Report: Over 63 Million US Citizens Exposed in Massive Data Leak
Led by Ran Locar and Noam Rotem, vpnMentor’s research team discovered that B2B marketing company OneMoreLead was leaking the private data of up to 126 million American people.
OneMoreLead was storing all this information on an unsecured database, which the company had left completely open. As a result, the names, email addresses, and workplace information were exposed to anyone with a web browser.
Had malicious hackers discovered this database, it would have been a goldmine for various criminal activities, from financial fraud and identity theft, to large-scale phishing attacks targeting US companies and government institutions.
The origins of this data remain a mystery. It’s unlikely that OneMoreLead invested the necessary resources to manually collect data from 126 million US citizens, unless they started doing so long before launching the company. But regardless of how OneMoreLead obtained these records, it’s still responsible for any damage caused by not keeping them protected.
Data Breach Summary
| Company | OneMoreLead |
|---|---|
| Industry | B2B Sales and Marketing SAAS |
| Size of data in gigabytes | 34 GB |
| Suspected no. of records | 126 million |
| No. of people exposed | 63-126 million (depending on duplicates) |
| Date range/timeline | The data was uploaded on 10th April 2021. The date of its origin before this is unknown. |
| Geographical scope | USA |
| Types of data exposed | PII data |
| Potential impact | Fraud; identity theft; phishing |
| Data storage format | ElasticSearch |
Company Profile
OneMoreLead offers corporate clients access to over 40 million business leads for their company, along with a host of related services and software tools.
It appears to be a new and small company, which started in April 2020. There’s very little information about OneMoreLead online, and its website wasn’t finished when we discovered the database.
For example, the ‘clients’ section was still blank, and the signup button didn’t work.
 A screenshot from OneMoreLead’s website
A screenshot from OneMoreLead’s website
Timeline of Discovery and Owner Reaction
- Date discovered: 16th April 2021
- Date vendors contacted: 20th April 2021
- Date of Contact with AWS: 20th April 2021
- Date of Response: 20th April 2021
- Date of Action: 21st April 2021
Sometimes, the extent of a data breach and the data’s owner are obvious, and the issue is quickly resolved. But rare are these times. Instead, we usually need days of investigation before understanding what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Furthermore, some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, vpnMentor’s cybersecurity team discovered the database during a routine research project. We quickly identified OneMoreLead as the database’s owner. However, the origins of the data, or how it ended up in OneMoreLeads’ hands, remain unknown.
The company is new, with no known clients and an unfinished website. So, it’s unlikely they collected data from 126 million people since opening in 2020 - unless the people behind OneMoreLead were working on a similar business previously.
Furthermore, the exposed data bears an uncanny resemblance to a leak originally connected to the German B2B marketing company Leadhunter in 2020. (Leadhunter denied responsibility for the leak at the time, and researchers couldn’t confirm a link.)
Based on our research, and the similarities between the two companies and data breaches, we suspect that one of the following scenarios took place:
- Both companies sourced their data from the same entity - possibly another business that sells leads to marketing companies. But since it's been over a year, OneMoreLead added more leads and removed some existing ones (which would explain the differences between both databases).
- One of the two companies (OneMoreLead and Leadhunter) sold the data to the other, but it would be difficult to know which one was the seller and vice versa.
- The people behind OneMoreLead discovered the Leadhunter leak, kept it silent, and downloaded the data (or part of it) to create their own company before the leak was secured in 2020.
- OneMoreLead was behind the original Leadhunter leak and has decided to monetize the data as part of a new company.
Ultimately, we may never know how OneMoreLead amassed such a vast amount of data before exposing it to the world. However, the company has a responsibility to close the vulnerability and ensure it’s not leaked again.
With this in mind, we contacted a person that was involved in OneMoreLead and presented our findings. We also reached out to AWS, as the database was stored on its cloud platform. They replied the same day, and the server was secured the following day.
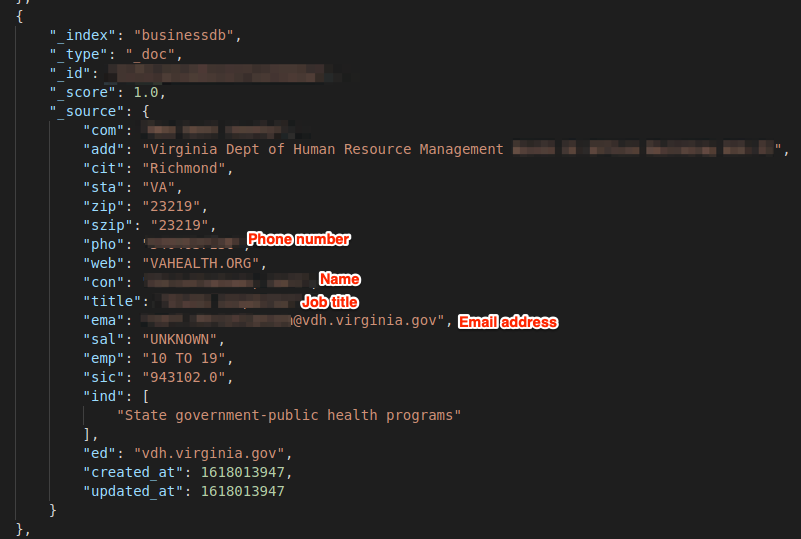
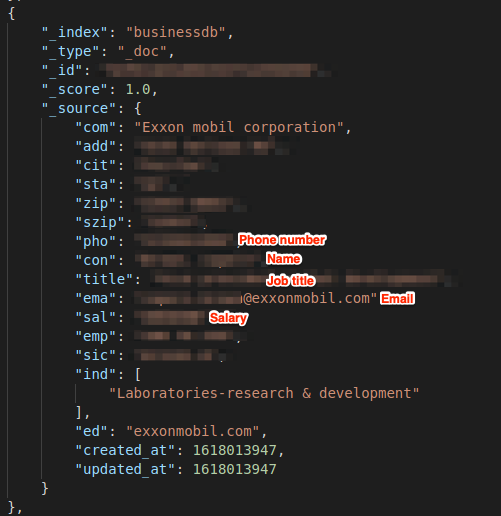
Example of Entries in the Database
OneMoreLead was using the exposed database to store the personal and professional information belonging to at least 63 million people. This information would most likely be offered to clients or customers signing up for its B2B marketing service.
