What Is Doxxing? Does It Mean Swatting & Is It Illegal? (2025)
Between multiple entries on the Urban Dictionary and hazy legal definitions, it can be hard to pin down exactly what constitutes doxxing (or doxing). While still a form of cyberbullying, doxxing is different from swatting and other types of online harassment.
So, what is doxxing? It’s the practice of releasing someone’s information online against their will. Around 4% of US citizens have been doxxed, while 14% report knowing someone who’s been doxxed¹. But is doxxing illegal? I’m taking a look into what counts as doxxing, its legal implications, and how it’s used for malicious purposes. I’ll show you how to protect yourself from doxxing and what to do if your information has been exposed.
Pro Tip: Use a VPN to Avoid Doxxing
You can enhance your online privacy with a reliable VPN, making it much harder for doxxers to obtain sensitive info. When you connect to a server, VPNs encrypt your connection and reroute your traffic through a private server, changing your IP address. This hides your real location and identity from third-party services (which are commonly breached), hackers, and even your ISP.
What Is Doxxing?
Doxxing (or doxing) means publicly exposing someone's private information without their consent. The term originates from the word ‘documents’ (or docs) and stems from the 90s hacker practice of compiling a personal dossier on a victim. The motivations for doxxing usually include revenge, personal grudges, ideological disagreements, or political targeting. Usually, the purpose is to harass, intimidate, or cause real-world harm.
High-profile doxxing incidents have had a particularly devastating impact. In the 2015 Ashley Madison data breach, hackers exposed sensitive user information from the dating site², leading to widespread harassment and several reported suicides. Another case is the 2013 Boston Marathon bombing investigation, where Reddit doxxed unrelated individuals who then faced threats.³
Types of information commonly exposed through doxxing include:
- Personal identifiers: Full name, home address, workplace location, school details, and frequently visited places.
- Contact information: Phone numbers, email addresses, and social media profiles.
- Financial data: Bank account details, credit card numbers, and PayPal accounts.
- Government IDs: Social security numbers, driver's license information, and passport details.
- Private communications: Content from personal emails, text messages, and direct messages.
- Background information: Criminal records, court documents, and legal history.
- Media content: Personal photographs, videos, and audio recordings.
- Sensitive details: Private information about relationships, medical history, or other potentially embarrassing personal matters.
How Do Doxxers Find Information About People?
Doxxers can gather publicly available data or use illegal tactics to steal sensitive information. Below, I've compiled the most common approaches and sources they use.
- Social media analysis: Doxxers piece together details from media, check-ins, friend lists, and liked pages (on Facebook, Instagram, LinkedIn, and others). People often post comments and photos revealing their location or social circle.
- Username tracking: Following the same username across different websites allows doxxers to connect accounts on gaming platforms, forums, and social media. It can help build detailed activity profiles and discover personal interests.
- Data broker exploitation: Data brokers like Spokeo or Whitepages aggregate and sell user data from public records, surveys, and online activities. Doxxers can cross-reference multiple databases to verify and expand their findings.
- Phishing campaigns: Deploying targeted emails and messages that appear legitimate can trick victims into revealing sensitive information. These often include malicious links that capture IP addresses or download malware to steal stored data.
- Packet sniffing: Criminals create rogue WiFi hotspots that you can connect to in public spaces. This allows hackers to capture your web traffic or sensitive credentials transmitted over the network.
- WHOIS database mining: Searching domain registration records for websites and blogs often shows private information. WHOIS databases can reveal domain owners' names, addresses, phone numbers, and email addresses.
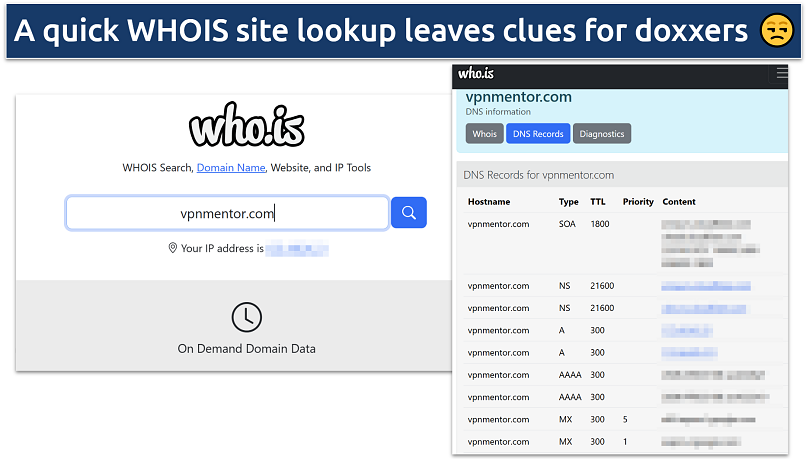 Without privacy protection enabled, your website can expose your information
Without privacy protection enabled, your website can expose your information
- Public records research: Government databases contain marriage certificates, property records, business licenses, and court documents. Many of these records containing personal information are freely available online.
