Report: Fast Growing Fitness Brand Exposes Customers in Massive Data Breach
Led by Noam Rotem and Ran Locar, vpnMentor’s research team recently discovered a data breach exposing customers of online fitness company V Shred.
V Shred sells numerous online and physical products related to dieting, nutrition, and fitness. The exposed files included meal plans, sensitive photos from V Shred customers, and CSV files containing the private data of over 99,000 people.
By not protecting these files, V Shred compromised the privacy and security of its customers and left them exposed to bullying, fraud, and more.
Data Breach Summary
| Company | V Shred |
|---|---|
| Headquarters | Las Vegas, USA |
| Industry | Fitness and nutrition |
| Size of data in gigabytes | 606GB |
| Suspected no. of files | 1.38M+ files and growing |
| No. of people exposed | 99,000+ |
| Date range/timeline | Up to May 2020 |
| Geographical scope | USA |
| Types of data exposed | Custom meal plans; user profile photos; before/after fitness photos; CSV files containing PII data |
| Potential impact | Doxing; bullying; extortion |
| Data storage format | Misconfigured AWS S3 bucket |
Company Profile
V Shred was founded in 2017 and is based in Las Vegas, USA.
The company offers many different products within fitness, nutrition, and dieting. These include mobile apps, customized diet plans, personal training, dietary supplements, workout plans, and much more.
For a brand that’s only two years old, V Shred boasts a massive international audience. Its website claims 740,000 Youtube subscribers, 12 million monthly website views, and over 40,000 clients in 119 countries.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s exposing the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, the data was stored on a misconfigured Amazon Web Services (AWS) S3 bucket, which was completely open to public access. The URL of the bucket contained ‘vshred,’ and many of the files contained the company’s logo and other identifiers.
Our team quickly confirmed V Shred as the S3 bucket’s owner and contacted the company immediately. We also reached out to AWS directly to notify them of the breach.
V Shred claimed it was necessary for user files to be publicly available and denied that any PII data had been exposed.
