How to Remove Bloatware: Android, Windows, & More (2025)
Bloatware — those pesky pre-installed apps you never asked for — can slow down your devices, eat up memory, and even put your privacy at risk. On some systems, removing them isn’t as easy as hitting Uninstall, especially if they’re baked into the operating system.
And it’s not just a personal annoyance — bloatware is everywhere. In fact, 89% of IT professionals say they waste time every week dealing with bloated applications1, making it a problem that affects productivity on a much larger scale.
How can I easily remove bloatware from Windows 10 and other devices? There’s no one-size-fits-all method, but depending on your device, you can use built-in settings, command-line tools like PowerShell or ADB, or third-party apps to get the job done.
In this guide, I’ll walk you through how to identify and remove bloatware from Windows, Mac, Android phones, iPhones, and even Firesticks. Whether you’re a casual user or a bit more tech-savvy, there’s a solution here for you.
What Is Bloatware and Why Should I Remove It?
Bloatware refers to unwanted software that comes pre-installed on a device — typically by manufacturers or carriers. This includes trialware, redundant tools, promotional apps, games, and utilities you likely never asked for. While not all pre-installed software is harmful, much of it offers limited value, duplicates existing features, and quietly consumes system resources.
Why is it a problem?
- Slows performance. Many bloatware apps auto-start at boot and run in the background, eating up CPU cycles and RAM.
- Wastes storage. Some can take up several gigabytes of space, reducing room for apps you actually use.
- Drains battery. Background processes can lead to faster battery depletion — especially on mobile devices.
- Privacy risks. Some pre-installed apps are known to collect user data without clear consent.
- Security risks. Bloatware often goes unpatched, leaving known vulnerabilities open (e.g., the infamous Superfish adware on Lenovo devices).
Getting rid of bloatware isn’t just about decluttering — it’s about optimizing your device and protecting your data. Removing it can:
- Speed up your device
- Free up RAM and storage
- Extend battery life
- Reduce potential privacy and security risks
- Give you full control over what runs on your system
How to Identify Bloatware on Your Device
Bloatware comes in several forms, depending on who installed it and why. Some are baked into the operating system by manufacturers, others are bundled through partnerships or meant to push paid upgrades. Understanding the source helps you decide what can be safely removed.
| Type | Description | Common Examples |
| OEM bloatware | Installed by the original equipment manufacturer | Samsung Email, Lenovo Vantage |
| Carrier bloatware | Added by mobile carriers | AT&T Navigator, Verizon Cloud |
| Trialware/adware | Limited-time software with upsells | McAfee trials, Office 365 trials |
| Promotional apps | Installed as part of partnership deals | Facebook, Candy Crush on Windows |
You can also use tools to help you identify bloatware. These programs scan your device for unnecessary software and highlight apps you may want to remove.
How to Remove Bloatware
The process of removing bloatware can vary depending on your device and operating system. You can uninstall manually or deploy automated methods, like dedicated third-party apps, to help you achieve a cleaner, more efficient device.
Method 1. Removing Bloatware Manually
If you’d rather not install additional tools or mess with advanced commands just yet, the simplest way to get started is by manually removing bloatware through your device’s settings. This works well for easily removable apps and gives you more control over what stays and what goes.
How to Remove Bloatware From Windows 10 and Windows 11
- Open the start menu and click on the settings icon (the gear-shaped icon on the left).
