Free VPN Data Breach Exposed 360 Million Records Online. Why Using the Right VPN Matters!

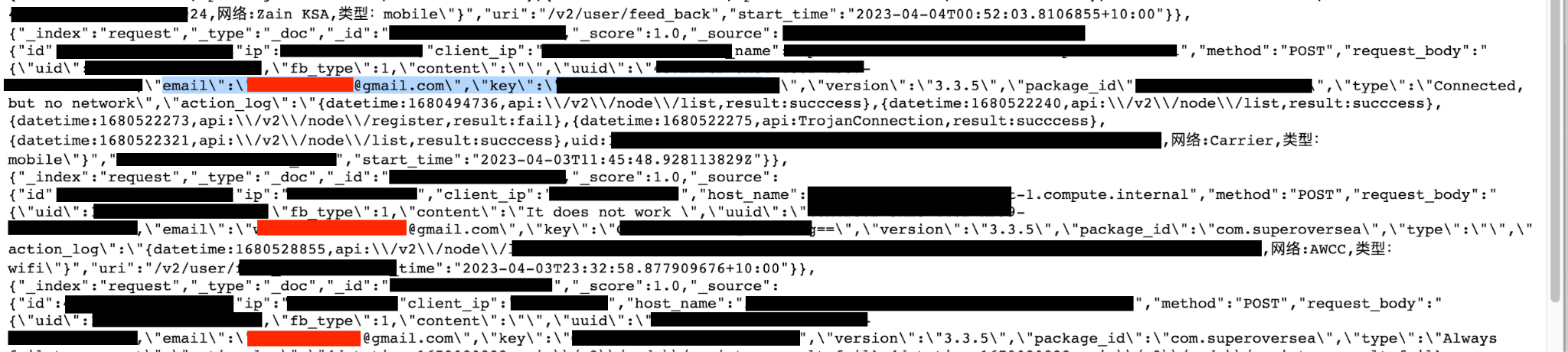
Cybersecurity security researcher Jeremiah Fowler discovered and reported to vpnMentor a non-password protected database containing over 360 million records related to a VPN data breach. The publicly exposed records contained email addresses, device information, and even references to sites that the user visited.
Nearly all of the records in the database mentioned references to SuperVPN, an application that advertises a free to download VPN service. There are two (2) apps named SuperVPN available officially on both the Apple and Google application stores. According to the Google app store page, they have a combined 100 million downloads worldwide.
After reviewing a limited sample of records, I sent a responsible disclosure about the exposure to all available email addresses associated with both apps. The database was subsequently closed although I never received any reply. This incident serves as a wake-up call for anyone who uses a VPN to understand why choosing a trustworthy and reputable service is important for your privacy in more ways than just your internet activities.
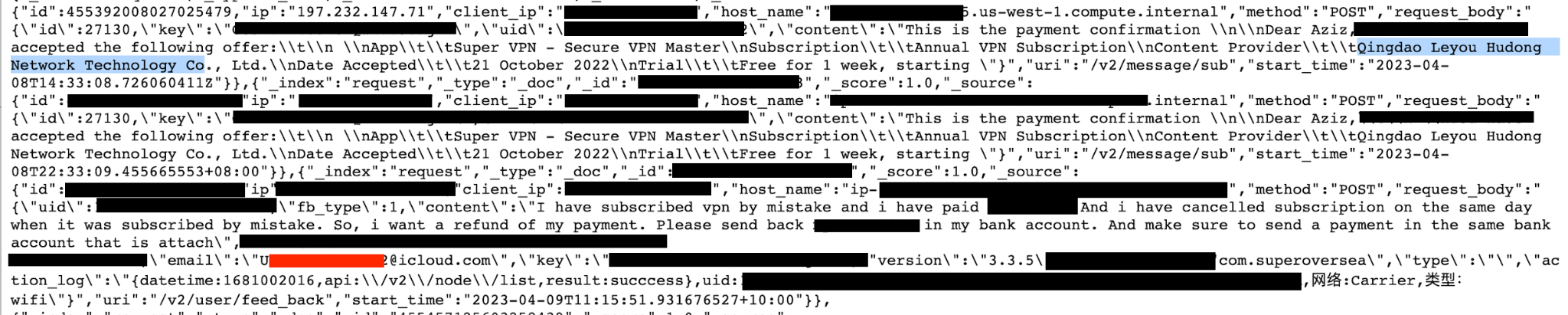
I observed many refund requests and paid-account details in the records, which makes sense since the Super VPN I assume was leaking offered paid subscription after a free trial. Notably, the two apps named SuperVPN are listed under separate developers on both Google Play and Apple’s app store. SuperVPN for iOS, iPad, and macOS are credited to developers Qingdao Leyou Hudong Network Technology Co., whereas the second app of the same name is developed by SuperSoft Tech. I also found references to a company named Changsha Leyou Baichuan Network Technology Co. within the database and mentions of Qingdao Leyou Hudong Network Technology Co.. All appear to have connections to China, and notes inside the database were in the Chinese language.
