The Digital Iron Curtain. Russia Prepares for a Total Ban on VPNs.

What Does it Mean for Personal Privacy, Secure Communication, and Access to Information?
Russian sources have announced that a ban on VPN services will go into effect on March 1st. The ban encompasses advertisements and websites that provide information about how to bypass blocked resources in Russia and occupied territories of Ukraine. This is just the latest step in a years-long campaign to regulate access to information, isolate internet users within Russia, and increase surveillance capabilities by the authorities. Restricting VPNs could be seen as reducing one of the last tools Russian citizens have to access the outside world and hear opinions, news, and perspectives beyond the narrow scope of approved topics presented by state media.
The most basic way to describe a VPN is that it acts like a secure tunnel that helps internet users protect their online privacy. It works by encrypting the internet connection, making it harder for others to see what you're doing, reading, watching, or sending online. Outside of bypassing government censorship, people generally use VPNs to keep their data safe, access geo-restricted content, and browse the internet privately without being tracked.
As Russia prepares to implement restrictions on VPN services, I recall another time in history when information, expression, and speech were under tight control. During the times of the Soviet Union, the “Iron Curtain” represented the physical and ideological barriers to restrict the flow of information, ideas, and people. The Soviet government maintained strict oversight over all forms of media, and only state-approved content could appear in newspapers, on the radio, and on television. Dissenting voices or alternative viewpoints were often subjected to scrutiny, with strict measures against those who diverged from state policies. No matter what your views on geopolitics are, the implementation of technology in Russia to restrict access to information, monitor online activities, and intercept communications brings to mind the concept of a new “Digital Iron Curtain”.
The Russian government’s ban on VPN services seems to be about much more than limiting the freedom of expression. The internet is the final frontier where people from around the world can access limitless knowledge and information. Social media allows us to build networks of like-minded friends and interact with others in ways we never imagined. Messaging apps offer us secure communication methods and a sense of privacy that traditional phone services never could. After years of relative digital freedom in Russia, the government is facing the significant challenge of managing and restricting access to virtually all outside information — and here’s where the VPN ban comes in. The real reason the Russian government wants to restrict VPN usage is probably because people are using the VPN technology to effectively access banned content and bypass strict government surveillance measures.
In the last few years, Russian authorities have pressured social media companies to restrict content, establish local business entities, store data locally, and allow security services unrestricted access to user data (as required by Russian law). Some western social media companies have decided not to comply with local regulations, even if it means leaving the Russian market. In 2018, Russia requested that Telegram (the encrypted messaging app) provide security services with encryption keys to allow the government access to users' messages, audios, and pictures. Telegram declined this request and adapted by changing their IP address. In return, the state regulator (Roskomnadzor) blocked nearly 20 million Amazon and Google Cloud IP addresses to prevent Telegram from switching IPs to circumvent the ban. In 2020, Telegram re-entered the Russian market and — according to a report by Wired — there have been instances of users being contacted by the authorities regarding their private communications in the Telegram app.
