How to Bypass Netflix VPN Blocks and Errors in 2025
- How Do You Avoid Netflix VPN Detection?
- How To Get Past the Netflix VPN Blocks and Errors? 12 Ultimate Tips
- Best VPNs for Bypassing Netflix VPN Blocks in 2025
- Our Methodology for Testing VPNs for Bypassing Netflix VPN Blocks
- Why Does Netflix Block VPNs?
- Types of Netflix VPN Blocks
- Popular Netflix VPN Errors and Solutions
- FAQs on How To Bypass Netflix VPN Blocks
Getting blocked by Netflix when you're using a VPN shouldn't happen — after all, you've paid for both services. Netflix's VPN detection is ruthless, though, instantly blocking your connection and hitting you with that annoying proxy error message. And once you're blocked, good luck trying to watch anything until you figure out a workaround.
How do you bypass Netflix VPN blocks? Often, the solution is simpler than you'd think. Switching to a different server or clearing your cache might do the trick. But when those quick fixes fail, you'll need a VPN that's specifically built to outsmart Netflix's detection system.
ExpressVPN is my go-to for bypassing Netflix VPN blocks, as it requires no configuration. Your VPN use is automatically hidden with obfuscation on all servers. Plus, it’s one of the fastest VPNs, letting you enjoy shows without buffering from anywhere. It also has a 30-day money-back guarantee*, so you can get a full refund if you’re not 100% happy.
How Do You Avoid Netflix VPN Detection?
- Download a VPN. I recommend ExpressVPN because it consistently works with Netflix without getting blocked. It also has fast speeds, a large server network, and a 30-day money-back guarantee.
- Connect to a server. Nearby servers usually offer faster speeds for seamless streaming.
- Start watching. Log in to your Netflix account, and start streaming in HD from anywhere.
How To Get Past the Netflix VPN Blocks and Errors? 12 Ultimate Tips
1. Use a Premium VPN That Actually Works
Netflix uses advanced detection systems that analyze traffic patterns and behavior to spot VPN connections. Free VPNs are usually the easiest to be detected. According to a report by NordVPN, 40% of Americans still use free VPNs despite their limitations1. Some free VPNs might occasionally work with Netflix, but they rarely maintain secure access — which explains the frequent proxy errors you may encounter.
The VPNs that consistently work with Netflix, like ExpressVPN, are the ones that actively fight these blocks. They regularly refresh their IP addresses, maintain a large server network to spread user traffic, and implement advanced features to avoid detection. Some even dedicate specific servers just for Netflix, constantly monitoring and updating them when Netflix's blocks improve.
2. Switch to a Different Server
Netflix keeps track of and blocks IP addresses associated with VPN use. When too many users connect from the same IP address or if Netflix detects suspicious traffic patterns, it adds that IP to its blocklist. This is why you might suddenly get the proxy error even if your connection was working earlier.
In 2021, Netflix started blocking residential IP addresses that showed VPN-like patterns. According to a report by Ars Technica, even regular users who weren't using VPNs got blocked and couldn't access their accounts, which shows just how far Netflix will go to stop VPN usage2.
That’s why it’s important to choose a Netflix VPN with a large server network. If you find the server you’re connected to is blocked, you can switch to a different one. Your VPN will assign you a new IP address that might not be in Netflix's blocklist yet. The best VPNs regularly add new IP addresses, so keep trying different servers until you find one that works.
3. Clear Cookies and Cache
Your cookies and cache store login information and other data from previous sessions. Netflix uses various browser data to detect VPN usage. If you’re browsing with a different IP within a short time frame, that might trigger security protocols on a website and get you blocked. However, you can easily prevent this by connecting to different servers.
Here's how to clear your browser data in Chrome:
- Open Chrome and click the three dots in the top-right corner.
- Click More Tools > Clear browsing data.
- Select Last hour or Last 24 hours in the time range.
- Check Cookies and site data and Cached images and files.
