Report: Paleo Lifestyle Brand Exposes Customers to Fraud in Massive Data Breach
Led by Noam Rotem, vpnMentor’s research team discovered a data breach affecting health and lifestyle brand Paleohacks.
Paleohacks teaches people how to adopt the paleo diet into their lifestyles through various media products, from recipes and meal plans to podcasts and courses.
The data breach originated from a cloud storage account Paleohacks was using to store the private data and personal details of over 70,000 customers and users. The company had failed to implement basic data security protocols. As a result, anyone whose data had been collected by Paleohacks was at risk of fraud, identity theft, hacking, and much more.
This data breach represents a serious lapse in security by Paleohacks, threatening the wellbeing of its customers - and the company itself. At the time of writing, the company has ignored every attempt we've made to help them close the vulnerability and told us they're 'not interested.'
Data Breach Summary
| Company | Paleohacks LLC |
|---|---|
| Headquarters | Nevada, USA |
| Industry | Health, Lifestyle, and Dieting |
| Size of data in gigabytes | 290 MB |
| Suspected no. of files | ~6,000 |
| No. of people exposed | ~ 69,000 |
| Date range/timeline | 2015-2020 |
| Geographical scope | Worldwide |
| Types of data exposed | PII data; profile photos |
| Potential impact | Fraud; identity theft; hacking; corporate espionage |
| Data storage format | Misconfigured Amazon AWS S3 Bucket |
Company Profile
Paleohacks is a multimedia online lifestyle brand founded in 2010. The company is currently located in Los Angeles, USA.
Paleohacks creates online products focused on promoting the Paleo diet, health and fitness tips, and wellness advice. These include written articles, a podcast, cooking recipes, and a member forum.
The company was sued in 2016 for false advertising and violating California state law, relating to its paid subscription products.
Timeline of Discovery and Owner Reaction
- Date discovered: 4th February 2021
- Date vendors contacted: 7th February 2021
- Dates of 2nd contact attempts: 8th February 2021, 16th March 2021, 5th April 2021, 12th April 2021, 19th April 2021
- Dates Amazon Contacted: 16th March 2021, 30th March 2021, 19th April 2021
- Date of Response: 19th April 2021
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue is quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s exposing the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, Paleohacks was using an Amazon Web Services (AWS) S3 bucket to store its customer data. S3 buckets are a hugely popular form of enterprise cloud storage used by 100,000s of businesses worldwide. However, AWS requires clients to manually set up their data privacy protocols when creating an S3 bucket account.
Paleohacks failed to install any privacy protocols on its S3 bucket - leaving the entire contents exposed to anyone with the most basic hacking skills.
Our team discovered the Bucket and quickly identified Paleohacks as its owner. After a quick but thorough investigation to confirm the nature of the breach and its implications, we reached out to the company and presented our findings.
Over a month later, we hadn’t received a reply and tried again. We also contacted AWS directly, to notify the company of a breach in its client's account.
In late April, nearly three months after we discovered the breach, and after sending numerous emails to Paleohacks, we finally received an email from a representative of the company. She told us she 'isn't interested' in the data breach. We reiterated that we were not disclosing the breach to sell our services or asking for compensation - we're simply trying to keep Paleohacks' customers safe.
The Paleohacks representative claimed to be an independent contractor and suggested we contact the company directly. We repeated that we had attempted to do so numerous times already, with no success. She replied simply "If no one replies then they aren’t interested. Sorry about that."
Example of Entries in the S3 Bucket
While the amount of files was small compared to some breaches and leaks we’ve discovered in the past, they still exposed sensitive data of close to 70,000 people worldwide.
Paleohacks was using the bucket to store Personally Identifiable Information data collected from its entire userbase, dating all the way back to 2015. Anyone who signed up to a service (like a course or newsletter) or bought a product from the company (like a recipe book) was potentially exposed.
Aside from PII data, the bucket also included details uploaded by users when creating accounts on Paleohacks’ "Q&A community", exposing a vast amount of personal information for 10,000s of people.