In 2022, nearly 23% of the Russian population used VPN services compared to only 9% in 2021. The surge in VPN usage is associated with Russia's invasion of Ukraine and the Russian authorities’ subsequent blockage of an estimated 138,000 websites, including social media platforms such as Instagram, Facebook, and X (formerly Twitter). In 2023, Russia received an index score of 21 out of 100 in the annual Freedom on the Net (FOTN) ranking by Freedom House. With the notable trend of censorship and legal restrictions online, it is clear to see why people in Russia may wish to stay anonymous while protecting their privacy — and why the government’s next move is to ban VPNs.
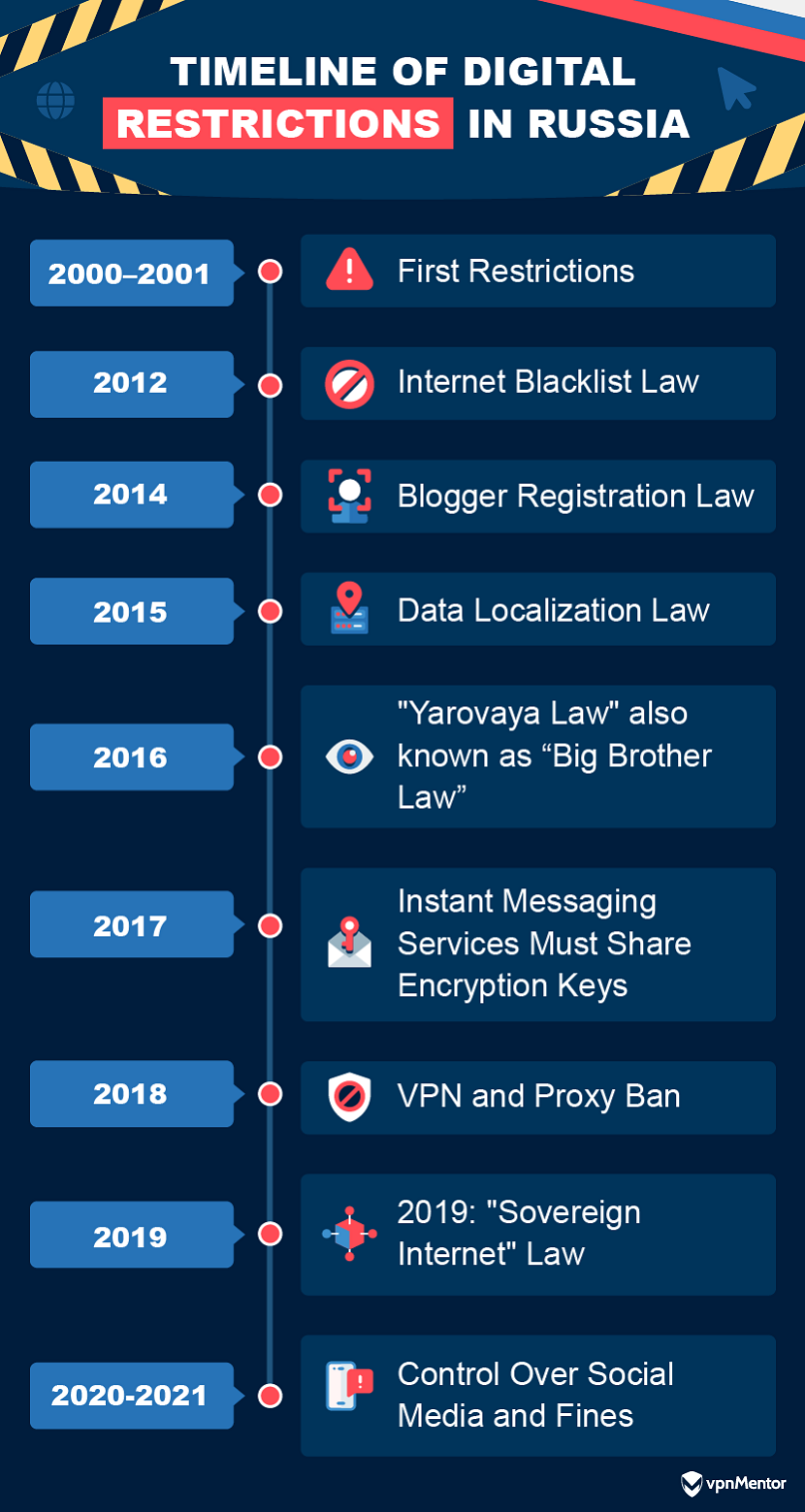
Timeline of Digital Restrictions in Russia
- 2000–2001: First Restrictions
The Russian government began creating and enforcing regulations to provide state control of the internet, including laws limiting online content and restricting user activities. - 2012: Internet Blacklist Law
The Russian government created a law to allow the blacklisting of websites without a court order or any real oversight to deem the website unacceptable. At the time, Russian civil society raised concerns that the laws could restrict freedom of expression. - 2014: Blogger Registration Law
Influential bloggers — or any person whose online presence or website draws more than 3,000 daily readers — have to register with the government, disclose personal information, and provide technical details to the principal security agency of Russia, which is the Federal Security Service of the Russian Federation (“FSB”). This move was seen by privacy advocates as an attempt to intimidate, monitor, and control influential individuals online. - 2015: Data Localization Law
Russia required internet companies (both foreign and domestic) to store the personal
data of Russian users on servers located within the country. This law also required the information to be accessible to authorities, effectively giving the state control over user data. - 2016: "Yarovaya Law" also known as “Big Brother Law”
This law expanded the Russian government’s surveillance powers, mandating that internet service providers (ISPs) store users' communications data for up to three years. They were also required to provide full access to security agencies, which involved installing surveillance hardware and software. Additionally, the law banned search engines from displaying results for blacklisted websites. - 2017: Instant Messaging Services Must Share Encryption Keys
Under this law, all instant messaging services operating in Russia were required to provide the FSB with access to users' encrypted messages. This rendered any privacy features of the app worthless as all communications could be decrypted using the keys provided by law. In addition, all users of messaging apps had to be identified through the registration of the mobile provider. - 2018: VPN and Proxy Ban
Russia passed a law banning the use of virtual private networks (VPNs) and proxy servers — both of which allow users to access blocked content — in an attempt to tighten control over online information access. The law is supposed to take effect on March 1st, 2024, nearly six years after it was first passed. The delay could be due to the difficulty of the technical capabilities needed to fully block all VPN services. - 2019: "Sovereign Internet" Law
This law gave the government the authority to centralize state control over the country's internet infrastructure in the event of perceived threats to national security. The legislation, which was enacted that same year, also set fines for spreading "disrespectful" content about the government and state officials online, further restricting freedom of speech. - 2020-2021: Control Over Social Media and Fines
Under these laws, authorities could fine social media platforms for failing to delete content deemed illegal. This mandate put pressure on platforms to comply with state censorship requisites, including requirements to establish legal entities, store user data locally, and make said data accessible to authorities.