- Click Clear data.
You can also use your browser's incognito mode while connected to your VPN.
4. Change VPN Protocols
If you’re still getting an error, switching protocols might help. VPN protocols handle your connection differently, and some are better at avoiding detection than others. OpenVPN, WireGuard, and IKEv2 are common options, while some VPNs offer their own protocols, like Lightway (ExpressVPN) or NordLynx (NordVPN).
Most VPNs let you change protocols in their settings menu. While the automatic setting usually picks the best protocol for your connection, manually trying different ones can help fix the Netflix error.
For example, OpenVPN TCP on port 443 often works well because it disguises VPN traffic as regular HTTPS traffic, making it harder for Netflix to detect. Keep experimenting with different protocols until you find one that works.
5. Use Obfuscation
Obfuscation is a feature that disguises your VPN traffic as regular internet traffic. How does it help avoid Netflix detection? Simply put, it scrambles your data in a way that makes it much harder for Netflix to identify VPN patterns.
Not every VPN offers this feature, but those that do might call it Stealth mode, cloaking, or Camouflage mode. Some VPNs like ExpressVPN offer obfuscation that kicks in automatically when the app detects restrictions.
Enable obfuscation before connecting to Netflix if your VPN offers it. This extra layer of protection can often bypass blocks even when other methods fail.
6. Use a Different Browser
Every browser handles VPN connections differently and stores various types of data that can reveal VPN use. Browser fingerprinting is one way Netflix can detect VPNs — it collects details about your browser setup and compares it against your location data to spot inconsistencies.
Switching browsers gives you a fresh start with different privacy settings and data handling. Chrome typically shares more data that could reveal VPN use, while Firefox and Brave are designed with stronger privacy protections that might help avoid Netflix VPN detection.
7. Disable IPv6
While most VPNs encrypt IPv4 traffic, many devices automatically send IPv6 requests that might not be properly protected. This creates a mismatch between your IPv4 and IPv6 addresses, making it easy for Netflix to spot VPN use. When you disable IPv6 on your device, all your internet traffic is forced through IPv4, which your VPN can properly protect.
8. Use Smart DNS
Smart DNS replaces the DNS address provided by your ISP with one for a different server. It’s usually designed with streaming in mind, plus it’s a bit faster than a standard VPN connection as it doesn't encrypt your traffic. All the VPNs on my list offer Smart DNS (ExpressVPN calls it MediaStreamer).
9. Try Desktop Instead of Mobile
The Netflix mobile app has stricter VPN detection than the browser version. Mobile apps can access your device's GPS, network information, and other identifiers that aren't available to browsers. They can also detect VPN apps running on your device.
The browser version of Netflix has more limited access to your system information and relies mainly on IP-based detection. This makes it easier to bypass blocks when watching Netflix through a desktop browser with your VPN enabled.
10. Get a Dedicated IP
When you use a regular VPN connection, you share IP addresses with other users. Netflix easily spots this because hundreds of accounts try to stream from the same IP address — something that wouldn't happen from a regular home connection. A dedicated IP address solves this by giving you an address that only you use.
How can you bypass Netflix’s password-sharing restrictions? Well, a dedicated IP address can help with this, too. Netflix now tracks your home location and limits streaming to specific households. A dedicated IP creates a consistent access point that looks like a regular home connection, making it much harder for Netflix to detect.
11. Check Network Admin Settings
Network configurations can interfere with how your VPN connects to Netflix. Corporate firewalls, school network restrictions, or even home router settings might force your traffic through specific routes or block VPN protocols. This can create conflicts that make Netflix more likely to detect your VPN.
Check your router and network settings for any VPN restrictions or forced traffic routing. If you're on a managed network (work, school, etc.), the network administrators might have policies that affect VPN connections.
12. Contact Your VPN’s Support
When nothing else works, your VPN's support team can provide specific solutions. They constantly monitor which servers and configurations work best with Netflix and can guide you through advanced troubleshooting steps.
