VPN Leak Test: How To Check If Your VPN Works & How To Fix It
You might think that by using a popular and leading VPN solution you ensure that your IP address and online activities remain concealed. Unfortunately, even the priciest and most sophisticated VPN won’t protect you from IP leaks originating in your browser or operating system. To verify that your information and identity are indeed safely concealed, you need to check that your system is not vulnerable to IP or DNS leaks, and stop IP leaks you come across in your tests.
The Anatomy of DNS and IP Leaks
Every device on a network, including the Internet, has a unique identifier – its IP address (you can check your IP address using this tool). To allow servers to store more than one website, and to make it easier for users to access these websites by typing in words instead of numbers, DNS (Domain Name Service) servers translate strings of text (addresses) to numeric values (IP addresses) and different folders on the server.
When you try to access a specific website address, your browser requires a translation from the web-page URL to the numeric identifier (IP address) and destination folder on the specific server. A request is then passed to the DNS server that returns a valid destination for the file the browser will then load. This process is called DNS resolution.
The DNS server is chosen for resolution as a result of prioritization within the browser and operating system including browser configuration, local DNS server, the HOSTS file, Netbios, etc. This hierarchical choice of server is important when discussing IP privacy and security.
When using virtual private networks (VPN) to secure your connection, the DNS resolution should take place on the servers configured by your VPN provider. Unfortunately, this is not always the case.
When the DNS resolution is performed on a different server, it is possible to determine the IP address from which the DNS resolution request originated – your IP address. Thus, using a VPN for online anonymity and privacy becomes futile. Similarly, if a third party can eavesdrop on your DNS requests (think of a man-in-the-middle attack), they can capture your information even if you use a custom (and secure) DNS server. One way to prevent that is to use DNSCrypt, encrypting the traffic from your system to the DNS server. However, this does not protect your IP address from leaking.
How to Detect a Leak
Before we discuss the causes and types of common leaks, it’s important to know how to check if your system is vulnerable.
There are many available websites and services online that can quickly test whether your system is leaking your DNS traffic or IP address. If you don’t already have a favorite IP leak testing tool, you can check your connection security with our IP Leak Test Tool.
No matter what tool you use, the steps are pretty identical:
- Disconnect your VPN client and point your web browser to the testing website.
- Make note of your public IP and DNS server address displayed.
- Connect your VPN client and go to the same website. Make sure to refresh the page.
Once connected to a VPN, the website should not display your previously noted IP or DNS server. If it does, you are suffering from a privacy leak in your system.
As you can see in the screenshot below, since there is nothing shown in the public IP address section, it is safe to say that my IP and DNS information is secure.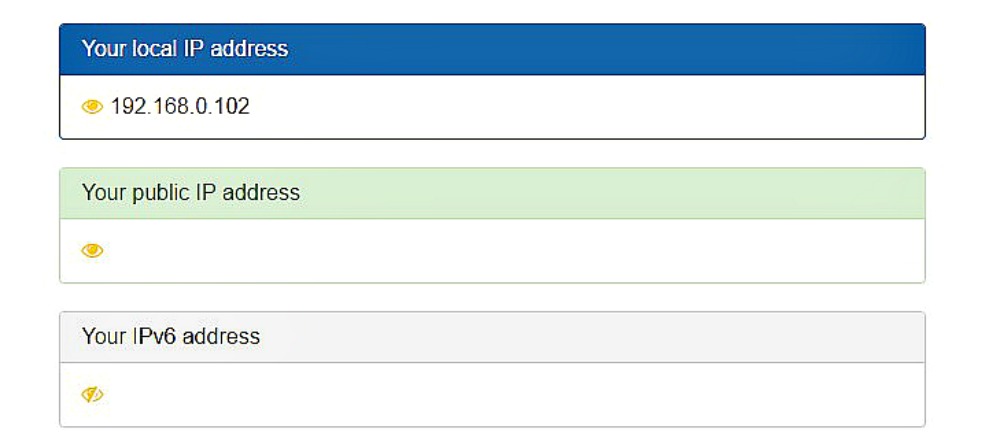
However, if you’ve tested your VPN connection using our IP leak detection tool and found that your VPN doesn’t quite anonymize your web access, below are the most common causes (and fixes) to the leak in your privacy.
1. Browser IP Leaks
A prevalent reason behind IP leaks is a browser vulnerability associated with the usage of WebRTC. WebRTC is an application programming interface (API) that enables web-based applications, such as chat and peer-to-peer file sharing, to operate without the need for installed extensions or plugins. However, this convenience does come with a drawback.