Media and internet services in the Russian Federation are regulated by Roskomnadzor (Federal Service for Supervision in the Sphere of Telecom, Information Technologies and Mass Communications), a branch of the Ministry of Telecom and Mass Communications. Although censorship and surveillance measures may be implemented under the guise of national security or antiterrorism, their implementation shows there is a real fear inside of Russia over the freedom of information, expression, communication, and thought. Any view that deviates from the ever-shrinking list of government-approved topics appears to be considered a threat to national security. In today’s age of information and technology, it’s hard to believe that simply accessing information, liking a social media post, or using the wrong word to describe a non-approved topic can get you arrested and sent to prison for a long time. Wanting personal privacy, access to information, and confidential communication should not inherently make a person a threat to national security.
How Easy Is It to Block VPN Usage?
Blocking VPN services is a significant challenge, but it’s not impossible. Countries such as Russia that have strict censorship laws and state control over the ISP and telecom providers have unrestricted access to data and network systems. With such access, it is possible to identify when someone is using a VPN.
In theory, VPNs are designed to provide secure and private connections, based on the idea that ISPs are private companies and independent of government security services. In most Western countries, intelligence agencies need a court order to intercept or review personal user data; Russian special services, on the other hand, legally require telecom and internet operators to install specific software and hardware. The System for Operative Investigative Activities (SORM) is basically legally required spyware that allows the FSB to have full access to all data without the knowledge of telecom or internet companies. When all non-encrypted data is tracked and monitored by the state, using a VPN is key for citizens to protect themselves, their communications, and their online activities.
How Does VPN Blocking Work?
VPN technology was first used in 1996. Since then, companies and governments alike have developed numerous methods to identify VPN usage (and, in response, ways for VPN users to avoid detection as well). Here are the most common methods to block VPN services.
- Deep Packet Inspection (DPI): Authorities can analyze the data packets as they pass through the network and try to identify the unique patterns (or the fingerprint) of how VPN traffic operates. The only real way to avoid detection is on the shoulders of the VPN providers and the technology they use to hide identifiable patterns. To avoid detection, most modern VPNs use techniques to make their traffic appear like regular internet usage data. Once the ban goes into effect, the authorities will most likely block any encrypted traffic that resembles VPN usage.
- Blocking VPN Servers: The Russian government already has a list of websites and IP addresses — and it continues to update that list regularly. Authorities identify known IP addresses associated with VPN servers and block access to these servers. Many legitimate VPN providers frequently update and change their server IP addresses to bypass the server-based bans. Identifying and restricting access to new IP addresses and VPN technologies can be like an endless cat-and-mouse game for authorities.
- Port and Protocol Blocking: VPNs use specific ports for their communication protocols. By identifying the ports being used by VPN services, the Russian authorities can block all known ports with the goal of restricting VPN traffic. This includes protocol blocking or restricting the use of specific communication protocols commonly associated with VPN traffic such as Point-to-Point Tunneling Protocol (PPTP), Layer Two Tunneling Protocol (L2TP), Internet Protocol Security (IPSec), and Secure Socket Tunneling Protocol.
- DNS Filtering: DNS stands for Domain Name System. Authorities could prevent a connection to all domain names that are associated with VPN services. Users can manually configure DNS servers or use IP addresses directly to bypass this method of restriction.
Risks of Using a Free VPN or Unknown VPNs
Using a free VPN in countries with strict internet censorship and surveillance, such as Russia and China, poses potential risks. In 2023, I discovered a publicly exposed database belonging to a China-based free VPN service that exposed 360 million records, including users’ email addresses, device information, and even references to sites that the user visited. I saw firsthand how the user data was not anonymous, so users could have easily been identified by authorities. Using a free VPN could compromise user privacy if the provider is improperly logging user data or selling that information to third parties. In countries with strict government surveillance, the use of a vulnerable VPN could lead to the exposure of sensitive personal information — not to mention the potential legal trouble for users who access forbidden websites or restricted content.
In September 2023, the Russian state news agency Tass published a statement by Digital Development Minister Maksut Shadayev saying “The authorities are not going to introduce penalties for the use of VPN services in Russia”. However, there is an old saying: you shouldn’t believe anything until the Russian Government denies it. I highly recommend those who wish to circumvent internet restrictions in Russia understand the risks and always use a reputable VPN provider. Choose a service that offers strong security measures, offers a wide selection of server locations, and prioritizes privacy. Although Russia has blocked several well-known VPN services, there are some VPNs that still work in Russia.
I recommend that users do their research and be wary of free VPNs, as they have numerous potential risks and often have a limited number of servers, which reduces the effectiveness of the VPN. They also tend to employ weaker encryption methods or outdated protocols, making it easier for authorities to intercept and monitor your traffic. It is no secret that authorities in countries like Russia and China actively monitor and regulate VPN usage. Using a free VPN, especially one that is not compliant with local regulations, poses a significant security risk to the user. No matter what your reason to use a VPN is, do your homework to find the right service for your personal needs, make smart choices with your internet activities, and stay safe online. The opinions in this article are my own and do not represent those of vpnMentor.
Disclaimer: The content and images in this article are the property of vpnMentor. We permit our images and content to be shared, as long as a credit with a link to the source is provided to vpnMentor as the original author. This way, we can continue our mission to provide expert content and maintain the integrity of our intellectual property.



Please, comment on how to improve this article. Your feedback matters!