Most premium VPNs have 24/7 support teams that deal with Netflix blocks daily. They can recommend working servers, help you configure optimal settings, or provide custom solutions based on your specific situation.
Best VPNs for Bypassing Netflix VPN Blocks in 2025
After extensive testing of over 50 VPNs, we’ve identified the providers that consistently bypass Netflix's VPN blocks. These VPNs regularly update their servers to avoid detection, maintain fast speeds for buffer-free streaming, and offer secure access to Netflix from anywhere.
1. ExpressVPN — Most Reliable Netflix VPN With Fast Speeds to Stream in UHD

Tested July 2025
ExpressVPN is the most reliable VPN for bypassing Netflix blocks. During our tests, we could securely access 15+ Netflix libraries, including the US, UK, Japan, and Canada, without encountering any proxy errors. The VPN regularly refreshes its IP addresses, so you can stream Netflix consistently with ease.
The VPN delivered impressive speeds in our testing, so you can stream Netflix in HD or 4K from anywhere. On local servers, we only experienced a 3% speed loss, which is impressive considering many VPNs had a drop of over 30% on similar connections. This let us stream Don’t Move in HD without any buffering. ExpressVPN's proprietary Lightway protocol and extensive server network help maintain these fast speeds.
The only drawback is that this VPN costs a bit more than the other services on this list. However, ExpressVPN frequently offers great deals that make it more affordable. You can test ExpressVPN risk-free since it’s backed by a 30-day money-back guarantee. Plus, it offers a 7-day free trial.
- One of the fastest VPNs
- Works with top streaming sites
- A proven no-logs policy
- Limited customization
- Smart Location isn't always the fastest
2. CyberGhost — Netflix-Optimized Servers for Reliable Connections
CyberGhost makes streaming Netflix easy with its specialized streaming servers. These servers are regularly updated to bypass Netflix's VPN blocks and are clearly labeled by which Netflix library they can stream. During our tests, CyberGhost’s streaming servers worked as intended, and we never experienced any problems while streaming over a dozen libraries. Plus, the speeds were fast enough for 4K streaming from anywhere.
One downside is CyberGhost's expensive monthly plan, which also comes with a shorter 14-day money-back guarantee. However, the long-term offers are much more affordable and include the full 45-day refund period.
- Secure access to streaming
- Military-level security
- Designed for ease of use
- Slower long-distance servers
- Doesn't work in China
3. NordVPN — Advanced Obfuscation to Get Around Netflix VPN Blocks
NordVPN's obfuscated servers make it an excellent choice for bypassing Netflix VPN errors. These servers scramble your metadata and mask VPN traffic patterns, making your connection look like regular HTTPS traffic to Netflix. In our tests, NordVPN worked with 12+ Netflix libraries without any proxy errors.
The only issue is that the app can be slow to launch, sometimes taking up to 30 seconds to start up. But once you're connected, there are no issues — we streamed Netflix in HD without any buffering or disconnections. You can test all of NordVPN's features risk-free with its 30-day money-back guarantee.
- Strong security and privacy
- Fast local and faraway servers
- Great for streaming
- Some long connection times
- High renewal prices
Our Methodology for Testing VPNs for Bypassing Netflix VPN Blocks
We rigorously test each VPN's ability to bypass Netflix's detection systems across multiple regions. This involves connecting to different servers throughout the day to monitor how consistently they work with the platform. Plus, we check how quickly providers respond when Netflix blocks their IPs. Our team also tests various features like obfuscation and specialized streaming servers to see which ones effectively avoid detection.
In addition, we conduct comprehensive speed tests to ensure these VPNs can handle Netflix streaming. Using servers from different locations, we measure connection speeds, check for buffering during HD and 4K playback, and verify if the VPNs maintain stable connections throughout entire shows. For complete transparency about our testing process, you can check out our VPN testing methodology page.
Why Does Netflix Block VPNs?