- Reverse phone lookups: If a doxxer obtains your phone number, they can use services that reveal your identity and associated addresses. Doxxers combine this with other methods to verify information and discover extra details.
What Is Doxxing Used For?
Doxxing is often the first step in a harassment and intimidation campaign. Once attackers obtain someone's personal information, they can deploy malicious tactics to cause psychological, financial, and even physical harm. I've identified several common ways this information gets weaponized against victims.
- Identity theft: Attackers use exposed personal and financial information to open fraudulent accounts and make unauthorized purchases. They may also file false tax returns or take out loans in the victim's name, causing financial and legal nightmares.
- Coordinated harassment: With personal details, attackers launch persistent campaigns across multiple platforms. They flood victims with threatening messages, coordinate attacks on social media, and may even show up at the victim's doorstep.
- Malicious sign-ups: Overwhelming victims by registering their information for countless unwanted services. This includes ordering repeated food deliveries, signing up for adult websites, or subscribing to endless spam emails.
- Extended cyberbullying: Beyond targeting the individual, attackers harass family members, employers, and colleagues. They spread false rumors, manipulated photos, or embarrassing information to damage reputations.
- Swatting: In a dangerous practice known as swatting, doxxers make false emergency calls about the victim's address. It results in armed police responses, putting both the victim and law enforcement at risk.
- Public figure exploitation: Celebrities and influencers face unique risks when doxxed. The information often leads to stalking incidents, blackmail attempts, or leaks that damage their public image.
- Discriminatory attacks: Doxxers can target individuals based on their identity or beliefs, publishing personal details to incite harassment from hate groups. These attacks often escalate into coordinated campaigns of intimidation.
Is Doxxing Illegal?
Sharing publicly available information isn't always illegal, but doxxing often intersects with hacking, harassment, and cyberstalking laws. For example, doxxing is unlawful if the information is obtained through illicit means (like hacking). Similarly, using your information for harassment can violate multiple criminal laws.
The legal status of doxxing also varies by location and jurisdiction. For instance, posting personal information intending to cause fear or harassment is criminalized under California's Penal Code (section 653.2).⁴ Maryland's Grace's Law 2.0 also criminalizes using electronic means to share private information maliciously.⁵ Both legislatures make doxxing punishable by fines and prison time and allow victims to sue doxxers in civil court.
 Not all jurisdictions define doxxing identically, though
Not all jurisdictions define doxxing identically, though
Generally, criminally punishable doxxing should meet these legal criteria:
- Deliberate behavioral pattern: The perpetrator must knowingly and repeatedly engage in electronic communication targeting the victim.
- Specific targeting: The actions must be directed at a particular individual rather than a general posting of information.
- Malicious intent: The communication must serve no legitimate purpose. Instead, it’s intended to cause harm or distress.
- Measurable impact: The actions must cause reasonable fear, emotional distress, or disruption to the victim's well-being and social life.
How Do I Stay Safe From Doxxing Online?
Protection from doxxing requires following good internet safety and privacy practices. No single measure can guarantee complete protection, but a sound strategy significantly reduces your risk. I'll guide you through some essential rules of conduct.
1. Limit Sharing on Social Media
Social media platforms are goldmines for personal information. Your posts, media, and interactions often reveal more than you intend.
 Turn of discoverability on social media to prevent doxxing
Turn of discoverability on social media to prevent doxxing
- Check your content before posting. Consider if the information or photo has landmarks or data that can reveal your location, workplace, or routine. You should also remove metadata from the media you upload online.
- Be careful with usernames. Use nicknames or pseudonyms on public forums and social platforms instead of your real name. And switch them up — using the same username across different platforms allows doxxers to cross-reference your information.
- Keep an eye on your followers. Consider setting your accounts to private, or limiting your followers to people you know in real life.
2. Use Strong Security and Privacy Settings
Basic security measures are your first defense against doxxing. Implementing robust security practices across your accounts helps prevent unauthorized access and data leaks.