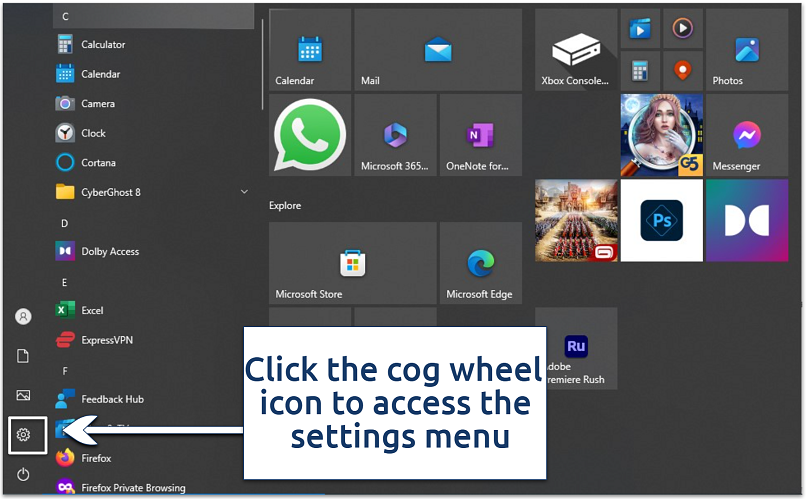 You can also press Windows + I on your keyboard to open settings instantly
You can also press Windows + I on your keyboard to open settings instantly - Click on System Components > Apps & features.
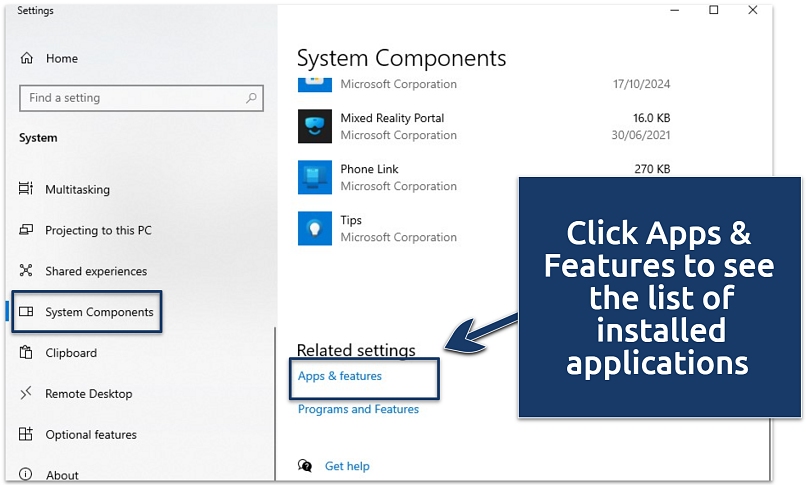 Some preinstalled programs may not appear on the apps and features list
Some preinstalled programs may not appear on the apps and features list - Scroll through the list and look for anything you don’t use or recognize. Not sure what something does? A quick web search of the app name can help you avoid removing anything important.
- Click on the app and select Uninstall. Follow the prompts to complete the removal.
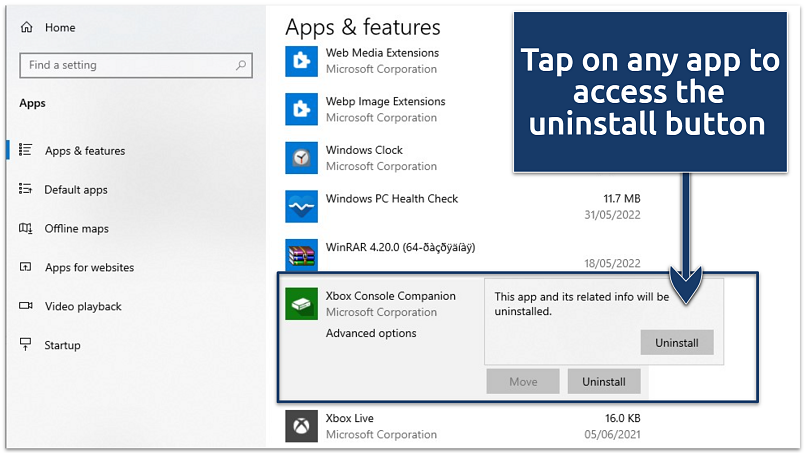 If you see “Modify” instead of “Uninstall,” the app is likely a system component or harder to remove
If you see “Modify” instead of “Uninstall,” the app is likely a system component or harder to remove
How to Remove Bloatware From Mac
- Open Finder and navigate to the Applications folder.