Netflix blocks VPNs primarily due to licensing agreements with content creators. These agreements restrict where shows and movies can be streamed, as content rights are often sold separately in different regions. If Netflix didn't block VPNs, they could face legal issues and fines for breaching these contracts.
When Netflix detects VPN use, you may see a variation of the following error codes (M7037-1111, M7111-5059, or M7111-1331-5059) and be temporarily blocked from accessing the service.
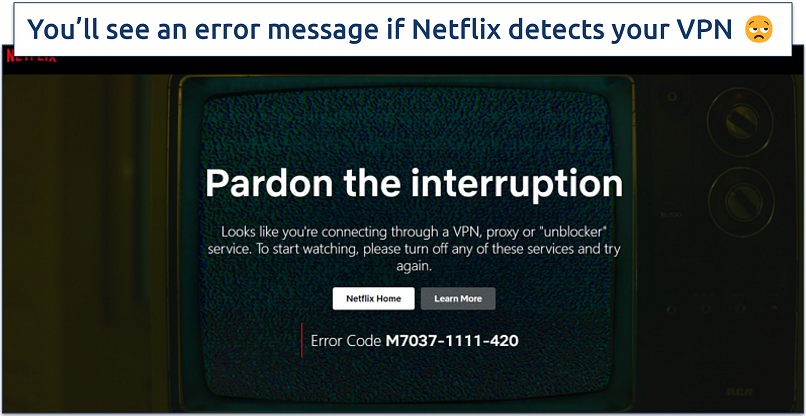 Netflix immediately detected a free VPN we used for testing
Netflix immediately detected a free VPN we used for testing
Beyond licensing, Netflix might also block VPNs to protect against fraud and account abuse. VPNs can be used to exploit regional price differences, where users might subscribe from a country with lower prices while watching from elsewhere. Netflix also needs to prevent automated bots that use VPNs to create fake accounts or attempt unauthorized access.
Types of Netflix VPN Blocks
Netflix uses several methods to detect and block VPN connections. Here are the main techniques it uses to identify when someone is watching its content through a VPN:
IP-Based Blocking
Netflix maintains a database of known VPN IP addresses. When you try to watch Netflix using one of these IPs, you'll get blocked instantly. The platform regularly updates this database by identifying IPs that show patterns typical of VPN use.
Traffic Pattern Detection
Netflix analyzes how traffic flows through its network. When it spots patterns characteristic of VPN connections, like multiple users sharing the same IP or unusual routing patterns, it blocks that connection.
DNS-Based Detection
Even if your VPN hides your IP address, Netflix can detect VPN use through mismatched DNS requests. If your DNS server location doesn't match your IP location, Netflix will block the connection.
Other detection and blocking methods, like port blocking or deep packet inspection, are typically associated with corporate networks and government firewalls rather than streaming services. Netflix focuses primarily on IP-based detection and traffic analysis, as these methods are most effective for its needs.
Popular Netflix VPN Errors and Solutions
In addition to the errors mentioned above, you might encounter other common issues when using a VPN with Netflix. Let’s take a look at some of these errors and how to resolve them:
M7111-1331-5059: "Pardon the Interruption"
As mentioned above, this error occurs when Netflix detects a VPN connection. The solution is to use a reliable VPN. If the issue persists, clear your browser cookies and cache, then restart your browser to fix this.
22004: "This Title Is Not Available to Watch in Your Area"
If you see this error on iOS, it usually means you're in a country where the title you've downloaded isn't available due to regional licensing restrictions. To resolve it, you’ll need to connect to the internet in a country where the title is available, which is often the country where you downloaded the content.
UI3012 and NW-2-5: "Netflix has encountered an error"
These network-related errors can indicate issues with your VPN connection. If Netflix works without the VPN, contact your VPN provider for troubleshooting, as the issue is likely on their end.
Netflix Originals
Netflix might limit your viewership to Netflix Originals if it detects VPN use. This is because Netflix owns global rights to these titles and doesn't need to block them based on your location. To resolve this, try connecting to a different VPN server that the platform hasn’t detected.
