What is Cyberstalking? Definition, Example, and the Law
Picture this — you're online, minding your own business, when suddenly you find yourself relentlessly pursued by someone lurking in the digital shadows. That's cyberstalking. It's when an individual exploits the internet to stalk or threaten someone else, transforming the expansive digital world into a stage for crime and harassment.
As we dive deeper into the internet era, the importance of discussing cyberstalking skyrockets. Our daily routines are so intertwined with online activities that it's vital for you to be aware of the risks lurking out there. After all, the line between our online and offline lives has never been so thin.
I’ve put together this guide to help explain what cyberstalking is, present its legal definition, highlight key examples, and contrast it with cyberbullying. Plus, you'll get insights on the laws surrounding it and advice on how to report incidents, gather evidence, and bolster your defenses against such threats.
What is Cyberstalking and How Does It Work?
Cyberstalking consists of persistent online harassment and unwanted attention. The stalkers employ social media, emails, and messaging apps to intimidate their victims. Such intimidation and harassment usually takes place over a sustained campaign that invades the victim’s privacy over time. Often, the harasser is someone known to the victim personally or professionally.
Unlike traditional stalking, the online world allows perpetrators to hide behind screens. But cyberstalkers still have the same goal as traditional stalkers: to implement a perpetual state of fear and anxiety in the victim.
According to the Pew Research Center survey of US adults, 41% of Americans have personally experienced some form of online harassment, including cyberstalking. The National Center for Victims of Crime reports that over half of cyberstalking victims are women under 30.
Is Cyberstalking Legal?
Cyberstalking is illegal and considered a crime almost everywhere. However, the definitions and penalties vary across jurisdictions:
- United States: Governed by federal law 18 U.S.C. §2261A, cyberstalking is defined as using electronic communication means to cause a person to fear for their life or suffer substantial emotional distress. Penalties can include imprisonment for up to 5 years, fines, or both. State laws, like California Penal Code § 646.9, may also impose additional penalties and provide more specific definitions.
- Canada: While Canada doesn't have a specific cyberstalking law, behaviors related to cyberstalking can fall under various offenses in the Criminal Code, such as criminal harassment or uttering threats.
- United Kingdom: The Protection from Harassment Act 1997 defines harassment, which includes cyberstalking, as a course of conduct that causes another person to feel alarmed or distressed. Penalties can range from a fine up to a jail term, depending on the severity and duration of the harassment.
- Poland: The Penal Code, through Articles like 190a, 191, 207, and 217, provides various definitions related to harassment, violation of personal inviolability, and more. Penalties can vary from monetary fines to imprisonment, based on the specific article violated.
- Australia: As a part of the Stalking Amendment Act 1999, cyberstalking is when a person intentionally uses electronic communication to harass or menace another person. The penalties can include fines, imprisonment, or both, depending on the state or territory's legislation.
Intent plays a pivotal role in defining cyberstalking. As per US legal frameworks, it's vital for a perpetrator to possess the intent to harm, harass, intimidate, or surveil with harmful intentions.
The victim should also have a justifiable reason to anticipate danger. A cyberstalker will generally have to pose a real threat to yourself or your loved ones, including family, partners, or even pets. To come under cyberstalking laws, threats and harassment must be executed using any form of computer or digital communication device.
Main Types of Cyberstalking
Cyberstalking manifests in many types, with the most common being:
- Vindictive — driven by revenge, perpetrators aim to ruin the victim's reputation, emotional peace, or financial standing.
- Personal — involves obsessed criminals who monitor victims’ daily activities, send them unwanted gifts, or physically locate them using technology.
- Collective — groups that coordinate online harassment campaigns and expose the personal information of other individuals or organizations.
- Indirect — a criminal directs another person or group to harass or follow the victim.
- Intimate — often emerging from strained romantic relationships, this type involves control, manipulation, and retaliation.
What Is Considered Cyberstalking
Cyberstalking takes on many forms, with all attempting to disturb, demean, or control the victim. Here are some common examples:
- Harassment. Sending constant offensive, suggestive, or threatening messages directly to the victim. It can either be sent via private messages or posted publicly on the victim’s social media profiles. Public slander of the victim can fall under harassment, too.