The private personal user data we viewed included:
- Full names
- Usernames
- Email addresses
- Hashed passwords
- IP addresses
- Timestamps for logins
- Profile descriptions (bios)
- Employers and company details
- Location
- Personal websites
- Date of birth
- Avatar URL (profile picture)
- Points earned on Paleohacks products
The following screenshots demonstrate how the data was stored and the type of photos exposed.
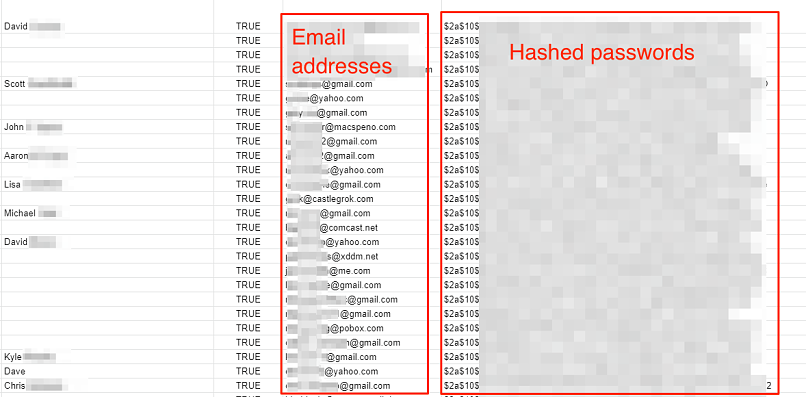 Paleohacks customer data
Paleohacks customer data
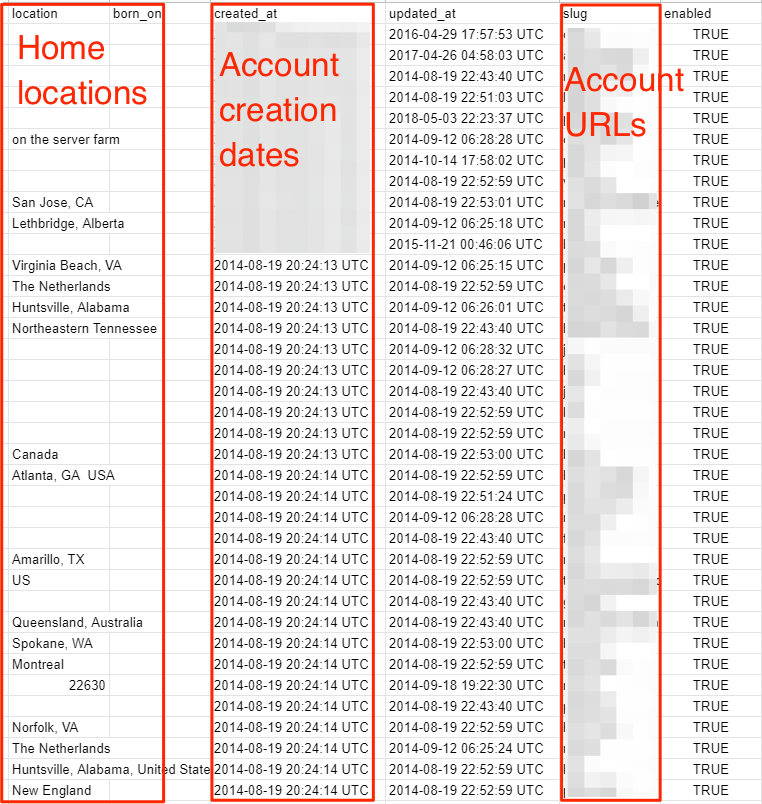 Paleohacks customer data
Paleohacks customer data
 Photos of Plaehacks customers exposed in the data breach
Photos of Plaehacks customers exposed in the data breach
Reset Password Tokens
Aside from PII data and personal information, some entries in the bucket also contained password reset tokens for account holders on Paleohacks’ subscription and membership products.
While the passwords were protected by the BCRYPT hashing algorithm (a sophisticated form of password encryption), a hacker could easily use the tokens to reset a person’s password, gain access, and lock the original user out of their account.
Doing so would allow the hackers to take control of 1,000s of Paleohacks accounts and any additional data stored therein.