In response, we provided a detailed breakdown of exactly how the S3 buckets setup allowed public access to files containing PII data, forwarded to the company via an AWS representative.
In time we learned that V Shred had removed the files containing lists of PII data from the S3 bucket, but would be leaving all other files publicly accessible, despite the risks involved.
- Date discovered: 14th May 2020
- Date vendors contacted: 18th May 2020
- Date AWS contacted: 20th May 2020
- Date of Response: June 1st (via Amazon) 2020
- Date of Action (file disabled): June 18th 2020
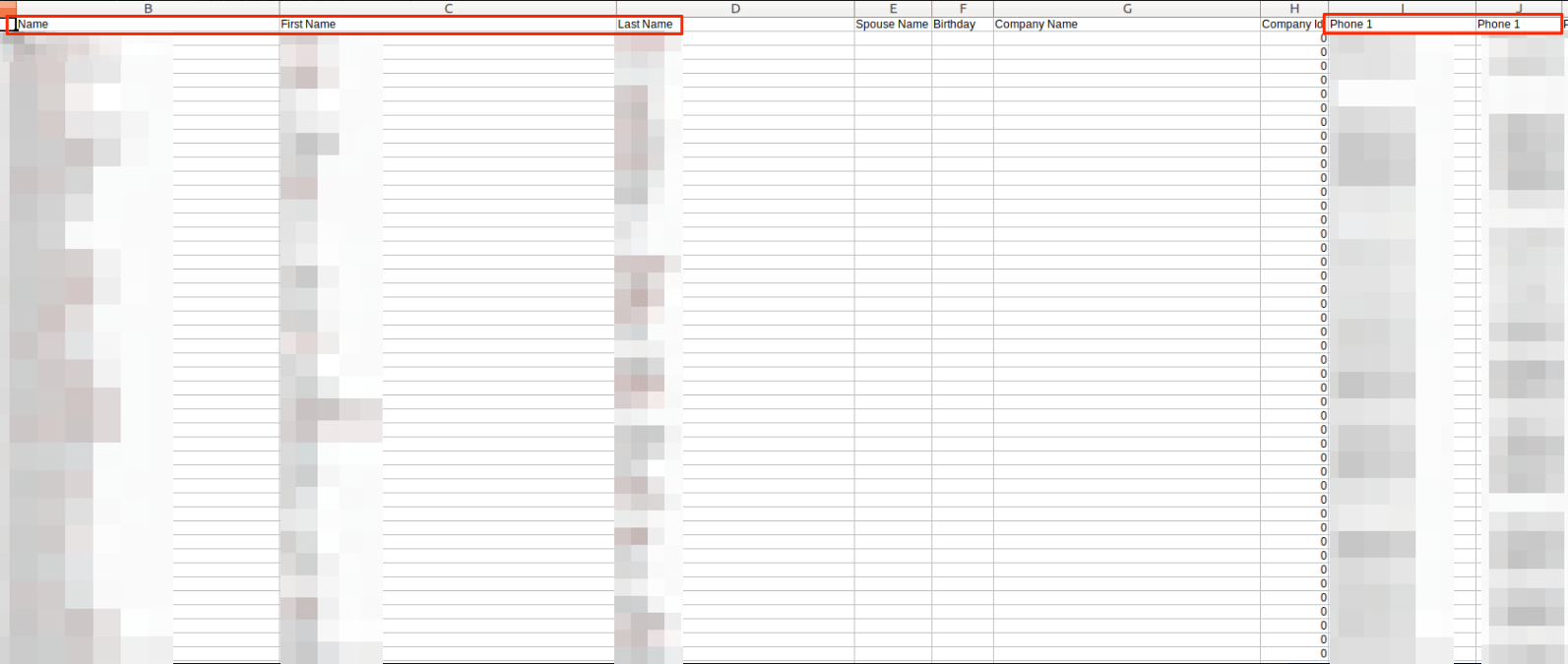
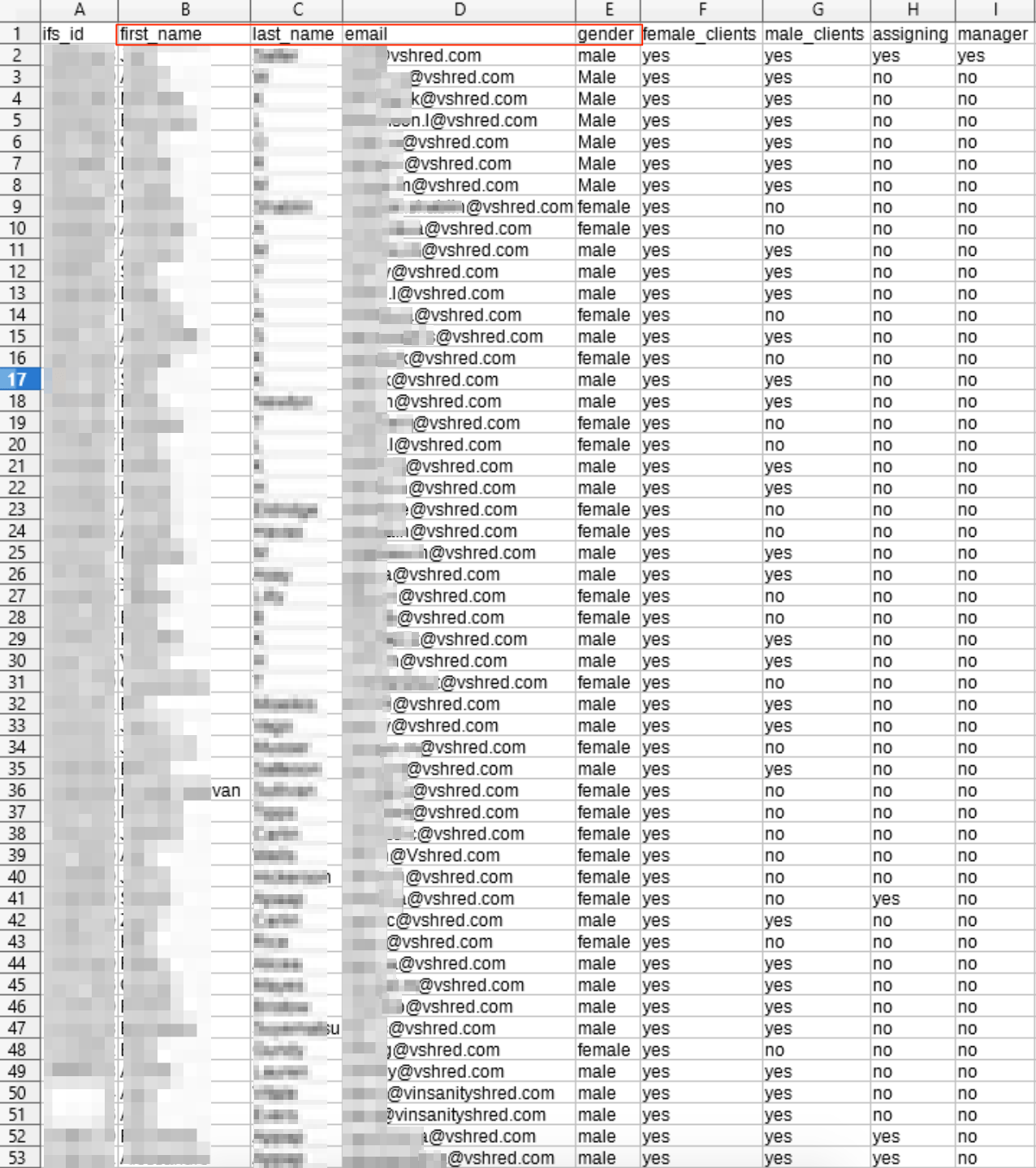
Example of Data Entries
The unsecured S3 bucket contained over 1.3 million individual files, totaling 606 gigabytes of data.
Most of the files related to individual users of V Shred’s products, and included:
- Account profile photos
- Very revealing ‘before and after’ body photos
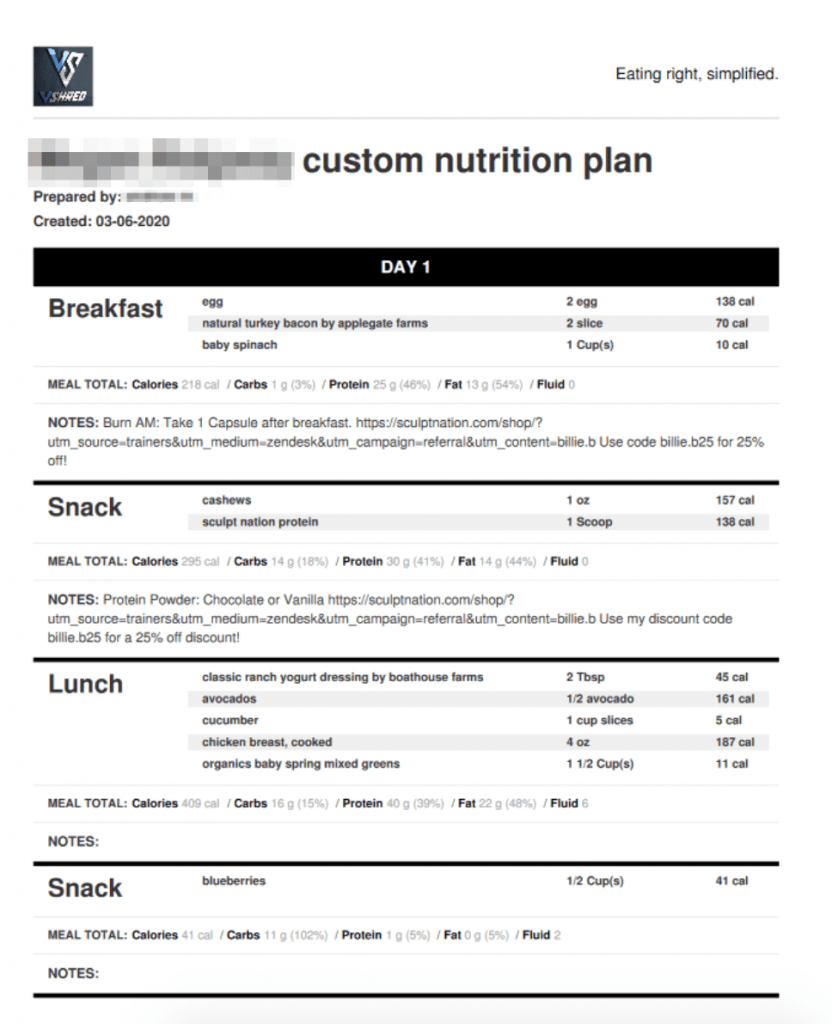
- Custom meal plans
Many of these photos and documents contained various pieces of Personally Identifiable Information (PII) data that revealed sensitive information about the people exposed.
