even more.
- Assess your important company data. How much of it is stored or backed up on a cloud platform, and is this platform secure?
- Research cloud platforms and look for a level of security that best meets your company’s needs
C. Protect your passwords

The most common way to authenticate the identity of who accesses your network or your important data is via a password. Unlike other high-tech authentication systems like smart cards and fingerprint or iris scans, passwords are useful because they do not cost anything and are easy to use. However, passwords are also open to attack. Hackers have developed sophisticated, automated tools that enable them to crack simple passwords in just a few minutes. They can also use various fraudulent methods to access your company passwords, like a phishing attack, in which they disguise themselves as an official entity (like Google) and trick people into providing their passwords.
Passwords can become ineffective for a variety of reasons. Often, we neglect to password-protect our sensitive documents, meaning anyone sitting at one of your office’s computers can gain access to that document. In order to avoid forgetting their passwords, many employees write them down in plain sight. And, most crucially, people tend to use weak passwords that are easy to remember, use the same password over and over again, and never change their passwords. All of these mistakes leave the door open for hackers.
These seven steps to creating a strong password will help prevent hack attacks:
- Create different passwords for different services
- Change your passwords regularly
- Choose a strong password
- Opt for two-step verification
- Disable autocomplete for usernames and passwords
- Use a password manager - an app or program that securely stores all of a user’s passwords
- Don’t send your password out via email or give it out over the phone
Creating a stronger password isn’t that difficult. Use a password tool, like this one, which tells you how good your password is and how long it would take for a hacker to crack it. You can also use a secure random password generator that will create a completely randomized password.
Educating your staff about the importance of strong passwords is crucial if you want to make passwords a key tool in your cybersecurity arsenal, rather than a backdoor that hackers can walk through.
- Have all employees check their passwords with a Password Meter tool. If their passwords are crackable within a few minutes or even hours, require them to change their password to something more secure.
- Enable two-step verification for all employee accounts wherever possible.
D. Establish permissions
If you think about who has access to sensitive information in your company, the answer is probably too many people. Take steps to restrict access to your system. Only those staff members who are authorized to manage your system and to install software should be given administrator accounts.
Companies can also be lax by allowing multiple staff members to share one login and password. This makes it impossible to determine how or when a breach in your system occurred. Give each user his or her own account, enabled with permissions specific to his or her job. If you’re using Windows, you can assign users different permission levels based on their roles within your company. If a staff member is absent for a long period, or has left your company, revoke their access and permissions as soon as possible.
- Work with your system administrator to assess the level of access each staff member has.
- Change your permissions so that each staff member only has access to the software and settings required for his or her job.
E. Protect your wireless networks
Another way hackers can get into your system is via your office’s wireless internet network. Because Wi-Fi networks use a radio link rather than cables to connect computers to the internet, all it takes is moving within radio range of your network plus a few free software tools to break in. Intruders who can gain access to your network can steal your files and damage your systems. While Wi-Fi devices are enabled with security features to prevent this from happening, most have these features switched off by default in order to make the setup process easier.
If you’re using a Wi-Fi network, make sure you have these security features switched on. You can also restrict wireless access to office hours so that hackers can’t get into your system overnight. And you can prevent passers-by from accessing your connection by restricting Wi-Fi access to specific computers by setting access points.
- Ask your IT person to make sure that your Wi-Fi has the highest-level security features switched on and that WiFi access is restricted to office hours.
F. Browse the internet safely
As you and your staff members browse the internet, your activities are being tracked in a multiplicity of small, subtle, and unnoticeable ways. These activities can then be aggregated by third-party agents without your consent. Your employees could inadvertently browse to dangerous websites that steal your company’s data. And your personal or business information could be compromised if it is entered into websites over a non-encrypted connection.