- Persistent following. Joining the same online groups or forums as the victim to keep tabs on their activities.
- Identity misuse. Setting up fake profiles to engage with or track the victim (often referred to as catfishing). This can also refer to stalkers who set up fake accounts to impersonate the victim, or situations where the stalker has managed to take over the victim’s real account. In both cases, the stalker can cause real harm to the victim’s life and career by posting whatever they like.
- Unwanted tagging. Excessively tagging the victim in unrelated posts, as well as commenting or liking every post they make.
- Explicit content. Sending or posting sexually explicit photos or attempting to extort such content from the victim. The latter is known as sextortion, which falls under the federal cyberstalking law In the US. In more recent years, cyberstalkers have also been using “deepfake” technology to digitally overlay the faces of the victim and their family onto explicit content, such as pornographic images or videos.
- Information exposure. Releasing the victim’s private information online (doxxing). This is usually done to get other online criminals to join in with the targeted harassment — the forum Kiwi Farms is well known for facilitating this.
- Physical intrusion. Sending unwanted gifts or ordering services (like tow trucks or food delivery to the victim’s home). Swatting is also possible, which is where the stalker makes an anonymous call to law enforcement regarding dangerous activity at the victim’s home address in the hope a SWAT team will breach the property.
- Digital spying. Compromising the victim’s device with stalkerware — malware that’s specifically for tracking and monitoring. Stalkerware may be sent via malicious links to the victim, or installed directly on their device if the stalker has physical access. Once the victim has been compromised, the stalker may be able to spy on the victim’s location, listen to call recordings, gain camera access, and more.
Examples of Cyberstalking
Cyberstalking has sadly touched the lives of many, including those in the public eye. Here are two high-profile instances that serve as stark reminders of the potential dangers in the online world:
1. Alec Baldwin and Genevieve Sabourin. In a case that grabbed headlines, Alec Baldwin, the renowned actor, became the victim of cyberstalking. Genevieve Sabourin, a Canadian actress, sent Baldwin numerous emails and text messages. These ranged from declarations of love to threats. Sabourin's obsession didn't stop at virtual communication, either. She attempted to confront Baldwin in person at his home and other public events, leading to her arrest in 2012.
2. Ashley Tisdale and Nicholas Fiore. Actress and singer Ashley Tisdale faced a harrowing cyberstalking experience when Nicholas Fiore bombarded her with over 18,000 tweets. He also sent her emails containing graphic songs and images. Believing the messages held threats against her life, Tisdale was granted a restraining order against Fiore in 2013.
Both examples underline the importance of recognizing the signs of cyberstalking and taking the appropriate actions.
Negative Effects of Cyberstalking
 Cyberstalkers can significantly impact your mental health
Cyberstalkers can significantly impact your mental health
Cyberstalking can lead to psychological, social, and physical consequences. Here's a look at some of its harmful impacts:
- Trust issues. Online stalking can lead a victim to believe everyone they run into online could be their stalker in disguise or someone doing their bidding.
- Cognitive impairments. A noticeable decline in concentration, memory retention, and decision-making skills often accompanies online stalking.
- Anxiety and depression. The relentless abuse can cause significant anxiety and depression, making daily life difficult. The victim may feel helpless, and it’s common for their self-esteem to plummet. In some cases, it can even lead to suicidal ideation.
- Post-traumatic stress disorder. Victims may develop PTSD, reliving the terror even without ongoing stalking.
- Social withdrawal. Out of fear or shame, victims may retract from social circles and become more distant with friends, partners, and family.
- Reputation damage. Slander, or the exposure of personal data, images, or videos, can severely tarnish the victim’s reputation. This could lead to the loss of relationships, jobs, and more.
- Sleep disorders. The constant worry can lead to insomnia or disrupted sleep patterns.
- Physical ailments. Headaches, stomach issues, muscle tension, and fatigue are common among victims.
- Physical harm. In extreme cases, digital stalking may transition to real-world stalking, directly threatening the victim's physical safety.