Incorrect Password Error
Sometimes, Netflix may display an "Incorrect password" error even when your login credentials are correct. This typically happens when Netflix blocks the IP address of the VPN server you're using. To solve this, either switch to a different VPN server or, if you're using a less reliable VPN service, consider upgrading to a better-rated provider.
FAQs on How To Bypass Netflix VPN Blocks
How do I know Netflix has detected my VPN?
Netflix shows specific error messages when it detects VPN use. You'll usually see: Looks like you’re connecting through a VPN, proxy, or unblocker service. When this happens, you won't be able to play any content until you either disconnect your VPN or switch to a server that isn't blocked.
Sometimes, Netflix might not show an error message but will only display Netflix Originals content even when connected to a VPN.
Is using a VPN with Netflix legal, or will I get banned for using one?
Using a VPN is legal in most countries, and Netflix won't ban your account just for using one. While Netflix actively blocks VPN connections to comply with its licensing agreements, it typically just shows an error message asking you to turn off your VPN. There haven't been any reported cases of Netflix permanently banning accounts for VPN use.
The only exceptions are restrictive countries (like China and Saudi Arabia) where VPN use is heavily regulated or banned altogether. It can be illegal to use one in such countries. We don’t condone illegal activities, so please check your country’s local laws regarding VPN/site use to avoid facing consequences.
Can I bypass Netflix VPN blocks with a free VPN?
It’s very unlikely since most free VPNs have small server networks and don't have obfuscation. In addition, they usually have slow speeds and data restrictions (usually only 1 or 2GB per month), making it impossible to stream Netflix for long. A premium VPN with a money-back guarantee is a more reliable option.
On top of this, many free VPNs can be dangerous — some have untrustworthy privacy policies, while others have weak security because they don't have the means to upgrade their software often enough. Some free VPNs also come packaged with malware that can harm your device.
Will a VPN help me bypass Netflix password-sharing restrictions?
NordVPN offers a feature called Meshnet that could theoretically get around Netflix's Password-sharing ban. You can use Meshnet to connect two devices so that both have the same IP address, so it appears they’re in the same location. However, vpnMentor is against this. Still, NordVPN is one of the best VPNs for streaming Netflix without interruptions.
References
- https://nordvpn.com/blog/nordvpn-usage-survey
- https://arstechnica.com/gadgets/2021/08/netflix-is-adding-residential-ip-addresses-to-its-vpn-blocklists/
Your online activity may be visible to the sites you visit
Your IP Address:
216.73.216.208
Your Location:
US, Ohio, Columbus
Your Internet Provider:
Some sites might use these details for advertising, analytics, or tracking your online preferences.
To protect your data from the websites you visit, one of the most effective steps is to hide your IP address, which can reveal your location, identity, and browsing habits. Using a virtual private network (VPN) masks your real IP by routing your internet traffic through a secure server, making it appear as though you're browsing from a different location. A VPN also encrypts your connection, keeping your data safe from surveillance and unauthorized access.
Leave a comment
sorry, but express vpn, I use a paid version, gets detected within a couple hours on Netflix. no matter what location I use.
Thank you for sharing your experience! While ExpressVPN is generally reliable for Netflix, occasional detection can happen due to Netflix's aggressive VPN-blocking techniques. Here are a few tips that might help:
1. Switch Servers Frequently: Some servers may be flagged; trying a different one can often resolve the issue.
2. Clear Cache and Cookies: Netflix may store location data in your browser or app. Clearing them can reset your session.
3. Use a Different Protocol: Switch to OpenVPN (TCP) or Lightway in ExpressVPN's settings for better obfuscation.
4. Contact Support: ExpressVPN's 24/7 support team often has updated server recommendations specifically for Netflix.
Let us know if these steps work for you!



Please, comment on how to improve this article. Your feedback matters!