What Is a Man in the Middle Attack & How to Prevent It
- What is a Man-in-the-Middle Attack & How Does It Work?
- How to Prevent a MITM Attack With a VPN
- Use a VPN Together With Other Security Measures to Prevent MITM Attacks
- Types of MITM Attacks
- Dangers of MITM Attacks
- How to Detect a Man-in-the-Middle Attack
- Real-World Examples of MITM Attacks
- Difference Between Man-in-the-Middle Attack and Other Cyberattacks
- FAQs on the Man-in-the-Middle Attacks
Man-in-the-middle (MITM) attacks are one of the most subtle and dangerous forms of cybercrime, having the potential to steal your personal data before you even realize you’re at risk. All it takes is to join a public WiFi network that’s been compromised by a hacker, or simply clicking the wrong link.
These attacks allow hackers to intercept and manipulate personal information and traffic data in real time, posing a serious risk to everything from personal messages to financial information. Understanding and preventing MITM attacks is essential to ensuring your privacy and security online.
What is a Man-in-the-Middle Attack & How Does It Work?
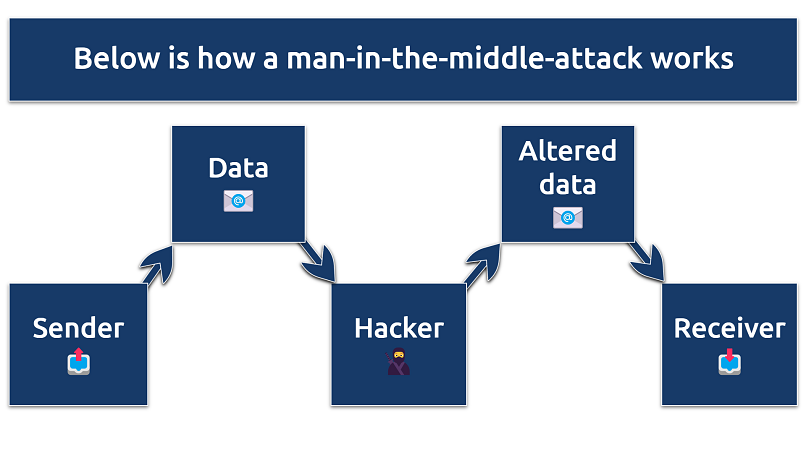
A MITM attack is a cyberattack in which a hacker secretly intercepts communication between two parties. It’s like eavesdropping, but worse — the attacker can not only listen in but also alter the information being shared. These attacks often target users of financial apps, SaaS platforms, and e-commerce sites.
 The hacker acts like a proxy between two parties
The hacker acts like a proxy between two parties
Here’s how a man-in-the-middle attack works from the hacker’s perspective:
- Interception phase. The attacker inserts themselves between two parties, often by exploiting weak or unencrypted networks. This could happen on unsecured WiFi networks, where attackers set up rogue access points (a faked version of the public WiFi network you can be tricked into connecting to) or use software to intercept data.
- Decryption (or data capture) phase. Once positioned between the sender and receiver, the attacker can capture sensitive information — like login credentials, credit card details, or personal messages. If the data is encrypted, some hackers may still be able to decrypt it if the encryption protocol is poor quality.
- Manipulation phase. In some cases, the attacker not only intercepts the data but also changes it. For example, they might alter transaction details (making themselves the recipient of sent funds, for example) or inject malware into a sent file.
All MITM attacks generally fall into two main categories based on how they interact with the communication between the victim and the intended server. Attackers can either actively interfere with the data exchange or passively observe the interaction to gather information without detection. These attacks are known as:
- Active session attack: In this approach, the attacker reroutes your traffic through a fake website before reconnecting you to your intended destination. For example, you might believe you’re accessing your bank’s website, but you’re actually viewing a spoofed version hosted on the attacker’s server. This method allows the attacker to collect or alter data in real time.
- Passive session attack: Here, the attacker monitors the data flow across the network without directly interfering with the communication. You may successfully connect to your bank’s website, but the hacker will quietly observe all incoming and outgoing data. This type of attack is harder to detect, as it relies solely on eavesdropping.