How to Prevent Cyberstalking and Online Harassment
Taking the right proactive steps is the most effective way to ward off cyberstalkers. In this section, I'll highlight practical measures you can take to protect your online presence and deal with potential threats:
1. Warn a Stalker About Criminal Responsibility
If you ever get unwanted messages or attention online, it's okay to nip it in the bud straight away. Tell the person clearly, "Please stop contacting me." And if they do keep bothering you, here's what you can do next:
- Tell the perpetrator that you feel you are in danger due to their persistent interactions. An explicit acknowledgment of threat is mandatory subjective corpus delicti (a necessary element of a crime).
- Notify the stalker about the criminal liability for cyberstalking and other forms of online harassment.
- Warn the perpetrator that you will report them to the authorities if the harassment continues.
- Document all communication (including your warning) in case legal action becomes necessary.
2. Change Your Email Address and Social Media Names
Cyberstalkers use social media and email to learn more information about you. Here are some tips to throw criminals off your trail and prevent them from stalking you:
- Create a separate email address and social media name for online interactions (that doesn’t provide personally identifiable information).
- Notify only trusted contacts about your online contact information.
- Delete or deactivate old accounts that may contain your personal information.
- Use email spam filters to minimize the possibility of email-based phishing attacks — your stalker may send scam emails in an attempt to trick you into handing over personal info.
3. Enable Strong Privacy Settings on Social Media
Tightening your privacy settings can make a significant difference in keeping unwanted eyes away from your personal content. For example, an estimated 63% of Facebook profiles are publicly visible, meaning anyone can access them. Don’t make it easy to cyberstalk you:
- Set your social media accounts to private or friends-only mode to limit who can see your content. Regularly review and update your privacy settings across all platforms you use.
- Enable two-factor authentication (2FA) on your accounts to improve security. It allows you to log in only after you enter a temporary unique code available only to you.
- Be cautious when accepting friend requests and ignore individuals you don't recognize. Accepting requests from unknown individuals can expose you to potential cyberstalkers.
- Limit who can post on your timeline and see your posts.
- Turn off displaying metadata on social media posts (like geolocations in your photos on Instagram).
- Disable tagging and mentioning your account in other people’s posts.
- Regularly review the list of people who follow you and remove or block any suspicious or unknown individuals.
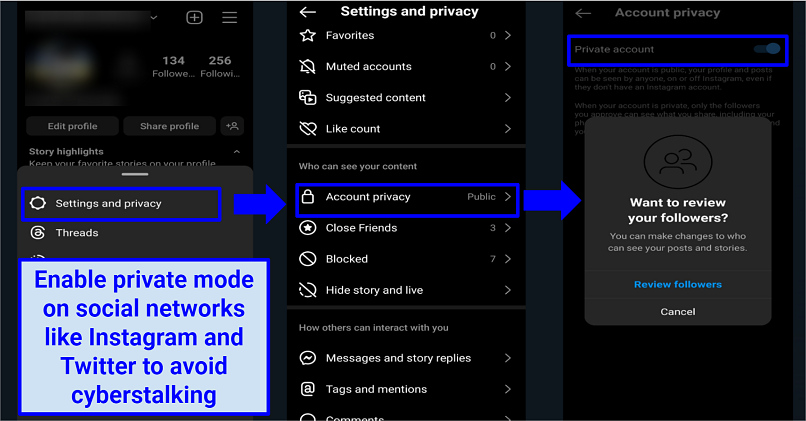 Instagram makes it easy to hide your account from strangers and to also verify followers
Instagram makes it easy to hide your account from strangers and to also verify followers
4. Set Online Calendar Accounts to Private
Online calendars can inadvertently disclose your daily routine and planned events to cyberstalkers. Protecting your online calendar is a step towards safeguarding your privacy.
- Set your calendars to private, ensuring only you or trusted individuals can view or edit them.
- Avoid sharing calendar links or invitations publicly or with individuals who don't need access to your schedule.
