The Ultimate WiFi Security Guide: Government Agent's Tips You Can Do at Home for Free
When was the last time you thought about your WiFi router? Let me guess: When your internet connection got sketchy, and you made your magic move - disconnecting the power cord, waiting 10 seconds, and then reconnecting. Poof! You were able to reboot it and were up and running again, after a sigh of relief. But I know hackers, and you won't believe how much they care about your little old router. They treasure it - because they’re just drooling to pave it into a speedway of stolen data:
- All of your devices? Hacked.
- Everyone who ever visits your home? Personal information breached.
- All of your most sensitive financial and personal data? Robbed - and then sold for a fraction of its worth on the dark web.
Don't be surprised if somebody makes a huge donation in your name to a fake front organization or takes out a mortgage using your identity.
And your problems could just be starting. Once hackers break into your home network, they have access to your laptops, smart security cameras, and other connected devices - including the webcam you use to Zoom or Skype with friends and family.
Not only will the hackers easily discover where you live - but they’ll know the age of your children and where they go to school. And they might sell your internet access to pedophiles and perverts on the dark web, turning your home into a perv theme park.
These risks started before your home network was even up and running
Like many other home internet users, you probably got your WiFi router from your Internet Service Provider (ISP). To pad their bottom line, ISPs are notorious for providing some of the most basic routers on the market - while limiting you to 2G or 5G connection speeds.
They provide millions of these basic, techno-skimpy routers - making users a prime target for spy agencies and other bad guys. In fact, because hackers put most of their efforts into finding new weaknesses to exploit, the odds that they'll find them is only a matter of time. These vulnerabilities provide them a master key to millions of homes.
You would think that the company that gives you secure internet access is also protecting your privacy. But it isn't. The ISP router comes with default keys and passwords that enable the company to spy on you. They may say they need your information to maintain their quality of service. But your ISP is also in the money-making business of keeping your data accessible for target-marketing purposes.
And on top of all that, the IP address that identifies your specific router's access to the internet contains nodes and gateways, which enable hackers to find out who you are. However, while you need an IP address to have internet access, it’s also possible to hide your address from hackers and your ISP.
That's where my experience as a federal specialist comes in. I’ve created this router-interface guide based on my experience studying and applying advanced internet security tactics for many public entities. But I’m also a family man - with a deep devotion to protecting my home. Some of my tactical tips to take control of your router may require some special tools and services. However, the vast majority will cost you NOTHING, and you can do it yourself.
Here’s what I’ll cover:
- Router and WiFi passwords
- WiFi network names
- Encryption security settings
- Automated security updates
- Unique guest internet access codes
- Parental controls
- Backdoor Ping hacker access
Plus, I'll give you some pointers on how to choose and manage your passwords. Additionally, I'll provide you with some basic tips for browsing and searching more privately, including the use of Virtual Private Networks (VPNs).
1. Take Control of Your Router
My guide's primary purpose is to make your WiFi router access to the internet more secure from hackers — using the "codes and credentials" that only you will know. However, the "residential gateway" you're renting from your ISP also means you're using all of its gateway codes. Some of the gateway codes your router controls cannot be changed because it makes it possible for you to have internet access. But others are controllable, for example, your password, your network name (or SSID), your guest access, your encryption standards, and the like.
To control these, you need to get into your router's interface — its console. To do this, you also need a username and password (Administration Credentials).Every ISP router comes with a default username and password. The idea is to let you or your ISP technician set up your router by using “universal” administrative credentials. These credentials are public knowledge.
However, suppose you keep these defaults to access your router. In that case, you're also saying, "Yo, Mr. Fox-please guard my hens," as every hacker can use the default access codes, and every tech-savvy visitor to your home could easily log into your router and mess with its innards.