That said, these types of attacks often have many permutations as attackers adapt their techniques to exploit different technologies and security weaknesses. As a result, individuals and organizations must stay updated on emerging threats and strengthen their security measures against active or passive threats accordingly.
How to Prevent a MITM Attack With a VPN
A virtual private network (VPN) is one of the most effective MITM attack prevention tools. It encrypts data as it travels from your device to the VPN server, making it unreadable to unauthorized third parties. This encryption helps protect sensitive information, like login credentials, from being intercepted on unsecured networks (e.g., public WiFi).
Plus, by replacing your IP address, a VPN can reduce direct targeting by attackers who rely on IP-based methods to conduct MITM attacks. Below is a step-by-step guide to help you protect yourself against MITM attacks by using a VPN.
Step 1. Choose a Reliable VPN Provider
Step 2. Download and Install
Step 3. Connect to a Secure Server
Launch the app and sign in with the credentials you used during sign-up. Then, select a server location. For the best speeds, choose a server close to your physical location. Click the Connect button to establish a secure connection.
Step 4. Turn On Extra Security Settings
Step 5. Test Your Connection for Leak Protection
Visit an IP leak test site. For this test, I used our leak test tool to confirm that my actual IP address was hidden. This step is crucial to verifying that your VPN is working correctly and ensuring that no data is exposed to potential attackers.
Use a VPN Together With Other Security Measures to Prevent MITM Attacks
A VPN is an excellent tool for lowering the risk of MITM attacks on public or unsecured networks. By encrypting your internet traffic and hiding your IP address, it makes it significantly harder for attackers to intercept your data.
However, a VPN is even more effective when paired with other security measures that address two key requirements for protecting against MITM attacks:
- Non-repudiation: ensuring the message came from the claimed sender.
- Message integrity: verifying that the message hasn't been altered in transit.
To achieve these, consider implementing:
- HTTPS. TLS and HTTP work together to produce HTTPS, which provides encryption and non-repudiation. HTTPS offers secure connections to websites, ensuring both confidentiality and integrity of data.
- Digital signatures. Verify the sender's identity, supporting non-repudiation.
- Two-factor authentication (2FA). Adds an extra layer of account protection.
- Antivirus software. Helps detect and block malware or other threats.
- Strong WEP/WAP encryption. Implement robust encryption on wireless access points to prevent unauthorized users from joining your network and launching MITM attacks through brute-force methods.
- Strong router login credentials. Change default router login credentials (not just WiFi passwords). This prevents attackers from accessing your router settings, where they could change DNS servers to malicious ones or install malware.
- Public key pair based authentication. Use RSA or similar public key pair authentication across various network layers to verify that you're communicating with legitimate entities.
Make sure you also install software updates as soon as they’re available. Many MITM attacks exploit known vulnerabilities in outdated software. Keeping your OS and applications (especially browsers) up to date is crucial as these issues are likely fixed already.
Lastly, avoid unsafe WiFi whenever possible. Public WiFi networks are often a common starting point for MITM attacks. If you need to connect in public, use a secure VPN. By combining these tools, you can build a more complete defense against cyber threats.
Types of MITM Attacks
Here's an overview of the types and dangers of man-in-the-middle attacks:
- WiFi eavesdropping. Attackers intercept data transmitted over unsecured WiFi networks, particularly in public places. This vulnerability allows attackers to access sensitive information, such as passwords and personal data. They can achieve this through three main techniques: creating fake wireless access points with names similar to legitimate ones, exploiting wireless network vulnerabilities to compromise legitimate access points, or using rogue devices like smartphones to create deceptive hotspots that lure unsuspecting users.
- Email hijacking. Cybercriminals gain unauthorized access to email accounts, enabling them to manipulate communications. This can result in fraudulent transactions or the spread of malware.
- IP spoofing. Attackers send IP packets from a false (or "spoofed") source address to deceive the recipient into believing they are communicating with a trusted entity. This can lead to unauthorized access to systems and sensitive data.
