The Ultimate Guide to VPN Tunneling & How To Use It In 2024
- What is VPN Tunneling?
- What Should I Look for When Choosing a VPN?
- What Is Split Tunneling All About?
- What Do I Need to Know About Tunneling Protocols?
- What Are the Different VPN Tunneling Protocols?
- Point-to-Point Tunneling Protocol (PPTP)
- Layer 2 Tunneling Protocol (L2TP)/Internet Protocol Security (IPSec)
- Internet Key Exchange (IKEv2)/Internet Protocol Security (IPSec)
- Secure Socket Tunneling Protocol (SSTP)
- OpenVPN
- The 3 Best VPNs that Use Tunneling
- ExpressVPN
- CyberGhost
- PrivateVPN
- Concluding Remarks
You may have heard that Virtual Private Networks (VPNs) use a process called “tunneling” to extend a private network across a public network (the internet). Tunneling is the process of encrypting data and keeping it separate from other traffic on the internet. It enables a VPN to protect the confidentiality (data remains secret) and integrity (data remains unaltered) of messages as they travel over the public network.
But how does the tunneling process actually work? And does it really keep your online activity safer?
For starters, the best way to protect your data would be to never transmit it through the public network in the first place, but you know that’s nearly impossible. That is why we rely on a VPN to enhance our privacy while we engage in online activities.
What is VPN Tunneling?
The term VPN tunneling describes a process whereby data is securely transported from one device or network to another through a non-secure environment (such as the internet) without compromising privacy. Tunneling involves protecting data by repackaging it into a different form.
In reality, no physical tunnel exists, of course; the data has to travel through the same wires as any other data passing through the public network. Rather, VPN tunneling employs the concepts known as data encapsulation and encryption to safely carry data traffic through the non-secure environment. Encapsulation insulates the packet of data from other data traveling over the same network, while encryption makes the data “invisible” (unreadable) even to surveillance agents and criminals who recognize it as encrypted information. So it’s like the data is traveling inside a tunnel. Figure 1.0 below might help you visualize the process.
You can think of VPN tunneling as similar to the process of moving physical cash from one bank location to another using an armored transport van along public highways. The cash in this instance is your data, the public highway is the non-secure public network, and the armored van is analogous to a VPN tunnel (data encapsulation and encryption).
Even if sophisticated spy agencies and skilled criminals recognize the armored van and its contents, they can’t break into it. So there are actually two levels here – encapsulation disguises the van so in most cases it won't be recognized as a vehicle carrying cash, while encryption ensures that even if the van is recognized, no one can reach the cash inside.
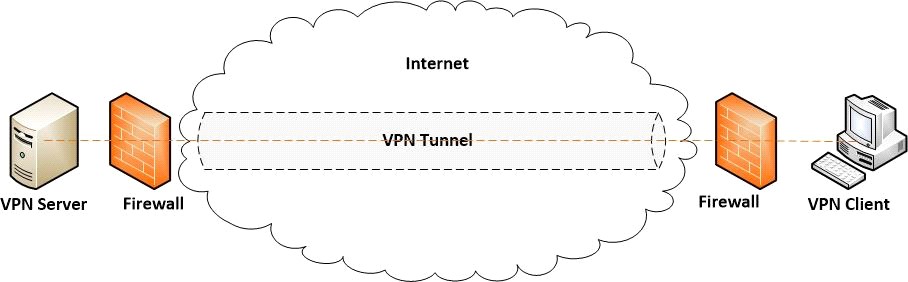 Figure 1.0 VPN Tunneling Diagram
Figure 1.0 VPN Tunneling Diagram
To sum up, encryption makes your readable data (plaintext) completely unreadable (cipher text) by any person that intercepts it, while encapsulation wraps data packets with successive layers of control information so that in most cases it won’t even be recognized as encrypted data. VPN tunneling employs these techniques to obscure your data in order to keep your browsing activities private and confidential.
What Should I Look for When Choosing a VPN?