- Use complex passwords. Create unique passwords using a mix of uppercase, lowercase, numbers, and symbols. Aim for at least 12 characters to resist brute-force attacks.
- Separate your accounts. Use different passwords for each online account. If one service gets breached, your other accounts will remain secure.
- Enable two-factor authentication (2FA). Multi-factor authentication (MFA) requires you to input additional security codes (usually via SMS or an authentication app) in addition to your passwords.
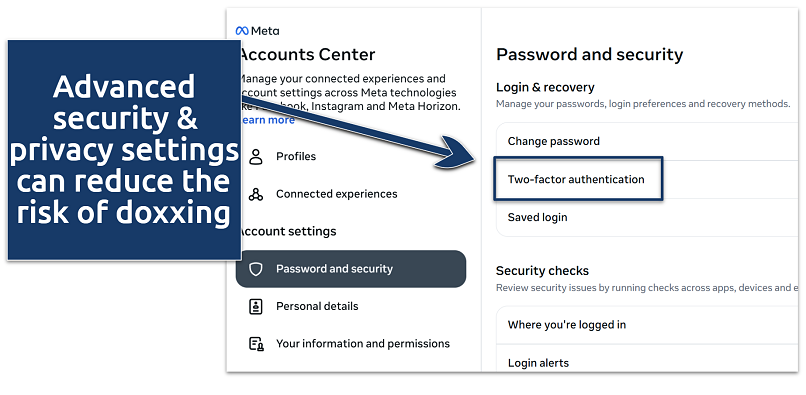 Look for multi-factor or two-factor authentication in your settings to prevent unauthorized logins
Look for multi-factor or two-factor authentication in your settings to prevent unauthorized logins
- Review privacy settings. You can limit who can view your posts, photos, friend lists, and personal details. Platforms update settings regularly, so you might need to remember to do this more than once.
Social media networks all have their own different privacy policies and settings. Check out our guides to find out more about how to protect yourself from doxxing on each one:
3. Use a Dedicated Email Account
Email management helps you stay safe online. Strategic use of email addresses can isolate your main account, reducing the risk of exposure.
- Separate email accounts. Create distinct email addresses for different purposes. For example, you can have different addresses for personal communication, work, and anonymous social media accounts.
- Protect your main email. Reserve your primary email address for important communications only. Never use it for forum registrations or newsletter subscriptions.
- Configure security. Apply robust security settings to all your email accounts, including strong passwords and two-factor authentication.
4. Be Aware of Phishing Attempts
Phishing attacks often serve as entry points for doxxers to gather personal information. Learning to spot and avoid these attempts protects your sensitive data from falling into the wrong hands.
- Avoid unknown senders. Don’t open attachments or links you receive from unknown senders. These can contain viruses, trackers, and other malware that can expose your information.
- Verify senders. Double-check email addresses carefully, looking for slight misspellings or unusual domains. Hover over links without clicking to preview their destination.
- Information requests. Never share personal details via email, even if the sender appears legitimate. Contact organizations directly through their official websites or other contact details.
5. Check Google
Search engines can expose surprising amounts of personal information. Taking control of your digital footprint through search engines minimizes your exposure to potential doxxers.
- Try doxxing yourself. Search your name, email addresses, and phone numbers monthly. Use quotation marks for exact matches and check multiple pages of results. Perform reverse image searches on your photos to find unauthorized uses. Try finding your information on data broker sites.
- Configure Google Alerts. Google can notify you if your name, address, phone number, and other personal details appear online. If your credentials have been leaked, make sure to change them across your accounts.
6. Configure Your Mobile Device
Mobile devices can leak personal information if not properly secured. Here are the things that can prevent location tracking and data theft.
- Turn off location services. On iOS, go to Settings > Privacy, and disable GPS tracking in Location Services. For Android, go to Location from the device’s Settings. I advise keeping the location services enabled only for essential apps.