How to Access Your Router’s Settings
Your router consists of embedded service software that controls it — firmware. A router's firmware consists of a console of commands that is your router's interface. The basic way to get to your router's console is to open your browser, go to the address bar and type in the following: "192.168.1.1"
This number is normally the router's IP address, bringing you to the log-in screen of the router console. The screen will look something like this:
 Netgear login screen
Netgear login screen
Sometimes, however, routers use a different IP address. If you don’t know this address, here’s what to do:
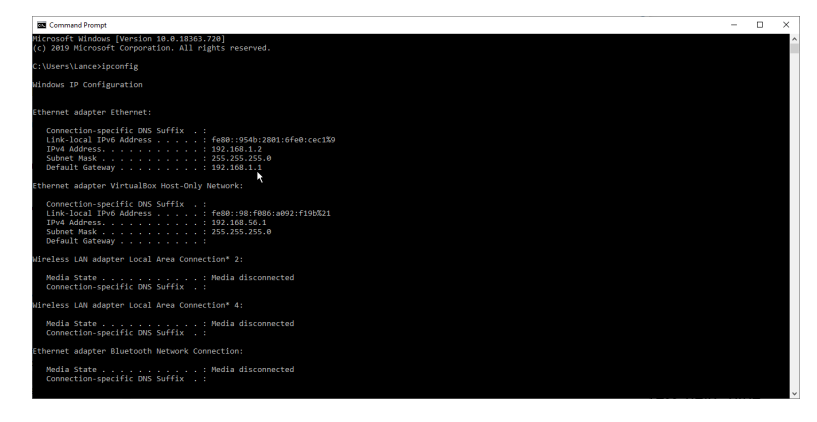
- Type “cmd” in your windows start menu and click Enter. This opens the command prompt.
- Type “ipconfig” in the command prompt, and click Enter.
- Scroll to “Ethernet” or “WiFi” and find the listing for “Default Gateway.” That’s your IP address.
- Copy the address and then paste it into your browser address bar, and you'll get access to the settings screen.
 At this point, you need to enter your user name and password. The entries are the default codes that come with the router. (They could be the codes you've assigned to it if you purchased your router.)
At this point, you need to enter your user name and password. The entries are the default codes that come with the router. (They could be the codes you've assigned to it if you purchased your router.) - If your router is the one you rent from the ISP, you’ll probably be using the router manufacturer’s default codes. In that case, you’ll need to consult the manual that came with the router, or ask your ISP for the codes.
- Don't know where the manual is? No problem. Just look under your router for the serial number. Then, search online for "Router [Manufacturer] [Serial number] Operating Manual". You can also visit a universal list of router default user names and passwords https://cirt.net/passwords and find your specific router codes.
These passwords are well known to hackers and of course, to the ISP technician who may be in your home to help you set up the router. However, don’t worry — only the router you’re using on-site at your home will accept these defaults. Still, if you have visitors to your home who bring their techie but bad-seed child along with them, you may have a problem. So, change the user name and password that you use to access your router.
Note that all routers have a specific way of changing their default administrative credentials. I encourage you to use the manual that comes with your router (or search engine information) to make the changes.
Important Note: Not all Routers were created Equal!
- The rest of the tips I give you in this guide are accompanied by screenshots of a router console - But your router might look a bit different. Router makers have unique interfaces. They sometimes use their own terminology for setting options. For example, NetGear puts its router password option under the "Wireless" menu, while Edimax puts it under "Administration" and D-Link has it under "Manual Wireless Security Setup."
- I’ve chosen to use screenshots of Netgear’s AC1450 router (an older router, of 2014 vintage) because its firmware interface provides fairly straightforward tabs and options for taking control of your router and enhancing your internet-access security. The intent here is to make you more familiar and comfortable with the types of tabs and settings you’ll see in your make and model.
- To make the required changes, consult your router’s manual. For screenshots, you can also visit PortForward or Setuprouter to make you more comfortable with changing settings in your specific console.
In Netgear AC1450, logging onto the router console brings you to the following screen:
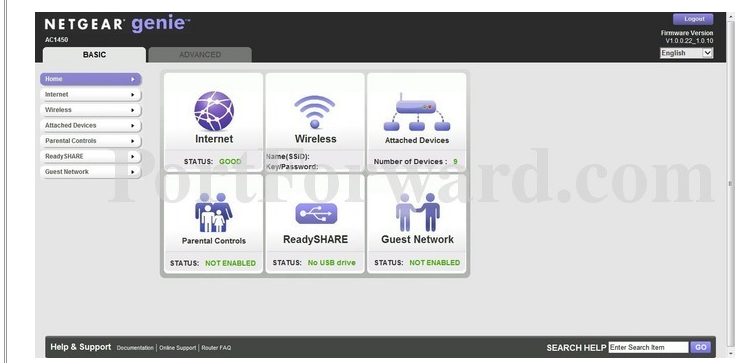 Say hello to your router interface
Say hello to your router interface
You can see the options along the left-hand tabs, plus the icons across the middle, which also give you the “status” of these options.
