What is DNS Hijacking and How to Stop It | 2025 Update
More people than ever before are using the internet. Internet threats and vulnerabilities continue to expand alongside this growing user base. That's why it's more important than ever to take the necessary measures to protect your internet traffic and data.
Using a Virtual Private Network (VPN) and only visiting sites that use HTTPS encryption are two ways to protect yourself. However, you may still be vulnerable to other attacks. DNS requests sent from your computer can be hijacked and used for many malicious activities.
If this is at all confusing or worrisome, there’s no need to panic. In this article, we’re going to break down DNS hijacking piece by piece: from what DNS is to how best to prevent and protect against DNS hijacking.
What is DNS?
Domain Name System (DNS) is a system of directories that links a website to its IP address. Whenever you type the name of a site into your browser, your browser sends that name – the Universal Resource Locator (URL) – to the DNS. This is known as a DNS request.
In response to the request, your browser receives the IP address of the website – its exact numerical location on the internet. Once your device has the IP address, you are able to access and communicate with the site.
What is DNS Hijacking?
DNS hijacking is a type of attack that uses intercepted DNS queries to redirect users to malicious sites or pop-ups. Cybercriminals are not the only ones exploiting DNS. Internet Service Providers (ISPs) also hijack your DNS to redirect your traffic to suit their objectives.
Not too long ago, DNS hijacking was believed to have been a thing of the past. This couldn’t be further from the truth, however. Many companies and organizations, including Gmail, Netflix, and PayPal, have been targeted by DNS hijacking.
Although all DNS hijacking functions using the same core principle – exploitation of DNS –there are small differences in the way that these attacks are carried out. We will discuss these various types of attacks below.
The full website name that we type into our browser is known as a fully qualified domain name (FQDN). This name can be broken down into discernable pieces: namely the top-level domain (TLD), the sub-domain, and the host.
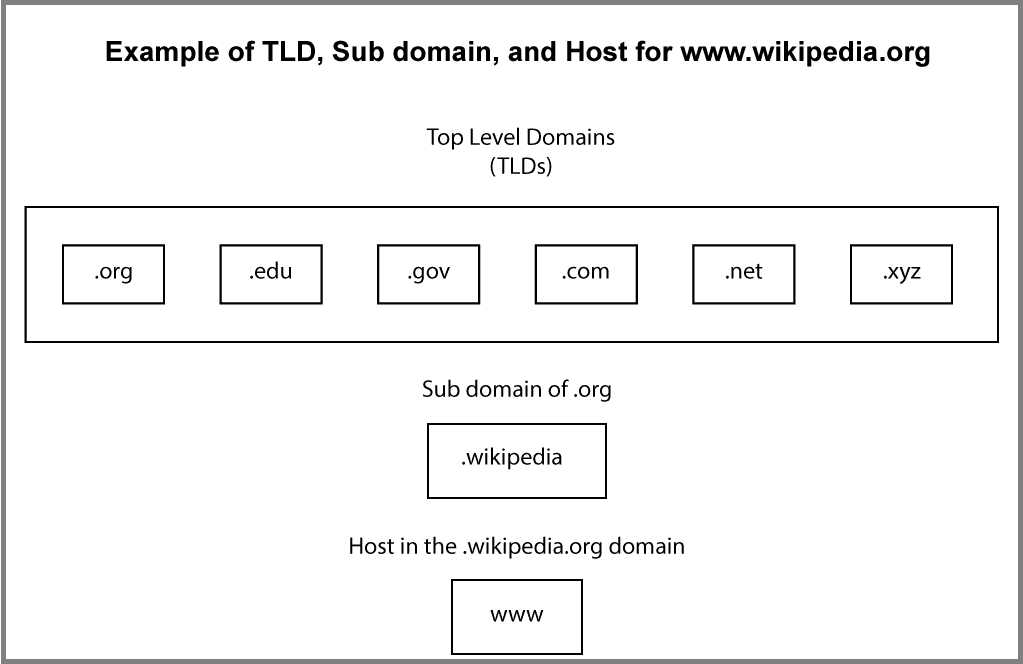 Each of these elements has a corresponding DNS server which is involved in the process of DNS requests.
Each of these elements has a corresponding DNS server which is involved in the process of DNS requests.
First, your browser asks the DNS resolver – the first server – for the location of the domain. The resolver then passes along this inquiry to the TLD’s DNS server, which then asks the DNS server belonging to the website. A hijacking can take place anywhere in this “chain.”
Today, the average user’s DNS settings are set up and configured by your ISP (or Google) by default. These companies can exploit these settings not only to gather data but also to direct you to sites and content that benefit them.
The more malicious forms of DNS hijacking involve compromising DNS servers and adding fake IP addresses, in order to redirect users to incorrect locations. Because DNS requests are an often overlooked process, these attacks can be hard to detect or prevent.
Moreover, because of the way DNS requests work – each server involved asks assistance from one ‘further along in the chain’ in order to resolve the address – a thorough DNS hijacking can spread rapidly affecting a mass of users and servers.
Types of DNS Hijacking Attacks
In broad terms, you must guard yourself against five categories of DNS hijacking assaults:
1. “Man-in-the-Middle-Attack”
The classic attack synonymous with DNS hijacking. An attacker simply intercepts a user’s DNS request and redirects it to his/her own hostile DNS server. This server then uses a trojan to return an incorrect IP address – sending you to a “spoof” website.
“Spoof” websites are created to look very similar to the specific websites you wish to visit in order to fool you. Any information you enter into these sites will be stolen.
This follow-up exploit is known as "phishing," and may be carried out following any type of DNS hijacking.