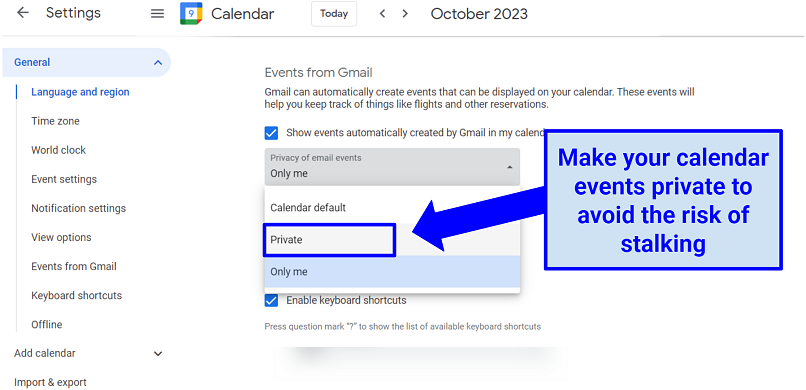 Google Calendar lets you share or restrict the visibility of your events
Google Calendar lets you share or restrict the visibility of your events
5. Change Your IP Address or Internet Service Provider (ISP)
Your IP address is a unique identifier online. Cyberstalkers may use the IP address to track your online activities. Changing it can disrupt their tracking efforts.
- Use different networks or devices to access the internet to alter your IP address.
- Contact your ISP for a new IP address if your geo-location was detected by a cyberstalker.
6. Avoid Suspicious Websites and Links
Some links and emails lead to fraudulent websites that harvest your data. They may also infect your device with malware or spyware that tracks your activities.
- Don’t open files or links in emails, direct messages, or comments (especially from accounts you don’t recognize).
- Check the names of the links (spelling errors or weird domain names usually indicate fraud).
- Look for a website via search engines instead of following a link. It’s better to Google a brand instead of clicking a URL in your message.
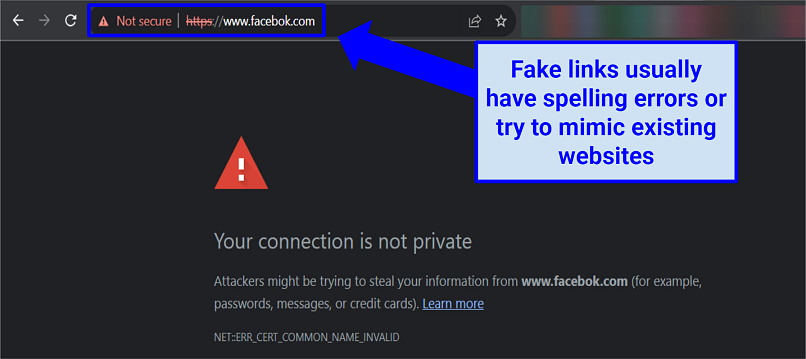 Another indicator of a potentially fraudulent website is the “HTTP” prefix, as opposed to “HTTPS”
Another indicator of a potentially fraudulent website is the “HTTP” prefix, as opposed to “HTTPS”
7. Use Strong Account Credentials and Passwords
Your online accounts are only as secure as the credentials guarding them. Strong, unique passwords can fend off hacking attempts from cyberstalkers.
- Use a mixture of uppercase, lowercase, numbers, and symbols in your online passwords. You can use secure password generators to create and store passwords that are difficult to hack.
- Avoid using easily guessable information such as your name, birthday, or common words as passwords.
8. Log Out From Your Accounts and Create a Password for Shared Devices
Staying logged in on shared or unsecured devices can expose your accounts to unauthorized access. Logging out and locking your devices keeps your digital life secure, as unattended devices can be infected with spying software.
- Log out of your accounts once you are done using them.
- Set up strong lock screen passwords on all your devices to prevent unauthorized access.
- Never leave your devices unattended in public places or at work.
- Ensure you have tracking enabled like Find My Device on Android or Find My on iOS, to locate or remotely wipe your device’s data if it's lost or stolen.
9. Avoid Apps That Ask for Unnecessary Permissions and Data
Some apps may request unnecessary permissions for their functionality, which cyberstalkers could exploit.
- Disable unnecessary permissions for apps, only allowing what's necessary for the app to function.
- Download apps from trusted sources and read reviews to estimate their safety.