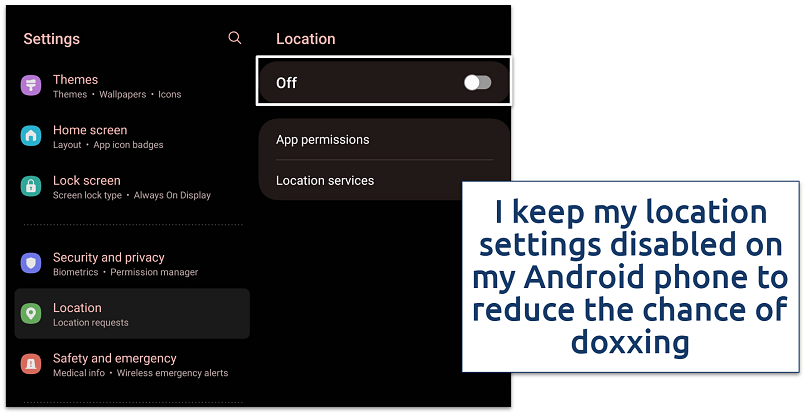 Additionally, you can manually disable location settings for different applications
Additionally, you can manually disable location settings for different applications
- Restrict app access. Review what each app can access on your device. Deny unnecessary permissions — especially for location, contacts, and camera access.
- Don’t link accounts with social media. Avoid using social media accounts to log into other apps. Create separate accounts instead to prevent data sharing between services.
- Delete unused software. Regularly check unused applications. Delete the services and tools you don’t need to minimize data exposure.
7. Use a VPN to Hide Your IP Address
VPNs are crucial to maintaining online privacy and preventing tracking. A VPN encrypts your online activity and disguises your location, making your personally identifiable data unreadable to third-party sites, hackers, WiFi networks, and your Internet Service Provider (ISP).
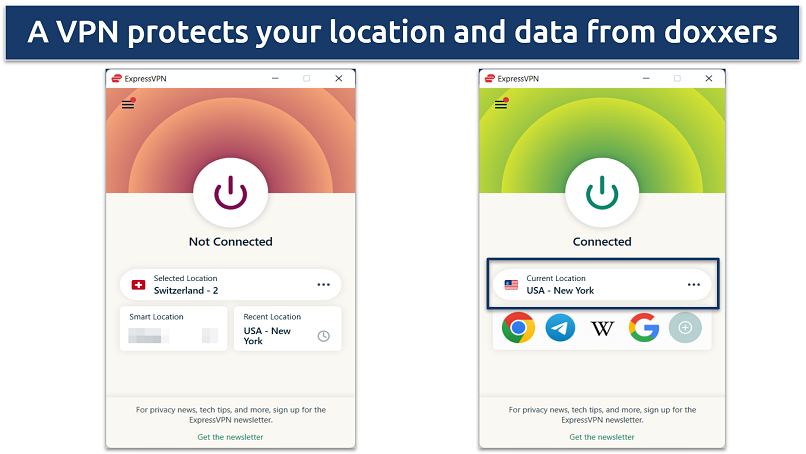 Use a VPN with military-grade encryption and IP protection, like ExpressVPN
Use a VPN with military-grade encryption and IP protection, like ExpressVPN
What Do I Do if I’ve Been Doxxed?
When your personal information is exposed, these immediate actions can minimize the damage. To help you out, I divided them into steps.
Step 1: Document the Incident
Before removing exposed information, you need to record what was posted, where, and who did it. Detailed documentation improves the success rate of takedown requests and legal action.
- Assess the damage: Identify what personal information has been exposed and where it appears online. Note any immediate safety concerns that need urgent attention.
- Screenshot everything: Take detailed screenshots of all posts, comments, and messages containing your personal information. Include timestamps and URLs.
- Record a timeline: Document when the information first appeared and how it was subsequently shared.
- Preserve identifiers: Keep a detailed list of usernames, profile links, and any other information that could help identify the source.
- Save threatening content: Record any false statements or threats against you, as these will be crucial for legal action.
Step 2: Lock Your Social Media Accounts
You should prevent doxxers from gathering additional information or using your accounts to cause further harm.
- Enable privacy mode: Set all social media settings to their most restrictive privacy settings.
- Suspend accounts: Consider temporarily deactivating (or deleting) your accounts until the situation is under control.
- Update your credentials: Change all your passwords, enable multi-factor authentication where possible, and review connected apps and devices.
Step 3: Report the Content for Removal
Request the removal of the leaked information to limit its spread. Well-documented removal requests have the highest success rate.
- Contact platform and website admins: Start with major platforms and work down to smaller sites. Make sure to check the site hosting companies, data brokers sites, and search engines.
- Explain your request clearly: Explain how the doxxing violates platform policies and your rights.
- Use multiple channels: Utilize all available reporting options, including harassment and privacy violation forms.
Step 4: Protect Your Financial and Online Accounts
Exposed information often leads to identity theft and financial fraud. Take immediate steps to secure your finances and monitor your accounts for suspicious activity.