- DNS spoofing. By corrupting the Domain Name System (DNS), attackers can redirect you to malicious websites instead of legitimate ones, facilitating phishing attacks or malware downloads.
- SSL stripping and hijacking. Attackers downgrade secure HTTPS connections to unsecured HTTP, allowing them to intercept sensitive information. SSL stripping can make you unaware of their compromised security.
- Session hijacking and cookie theft. Attackers capture session tokens or cookies to take control of your active session, granting them unauthorized access to accounts and sensitive information.
- ARP poisoning (ARP spoofing). By sending falsified Address Resolution Protocol (ARP) messages, attackers can associate their MAC address with the IP address of a legitimate device on the network, allowing them to intercept and manipulate traffic.
- Port stealing. Port stealing is an advanced attack targeting a LAN switch, where attackers configure a device to listen on the same port as a legitimate user, capturing and manipulating data packets. This exploits the switch’s Content Addressable Memory (CAM) table, which maps MAC addresses to specific ports, allowing attackers to disrupt communication flow on larger networks.
- Sniffing. This is a type of eavesdropping that captures and analyzes network traffic using tools like packet sniffers. It can be passive, where the sniffer only listens to traffic without making changes, or active, where it interacts with the network by injecting or modifying packets to gather additional information.
- Inelegant MITM attacks. These are less sophisticated techniques that may involve straightforward interception of communications without advanced tools. While they may be less stealthy, they can still lead to significant data breaches.
Advanced MITM Attacks
Here's an overview of the types and dangers of advanced MITM attacks:
- Reverse proxy credential harvesting. This method involves an attacker using a proxy to intercept and capture login credentials in real time. Tools like Evilginx and Modlishka are examples of reverse proxy techniques that trick you into logging into fake sites that closely mimic the real ones, allowing attackers to capture usernames, passwords, and session cookies.
- Car key fob interception. This is a specialized MITM technique targeting the wireless signals sent by key fobs to unlock or start vehicles. Attackers can use devices to intercept and replay these signals, gaining unauthorized access to vehicles. Car key fob interception is a growing concern for modern cars equipped with keyless entry features.
- IMSI catchers/stingrays. These devices impersonate cell towers, tricking nearby mobile phones into connecting to them. IMSI catchers, or Stingrays, intercept mobile data and can reveal your locations, intercept calls and messages, or even eavesdrop on conversations. While often associated with law enforcement, they can also be exploited for malicious purposes.
- Browser-in-the-Browser (BitB) attacks. This advanced phishing technique creates a fake, seemingly legitimate browser window within a website. Attackers can mimic common login pages, like those for Google or Microsoft accounts, making it highly convincing. You may unknowingly enter your login details, which are then captured by attackers.
- Man-in-the-browser (MitB) attacks. They involve installing malware, typically a Trojan horse, on the victim's computer. This malware can modify web transactions and alter the configuration and content of web pages without the user or online service noticing anything unusual.
- Evilginx attack. Evilginx is a sophisticated phishing technique that uses a reverse proxy to capture login credentials and session cookies. Attackers set up a proxy server that closely mimics legitimate websites, such as social media or email login pages. When you enter your credentials, Evilginx captures the data in real time, including any two-factor authentication tokens, allowing attackers to bypass standard security measures and gain full access to your account.
Dangers of MITM Attacks
Man-in-the-middle attacks pose significant risks, primarily through data and identity theft. Attackers can intercept sensitive information such as login credentials and financial data, enabling them to impersonate individuals and engage in fraudulent activities. This not only affects victims on a personal level but also can have broader implications, including legal issues for organizations.
Financial loss is a critical concern as attackers can access online banking and payment accounts, leading to unauthorized transactions and exploitation. Additionally, successful MITM attacks can inflict reputation damage on organizations, resulting in business sabotage and a loss of customer trust. Such breaches may also entail legal repercussions, further complicating the aftermath for affected entities.