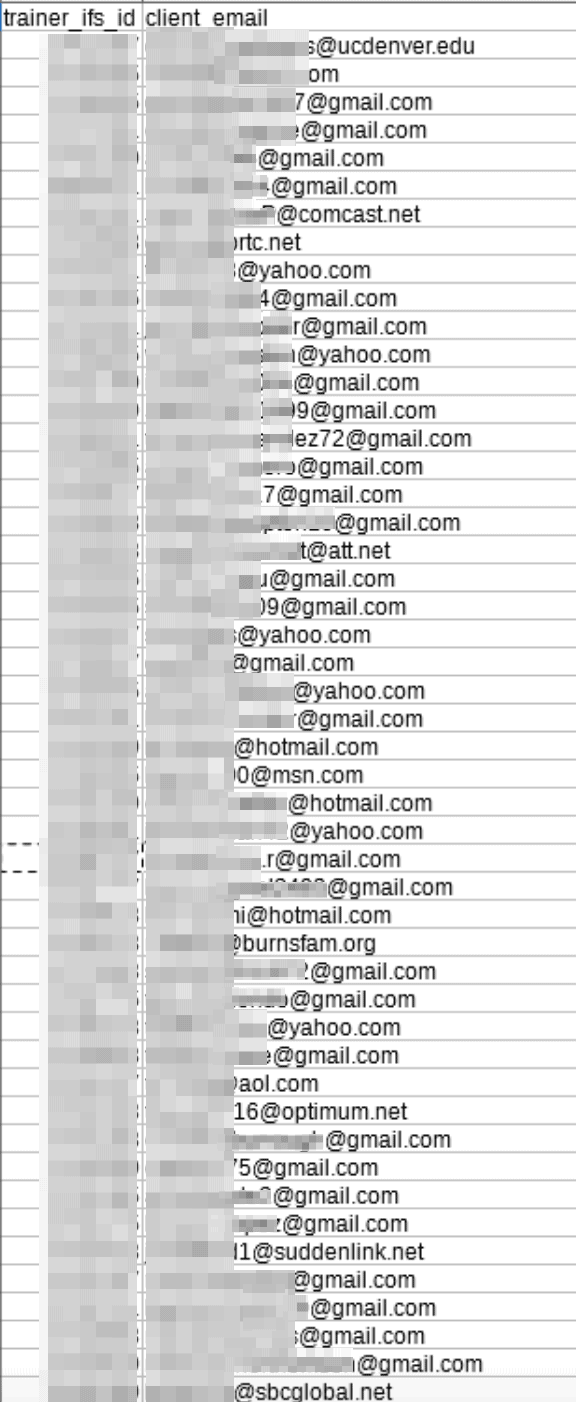
However, among the meal plans and photos, we discovered at least three separate CSV files with PII data from 10,000s of individuals across the USA, and abroad. (For ethical reasons, we didn’t check all the files in the V Shred’s S3 bucket, so it's possible there were more files with PII data elsewhere that were also exposed.)
Each CSV file appeared to have a distinct function, containing the following:
- CSV file #1: 96,000+ entries, potentially from lead generation activities by V Shred
- CSV file #2: V Shred client email list, with 3,522 entries
- CSV file #3: List of 52 trainers working for V Shred, including their email addresses
The CSV files presented a much greater immediate risk. Combined, they contained huge amounts of PII data for each individual listed.