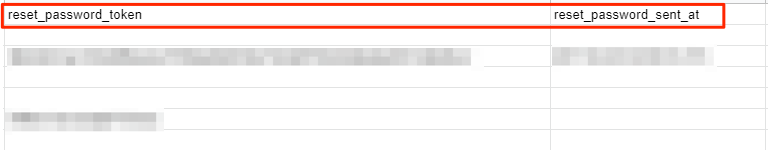 Password reset tokens for Paleohacks ser accounts
Password reset tokens for Paleohacks ser accounts
Data Breach Impact
By failing to store years of customer data correctly, Paleohacks exposed nearly 70,000 people to numerous risks. Due to the nature of the data breach, and the fact that people exposed are spread across the globe, any crimes committed using Paleohacks’ customer data may never be traced back to the company.
For Paleohacks' Customers
Hackers and cybercriminals could use the PII data to target Paleohacks' customers in a wide range of financial fraud schemes, including wholesale identity theft.
By combining a customer’s PIII data with records of their purchases and orders on the Paleohacks website, a criminal enterprise could create highly effective phishing emails posing as the company and trick customers into providing additional data and credit card details. They could also be enticed into clicking a link embedded with malware, spyware, or another form of malicious software.
Furthermore, the breach potentially allowed hackers to ‘break into’ a Paleohacks user’s account by using the “reset password” tokens. They could access 1,000s of Paleohack’s private accounts and pursue numerous criminal activities.
For Paleohacks
Paleohacks also faces numerous issues as a result of the data breach.
As the company is based in the US state of California, it comes under the jurisdiction of the California Consumer Privacy Act (CCPA). As a result, the company may face scrutiny from the body in charge of the CCPA, along with potential fines or legal actions.
The same could also be true if Paleohacks compromised any EU citizens’ data, thus breaching the trade bloc’s GDPR rules.
Finally, in an era of increasing concern over data privacy, hacking, and cybercrime, a data breach of this magnitude could severely damage Paleohacks’ reputation amongst its customer base.
The field of diet and lifestyle is fiercely competitive, and if customers believe that Paleohacks isn't reliable in safeguarding their personal information, they might turn to other sources for advice and direction.
Regardless of whether criminal hackers had discovered the Paleohacks data, each of these outcomes could have long-lasting negative consequences for the company.
Advice from the Experts
Paleohacks could have easily avoided exposing its customers’ data if it had taken some basic security measures. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
- Using unique random strings of characters for asset names to reduce your online footprint and minimize the risk your assets are discovered.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online data from hackers.
Securing an Open S3 Bucket
It’s important to note that open, publicly viewable S3 buckets are not a flaw of AWS. They’re usually the result of an error by the owner of the bucket. Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
In the case of Paleohacks, the quickest way to fix this error would be to:
- Make the bucket private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to the S3 bucket to further restrict who can access it from every point of entry.
For Paleohacks' Customers
If you’re a customer of Paleohacks and are concerned about how this breach might impact you, contact the company directly to determine what steps it's taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the breach in Paleohacks’ data as part of a huge web mapping project. Our researchers use large-scale web scanners to search for unsecured data stores containing information that shouldn’t be exposed. They then examine each data store for any data being leaked.
Our team was able to access Paleohacks’ S3 bucket because it was completely unsecured and unencrypted.
Whenever we find a data breach, we use expert techniques to verify the owner of the data, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to Paleohacks, not only to let them know about the vulnerability but also to suggest ways to make their system secure.
These ethics also mean we carry a responsibility to the public. Paleohacks users across the globe must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We have no evidence - and no way of knowing - whether the data in our reports have been accessed or leaked by anyone else; only the database owner can know that.
We do our best to prevent this from happening by reaching out to the companies and ensuring they secure their leaking database as soon as possible.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included an enormous data breach exposing the data of 10,000s of online shoppers worldwide. We also uncovered separate scams targeting users on Facebook, Instagram, and Spotify. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to report any data breach they find online anonymously. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.
Leave a comment
Utterly reprehensible by this company. They should be investigated by The authorities if it hasn't happened already.




Please, comment on how to improve this article. Your feedback matters!