Attackers can inject malware into data streams, compromising devices and networks. They can conduct ongoing surveillance to monitor the activities of targeted individuals or organizations, gathering sensitive information for future attacks. This level of network exploitation allows them to manipulate data flows and identify vulnerabilities, increasing the risk of prolonged surveillance, data theft, and additional attacks on users and connected devices.
How to Detect a Man-in-the-Middle Attack
MITM attacks can be difficult to detect because attackers aim to remain invisible while intercepting sensitive data. However, specific signs and methods can help identify potential MITM activity. Below are common indicators, possible MITM attack types, and recommended detection methods:
| Indicator | Potential MITM Attack Type | Detection Method |
| SSL/TLS warnings | SSL/TLS spoofing, HTTPS spoofing | Check for frequent SSL/TLS certificate warnings on trusted sites. Fake certificates can trigger these warnings. Monitor for the use of vulnerable SSL/TLS versions (e.g., TLS 1.0) that are susceptible to cyber attacks. |
| Slow internet speeds or frequent disconnections | General MITM | Be cautious if you experience frequent slowdowns or disconnections, especially on specific networks. MITM attacks may cause lag as your data is rerouted and/or stolen. |
| Unusual account activity | Account hijacking | Check account logs (e.g., email, banking) for unfamiliar locations or login times that may indicate unauthorized access. |
| Unexpected network traffic patterns | General MITM, ARP spoofing, DNS spoofing | Use IDS tools like Snort or Zeek to monitor for unusual IP patterns or data duplication. These tools can flag unusual IP addresses, ARP spoofing, or DNS anomalies, which can signal MITM attempts. |
| Duplicate MAC addresses | MAC spoofing | Use tools like arp -a or arp-scan to detect duplicate MAC addresses on the network. Attackers may use MAC duplication to mislead devices. |
| HTTP downgrade (HTTPS to HTTP) | SSL stripping | Monitor for websites loading as HTTP when they should use HTTPS (most browsers mark a site that isn’t using HTTPS as unsafe, but it’s better to double-check). |
| Unexpected pop-ups or software update requests | General MITM, malware injection | Watch for unexpected credential pop-ups while browsing, especially on sites that typically don’t request credentials. |
| Applications behaving differently or crashing | General MITM, malware injection | Watch for sudden changes in application behavior or stability. |
| Typos or altered communications | General MITM | Look for unexpected changes in the content of communication. |
| Increased latency or bandwidth utilization | General MITM | Monitor for unexplained increases in network latency or bandwidth usage. |
Real-World Examples of MITM Attacks
There are several well-known examples of MITM attacks. The incidents below highlight how quickly and cleverly MITM attack methods can evolve, adapting to new security challenges:
- 2011 — DigiNotar, a Dutch certificate authority, issued security certificates for various websites. However, fraudulent certificates had been created for numerous sites, including Google, enabling a man-in-the-middle attack that targeted Iranian citizens. The hacker, known as Comodohacker, was never identified. This breach led to major browsers rejecting DigiNotar certificates, resulting in the company's closure.
- 2013 — Edward Snowden disclosed that the NSA conducted MITM attacks to intercept internet traffic and introduce malware into systems using Tor and Firefox.
- 2015 — Lenovo’s PCs were discovered to have Superfish adware pre-installed, which tampered with SSL certificates to show pop-up ads. This created serious security risks, forcing Lenovo to issue quick patches and recall affected products.
- 2015 — A British couple lost £340,000 after a MITM attack intercepted their property sale payment and redirected it to the hacker’s account.
- 2017 — Equifax had to retract its mobile app after a data breach exposed that it transmitted data over HTTP instead of HTTPS, allowing hackers to access sensitive customer information.
- 2019 — In this ultimate MITM attack involving a Chinese venture capital firm and an Israeli startup, hackers stole $1 million by intercepting and altering their email exchanges. Cybercriminal groups Lunar Spider and Wizard Spider collaborated using malware to weaken security measures and facilitate fraudulent transfers.
- 2020 — Kodi Media Center, a popular open-source media player, became a target for MITM attacks through its add-on ecosystem. Attackers exploited Kodi's unencrypted update process to intercept and alter add-on content. This allowed them to distribute malicious code, potentially turning users' devices into parts of botnets for DDoS attacks.