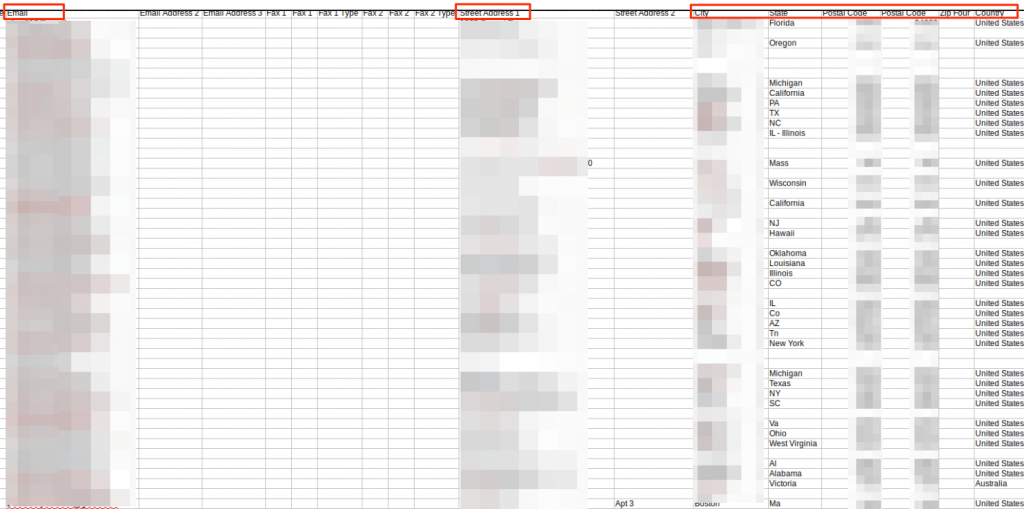
This included:
- Full names
- Home addresses
- Email address
- Phone numbers
- Birthdays
- Social security number
- Spouse names
- Social media accounts
- Username and password
- Gender
- Health conditions
- Age range
- Citizenship status
- Much more
The following screenshots were taken from the S3 bucket, showing how detailed the entries were on the CSV file were.
We’ve also included some of the meal plans and photos uploaded by V Shred customers.
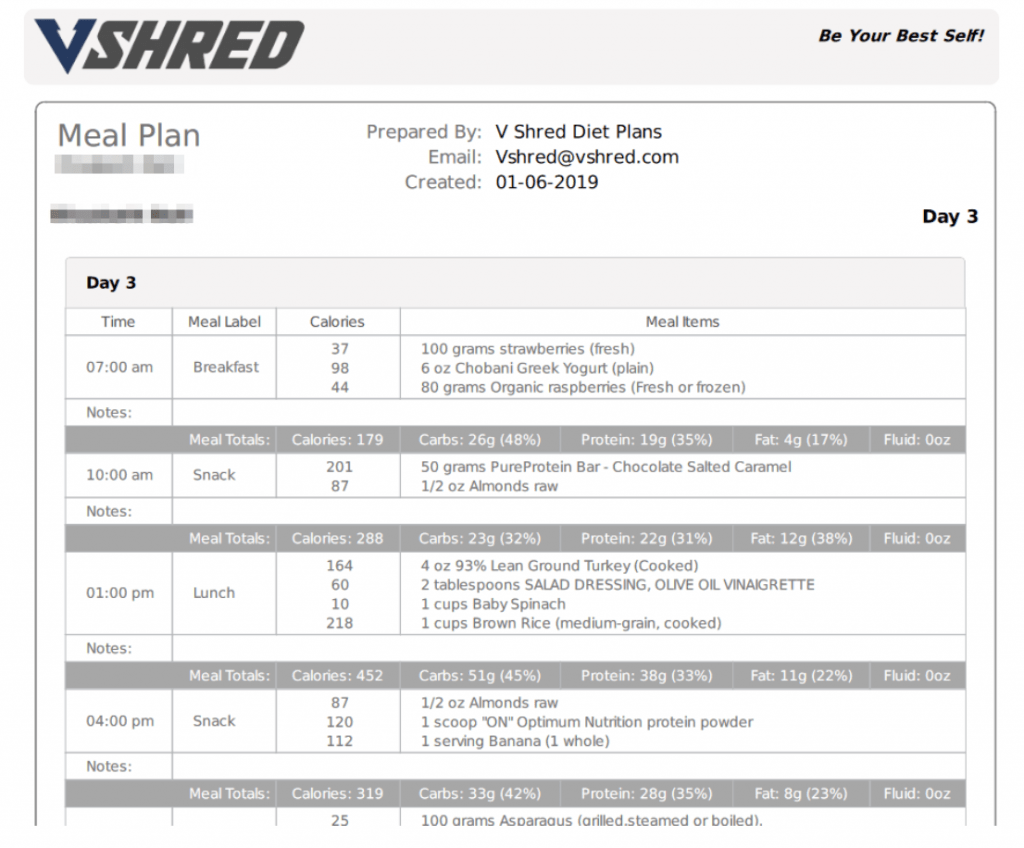

As you can see from these examples, the files revealed a great deal of personal information about V Shred’s customers, compromising their privacy and exposing them to many potential issues.