- Locate the bloatware app you want to remove.
- Drag the app to the trash bin or right-click on the app and select Move to Bin.
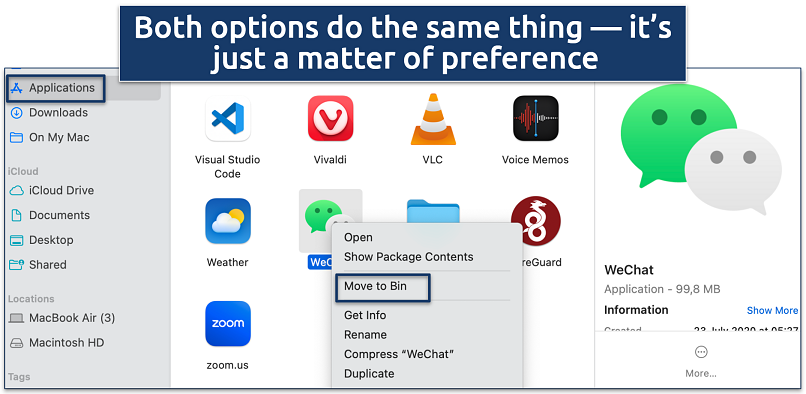 Some apps may require your password — that’s normal for system apps
Some apps may require your password — that’s normal for system apps - Empty the bin to complete the uninstallation process.
How to Remove Bloatware From Android
Getting rid of bloatware on Android can vary a bit depending on your phone’s brand — whether it’s Samsung, Xiaomi, Realme, or another manufacturer. Even custom Android skins like Funtouch OS or ColorOS may change the menu names slightly, but the general process is similar across devices.
Here’s how you can do it:
- Open the Settings app and look for Apps, Apps & notifications, or Application Manager — the name depends on your device.
- If you don’t see the full list right away, tap Manage apps or a similar option.
- Scroll through the list and look for apps you didn’t install or never use.
- Tap the app and choose Uninstall if it’s available. If there’s no uninstall button, tap Disable instead. This stops the app from running or using resources — without fully deleting it.
How to Remove Bloatware From iPhone
Unlike Android, Apple doesn’t let you completely uninstall most pre-installed apps — but you can still tidy things up by hiding them from your home screen.
- Tap and hold the app icon until a menu appears.
- Select Remove app from the pop-up menu.
- Choose Remove from Home Screen to make it disappear without deleting it.
How to Remove Bloatware From Firestick
The Amazon Fire TV Stick can also come with extra apps you don’t need — and it includes some data tracking settings you might want to turn off.
To remove unwanted apps:
- Go to Settings > Applications > Manage Installed Applications
- Choose the app and select Uninstall
For better privacy, you can also tweak a few settings:
- Go to Settings > Preferences > Privacy Settings
- Turn off Data Monitoring and Interest-Based Ads to stop Amazon from collecting usage info and personalizing ads
Method 2. Using Third-Party Apps to Remove Bloatware From Your Device
If the regular uninstall option isn’t available — or the app doesn’t even show up in your device’s app list — don’t worry. You still have options. Some built-in tools and third-party apps can help you remove stubborn or hidden bloatware that can’t be deleted through the usual settings menu.
PowerShell (Windows)
PowerShell is a powerful tool built into Windows that lets you run commands to remove system apps — including ones that don’t show an Uninstall button in the settings. It might look intimidating at first, but if you follow a few simple steps, it’s pretty straightforward. Here’s how to use PowerShell to remove bloatware:
- Click the Start menu and search for PowerShell.
- Right-click Windows PowerShell and choose Run as administrator.