When choosing a VPN, it’s important for you to consider how you intend to use the service, and which tunneling features are best suited for that use. The table below summarizes some the most popular VPN uses and the corresponding tunneling features to look for. In turn, the features available to you will be determined by which tunneling protocols the VPN offers. Protocols are discussed in detail in the sections to follow.
| VPN use | Most important tunneling feature to have | Why is this important |
| Online streaming | Speed and ability to bypass blocking software | Minimize buffering and remove content access restrictions |
| Accessing banned websites | Security with strong encryption | Evade surveillance and bypass content restrictions (censorship) |
| Cloaking VoIP calls | Security with strong encryption | Evade surveillance |
| Public WiFi use | Security and privacy | Protect data that would otherwise be visible to any user of the shared network (WiFi networks are very poorly secured) |
| P2P file sharing | Security and privacy | Evade surveillance, especially tracking of data transmissions |
| Combating ISP bandwidth throttling | Speed | Minimize constant buffering |
| Mixed uses | Ease of switching between different protocols | Want to be able to choose the best protocol for each use |
| Multitasking, including local and remote uses | Split tunneling (detailed explanation below) | Simultaneous access to your local ISP and the VPN server without interruptions |
There are other advanced VPN features that are essential to the effectiveness of tunneling, such as a kill switch and split tunneling.
A kill switch is a mechanism setup to regularly monitor your connection for any changes in status. If it observes any disconnection from your VPN server, it automatically stops your device or terminates specific apps from connecting to the internet through your ISP so that your data and activity are not exposed to prying eyes.
There are times when you do not need all your data traffic to go through your VPN tunnel, however. That’s where the concept of split tunneling comes into play.
What Is Split Tunneling All About?
Split tunneling basically enables you to route some of your online activities through the VPN tunnel while you directly access the internet through your ISP for others. Why is this important?
One of the main functions of a VPN is to provide you a secure and private channel to send and receive information anonymously. But the truth is, not everything that we do on the internet needs to pass through a VPN tunnel. For example, there are times when you want to access foreign movies on a streaming service like Netflix and at the same time access local web services. When the protection of tunneling is not needed, a VPN can be a bottleneck that slows down your connection.
Or suppose you want to carry out online banking activities while also maintaining access to web services in other countries that require VPN use. Changing your IP address (and apparent location) using a VPN could be flagged as suspicious activity by your bank, which could actually lead to more invasions of your privacy.
In such cases, split tunneling lets you gain access to web services for which you want or need the protection of tunneling, without losing direct access to local web services. Otherwise, you would find yourself continually connecting and disconnecting from your VPN service. Besides, split tunneling will help you conserve a lot of bandwidth, as your internet traffic does not all have to pass through the VPN server.
Fortunately, most highly rated VPN service providers include a split-tunneling feature within their apps.
What Do I Need to Know About Tunneling Protocols?
Most VPN providers give users the option to choose from several tunneling protocols. The VPN tunneling protocol you select to use has significant implications for the quality and performance of your tunnel. Some key questions to ask before choosing a tunneling protocol include:
- How fast is it?
- How secure is it?
- How easily can it transverse (get past) blocking software?
- How easily can I access and use it?
Because your choice of tunneling protocols can be critical, it is important that you have a good understanding of the various protocols so you can make an informed choice.
What Are the Different VPN Tunneling Protocols?
A VPN tunneling protocol is an agreed-upon set of rules for data transmission and encryption. Some of the most commonly used protocols include Point-to-Point Tunneling Protocol (PPTP), Layer Two Tunneling Protocol (L2TP), Internet Protocol Security (IPSec), Secure Socket Tunneling Protocol (SSTP), and Open VPN (SSL/TLS).
Point-to-Point Tunneling Protocol (PPTP)
PPTP was developed by a group of vendors led by Microsoft and has been implemented in Microsoft operating systems since Windows 95. PPTP supports site-to-site as well as remote access VPN over the internet.
PPTP is therefore one of the oldest, fastest, most widely used, and easiest-to-setup VPN tunneling protocols. It is easy to configure because it requires only a username, password, and server address to establish a tunnel to the remote server. It’s one of the fastest protocols because of its low level of encryption. For that reason, PPTP is useful for applications in which speed is more important than complete security.