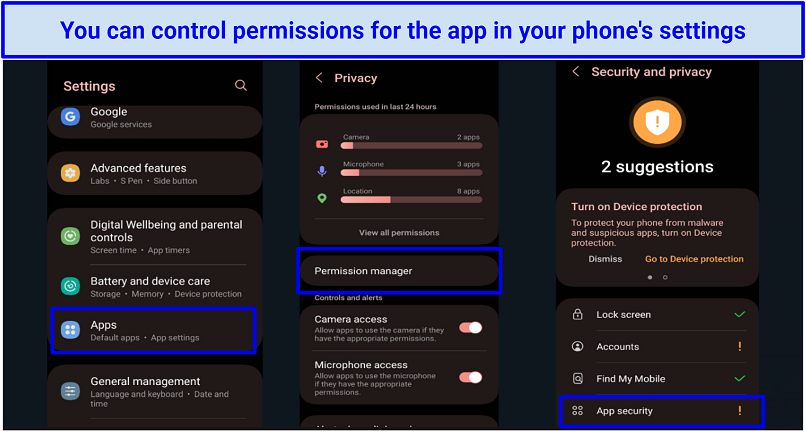 On Android, access the "Security and privacy" settings; on iOS, head to "Privacy & Security"
On Android, access the "Security and privacy" settings; on iOS, head to "Privacy & Security"
10. Regularly Update Antivirus and Malware Software
Up-to-date antivirus software can provide a shield against malicious attempts to infiltrate your devices.
- Regularly update your antivirus and anti-malware software to the latest versions.
- Schedule regular device scans to keep your devices free from malware and other security threats.
- Remove any suspicious programs or applications from your devices immediately upon discovery.
11. Use Secure Browsers and Privacy (Incognito) Mode
Secure browsing practices can thwart cyberstalkers' attempts to track your online activities.
- Opt for browsers with built-in security features like data encryption, ad blockers, and firewall protection.
- Use privacy (incognito) mode to prevent the storing of browsing history, cookies, and passwords.
12. Remove Your Personal Information From the Internet
Minimizing your digital footprint can be a strong deterrent for cyberstalkers searching for information about you.
- Regularly search your or your relatives’ names online to monitor the personal information available about you. You can check online people databases like Zabasearch, Spokeo, Pipl, Wink, and PeekYou, as well as social media sites like Facebook, X (formerly Twitter), and LinkedIn.
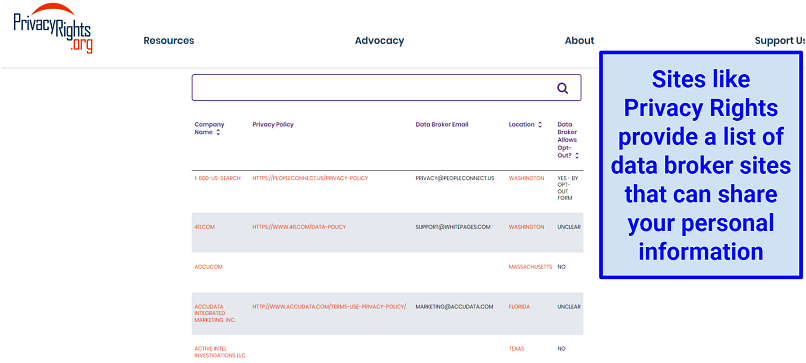
- Contact data brokers and other websites to remove your personal information from the internet. You can also use data removal services like Incogni.
- Prohibit data collection and ad sharing on social media, marketing associations, and other online services.
- Use tools like Google Help Center to delete your information from search engines and databases.
 You can search your name on Google, Bing, or Yandex to find sites with your sensitive data
You can search your name on Google, Bing, or Yandex to find sites with your sensitive data
How to Report Cyberstalking
If preventive measures don't suffice, understanding how to report cyberstalking becomes crucial to halt harassment. Learn the appropriate methods to record and address online stalking incidents.
1. Docment All Evidence of Harassment
It's crucial to not discard any form of interaction with the cyberstalker. Keeping a meticulous record of all harassment can significantly strengthen your case when reporting.
- Take screenshots of offensive messages, posts, or comments. You should also record conversations, if possible.