- Notify your bank: If you believe your financial information has been exposed, immediately alert your bank or the relevant payment service.
- Credit monitoring: Freeze your credit and set up fraud alerts. You might want to reissue your credit cards.
- Password reset: Update login credentials for all financial accounts and payment platforms, starting with banking apps and digital wallets (like PayPal or Binance).
Step 5: Inform Relevant Parties & Legal Bodies
A support network strengthens your response to doxxing. Alert key people who can help protect you and monitor for escalation.
- Professional contacts: Notify your employer or school about the situation. Students can work with campus security to develop a safety plan.
- Personal network: Brief close friends and family about the situation so they can avoid sharing more information online.
- Support services: Connect with counseling services or support groups for emotional assistance.
- Legal counsel: Consult a lawyer familiar with cybercrime and harassment cases.
- Law enforcement: File a police report if you've received threats or the doxxing involves criminal behavior (like hacking or phishing).
Best VPNs to Stay Safe From Doxxing in 2025
- ExpressVPN — Military-grade encryption and leak protection safeguard your information from doxxers.
- CyberGhost — Easy-to-use apps help you quickly connect to a server and protect your data.
- Private Internet Access — Unlimited device connections mean you can secure all your devices simultaneously.
Editor's Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: Intego, CyberGhost, ExpressVPN, and Private Internet Access. However, this does not affect our review process, as we adhere to a strict testing methodology.
FAQs on Doxxing
What is doxxing slang for?
Doxxing originated in hacker culture as “docs dropping”, meaning the release of someone's documents or personal information online. Malicious actors have several legal and illegal ways to collect private information. The term evolved from the misspelling of "docs" to "doxx" as it spread beyond hacker circles and IRC channels. Urban Dictionary added it in 2011, defining it as exposing someone's private details without consent.
Why is doxxing so scary?
Doxxing weaponizes casual online activities. An everyday digital footprint — from social media posts to online shopping — creates a trail. Once personal information is exposed, it triggers escalating threats, such as cyberbullying, swatting, stalking, or identity theft. Seemingly harmless leaks often lead to serious and even fatal consequences. This is why many countries criminalize hacking or activities related to doxxing.
Can I take legal action against people who doxxed me?
Legal action is possible if the doxxing is malicious, systematic, or carried out via illegal means. Most doxxing incidents involve harassment, stalking, or threats. However, it’s necessary to document everything regarding the doxx and its consequences. Before going to the police, record messages, URLs, and other evidence of harassment and leaks. It can also be a good idea to consult with a legal professional.
How can I protect my children from being doxxed online?
Children need good privacy habits and tools to avoid doxxing. Teach your kids about account security settings, understanding phishing attacks, creating strong passwords, and staying safe from strangers online. Parents should also avoid posting sensitive information or photos of their children that may reveal their identity or location.
Avoid Doxxing and Cyberbullying
If you become a target of a dox attack, you can limit the damage with quick action and thorough documentation. Since online stalking and cyberbullying are related crimes, it’s possible to pursue legal recourse to bring the attacker to justice. However, the best method is prevention.
While complete online anonymity is challenging, strong privacy and security practices can reduce the risks of doxxing. Be aware of the information you share online and use tools that safeguard your real location and browsing habits, as these can leak to data broker sites. That way, your personally identifiable information stays on lockdown and safe from doxxers.


References
- https://www.safehome.org/family-safety/doxxing-online-harassment-research/
- https://krebsonsecurity.com/2022/07/a-retrospective-on-the-2015-ashley-madison-breach/
- https://www.bbc.com/news/technology-22214511
- https://leginfo.legislature.ca.gov/faces/codesTOCSelected.xhtml?tocCode=PEN&tocTitle=+Penal+Code+-+PEN
- https://www.peoples-law.org/bullying#:~:text=Grace's%20Law%20prohibits%20a%20person,without%20a%20legal%20purpose.
Your online activity may be visible to the sites you visit
Your IP Address:
216.73.216.5
Your Location:
US, Ohio, Columbus
Your Internet Provider:
Some sites might use these details for advertising, analytics, or tracking your online preferences.
To protect your data from the websites you visit, one of the most effective steps is to hide your IP address, which can reveal your location, identity, and browsing habits. Using a virtual private network (VPN) masks your real IP by routing your internet traffic through a secure server, making it appear as though you're browsing from a different location. A VPN also encrypts your connection, keeping your data safe from surveillance and unauthorized access.





Please, comment on how to improve this article. Your feedback matters!