Routers normally offer two top tabs - “Basic” and “Advanced”.
The Basic tab give you information about the router and your internet access stats. The Advanced tab give you the options for changing the settings. You might want to click on all of the available tabs to see what your router offers.
Yes, I know you think you’ll screw something up, and you’ll have to admit to your ISP that you just didn’t trust the router or the settings the ISP palmed off on you. Bah! Take control. It’s easy, and you will always have the choice of making your decision permanent (“Apply” usually), or “Cancel” to go back to the previous screen.
2. Change the Two WiFi Internet Access Identifiers
You use a WiFi password to access the internet through your router, but did you know that your network has another identification code that can be a serious risk? That is your WiFi's “network name” (Service Set Identifier, or SSID), which designates the “channels” (or the networks) your ISP is giving you to access the web. In short, that's the network name your neighbors can see and also cybercriminals and pervs who want to hack your nanny cam.
You’ll find the SSID on your computer or mobile device by clicking on the icon that shows your “Network and Internet Settings.” (When you get disconnected from your internet connection, you click on this setting->your network name to reconnect. Most people are using both the password and the SSID your ISP gave them as default codes with the router. The problem is, your ISP probably doesn’t provide each consumer a unique password. For instance, it may assign “stormynight 465” to one user while assigning “stormynight327” to another. In addition, an ISP normally assigns an SSID designation that includes the name of the ISP itself - for example, “MyComcast5G1234.”
Yup, you guessed it. These defaults are what hackers look for. If they know who your service provider is, they can start guessing the type of router you have. That’s when they begin brute-force attacking - inputting all possible combinations of alphanumeric codes to locate a password. Of course, knowing some of the password prefixes, your ISP assigns may be a drool factor for any hacker.
Why would you let anyone else assign you a personal password? So change these two internet-access identifiers now - and make a point of it to change them on a regular, periodic basis.
How to Change Your WiFi Password
Before you start, take a look at your manual (or your search engine information) for the router tabs to change your specific password. Here's how it goes with my example router:
- At the "Basic Home" screen, click on the “Advanced” tab on top. It brings you to the “Advanced Home” screen:
- Click on “WPS Wizard.” Scroll down to the side tab “Administration.” Click.
- Sub-options include “Set Password,” bringing you to the following screen:
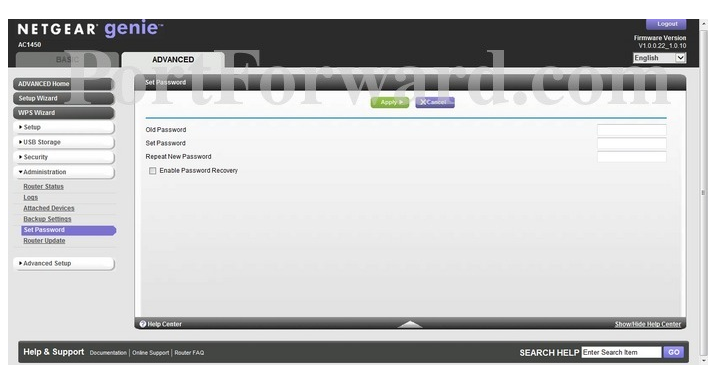
- Click “Old Password” and enter the password.
Click “Set Password” and enter your new password (see Textbox 1). Click on “Repeat New Password” and re-enter your new password.
Before I tell you how to change your SSID (your network name), it's important that you carefully consider your password.
How do I choose the right password?
You probably have many passwords you use — social media, online shopping accounts, an email password, an internet password, and passwords to access your browser app stores.
Wow, so much to remember. You might become “password-weary”. It simply means that you use a combination of the same alphanumeric codes over and over again.
Many users — even high-ranking government officials - tend to choose a password they can't forget, like "123456789." This is the most archaic, most well-known password since "Open Sesame.” Perhaps with less creativity, users will choose their phone number. By presenting a fake family emergency, attackers can easily manipulate you or people close to you to get the digits. It would be best if you choose the right password. Here are my best tips for picking passwords:
- Use complicated (“longtail”) passwords - containing letters, numbers, and symbols.