 You’ll need admin privileges to remove system-level apps
You’ll need admin privileges to remove system-level apps - In the PowerShell window, copy and paste this command to list all installed apps:
Get-AppxPackage | Select Name, PackageFullName
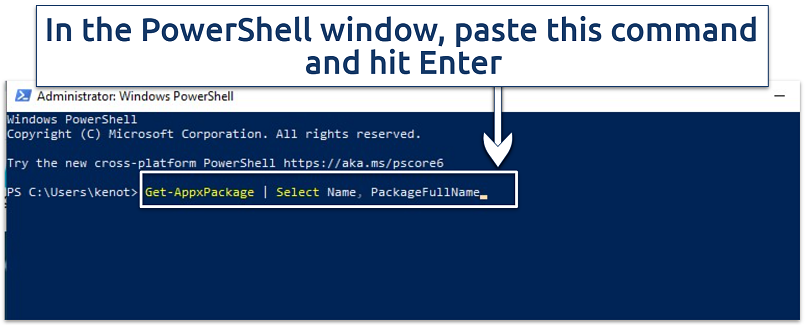 The output will include two columns: the Name and the PackageFullName
The output will include two columns: the Name and the PackageFullName - Find the app you want to remove, and copy its full name from the list that appears.
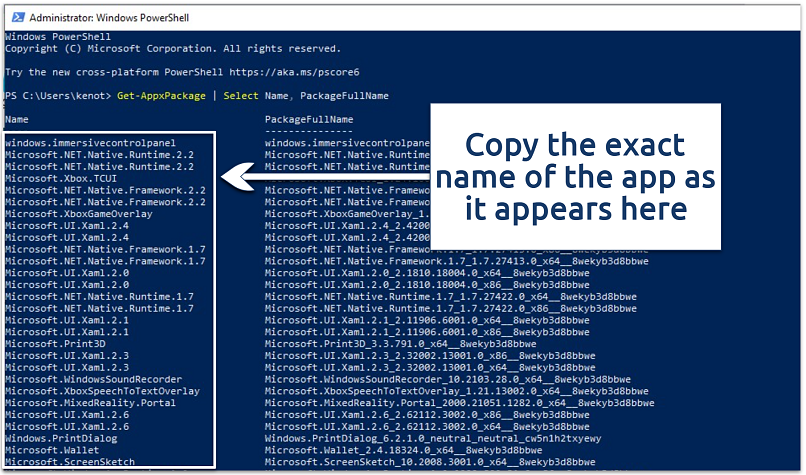 If you’re overwhelmed by the number of entries, try narrowing it down by searching a keyword
If you’re overwhelmed by the number of entries, try narrowing it down by searching a keyword - Use this command (replacing the placeholder with the app’s real name):
Get-AppxPackage *AppName* | Remove-AppxPackage
For example, to remove the built-in Movies & TV app:
Get-AppxPackage Microsoft.ZuneVideo | Remove-AppxPackage - Press Enter, and the app should be removed from your system.
Android Debug Bridge (ADB) — No Root Needed
If you’ve tried uninstalling bloatware on Android but ran into apps that can’t be removed through Settings, Android Debug Bridge (ADB) can help. It’s a command-line tool that gives you more control over your device — including the ability to remove system apps — without needing to root your phone. Here’s how to use ADB to clean up your Android device:
- Go to Settings > About Phone, then tap Build Number seven times. This will unlock Developer Options. You may need to look under System or About Device, depending on your Android version or brand.
- In the newly visible Developer Options menu, scroll down and toggle on USB Debugging.
- Connect your phone to your computer via USB. Make sure USB Debugging is allowed when prompted on your phone screen.
- Open a terminal or command prompt on your computer. If you haven’t already, download the Android SDK Platform Tools to access ADB.
- Run this command to see a list of installed packages:
adb shell pm list packages
This will show you all apps on the device — both system and user-installed. Look for package names like com.samsung.android.bixby.agent. - Find the app you want to remove, then use this command (replace com.example.app with the exact package name):
adb shell pm uninstall -k --user 0 com.example.app
Using Dedicated Bloatware Removal Tools
If command-line methods aren’t your thing, don’t worry — several third-party tools can help you identify and remove bloatware with just a few clicks. These tools scan your system for unnecessary apps and offer suggestions for cleanup. Here are some popular choices for Windows and macOS:
- CCleaner (Windows & Mac) — Great for basic cleanup, removing unwanted apps, and clearing out junk files.