All indications point to Qingdao Leyou Hudong Network Technology Co. as the owner of the database and I cannot confirm if there is a connection to SuperSoft despite the many similarities. The logos of both companies are very similar, particularly the logos of SuperVPN for Mac and SuperVPN for other iOS devices. I reached out to both companies for further confirmation to determine if they are connected or share the same developer. However, I never received a reply or comment on my discovery. Neither company provides much information about their ownership or location on their websites, which has raised concerns about the transparency and security of these free VPN services.
What the leak exposed:
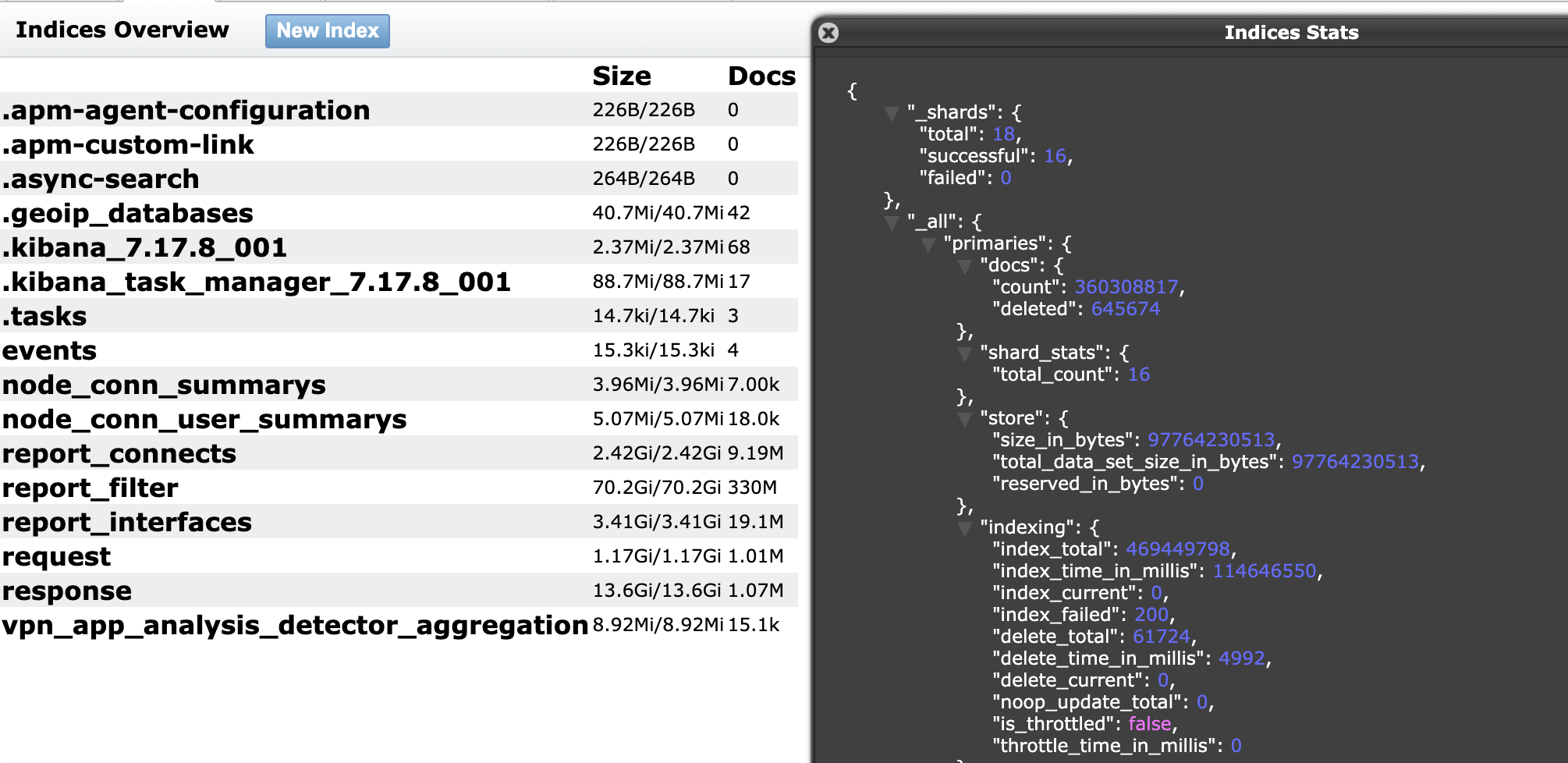
- 360,308,817 total records exposed with a size of 133 GB.
