Webroot – Cloud-Based Protection For Home Users and Businesses
- Let’s start with a little bit about yourself and your background.
- According to the video on your home page [included below], Webroot has been around since 1997. That is impressive since the Internet as we know it has barely been around since then. How did the company begin and how has it evolved over the years?
- The video also states that you classify and score 95% of the Internet 3x a day. How do you do that?!
- You address the home user and the business user as completely different markets, with distinct product suites for each of them.
- How much common technology is there between the two product families?
- Your home user product suite – SecureAnywhere ™, competes with the more well-known brands such as Norton, McAfee, and AVG. How do you see your tools as different and/or better than theirs?
- Your business software targets the SMB (Small and Medium Business) market as opposed to the enterprise market – correct?
- Can you please give me an overview of the Smarter Cybersecurity ™ business software suite?
- How many active business customers do you have today? Where are they mainly located?
- One of the things dominating the news these past few weeks – including the general news outlets – has been the WannaCry ransomware attack. Do you have any particular comments or lessons learned from this attack?
- What are your top three security tips for home users?
- How do you see computer security technology and the security protection market evolving in the coming years?
- What are your future plans for Webroot?
- How many employees do you have today? Where are they located?
- How many hours a day do you normally work? What do you like to do when you are not working?
Although Webroot is not yet a household name, it may very well become one very soon. In my discussion with Paul Barnes, Senior Director of Product Strategy at Webroot, I learned that Webroot is the current leader in both retail sales share in the US and has the highest Net Promoter score for security software. Webroot software was also very successful in protecting its customers from the recent WannaCry ransom attack. This is mainly because Webroot is totally cloud-based and can therefore update all user devices very, very quickly.
In our conversation, Paul shared with me his top three security tips for home users. We also discussed what he sees as the major risk areas driving security technology for the next few years.
Let’s start with a little bit about yourself and your background.
I have been in the security industry for more than 10 years. I have worn many hats, including being a company owner and as a corporate employee. At first, I focused on product management, but now I focus more on long-term strategy rather than short-term execution.
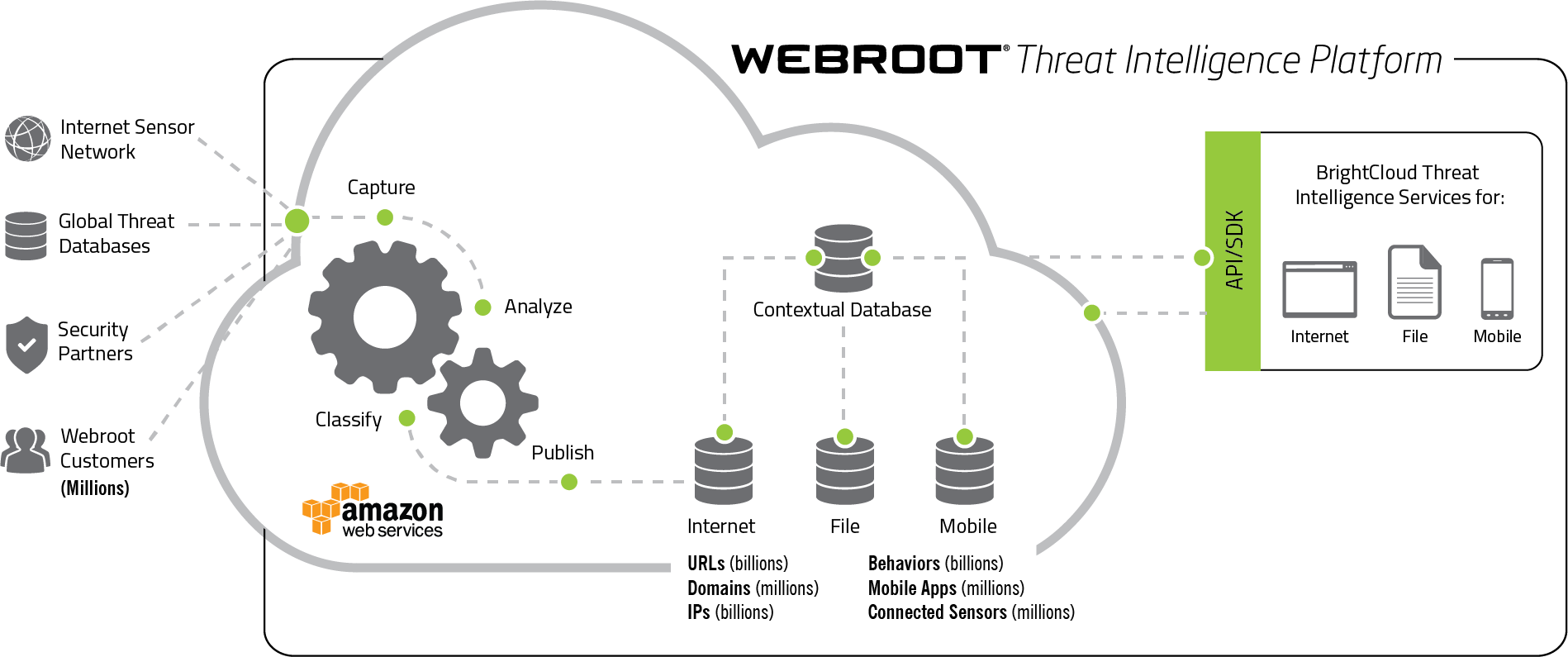
According to the video on your home page [included below], Webroot has been around since 1997. That is impressive since the Internet as we know it has barely been around since then. How did the company begin and how has it evolved over the years?
The company started in 1997 with a vision to provide anti-spyware solutions, which was still in its infancy. This propelled Webroot into the security space and we have since broadened the scope of our solutions. In addition to our own in-house development, we have grown via several key acquisitions. Our behavior-based antivirus knowledge is based on technology we acquired from Prevx, which is the company that I came from. Our threat intelligence component is based on technology we acquired from BrightCloud. More recently, we acquired a network anomaly detection company, called Cyberflow Analytics.