The browsers that support WebRTC – like Chrome and Firefox – utilize a STUN server (Session Traversal Utilities for NAT) to obtain an external network address. A website that wants to know your real IP address can very easily conceal a piece of Javascript code to make UDP requests to this STUN server, which would then route these requests to all the available network interfaces.
In this situation, both your real IP address and VPN IP address can be exposed, and it’s worryingly easy to embed such a code in a supposedly innocent website. To make the situation worse, since these requests are not like typical HTTP requests, the developer console cannot detect them and so browser plugins cannot reliably block this kind of leak (even if they advertise such an ability).
The are two ways to prevent WebRTC from putting your privacy at risk:
- Set proper firewall rules that block requests made outside your established VPN connection.
- Disable WebRTC in the supported browsers. You can poke around your browser’s privacy settings, or simply Google “how to disable WebRTC”. There’s no shortage of tutorials and guides to help you.
2. IP address Leaking from the VPN
Even with a VPN connection active, you should never rely on the DNS server provided by your ISP because your privacy could be at risk. You can try using public DNS servers, such as the ones provided by Google, but if you are paying for a VPN service package, there is really no reason for it not to include secure DNS resolution on a dedicated server.
Another scenario in which your VPN service provider could be the culprit for a leak is when it doesn’t support IPv6. The IPv4 protocol, which uses 32 bits addressing, allows for up to 2^32 devices in the world to receive a unique public IP address. With the unprecedented growth of the internet, we began to run out of these addresses, so IPv6 was introduced. It uses 128 bits addressing so the number of available IP addresses is now 2^128 – a much higher number.
Unfortunately, the worldwide adoption of the newer IPv6 protocol has been too slow. Some major websites support both of these protocols and serve the appropriate channel as per the client system. The issue arises when a VPN service provider doesn’t support IPv6 and instead of addressing the problem, just blindly ignores it.
When using such an out-of-date VPN service, websites supporting IPv4 alone are safely accessible using the VPN. However, for IPv6 enabled websites, the VPN connection will fail to tunnel the request, so your browser will be sending a clear text (unencrypted) request outside of your VPN. Thus, leaving your real IP address exposed.
To stop your IP address leaking through your VPN connection, make sure you do the following::
- Use a VPN that provides a dedicated DNS server and built-in DNS leak protection.
- Use a VPN that supports IPv6 or at least one that offered some kind of workaround for this (like disabling IPv6 in your OS).
- Disabling IPv6 in the OS manually. You can find multiple guides online on how to do so on various devices.
3. DNS Leaking from the operating system
As much as people love or hate Microsoft products, the reality is that a majority of people use Windows as their main desktop operating system. However, there are some nuances you need to be aware of when using a VPN on Windows.
DNS resolution is done in a particular hierarchical order on any operating system. The first in order is the HOST file, where you can specify DNS mappings. If these are not available, the operating system will use the network connection configured DNS servers, and if they also fail to resolve the requested URL, the request will then be sent to Netbios. So if the highest priority DNS server is able to resolve the request, Windows does not consult other servers.
In the case of Windows 10, however, requests are sent out to all available network adaptors and whichever DNS server responds first, get to direct your browser to its target web address. What this means is that even if you are connected to a VPN, the DNS resolution requests might still go to your ISP’s server leaving you completely vulnerable.
Another thing to consider when using VPN on Windows is the issue with IPv6 addresses, which we discussed above. Windows uses Teredo tunneling in order to support IPv6 addresses for hosts still on the IPv4 network and do not have native IPv6 support. What this means is that you might be leaking your DNS outside of your VPN network. To prevent this type of leak, take the following steps:
- Disable Teredo tunneling
- Turn off the Windows 10 optimization by disabling smart-multi homed name resolution in group policy editor. Please note that Windows 10 home basic doesn’t have an option to edit the group policy.
To ensure your IP address and DNS traffic are truly private and secure, VPNs are a great solution. However, they are not without flaws, and it is important to check their effectiveness regularly, rather than blindly rely on VPN service vendors.
To Prevent VPN Leaks - Use A Tested VPN
We have tested hundreds of VPNs - for security, speeds and of course - leaks. We can guarantee you that the VPNs listed here won't leak and put you in danger (but if you want to see the full list - click here)





Please, comment on how to improve this article. Your feedback matters!