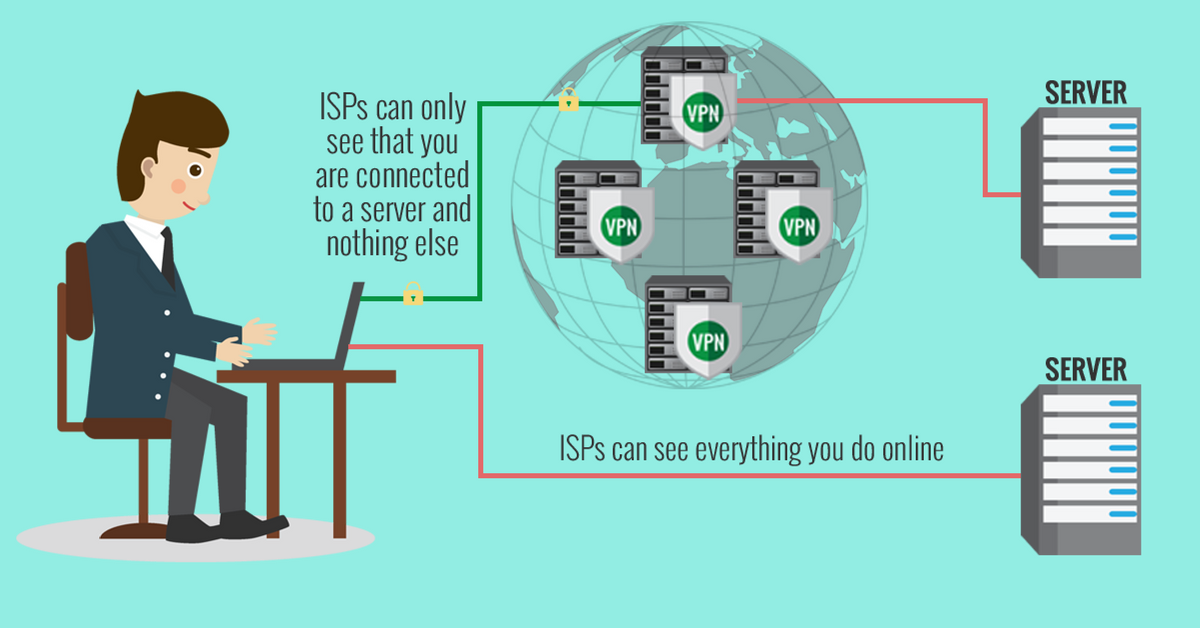
The best way to encrypt your connection and ensure both your businesses’ privacy and the personal privacy of your individual employees is to install a VPN. A VPN, or virtual private network, masks your company’s IP address and encrypts your browsing data. They also anonymize your browsing, which could be important if your business frequently does research on your competitors, or if your aggregated browsing history could reveal proprietary information to your competitors.
The downside to using a VPN is that trustworthy and feature-rich VPN services cost money for a monthly subscription. Many individuals and companies have opted to use a free web proxy as an alternative. The problem is, we don’t know who exactly is operating the proxies available for free online; they could very well be hackers themselves, or they could be used for intelligence gathering by various public or private entities. While a proxy hides your identity and activity from the sites you visit, it can potentially see everything you are doing online. That’s one of the reasons that we recommend investing in a VPN rather than a proxy, for truly secure browsing.
You can also bolster your security by adding a number of security features to your browser. Because the Firefox browser is open-source, a robust group of security add-ons have been created for it over time. These include multipurpose ad blockers, encryption extensions, browser data protection, cookie and cache managers, and more.
- Consider subscribing to a VPN service that offers business solutions.
- Start using the Firefox browser with security add-ons as appropriate to your company.
G. Protect sensitive data created by remote workers and workers on the go
Many small businesses employ remote workers to perform a wide range of tasks. With the internet, working with others across the world is easy to do. Hiring remote workers comes with numerous benefits: it means you don’t have to hire an employee to take care of one specific technical or monotonous task, and it also means that you open the pool of qualified candidates. However, remote work comes with some cybersecurity pitfalls. You may have implemented all of the protections that we have outlined above, but many of them are rendered ineffective if your sensitive data is accessed by remote workers operating outside of your protected company network, especially if they are using a public WiFi hotspot.
As outlined in section 2.D., a mobile device management solution could assist in managing your remote staff, including those traveling for work. Crucially, it is vital to make sure that if your remote employees need to access confidential company information, they do so through your secure company network, maintaining a safe connection.