The video also states that you classify and score 95% of the Internet 3x a day. How do you do that?!
We create a reputation score for URLs and IP addresses through a combination of our own web crawlers and data that we receive from customers and partners.
You address the home user and the business user as completely different markets, with distinct product suites for each of them.
When Webroot as founded, we focused on providing endpoint security solutions to home users, over the years we expanded our focus to business users with an expanded suite of security products.
How much common technology is there between the two product families?
A lot actually. Both tool suites are built on the same technologies, which means that we are delivering business level protection to consumers. The main difference between the home tools and the business tools is the user interface and experience. The home user will manage the software directly on the computer or device where it is installed. For the business user, we provide a centralized, cloud-based console to manage all of the business’s computers and devices. We also provide greater detail of reporting for business customers, so they can better assess their user environments.
Having both product suites based on the same technologies is also great for threat intelligence gathering used to better protect all customers, since we can collect from a wider set of scenarios. For example, we detect many more threats on consumer devices – consumer users are 5x more susceptible to phishing attacks and 4x more likely to click on malicious download links.
We understand that threats between consumers and businesses can be different, especially in more targeted attack scenarios, so we offer more advanced controls to the business administrator to tune the protection for their users. We are about to launch a network protection solution designed to prevent users from accessing malicious content from any device in their network, this is called Webroot SecureAnywhere DNS-P.
Your home user product suite – SecureAnywhere ™, competes with the more well-known brands such as Norton, McAfee, and AVG. How do you see your tools as different and/or better than theirs?
Our software suites - both the consumer and business products - stand out in three main areas:
- Efficacy – Our software is always up to date since the analysis and all of the “heavy lifting” is done in the cloud. This allows us to respond to new threats much faster than our competitors can. Certainly, on the consumer side, no one is doing what we are doing in the cloud.
- Performance – We offer a fully cloud-based malware solution and our lightweight, high performance device agent has a very low impact on system performance.
- Ease of Use – We design our software to be “Set & Forget” – simple to initially setup and with a minimum of popups during use. When the software runs, we manage and make the necessary decisions for the user.
Another aspect of our software that is pretty unique is that we work hard to make sure that it is compatible with other security and anti-virus/malware tools so that our customers can run multiple tools simultaneously if they would like.
Our users and the market as whole have recognized these benefits. We currently have the #1 retail share in the US and the highest Net Promoter score for security software.
Your business software targets the SMB (Small and Medium Business) market as opposed to the enterprise market – correct?