Based on our investigation, it appears the company uploaded the data on 10th April 2021, which appeared on Shodan, a search engine for devices connected to the internet, a day later.
The database contained two distinct types of ‘leads’:
- An index named "personaldb" contained records that consisted of basic Personally Identifiable Information data for each person listed. (63.6m)
- An index named "businessdb" contained similar data and information about their job and employer. (63.7m)

The private personal user data we viewed across the two indexes of leads included:
- Full name
- Job title
- Personal email address
- Home address and phone number
- Home device IP address
- Work address and phone number
- Work email address
- Employer
Given the volume of data, and the unclear origins, there may be some inaccuracies. For example, a person may no longer work at a business listed in the indexes. However, this does not take away from the severity of the leak. Hackers could still use the data in a wide range of criminal activities.
It may also be possible to cross-reference entries with an individual’s online presence, such as a LinkedIn profile.
The following screenshots show the various forms of data exposed in the leak:
The database also contained another much smaller index with just 9 records.
We believe these records were access credentials for OneMoreLead’s backend, most likely belonging to OneMoreLead's customers. However, as the company doesn’t publicly list its clients or customers, and testing the login credentials would have breached our ethics, we can’t confirm this.
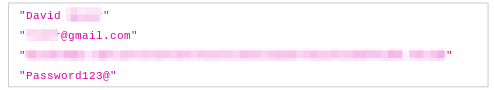
We also suspect that the customers exposed belong to business entities connected to OneMoreLead somehow, and they’re all managed by the same group of people.
Data Breach Impact
By not securing this database, OneMoreLead exposed at least 63 million people to fraud, identity theft, and much worse.
The database contained detailed personal information about 10s of millions of people - everything from their job title to their home IP address. Cybercriminals could easily use this information to pursue financial fraud against everyone exposed.
Simultaneously, they could use the information to build effective phishing campaigns, posing as a person's employer, the government, and other trusted organizations to trick targets into any of the following:
- Sharing additional data that could be used for identity theft and financial fraud (i.e., social security numbers, tax records).
- Providing credit card information or details about bank accounts.
- Clicking a link embedded with malicious software, such as ransomware, spyware, or another form of virus.
Given the massive amount of people exposed, cybercriminals would only need to successfully defraud or attack a tiny portion to be successful.
Worse still, we viewed numerous.gov and New York Police Department email addresses in the database. Considering the complete list contained at least 63 million people, there were potentially many more sensitive email addresses. However, we only viewed a small sample.
Private data from members of the government and police are a goldmine for criminal hackers - especially if a foreign government supports them. By attacking individuals in the US government, hackers can infiltrate otherwise secure, high-level government agencies. When this happens, it can result in major national security breaches and devastating loss of trust in the government.
This has happened numerous times over the last few years, and the issue is getting worse.
For OneMoreLead
Due to this data leak’s severity, size, and strange circumstances, OneMoreLead could face serious questions about its competency and trustworthiness.
Potential clients may be unwilling to work with a new company that has exposed millions of people to fraud and cyberattack before it’s even finished its website.
The company could also face legal action as a result. Many of the people exposed are California residents, which means they’re protected under the state’s CCPA data privacy laws. If the Californian government, or any other government entity, was to pursue this case, it could cripple OneMoreLead.
For OneMoreLead Customers
If the access credentials we discovered did belong to the company’s customers, they would also be vulnerable to account takeover and fraud via OneMoreLead’s platform. Hackers could access their accounts and steal information relating to their businesses and customers.
Advice from the Experts
OneMoreLead could have easily avoided this leak if it had taken some basic security measures to protect the database. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For OneMoreLead Clients
If you’re a customer of OneMoreLead and are concerned about how this breach might impact you, contact the company directly to determine what steps it's taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the exposed database as part of a vast web mapping project. Our researchers use large-scale web scanners to search for unsecured data stores containing information that shouldn’t be exposed. They then examine each data store for any data being leaked.
Our team was able to access this database because it was completely unsecured and unencrypted.
OneMoreLead was using an Elasticsearch database, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing schemata from a single index at any time.
Whenever we find a data breach, we use expert techniques to verify the owner of the database, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to OneMoreLead to let them know about the vulnerability and suggest ways to secure their system.
These ethics also mean we carry a responsibility to the public. OneMoreLead users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
In recent years, our team dedicated to ethical security research has uncovered and responsibly disclosed a series of highly significant data breaches.
This has included a data breach originating from a Microsoft company cloud account. We also revealed that a popular Paleo diet company compromised the privacy and security of its entire customer base. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to anonymously report any data breach they find online. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.
Leave a comment
I loved it because it really helped me see a huge and clear picture of these data breach incidents. I feel this is a very serious threat to the whole world and I want to keep being informed on the issues. Thank You Ethicals You are spectacular!




Please, comment on how to improve this article. Your feedback matters!