Windows offers a remote desktop connection feature, but this in itself is not enough to secure your data. If you rely on remote workers, and if you cannot afford for the data to be leaked or stolen, it is wise to implement a specialized VPN which allows the remote users to first get into the office network, after which they can connect to their machines using the remote desktop connection feature. This can get complicated, so talk to your IT person to see if he or she can arrange to configure a VPN especially for your office network.
- Assess your remote worker policy. How do your remote workers access company data, and is that company data sensitive?
- Speak to your IT administrator to set up a safe and secure way for remote workers to connect to your office’s private network.
H. Protect your customers’ data
It’s one thing if your sensitive company data is lost or stolen. It’s another matter entirely if your clients’ or customers’ data is compromised. There are serious legal consequences involved, so it pays to treat your customer’s sensitive information with the utmost care.
Typically, customer data is in transit through multiple points. If you run an e-commerce site or otherwise process payments through your website, the first transit of sensitive information (including names and credit card details) is from the customer’s web browser to the e-commerce web server. The best way to protect this data is to make sure that your website uses an SSL certificate and the HTTPS protocol, at the very least on pages that collect sensitive data. This will ensure that your client’s data is encrypted as it moves from their server to yours. If you are transferring client data within the company, you should apply all of the security features we have described above, especially those relating to cloud storage and transfer.
- Speak to your e-commerce provider or in-house developers to make sure that credit card and other sensitive information is collected in the safest way possible.
4. Instill a cybersecurity culture in your workplace

The measures that we have outlined in this guide are comprehensive, and if you follow all of the guidelines that are relevant to your business, you will significantly lower your risk of a cyberattack. That is, if your business is just you.
All it takes is one employee to send client data on an unsecured connection or click on an unsafe link and download malware, causing all of your security systems and all of your well-meaning efforts to come crashing down. That’s why the single most important measure you can take is to educate your staff on the importance of cybersecurity.
On the flipside, if you instill a cybersecurity culture in your workplace, if you explain your cybersecurity policies and why they are there, and if you train staff to manage company hardware and data safely, your employees will become your first, and most effective, line of defense against cyberattacks.
The best way to get your employees’ buy-in on your cybersecurity plan is to design it collaboratively with them. Involving them in the plan will increase their motivation in implementing it. Your staff members are also the experts in your business, in its weaknesses as well as its strengths. They are the ones who work with your sensitive company data all day long, so they are best placed to tell you where vulnerabilities lie and which systems need to be strengthened or improved.
Start holding regular training sessions with your staff on cybersecurity issues. This is the place to methodically work through important security techniques, like the ones we have outlined above. Ensure that their passwords and permissions are up to date and that they use passwords that are impossible to crack. Make sure that they do not leave passwords lying around on physical sticky notes or sitting on their desktop. Show them how to avoid getting tricked by phishing attacks via email and the risks of malware from dangerous websites. Teach your employees the many and nefarious ways in which hackers may try to get information out of them. Encourage them not to discuss any confidential company information in public – you never know who you could talk to, and who could be listening. Make these guidelines easy to understand and follow. We’ve created a printout that includes simple steps your employees can take to stay secure. You can hang this on the office bulletin board or fridge, or customize it to suit your specific needs.
Enshrine cybersecurity principles in a written policy, and have your employees sign a copy of this policy, making sure that they understand how serious an issue cybersecurity is. You can even have cybersecurity elements written into staff contracts.
Above all, remember that cybersecurity threats are constantly morphing and changing. Hackers are constantly coming up with more creative and more sophisticated ways of breaking into computer systems and stealing your data. Keep up to date with developments in cybersecurity, and make sure to educate your staff on these developments, too.
- Hang our cybersecurity guideline printout on your office bulletin board, and send out this email template to all employees.
- Start to formulate a cybersecurity training program for all of your employees.
Feel free to share and copy this post or parts of it to your site, blog, or social networks. All we ask is that you attribute it to us. We want to keep businesses safe, and your help to spread the word is important.
Click here to share it on Facebook or Twitter.




Please, comment on how to improve this article. Your feedback matters!