Another type of attack known as "pharming" can be launched using a man-in-the-middle attack or any of the other methods of hijacking below. This follow-up attack displays unwanted ads and pop-ups, intended to redirect you, in order to generate ad revenue.
The chain-like makeup of the DNS request process affords a number of potential entry points for any cybercriminal wishing to perform a man-in-the-middle attack.
By default, when the response reaches your device, there is no way to verify that the DNS request has not been tampered with.
2. Malware Attack
This is the most common type of attack today. An attacker infects your device (i.e. phone, tablet, computer, router) with malware trojans. These trojans will change the DNS settings of the infected device and redirect you to a malicious DNS server.
This type of attack is considered local, since it is initiated on your device, as opposed to a man-in-the-middle-attack, which compromises the request during the part of the process that takes place outside of your local area network (LAN).
3. Cache Poisoning
This is another way for an attacker to redirect you to a “spoof” site without directly hijacking your DNS requests. Fake DNS entries are inserted into the cache (memory) of your local DNS resolver, re-directing you to dangerous imitation sites instead of the actual sites requested.
Because the DNS resolver manages the requests of all devices on your network, a well-planned cache poisoning attack could endanger your entire LAN and those using it. Just one user clicking a malicious link in an email or pop-up could lead to a host of problems.
4. Rogue DNS Server
This type of attack occurs when a DNS server is targeted and hacked, and its records changed to redirect incoming requests to phishing sites.
5. DNS Hijacking Using Router Vulnerabilities
This form of attack involves someone gaining direct access to your router and then altering its DNS settings, re-routing your traffic to compromised DNS servers. These servers can then re-direct any traffic on your LAN to dangerous phishing sites.
While this type of attack may appear similar to malware attacks that infect your router, these attacks are initiated directly upon the router. Malware attacks tend to compromise your router indirectly by first infecting your device.
How to Stop DNS Hijacking and Stay Safe
Luckily for all of us, the tools and methods used to protect against DNS hijacking are very similar to those used to guard against many other common types of vulnerabilities and attacks.
As a baseline defense against DNS hijacking, we recommend you do the following:
- Use up-to-date security software, particularly software including malware protection.
- Avoid clicking on questionable links in your emails or on social media.
- Protect your router:
- Change the default admin and password for your router. These credentials are not the same as your wi-fi access password. This is the username and password used to log into your router and make changes such as those to DNS settings. This is important because there are only a few default admin usernames in circulation, and passwords are usually written on the router itself. Moreover, the login access screen is usually accessible at a known IP address like 192.168.0.1 or 192.168.1.1.
- Update the firmware of your router to protect against the latest security vulnerabilities.
- Don’t use public wi-fi networks to send or receive personal information or to log into sites that require credentials. We also recommend that you never use a network that allows use without first giving you a terms of service (ToS) page.
- Always check the URL of the site to make sure that it's the exact site you intended to visit. If any part of the address appears unfamiliar, close the browser immediately and check your DNS settings for vulnerabilities or leaks. Phishing sites usually do not have a valid SSL (secure sockets layer) certificate. Check to make sure that the site you are using has a valid SSL certificate indicated by the lock icon in your browser’s address bar. Never enter private data (i.e. credit card details, personal info) into a web form on a site that does not have have a valid SSL certificate.
Although the above steps will help defend you against DNS hijacking, these attacks are varied and new vulnerabilities continue to be exploited.
Moreover, while you can stay vigilant against unusual pop-ups and messages on pages and platforms that you use often, you have no way to prevent a DNS server from being compromised.
For these reasons, the safest and easiest means of protection against DNS hijacking is to use a VPN from a premium provider. VPNs began as a way for people to gain secure remote access to LANs. Today, however, their uses and advantages extend far beyond that.
Because a VPN creates an encrypted tunnel through which it ferries all your traffic, it bypasses your router's settings and performs a DNS request using the VPN's DNS resolvers.
Top VPNs like ExpressVPN offer advanced DNS protection to make certain that all your DNS requests are routed through their own DNS servers. These VPNs also block traffic to DNS servers provided by your ISP, government surveillance, or cybercriminals.
Not all VPNs are created equal, however. Some VPNs simply offer browser extensions while others offer more secure ‘tunneling’ protocols such as IPsec, to make sure that no DNS requests are hijacked and that all your traffic is sent through a secure tunnel.
Be wary when using free VPNs, as many free VPNs will keep a log of your habits, track your online activity, and bombard you with ads.
The selection of VPNs actually worth paying for is quite small. We suggest that you use one of our top recommended VPNs to properly protect yourself against DNS hijacking and a host of other attacks.
The Simplest and Best Way to Protect Yourself
DNS hijacking is an often overlooked exploitation used by cybercriminals to redirect you to dangerous “spoof” sites. DNS requests are largely overlooked, and so too is the potential harm that can be caused if they are compromised.
DNS hijacking is not just limited to criminals. ISPs will also run modified DNS servers to redirect your traffic for their own benefit. Often they will do this to collect statistics, and may even send you ads when you access unknown domains.
Many governments will also use DNS hijacking for surveillance and censorship, redirecting users away from banned sites and towards government-authorized sites.
If any of the above worries you, then now’s a better time than ever for you to get proper protection against DNS hijacking.
Fortunately, the simplest and most effective method to safeguard yourself is also the best: By using a premium VPN, you not only shield yourself from DNS hijacking but also defend against various other significant and emerging threats.
Further Reading
- We tested dozens of VPNs to find the fastest services
- Check out the 7 best REALLY FREE VPN services that still work




Please, comment on how to improve this article. Your feedback matters!