If security is your main concern, however, you should be aware that many serious security vulnerabilities have been found in PPTP. Most networks that use PPTP have to apply additional security measures to make up for the protocol’s security lapses. Unfortunately, doing so means that you to some degree lose the benefits of the protocol. We therefore recommend PPTP only in cases where legacy support is required and security isn’t a priority.
Layer 2 Tunneling Protocol (L2TP)/Internet Protocol Security (IPSec)
The L2TP tunneling protocol does not provide data confidentiality by itself, but instead relies on another protocol to wrap the data again, creating two layers of encryption to protect data going through the tunnel.
Because of its lack of complete confidentiality, L2TP is often used in combination with Internet Protocol Security (IPSec) to create a more secure tunneling protocol than PPTP. This combination is referred to as L2TP/IPsec.
However, the double encapsulation process makes L2TP/IPsec a little slower than PPTP. It can also struggle with bypassing restrictions because it uses fixed ports that VPN-blocking software can detect, making connections with L2TP easier to block. Many content providers like Netflix use VPN blockers nowadays, so if you use a VPN to access content in other countries, a tunneling protocol that makes you vulnerable to blocking might be a problem.
Internet Key Exchange (IKEv2)/Internet Protocol Security (IPSec)
To be precise, IKE is not actually a tunneling protocol. However, since it functions like one, we have included it here.
Generally seen as an improvement upon the L2TP protocol, IKEv2 uses some of the most sophisticated encryption methods currently available. It is also significantly faster than L2TP and allows for swifter and easier reconnection after a service interruption.
Like L2TP, IKEv2 is usually used in combination with IPSec. Its primary advantages are speed, stability, and ease of use. Its major drawback is that like L2TP, it is fairly easy to block.
Secure Socket Tunneling Protocol (SSTP)
Secure Socket Tunneling Protocol (SSTP) was developed by Microsoft to help protect your online activities. It is supported by default on Windows 7, 8 and 10 platforms, making it easy for Windows users to set up. It transports internet data using the Secure Socket Layer (SSL) – the same protocol used to power secure web connections (HTTPS).
SSTP employs robust encryption methods, positioning it as the most secure VPN protocol accessible by default in Windows systems. It can be used as an alternative to PPTP or L2TP/IPsec. SSTP's advantage over PPTP and L2TP is its resilience to easy blocking, as its traffic is transmitted via the widely-used HTTPS web connection.
This is good news for those who use VPNs to access content like Netflix in other countries. However, because SSTP is a proprietary Microsoft technology, it is difficult to perform independent examinations of the codes behind the protocol to identify potential flaws.
OpenVPN
OpenVPN is VPN tunneling protocol developed using open-source software (software with codes that anyone can inspect). It uses the well-known Secure Socket Layer (SSL) encryption protocol to ensure that all data traffic passed between your device and any other user’s device or any website remains private. It also supports a great number of other strong encryption procedures.
OpenVPN is fast and capable of traversing VPN-blocking software. Because of the open source nature of the protocol, security experts have been regularly combing it for potential security flaws and making improvements, boosting user confidence in the protocol.
Although not included by default, Open VPN is supported on Windows, Mac, and Linux operating systems, but requires third party client software to configure it. However, if you subscribe to a reliable VPN service provider, you won’t need to worry about all the configuration hassles, as OpenVPN will be readily available for use once you install the VPN app.
Table 1.0 below provides a detailed comparison of the various tunneling protocols.