- Don’t become password weary - use a different password for each account or application.
- Choose a difficult security question for your accounts - or use false answers to easy questions.
- Recognize the difference between “http” and “https” sites. The added “s” in http means that it is a secured website. Don’t ever set up password-protected accounts or make any purchase on “http”-only sites.
- Consider using easy-to-remember passphrases. Name the phrase after a line in your favorite movie or literary piece: “hastalavistababy” or “statelyplumpbuckmulligan”. But add another element to make it harder to guess - and stick it in the middle — for example, a random number. So “hastalavistababy” becomes “hastalavis7103tababy”.
- Don’t give people your WiFi password - especially people who just quickly stop by, like salespeople. Tell them to rather use their mobile data.
- Change your passwords (even your router’s) on a regular, periodic basis.
Better: Use a Password Management App
- It isn't easy trying to remember all the passwords you have. Long strings of alphanumeric passwords take time and energy to recall.
- A password management tool remembers all of your phrases for you — in encrypted form. All you need is one master password to access the tool.
- While most web browsers provide a password management service, they're not nearly as secure or private as a password management app under your control.
- Invest; It's cheap and simple and can save you from hackers. Here you can find the Best Password Managers around.
Your password to access the internet is the brute-force attack point where hackers make their living by pounding away furiously at their keyboards until their mass combinations of alphanumeric code strings hit on one that works.
3. How to Change Your SSID
Again, finding your network name on your PC, laptop, or mobile device is easy. You can get to it by clicking on a WiFi icon on your lower taskbar or your desktop or going to your Settings and clicking on the "WiFi "tab.
If you haven’t changed the designation from the default name provided by your ISP, then you can easily recognize it as your ISP’s name with probably a bunch of other numbers or codes. However, when you click on the icon that shows you your SSID, that particular screen shows not only your network but also those that may be in the broadcast range of your route - including your neighbors.
But let’s say your residence is near a public WiFi hotspot - like a café. Any intruder may click on that network and also see the other nearby network names. So if you’re still using your ISP’s default, that intruder will now have the name of your ISP.They can narrow down the router type you use just by knowing the rudimentary routers that the ISP is renting out.
It’s important that, as with your router password, you change the network name to something secure.
Don’t use your last name, name of your street, or phone number digits. Don’t use your pet’s name or anything that may link you or your family’s identity to the network name.
,strong.One last tip: Your ISP’s manual may caution you against changing the network setting. Why? In my experience, the reason is the same as why your ISP doesn’t want you to change their defaults - changing the manufacturer’s “network” name means that it will no longer be able to track you so easily.
For the Netgear AC1450, you can change the network name in the “Basic tab“ (contrary to expectations):
- Go to the “Basic” home screen (already shown) and click on “Wireless”— whether the side tab or the central icon. Here’s the screen you’ll get:
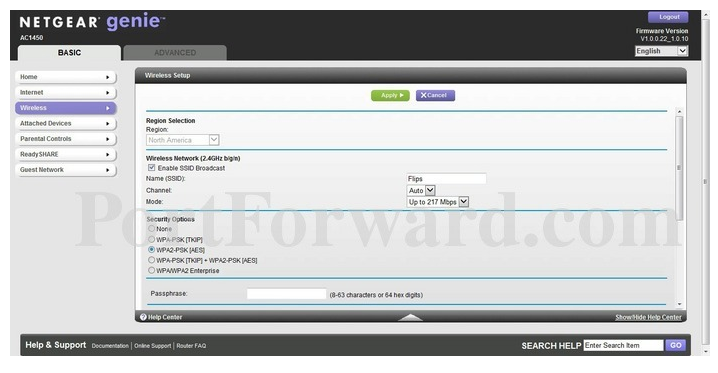
- Scroll down to the bottom box “Passphrase.” Type in your new network name.
Scroll back up toward the top and click “Apply.”
You’ll see that, later on, you’ll get the hang of manipulating your network name when you change your Guest Network to let visitors have their own access, not yours, to your home internet.