- Avast Cleanup Premium (Windows & Mac) — Provides comprehensive system optimization, including junk file removal, app management, and performance enhancement tools.
- AVG TuneUp (Windows & Mac) — Offers in-depth performance tuning, automatic maintenance, and bloatware suggestions.
- CleanMyMac X and AppCleaner (Mac only) — Designed specifically for macOS users to uninstall apps completely and remove leftover files that clutter your system.
How to Avoid Future Bloatware
Once you’ve cleaned up your device, the next step is making sure it stays that way. The good news? A few simple habits can go a long way in helping you avoid bloatware from creeping back in. Here’s how to keep things clean from the start:
- Go for a clean install when setting up a new device. Whether it’s a new Windows PC or Android phone, look out for setup options labeled “minimal” or “clean install.” These usually skip the extra apps and get you started with just the essentials.
- Pay attention during software installations. Ever seen those sneaky checkboxes that try to install a toolbar or “recommended app”? Yeah — uncheck those. Many free programs bundle extra software by default, so it’s worth reading each step before clicking Next.
- Stick to trusted sources for downloads. Downloading apps from random third-party websites can invite bloatware, adware, or worse. Whenever possible, use official stores like the Microsoft Store, Google Play, or Apple’s App Store — or go directly to the app developer’s website.
- Consider open-source or paid alternatives. Freeware is great, but it often comes bundled with extra “offers.” Open-source and paid apps are less likely to include junk and tend to respect your privacy a bit more.
- Use anti-bloatware tools for regular checkups. They can scan your system and flag any potentially unwanted applications (PUAs) before they pile up.
FAQs on How to Remove Bloatware
Does Windows 11 have bloatware?
Yes, Windows 11 does have bloatware. Depending on the manufacturer, it can come with pre-installed apps like trial antivirus software, games, promotional tools, or other third-party programs many of you don’t need (for example, Microsoft Teams and News). These apps often run in the background, take up space, and may affect performance — though most of them can be uninstalled or disabled.
Are there any pre-installed apps I should keep so my device functions properly?
Yes, there are some pre-installed apps you should keep because they’re essential for your device to function properly. These include apps like Settings, File Explorer, Microsoft Store, and any drivers or system utilities that manage your hardware (like your touchpad, display, or audio). Removing these can affect core functionality or stability, so if you’re unsure about an app, it’s always a good idea to look it up before uninstalling it.
Does resetting the PC remove bloatware?
Not always. Resetting your PC might remove some apps you’ve installed, but many manufacturers include bloatware in the recovery image — so when you reset, that software comes back too. If you want a truly clean system without manufacturer-added extras, it's better to do a fresh install of Windows using the Media Creation Tool from Microsoft.
Can bloatware come back after a system update?
Yes, bloatware can sometimes come back after a system update — especially major ones. Updates may reinstall default apps or include new promotional software from the manufacturer or Microsoft. It’s a good idea to review your installed apps after big updates and remove anything you don’t want again.
Is it safe to remove bloatware?
Yes, in most cases it’s safe to remove bloatware — especially apps you don’t use and that aren’t essential to system functionality. Just be careful not to uninstall critical system apps like Settings, drivers, or core Windows components. If you’re unsure about a specific app, it’s a good idea to look it up first before removing it.
Conclusion
Getting rid of bloatware is one of the easiest ways to make your device run smoother, faster, and more efficiently. You’ll notice better performance, longer battery life, and fewer distractions — all without needing to be super tech-savvy. In most cases, removing bloatware is straightforward, and if an app can’t be uninstalled, you can usually disable it or use a trusted third-party tool to help.





Please, comment on how to improve this article. Your feedback matters!