- Save all emails, messages, and any other form of communication with timestamps.
- Document the date, time, and context of each cyberstalking incident.
- Store all evidence securely, preferably physically and digitally (on cloud storage).
2. Report a Stalker to Social Media Platforms
Social media platforms have reporting mechanisms in place to handle harassment. Utilizing these can help put a stop to a cyberstalker’s malicious activities.
- Use the report feature on the respective social media platform to report inappropriate behavior or impersonating profiles. For example, Google has a support system in place for such cases.
- Block the cyberstalker on all platforms they use to contact or harass you online. If you have a website or blog, like WordPress, you can prevent a particular IP address from accessing it. Additionally, domain administrators can implement this block.
3. Notify Your Workplace or School
Notifying your workplace or school can provide you with a supportive environment and additional resources.
- Report the cyberstalking to the administration, like your workplace’s human resources department or school administration.
- Request support and assistance in dealing with the situation, ensuring your safety and privacy.
4. Contact the Complaint Centers and Help Agencies
Engage with the organizations and centers that can tell you how to deal with cyberstalking and connect you with professionals.
- Contact the Digital Security HelpLine for real-time assistance. They can help you find relevant organizations and mental health professionals.
- In the US, contact the National Center for Victims of Crime at 1-855-4-VICTIM (1-855-484-2846).
- Make a complaint with the IC3 (Internet Crime Complaint Center) under the “Other Cyber Crime” category to further document the cyberstalking incidents.
- Use the Cyberbullying Report for relevant contacts and guidance.
5. Inform the Police About Each Incident
Every incident reported provides a clearer picture of the harassment scale, aiding law enforcement in building a solid case against the cyberstalker.
- Contact emergency services if you or a loved one are in immediate danger due to cyberstalking.
- Keep a copy of the official report, noting the officer’s information for future reference.
- Report all online harassment incidents. Even if you don’t want to pursue charges, it can help other victims of the same cyberstalker and may make potential punishments more severe.
FAQs on Cyberstalking
What is the punishment for cyberstalking?
The punishment for cyberstalking depends on the jurisdiction and the nature of the offense. As an example, according to the US federal law (18 US Code §2261A), cyberstalkers face from 1 year in jail to life imprisonment. Factors that affect the severity of punishment include the degree of harm caused to the victim, duration of cyberstalking, and methods of harassment. Additionally, the penalties for stalkers of children are more severe.
However, the punishment for cyberstalking can greatly vary between jurisdictions. You should consult your local laws for a more accurate understanding of punishments regarding cyberstalking in your area.
Why is cyberstalking a crime?
Cyberstalking is a crime because it invades personal privacy and results in severe emotional and physical distress. It involves harassing, intimidating, or threatening a victim. The actions of cyberstalkers often escalate to offline stalking or physical harm. That’s why the punishment for online stalking in most countries is strict.
How can I identify someone’s actions as cyberstalking?
You can identify cyberstalking by common signs and patterns of behavior. This can include unwanted communication, persistent interaction on social media, online monitoring, impersonation, unwanted sharing of your information, and threats. The best way to stop cyberstalking is by taking immediate action and reporting the offender.
What is the difference between cyberstalking and cyberbullying?
Cyberstalking and cyberbullying are malicious online behaviors, but they differ primarily in intent and persistence. Cyberstalking involves persistent, unwanted attention towards an individual, often alongside surveillance and monitoring. You can prevent cyberstalking by following the best security and privacy practices.
Cyberbullying, on the other hand, is the use of electronic communication to bully someone. This might involve spreading rumors and making threats towards the victim, but not necessarily with the persistent harassment and monitoring often seen in cyberstalking.
Wrapping Up
Cyberstalking might sound like a plot from a sci-fi movie, but it's a real concern in our digital age. We've dived deep into what it means, looked at some eye-opening examples, and touched on the law's stance.
As you surf the web, chat with friends, or share your latest adventures, it's essential to stay aware and keep safety front and center. If you keep your online profiles watertight and proactively cut off those who give you a bad feeling, you’ll minimize your risk of cyberstalking.



Please, comment on how to improve this article. Your feedback matters!