4. Enhance the Router Encryption
Encryption protocols scramble the data that take you to and from websites. Intruders and hackers who are trying to intercept your whereabouts on the internet may know that you’re on the internet, but the scrambled data is unrecognizable, making it basically useless for attackers to follow you when purchasing a product online using your credit card.
Your router controls the encryption standards for your WiFi access. However, ISPs don’t always turn on these protocols by default. Why not?
Well, some fear it will impact performance or just not aware of its importance. Others want to keep an eye on your internet whereabouts because they can sell your website preferences to data brokers as part of the massive Consumer Data Analytics Industry. But don't worry; You can easily switch on the necessary protocols yourself.
The most common WiFi security types are WEP, WPA, and WPA2.
WEP stands for Wired Equivalent Privacy. It was the initial wireless encryption protocol to emulate the encryption available on traditional wired networks. However, hackers were fairly quick to crack the WEP’s encryption security codes, and the WiFi Alliance (which establishes and sets wireless encryption standards) came up with a new protocol - WPA.
When you go to router’s encryption settings, don’t ever have that WEP checkbox marked.
WPA - or WiFi Protected Access - debuted in 2004 and fixed many of the security gaps of WEP. However, it was merely a stopgap protocol because it wasn’t equipped with Advanced Encryption Standard (AES) technology.
AES is essentially a set of cryptographic ciphers, or data packets encrypted by algorithms between a server and a device. The WiFi Alliance fixed that problem a couple of years later with the release of WPA2 (AES). That was the standard and most robust wireless encryption protocol until 2018, when the Alliance released WPA3, offering much stronger AES technology. WPA3 is not available on all routers, obviously, but it is meant to provide greater security protection for weak passwords and public WiFi spots like hotels and airports.
The bottom line is: if your router offers only WEP or only WPA - go and get yourself a new router. If it provides a choice between WPA2 and WPA3 - go with WPA3.
How to turn on the WPA encryption standard
Because the Netgear AC1450 router was manufactured in 2014, it doesn’t offer a WPA3 option. Instead, it provides several WPA “security options” for WPA2.
On the Netgear AC1450 - Go to the main page of the router console.
- Click on the top tab “Advanced.”
- Click on the side tab “WPS Wizard.” This brings up the following screen:
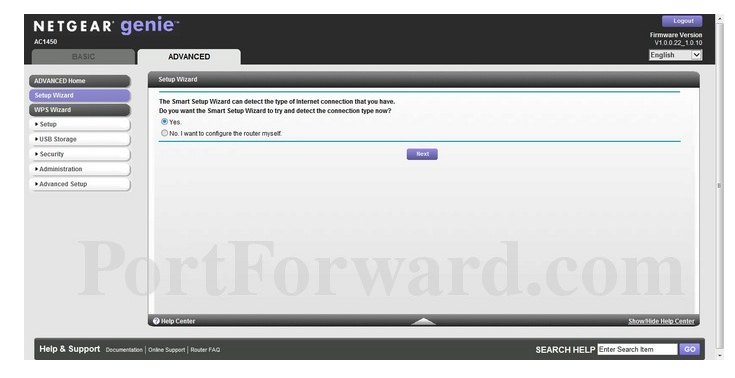
- Click “Next.”
That’s what you want to do - take control. But remember, you can always cancel a screen or have a “return to previous” screen option if you’re on the wrong track. Be encouraged, however, if you’re following the 6-year-old Netgear router screenshots I’m showing you; then you’ll be able to find the router settings you’ll be in control of, even in a newer router.
So now set your AC1450 encryption standard:
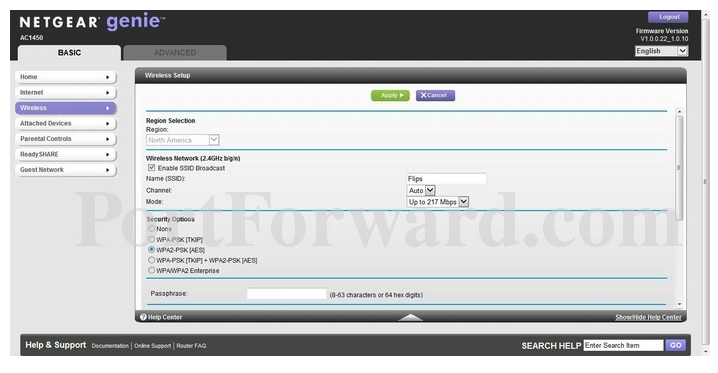
- Scroll down to “Wireless Setup” and click.