Table 1.0 Comparison of VPN tunneling protocols
|
VPN Tunneling Protocol |
|||||
| Features | PPTP | L2TP/IPSec | IKEv2/IPSec | SSTP | Open VPN |
| Ease of setup | Very easy | Easy | Easy | Easy | Tricky on its own, but easy if you use a good VPN |
| Stability | Struggles with most blocking software | Struggles with most blocking software | Struggles with some blocking software | Bypasses most blocking software | Bypasses most blocking software |
| Encryption | Basic | Strong | Very strong | Very strong | Very strong |
| Speed | Fast | A bit slow | Fast | Fast | Best performance |
| Security | Not secure | Secure but may be breakable | Very secure, but users are not free to access the codes to verify security claims | Very secure, but users are not free to access the codes to verify security claims | Very secure, and anyone is free to access the codes to verify security claims |
| Compatibility | Window, Mac OS, Linux, etc. | Window, Mac OS, Linux, etc. | Window, Mac OS, Linux, etc. | Windows only | Window, Mac OS, Linux, etc. |
The 3 Best VPNs that Use Tunneling
Now that you understand what VPN tunneling is, how it works, and why it’s so important, you know a lot about what separates the best VPNs from all the rest. At vpnMentor, we research and test hundreds of VPNs to determine which ones will keep you and your data protected while delivering the speed and content access you want. Here are our choices for the best available VPNs.
1. ExpressVPN

Tested April 2024
We have spent hours testing this VPN’s claim of being the fastest premium VPN in existence, and it has never let us down. That’s just one of many reasons why users rate ExpressVPN so highly, even though it costs a little more than other VPNs. Features like military-grade encryption and an automatic kill switch prove that this VPN didn’t achieve its speed by sacrificing privacy protection.
- Supported protocols: PPTP, L2TP/IPSec, SSTP, Open VPN
- Split tunneling: Yes
- Kill Switch: Yes
- Free Trial: Yes, mobile apps only
- Money-back guarantee: 30 days
2. CyberGhost
Best known for its intuitive, easy-to-use interface that users of all levels of experience love, CyberGhost also delivers fast, reliable connections through an extensive global server network. A verified no-log policy and an option to purchase a subscription anonymously with digital currency are just two of the many ways CyberGhost safeguards user privacy.
- Supported protocols: PPTP, L2TP/IPSec, Open VPN
- Split Tunneling: No
- Kill Switch: OpenVPN protocol only
- Free Trial: Yes, seven days with some access limitations
- Money-back guarantee: 45 days
3. PrivateVPN
PrivateVPN has climbed up the VPN ranks by providing excellent network speed and reliability along with some unique features, including a Team Viewer option that allows you to work directly with the provider’s tech team during setup. However, general customer service is neither as responsive nor as knowledgeable as it is with the VPNs listed above. Still, PrivateVPN remains a strong user favorite.
- Supported protocols: PPTP, L2TP/IPSec, IKEv2/IPSec, Open VPN
- Split Tunneling: No
- Kill Switch: Windows only
- Free Trial: Yes, seven days, but must obtain a gift code from customer service
- Money-back guarantee: 30 days
Concluding Remarks
A VPN relies on the concept of tunneling to protect your privacy by hiding your internet activity from your ISP and spying agencies, while also helping you navigate to blocked websites. The degree of protection, speed, and ability to get past blocks and restrictions depends greatly on your choice of tunneling protocol.
Among all the tunneling protocols, Open VPN is the most highly recommended, especially for anyone with serious security concerns. Its open source code, stability, strong encryption, and ability to bypass blocking software make it the finest tunneling protocol currently available, and one you can trust.
Finally, we should add that selecting a VPN with secure tunneling protocols is just one of many steps you should be taking to protect yourself online. See our complete guide to protecting your online privacy for more helpful tips to stay safe on the internet.
Your data is exposed to the websites you visit!
Your IP Address:
Your Location:
Your Internet Provider:
The information above can be used to track you, target you for ads, and monitor what you do online.
VPNs can help you hide this information from websites so that you are protected at all times. We recommend ExpressVPN — the #1 VPN out of over 350 providers we've tested. It has military-grade encryption and privacy features that will ensure your digital security, plus — it's currently offering 49% off.
Leave a comment

Thanks for submitting a comment, %%name%%!
We check all comments within 48 hours to ensure they're real and not offensive. Feel free to share this article in the meantime.



Please, comment on how to improve this article. Your feedback matters!