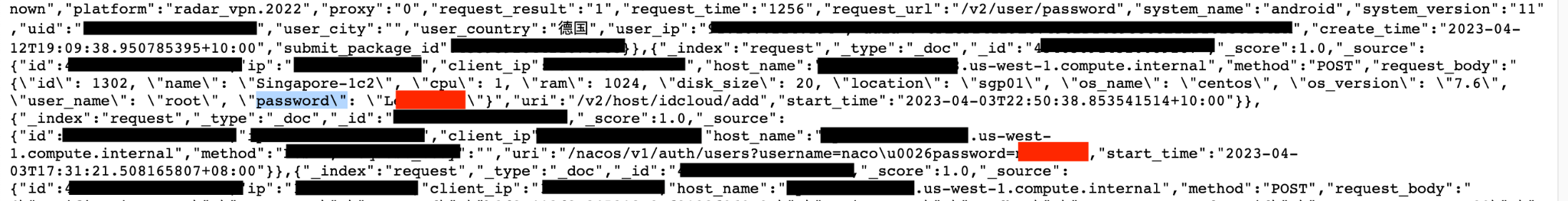
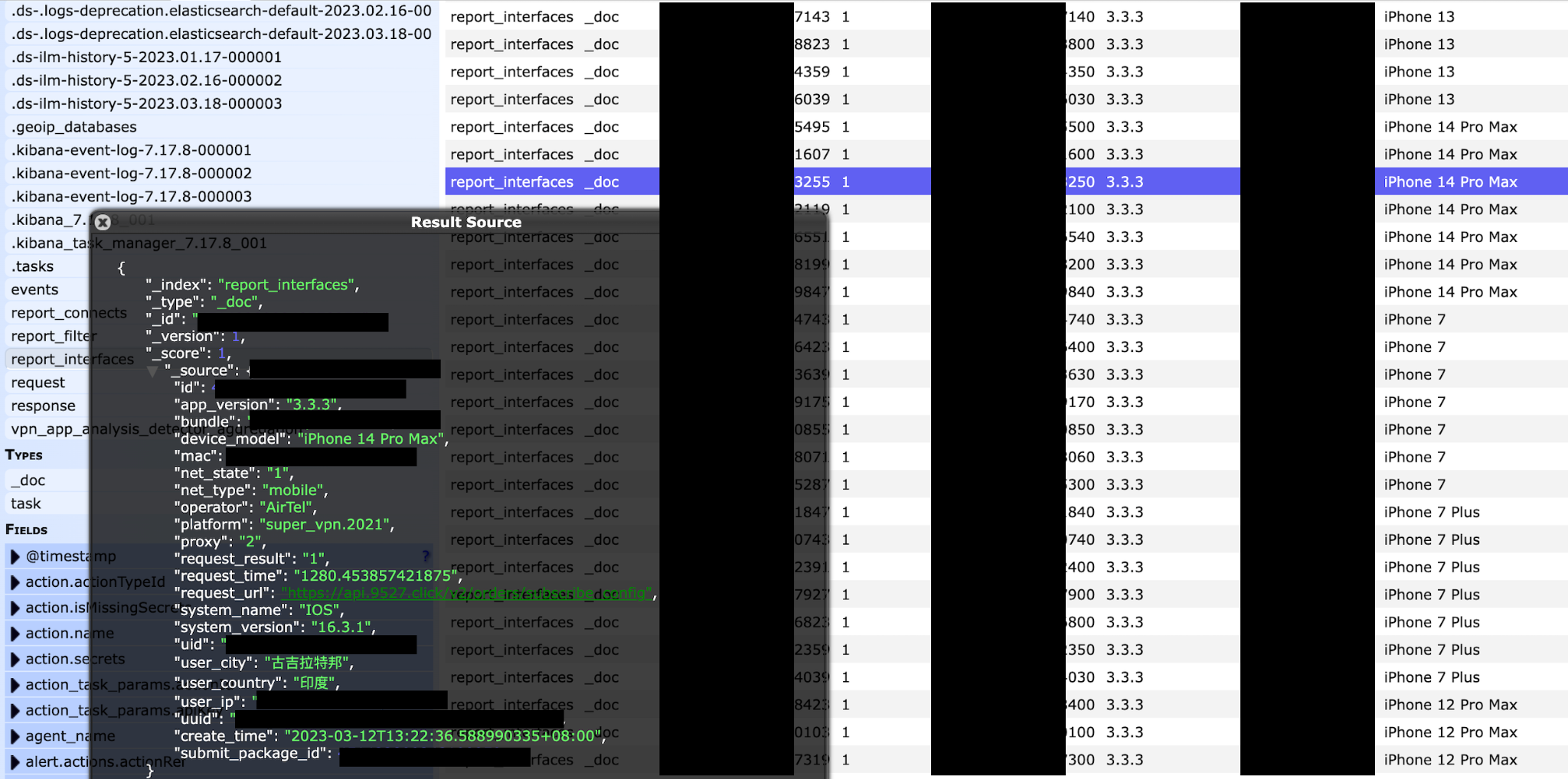
- The records contained sensitive information, including user email addresses, original IP addresses, geolocation, and records of servers used. Additionally, the records also contained what appeared to be secret keys, Unique App User ID numbers and UUID Numbers (a Universally Unique Identifier is a 36-character alphanumeric string that can be used to identify further information).
- Additional information in the records included phone or device model, operating system, internet connection type, and VPN application version.
- Refund requests from users who either purchased the product or were charged.
- Links to websites that the app users visited could identify their activity and be a privacy threat to the users who expect a reasonable degree of security.
The same Super VPN’s customer support emails were also linked to Storm VPN, Luna VPN, Radar VPN, Rocket VPN and Ghost VPN (not to be confused with CyberGhost VPN). In addition, references to these VPN provider names were found inside the database. At this point, it is not possible to determine if these VPNs are owned by the same company, yet I can assume they are somehow related. According to the customer support page of the app developed by Qingdao Leyou Hudong Network Technology Co.: “SuperVPN keeps no logs which enable interference with your IP address, the moment or content of your data traffic. We make express reference to the fact that we do not record in logs communication contents or data regarding the accessed websites or the IP addresses”. However, this data exposure appears to contradict this privacy guarantee. It should be noted that the application permissions allow the VPN to access the device’s files, images, and other device information.
In 2020, security journalist Zak Doffman reported about SuperVPN (the one developed by SuperSoft, I cannot know if related to the one leaking) to Forbes: “The issue was a security vulnerability a Chinese developer had repeatedly failed to fix—a vulnerability that exposed users to critical man-in-the-middle attacks. That risk has now been mitigated. But for those with the app—SuperVPN—installed on their phones, you should delete it right away." - Quote from the article.
The Risk of a VPN Data Breach
While VPNs are designed to afford users a greater degree of privacy and security when using the web, they are not immune to security vulnerabilities and can be subject to breaches. A VPN creates a secure and encrypted tunnel between your device and the VPN server, which helps to protect your online activities from prying eyes. However, if the VPN provider employs weak encryption methods, possesses security flaws, or lacks proper security measures, it can expose users' sensitive information and lead to a data breach.