- Go to the side tabs under “Security Options,” and click on WPA2-PSK (AES).
You may see other options. “TKIP” is a legacy key that would enable the router to go beyond WEP if necessary. “Enterprise” means only that the security option is one that a company, not a residence, would use.
It’s important only to remember - choose your WPA2 or WPA3 router buttons (with or without the PSK designation) with “AES” in parentheses.
While you’re at it, shut down “WPS” on any router; WPS means WiFi Protected Setup. It started as a good idea - a protocol that enables you to bypass passwords to connect devices (gaming consoles particularly) to your router. Instead, you connect the device and simply press a button on the router or enter an 8-digit PIN where prompted on the device screen.
However, because it is a password bypass, hackers found ways to exploit it, cracking it using brute force - in turn revealing your WiFi password.
The other problem is - this WPS feature normally is turned on by default with your ISP router. Turn it off.
On the Netgear AC1450:
- Go From where you are in changing your “Security Options” (the “WPS Advanced Wizard” tab), scroll down to the “Wireless Settings” and click on it.
- Scroll down to “Advanced Setup.”
- Click on “Wireless Settings”
- Click on the box that says: “Disable Router’s PIN.” (Note: on this specific computer, the router’s PIN is controlled by WPS, so disabling the PIN disables WPS.)
- Again, consult your router manual or online information for locating and disabling WPS.
ISP routers should offer automated firmware updates to ensure every security fix will be rolled out to your network. Not all of the routers provide this feature, depending on their age. Those that do have this feature may not have this box checked as a default setting. Just go to the firmware section and turn it on.
5. Create your Own Guest Network
You love your friends and love to have them visit you. For at least some of their visit time they’ll have their nose in their mobile device or will want to hook up their laptop to your network - hopefully not to present a slideshow of their vacation photos. In any case, the inevitable question will be: “What’s your WiFi password?”
You've probably given your password without even a second thought. But do you know if your friends' devices are free of malware and other bugs? If it's not, then your network will become infected, and you could carry it over to your work or other friends, contaminating their networks. Also, you're not sure what sites they might visit during their visit - sites that may also contain malicious codes. Fortunately, most routers offer guest networks that you can isolate from your regular home network.
On the Netgear AC1450:
- Go to the home screen, and click on the top “Advanced” tab.
- Scroll down the side tabs to “WPS Wizard” (by now, you’re familiar with that). Click.
- Scroll down to “Setup.” Click; Scroll down to “Guest Network.” Here’s the screen you’ll see.
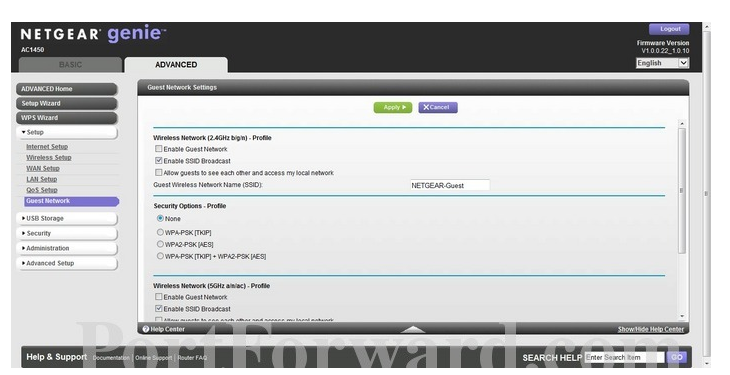
Not all the tabs are displayed. If you scrolled down, you’d find the one for creating your guest network name. Again - as with your network name (the SSID) - don’t create a guest network name that compromises your identity. You’ll also note the security option side tabs that need to be clicked; Again, “WPA2-PSK (AES)”.
6. Enable Parental Controls as Necessary
Most routers provide access to commands that let you monitor or set parameters on your children’s internet access and usage.
The tab for “Parental Controls” will also likely be on your Home page, under “Basic”. On the Netgear AC1450, the screen is the same one you’ve seen already (and many other router makers also make the parental controls easily visible).