- 2023 — Researchers at Eurecom discovered new MITM attack techniques labeled BLUFFS (Bluetooth Forward and Future Secrecy). These techniques exploit vulnerabilities in Bluetooth versions 4.2 to 5.4, allowing hackers to impersonate devices and decrypt communications.
Difference Between Man-in-the-Middle Attack and Other Cyberattacks
This comparison highlights how MITM attacks fit into the broader landscape of cybersecurity threats while also illustrating their unique characteristics.
MITM vs DDoS
A Man-in-the-middle attack involves intercepting and manipulating communications between two parties without their knowledge, allowing the attacker to eavesdrop, alter messages, or impersonate one of the parties.
In contrast, a distributed denial-of-service (DDoS) attack aims to overwhelm a targeted server, service, or network with a flood of traffic, rendering it unavailable. Unlike MITM attacks, which involve intercepting and altering communication, DDoS attacks focus on disrupting services by overloading them with traffic.
MITM vs Evil Twin
Evil Twin attacks are a specific type of MITM attack in which the attacker sets up a rogue WiFi access point that appears legitimate. By unknowingly connecting to this fake network, you allow the attacker to intercept all communications exchanged over it.
MITM vs Replay Attack
A MITM attack involves intercepting and potentially altering communication between two parties. A Replay attack, however, captures valid data transmissions and retransmits them to deceive the receiver into accepting them as legitimate. While both attacks involve interception, replay attacks specifically focus on reusing valid data rather than manipulating it in real time.
MITM vs Session Hijacking
Session hijacking is a specific form of MITM attack where the attacker takes over an active session by stealing session tokens or cookies. This tactic is a targeted approach within the broader category of MITM attacks.
MITM vs On-Path Attack
An on-path attack refers to a broader category that includes MITM attacks but doesn’t always imply active interception or message manipulation. In on-path attacks, the attacker is situated along the communication path and may use a range of techniques, including passive monitoring as well as more direct forms of interception.
MITM vs Phishing
While MITM attacks intercept legitimate communications, phishing attacks typically involve creating fake websites or emails to trick users into revealing sensitive information.
MITM vs APT
MITM attacks and Advanced Persistent Threats (APTs) differ in focus and scale but can be connected. MITM attacks intercept and alter communications to steal data in real time, typically being short and targeted. APTs, on the other hand, are long-term, stealthy campaigns aimed at deeply infiltrating a network. MITM attacks often serve as a starting point for APTs, providing stolen credentials or network insights to help attackers gain access. Protecting against MITM attacks is crucial to prevent more advanced threats like APTs.
FAQs on the Man-in-the-Middle Attacks
Can HTTPS prevent all MITM attacks?
HTTPS can’t prevent all MITM attacks. While it encrypts data in transit and verifies the server's authenticity, attackers can still employ techniques like SSL stripping or evil twin attacks, which downgrade or intercept connections before they are secured.
Who are the three main participants in a man-in-the-middle attack?
The three main participants are the attacker, the victim (client), and the legitimate server. The attacker intercepts the communication between the victim and the server, often impersonating one party to manipulate the information exchanged.
What is the difference between man-in-the-middle and meet-in-the-middle?
Man-in-the-middle refers to an attack where an intruder intercepts communications between two parties. Although various MITM attacks sound similar, they target different vulnerabilities. In contrast, meet-in-the-middle is a cryptographic attack technique that searches for matching values in the middle of an encryption process to help recover the plaintext or encryption keys.
Can I use a free VPN to protect from a MITM attack?
Maybe, but it’s not advisable. A free VPN can encrypt your internet traffic and provide some protection against MITM attacks. However, you’re better off using a premium VPN with a money-back guarantee. Free VPNs pose risks, such as data logging and unreliable privacy policies, which could compromise your security. Plus, many free VPNs don’t work on more niche operating systems, like Kali Linux.





Please, comment on how to improve this article. Your feedback matters!