Yes, that is correct. Although we do have enterprise customers using our SecureAnywhere solution, we made the business decision to focus on the SMB market. We believe there are huge opportunities there, without the need for the expensive go to market efforts required for enterprise sales. Businesses can simply order our software online from our website, or go via our channel partners, including VARs (Value Added Resellers), distributors, and MSPs (Managed Service Providers).
Our MSP business is very healthy as we have a 30% penetration with the top MSPs in world. We have a very strong strategy to serve our MSPs and see this as a mutually beneficial relationship, based on the how we engage and protect the MSP and their customer base.
We also serve many enterprises via our OEM relationships, where our Threat Intelligence technology is embedded in market leading technology providers
In general, we leverage channels to a great extent at Webroot.

Can you please give me an overview of the Smarter Cybersecurity ™ business software suite?
The Smarter Cybersecurity ™ set of tools includes the following components:
- Endpoint Protection
- Mobile Security
- Malware/Trojan Protection
- Network and DNS Protection
- Threat Intelligence
The key enhancements in the business tools are:
- Centralized management of devices
- Additional and more robust data
- Much deeper reporting for administrators
- Integration with Remote Monitoring and Management (RMM) tools
How many active business customers do you have today? Where are they mainly located?
We currently focus on English speaking countries. That means that the majority of our customers are in North America, followed by the UK, other European countries, and Australia. Today, Webroot has around 8,000 MSP customers worldwide securing over 160,000 businesses worldwide.
For the fiscal quarter ending on December 31, 2016, Webroot’s business segment bookings grew by 46% for the quarter and the consumer segment grew by 9%.
One of the things dominating the news these past few weeks – including the general news outlets – has been the WannaCry ransomware attack. Do you have any particular comments or lessons learned from this attack?
The challenge of ransomware attacks is front of mind at Webroot and we are investing a lot of money and effort to address it. We were ahead of the curve for the WannaCry attack and received some good media coverage as a result. We were able to prevent any damage to our protected devices, prior to the publication of the attack.
Internet attackers are getting increasingly sophisticated and ransomware threats are really just part of a bigger issue.
What are your top three security tips for home users?
- Backup your important data.
- Increase your awareness / education on cyber threats.
- Ensure you have a robust security/protection system in place.
How do you see computer security technology and the security protection market evolving in the coming years?
I see the following three risk areas driving security technology in the upcoming years:
- Explosion of devices and IoT (Internet of Things) – It is very easy today to prototype and to quickly bring new devices to market, but device security is not a priority for a lot of these vendors.
- Ransomware – Ransomware attacks are not going away. The business model is too good!
- Home Devices and Connections – With everything at home having an IP address and being connected to the network, consumers are at increasingly greater risk. This may include physical risk as well as we become more dependent on the devices in our day to day lives.
The security market will follow the pain points. Vendors that cannot adapt will suffer – they will either be consolidated or simply disappear. The more agile companies will thrive, especially in the IoT space.
What are your future plans for Webroot?
Based on the current technology and landscape trends, we will continue to focus on ensuring our customers and partners remain protected from the evolving threat landscape.
As we have been doing since 2010, we will continue to invest in machine learning technology to maintain and improve upon our threat intelligence. Endpoint and network protection feature highly in our strategy, as well as protecting the user and their data, whether at home or at work.
SMBs and MSPs are a key focus for us and we will continue to develop ways to make their job as friction-less as possible, when it comes to securing their user base.
How many employees do you have today? Where are they located?
We currently have over 575 employees, with the majority in our Broomfield, Colorado headquarters. We have additional offices in California, the UK, Austria, Japan, and Australia. Our R&D is distributed throughout all of our locations except for Japan and Australia.

How many hours a day do you normally work? What do you like to do when you are not working?
It should not come as a surprise that as a senior manager in an international company, I usually work 8-10 hours a day and am generally reachable outside of those hours as well. Webroot provides a great working environment and is flexible to our team’s needs, with the freedom and support to learn and grow in this rapidly evolving industry.
The majority of my leisure time is devoted to enjoying the company of my two children and my exceptional wife, who gracefully accommodates my demanding travel commitments and me. On the rare occasion that I find a few hours to spare, you'll likely find me on the golf course, honing my skills despite my occasional struggles on the fairways.




Please, comment on how to improve this article. Your feedback matters!