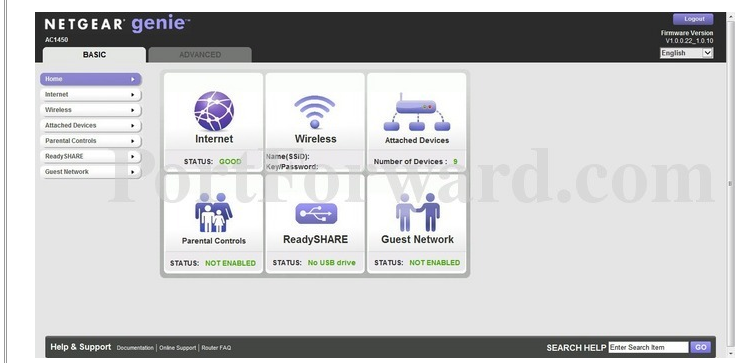
You can see that the status box for Parental Controls is “not enabled”. However, after you click on it, it will take you to a different website to set up your control standards. Not all routers will take you offsite, but they will give you a detailed explanation of control choices and straightforward ways to implement them.
When you’ve configured your Parental Control, you’ll click the button for “Apply” or “Take Me to the Status Screen.” The Parental Control status icon will now indicate “enabled".
7. Disable the Ping Option to Prevent Snooping
The last setting you have to deal with is what is known as Ping.
Ping is a component of the Internet Control Message Protocol (ICMP). The ICMP is an IP diagnostic application that your router uses to create error messages when server network problems block the flow of data to or from websites. It consists of several error codes.
However, Ping is not an “error” - Its basic function is merely to indicate whether a server is online. Ping consists of two codes - echo request and echo reply. You make a request by sending data packets to the server; the server replies with data that acknowledges the request. Some users apply Ping to test their connection speed.
Beyond this dubious utility of Ping, it also provides a way for hackers to “Ping” public WAN IP addresses to check whether they’re valid. So turning it on in your router (or not disabling it) runs the risk of being identified by IP scanners.
The Ping function resides in the Wide Area Network (WAN) interface of a router.
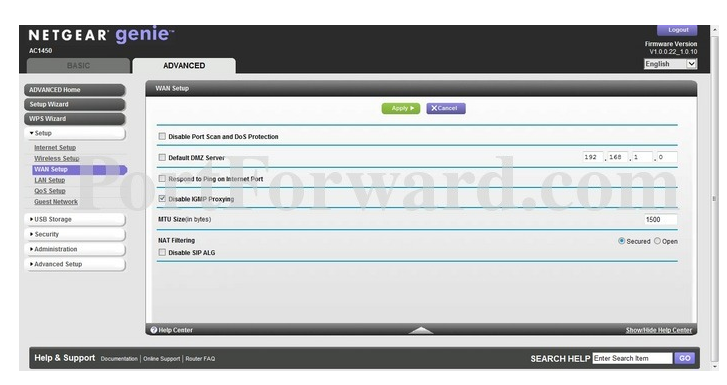
- Go to the home page. Click on the “Advanced” tab on top.
- Scroll down to the side tab “WPS Wizard” and click.
- That brings you to the “Settings” tab. Click, and then scroll down to “WAN Setup”. Click, and you’ll get the following screen:
8. Practice Safer Browsing
All of the router-configuration tips and tools I’ve just given you will make your home network much more secure, and that's a fact. But remember, these are just the first steps along the way to online safety and security.
Hackers have other ways of cracking your privacy. And if you have kids, the different online threats they face - and the special attention they require - will make you strongly consider the following online security tips.
Use private search engines
The most popular search engines you may be using to find the information you need at specific sites - Google, Bing, and Yahoo - have access to your search history and the websites you visit and leave tracking cookies on your device. They intenf to create profiles of you instrumental for targeted advertising in league with data brokers.
However, there are several high-quality search engines alternatives that don’t release information about your searches or website visits. You'll find the safest, most private ones right here.
 Startpage, a secure search engine
Startpage, a secure search engine
Use private browsers
As with search engines, the most popular browsers for navigating to websites - Chrome, Safari, and Internet Explorer - also collect and process information that can reveal your identity, including the personal passwords they promise to manage securely for you. Look into the following private browsers for better, more secure browsing.