Data Breach Impact
V Shred is a young company and appears to be run by a small team. However, it’s still responsible for protecting the people using its products and signing up for its services.
By not doing so, V Shred has jeopardized the privacy and security of the people exposed, and the future of the company itself.
Impact On V Shred’s Customers
Using the PII data exposed through the S3 bucket, malicious hackers and cybercriminals could create very effective phishing campaigns targeting V Shred customers.
A phishing campaign involves sending fake emails to a target, imitating a real business. These emails aim to trick victims into providing sensitive financial data, such as credit card details, or clicking a link embedded with malicious software like malware and ransomware.
If a phishing campaign was successful, hackers could also resort to blackmail and extortion, threatening to release the ‘before and after’ photos if a victim doesn’t agree to pay a ransom.
People using V Shred’s products and membership plans could be incredibly self-conscious and easily susceptible to such blackmail tactics.
Finally, if the CSV files contained the social security numbers of any individuals, this would be a goldmine for cybercriminals. They could utilize such information for a wide range of frauds and wholesale identity theft.
If any of the criminal schemes described above were successful, the impact on a victim's personal life and financial welfare could be devastating, especially during a global pandemic, with so much uncertainty, growing unemployment, and a looming recession.
Impact on V Shred
V Shred could potentially lose a lot of customers and followers due to this data breach. People may be reluctant to trust a company that doesn’t sufficiently protect their most private and sensitive data.
The fitness and health industry is a crowded space, and V Shred’s customers have plenty of other options among its many competitors.
These same competitors could exploit the data breach to entice V Shred’s customers over to their products and services, using negative marketing and publicity against the company.
With many people now spending a lot more time exercising and working out from home - as gyms and fitness centers are closed due to Coronavirus - the market for products and services like those offered by V Shred is increasingly popular.
As such, the industry it works in will become more competitive - and ruthless.
The exposed meal plans were paid products, for example, customized to each customer. As V Shred is a fast-growing, increasingly popular brand, competitors could also use these for insights to replicate its products and offerings, giving them a shortcut to further damaging V Shred’s market share.
A slip up like this data breach could cost V Shred dearly in the short and long term.
V Shred also risks regulatory issues, as it will most likely fall under the jurisdiction of California’s CCPA data protection law. As a result, the company may face investigations, audits, and even fines.
V Shred is a small business that may struggle to overcome the combined impact on its revenue from losing customers, being audited, and any negative publicity - all resulting from this data breach.
Advice from the Experts
V Shred could have easily avoided this breach if it had taken some basic security measures to protect the data. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online data from hackers.
Securing an Open S3 Bucket
It’s important to note that open, publicly viewable S3 buckets are not a flaw of AWS. They’re usually the result of an error by the owner of the bucket. Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
In the case of V Shred, the quickest way to fix this error would be to:
- Make the bucket private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to their S3 bucket to further restrict who can access it from every point of entry.
For V Shred Users
If you’re a customer of V Shred and are concerned about how this breach might impact you, contact the company directly to determine what steps it's taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
As part of a comprehensive web mapping project, the vpnMentor research group detected a breach in V Shred's S3 bucket. Our investigative team employs port scanning to scrutinize specific IP blocks and evaluate various systems for potential vulnerabilities or weak points. Each identified weak point is then thoroughly inspected for any signs of exposed data.
Our team was able to access V Shred's S3 bucket because it was completely unsecured and unencrypted.
Whenever we find a data breach, we use expert techniques to verify the owner of the data, usually a commercial company.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to V Shred, not only to let them know about the vulnerability but also to suggest ways in which they could make their system secure.
These ethics also mean we carry a responsibility to the public. V Shred customers must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
Introducing The Leak Box
To ensure our mission has the most significant impact possible, we’ve also built The Leak Box.
Hosted on the dark web, the Leak Box allows ethical hackers to anonymously report any data breach they find online. We then verify and report any submission deemed a legitimate threat to the public’s safety.
We never sell, store, or expose any information we encounter during our security research. This includes any information reported to us via The Leak Box.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included an enormous data breach exposing the data of 100,000s of people across the USA, including many families. We also revealed that a European home exercise company had compromised the privacy and security of its users around the world. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
[Publication date: 17th June 2020]




Please, comment on how to improve this article. Your feedback matters!