Additionally, if the VPN provider collects and stores user logs, it can compromise user privacy if those logs are leaked or misconfigured for public access. In this case, we can clearly see how a VPN data breach could potentially reveal sensitive user data, including login credentials, email addresses, browsing history, IP addresses, and other information about the user or service. This could subject the affected users to a wide range of potential problems such as unauthorized use of their credentials, spam or phishing attempts. Additionally, the IP address can be used to identify the approximate geographic location of a user and may also provide information about the user's internet service provider (ISP) and the type of device they are using. A cyber criminal could then use that information to launch a denial of service (DoS) attack.
If you're concerned about your privacy and want to reduce your chances of being affected by a data breach, it is important to choose a reputable VPN provider that uses strong encryption methods, has a transparent privacy policy, and regularly updates its security protocols.
China-Based VPN Services
I saw users from around the world in the records and although these users are not located inside of China any VPN based in China could have potential security risks. China has strict regulations on internet usage and controls the flow of information within its borders. The Chinese government censors and monitors internet activity, including social media, online messaging, and websites. As a result, many people in China use Virtual Private Networks (VPNs) to access restricted content and protect their online privacy. In recent years, the Chinese government has introduced measures to regulate the use of VPNs.
In 2017, the government announced that all VPN providers operating in China must be licensed by the government. This led to many VPN providers being forced to shut down, while the remaining providers are required to comply with strict government regulations. While VPNs are still used in China, they are not as readily available or as reliable as they once were. Additionally, the government continues to monitor VPN usage and has been reported to take action against individuals who use VPNs to access restricted content. Therefore, anyone who uses a VPN in China should exercise caution and use a reputable provider. The same potential privacy concerns extend to all users of Chinese-based VPN services.
The terms of service also outlined troubling restrictions that users must accept in order to use SuperVPN. These include potentially ambiguous and broad blanket prohibitions such as “subverting state power, undermining national unity or undermining social stability and / or damaging the honor and interests of the State” and “destroying the state's religious policies and propagating cults and feudal superstition”. These actions can be interpreted subjectively, and the statements are vague enough that many actions could potentially be considered against the law.
Red Flags to Consider When Selecting a Free VPN Service
- Unclear phrasing on what data the VPN collects and what it's used for: It’s crucial to verify that the service does not log your internet activity. The VPN provider could collect and sell your data to advertisers or other third-parties.
- No "Who We Are" / ”About Us” section on the VPN’s official website: This makes it tricky to know who is behind the company, which means you don't know who is handling your data. Also, pay attention to where the company is based; certain countries are known for internet censorship (like China or Iran) or surveillance (like the US, the UK, and other members of the Fourteen Eyes alliance).
- No DNS-leak protection: When there’s a DNS leak, your ISP (and potentially other prying eyes) can easily see your online activity even though you're using a VPN. In other words, the VPN isn’t protecting your privacy.
- The VPN offers anything other than 128-bit or 256-bit AES encryption: Using a weak or no encryption means a greater risk of prying eyes tracking your online activity and accessing your data.
- Poor reviews: Make sure to read the reviews other users have left on the app, especially the negative ones. It’s good practice to see what others have complained about. Also, check out what review sites have to say about that particular VPN service.
By doing your research and taking these factors into consideration, you can choose a free VPN that best fits your needs while also protecting your online privacy and security. I recommend that users ensure that apps are downloaded from sites with a https:// and valid SSL certificate. If a VPN app has no dedicated website or no information on who the developers are or this information seems to be hidden it is a potential risk. Where the VPN is located can also be a risk.
We do not insinuate nor imply any wrongdoing by the developers of the SuperVPN app or any of the other service names listed inside the database. We publish our findings to raise awareness of cyber-security issues and data-privacy protections and only state the facts of the discovery and potential real world risks of the exposure. Users should always be aware of security concerns with the applications and services that they use. It is crucial to note that observations drawn in this article are based solely on a limited sampling of available data. We strongly advise users to exercise due diligence and discretion when selecting applications and services. It is always recommended to read and understand the terms of service, privacy policy, and any other related user agreement of any service you opt to use.



Please, comment on how to improve this article. Your feedback matters!