Invest in a Virtual Private Network (VPN)
The most secure way to go online and navigate safely and anonymously is to subscribe to a VPN. In a nutshell, here’s how a VPN protects you:
- VPNs Mask Your IP Address - An IP address is the access point you use to connect to the internet. VPNs offer a vast network of remote servers throughout the world, sometimes numbering in the thousands. Each server provides its own IP address. VPNs let you choose which IP address you want to use, legally, to mask the one your prying-eye ISP offers. The masking IP address hides your identity and your location. It’s even invisible to your ISP — which knows you’re logged onto the internet but only to an unidentifiable VPN server.
- Advanced VPNs also offer a strict “no-logs” policy - Your ISP logs your online activities, so it can supposedly monitor the performance of your online experience (or, in reality, sell that data to data brokers). High-quality VPNs don’t maintain any files or records of your ISP address, connection time, or online settings or activity.
- VPNs use “tunneling” encryption technology. It consists of both data encryption and data encapsulation. The flow of data “tunnels” from the remote server through the anonymous IP address to the computer or device you’re using on the internet. The remote servers break down website and app data codes into minute packets of information before entering the data transfer tunnel, encrypting them and shielding them in a layer of control information. At the end of the tunnel, the VPN uses a unique algorithmic key to un-encrypt and un-shield the data in the exact form the website or app presented them.
- VPNs use AES-256 Encryption. The 256-bit AES protocol that VPNs use is certified by the National Institute of Standards and Technology of the U.S. Department of Commerce for use throughout the U.S. Government. It is considered the “gold standard” of encryption technology.
Find out more about how to get a fast VPN and which are the best out there.
You may also consider the option of proxy servers. A proxy server acts as a clandestine portal between your computer and various websites. Similar to a VPN, it conceals your server IP address by substituting it with its own, thereby keeping your identity and location unknown to your ISP. It further encrypts data inquiries and transmissions. However, this alternative possesses fewer supplementary security features and necessitates some technical proficiency.
Some of the high-quality proxy servers include Luminati, MyPrivateProxy (MPP), StormProxies, HighProxies, InstantProxies, Proxy-n-VPN, BuyProxies, Microleaves, YourPrivateProxy 6, Oxylabs.io, and Proxify.
Find out whether you’ve been compromised - either by hackers or breaches
Forewarned is forearmed; Here are some tools to find out more about the status of your online privacy and anonymity:
- The Electronic Frontier’s Panopticlick tool tells you how well you’re protected against non-consensual Web tracking.
- BrowserLeaks lets you know how your device is configured to protect your personal identity data. It’s a site designed particularly for tech-savvy online users, but casual users will find it of interest as well.
- Mybrowserinfo shows you your IP address and information about your browser settings, including whether browser firewall protection and (SSL) encryption technology are enabled.
- At have i been pwned? you can enter your email address to determine whether you have an account that has been compromised by a data breach.
Consider buying your own Router
As you saw in this guide, a router's firmware is filled with holes from the start. Therefore, many experts insist that you purchase your own router for better security. Most of the routers that ISPs rent to you are not top of the line models. If hackers find out which ISP you subscribe to, they'll know which routers your ISP offers. If those specific routers have "backdoor" weaknesses well-known in the hacking community, hackers will come in without knocking. Some experts suggest that you choose a commercial-grade router that small businesses would use.
 An advanced Linksys router, that goes for about $150
An advanced Linksys router, that goes for about $150
Yeah, it's going to cost you more than the $10/month you pay for your ISP router, but think about it this way: A secure, sophisticated router - one that automatically upgrades security and encryption settings, for instance - is an investment. A High-End router might cost you $120 to $200, But you'll reach such a cost after a year or two with your leaky ISO router anyway. Such an investment isn't for every household; it will give you a safer network with better control.
Bottom Line
My role as a security advisor took me to many places, and I've faced some advanced threat actors in my days. And while I try not to take my work home, some practices are just essential for every family man: safer router settings, home network control, safer browsing, and I'd add a VPN. I have shared these practices with you because I know that while internet access is a privilege, it doesn’t come without perils. Many innocent users have had their accounts hacked or breached - and from that has come frustration, angst, and tragedy. So please, take these WiFi security practices into your own home, so your family can enjoy everything the web has to offer without fear.




Please, comment on how to improve this article. Your feedback matters!