Twingate is a relatively new VPN alternative that uses a zero-trust model, and keeps your business and personal traffic separate. It’s not a VPN, and I quickly learned that Twingate is an entirely different tool. It allows you to set up secured proxy access to your organization's online resources, invisible to the rest of the internet.
The access is centrally managed, based on user-identity authentication via SSO and 2FA. This presents a more secure means of remotely accessing business infrastructure than your standard IP-based access. You can easily enable granular access for your employees throughout the world, and it offers similar levels of encryption and protection from hackers that you expect from a VPN.
However, it seems that by adopting this model you may be missing out on things that you may expect from a typical business VPN. From kill switches to the ability to bypass geoblocks, you may struggle to accomplish tasks you easily manage with a VPN. Currently there’s no port-access either to easily add temporary access when needed.
I had a good look at Twingate’s features to see if it’s a good substitute for a business VPN — it may not suit all companies.
Try Twingate Risk-Free Now!
Important. This VPN is primarily marketed towards businesses. Unlike most personal VPNs we review, it's not necessarily designed for activities like streaming and gaming. Therefore, consider that its overall score may be impacted since we grade every VPN using the same categories. To make an informed decision, read on to see how the VPN performed in the areas that matter most to your business.
Twingate Pros, Cons, and Needed Improvements
-
Good security
Even though you don’t connect to servers, the service provides strong encryption and robust identity-based authentication.
-
Free offer
Up to 5 users can connect free of charge, which is excellent if you’re running a small operation.
-
Fast speeds
This provider lets you distinguish between personal and business traffic, so you can get faster speeds for video calls.
Twingate Features — 2025 Update
6.8
|
💸
Price
|
5.00 USD/month
|
|
📝
Does VPN keep logs?
|
No |
|
🖥
Number of servers
|
31+ |
|
🛡
Kill switch
|
Yes |
|
🗺
Based in country
|
United States |
|
🛠
Support
|
Via Email |
|
📥
Supports torrenting
|
No |
Speeds — Segregates Personal High-Speed Traffic
5.0
Twingate could be faster overall than traditional business VPNs, as it uses split-tunnelling to segregate your personal and business traffic. This means that only items specifically designated as a business resource will go through Twingate. So, anything that doesn’t need to be access controlled by your corporation is not routed. This refers to streaming, video calling, and even gaming — if it’s not part of your corporation, it won’t be routed. This means your speeds won’t be affected by Twingate.
 Thanks to split-tunnelling, you don’t need to disconnect to improve speeds
Thanks to split-tunnelling, you don’t need to disconnect to improve speeds
With a regular VPN, you’d first need to connect to a location next to the local network you need to access. If you’re in a different part of the world, it would take a long time for your information to be encrypted and transmitted. Twingate eliminates the need to connect to a faraway server, and disconnect for some activities. Just don’t expect the added benefit of accessing geo-blocked content like certain streaming sites, or torrenting, for example — this isn’t designed for that.
It’s impossible to gather a speed-test result from traditional sites like Ookla while actually accessing a business resource through Twingate, because Ookla itself won’t be designated as your business resource. Normally, encryption will lower speeds a little bit, but you’re unlikely to be significantly affected by this unless you’re downloading huge amounts of data.
Server Network — Centrally Managed User Access
5.0
Twingate doesn’t have a traditional VPN network. Instead, it allows you to access your business resources through a proxy connection. This could be files, servers, or a gateway, for example.
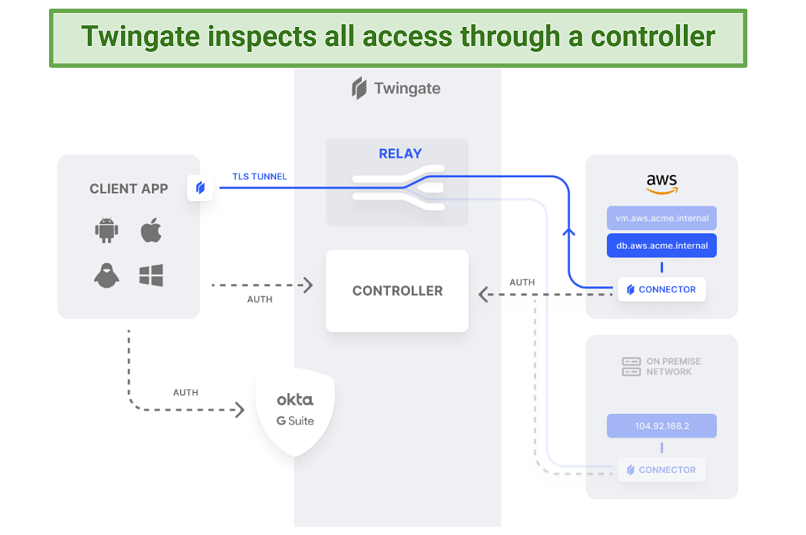 The twingate setup is more complicated than a traditional VPN
The twingate setup is more complicated than a traditional VPN
It works with 4 main components. The Twingate app detects the requirement for business resource access and forwards the request to the controller, where the user’s permissions are verified. This is then forwarded to the connector which ensures the connection is genuine (resolving the DNS request), and enables TLS encrypted access to the business resource via the relay.
If the files you’re trying to access are a defined business resource, the controller will grant you access to it. However, if you’re trying to access a website that’s normally available, you’ll be able to access it without going through the relay.
Your IP address changes only when you access business resources on the connector, as Twingate establishes a proxy connection to it. This means you could be anywhere in the world, but still appear to be sitting in the office whenever you need secure access to business material.
If this sounds overly complicated and you’d rather explore more familiar VPN setups, have a look at these top business providers.
Security — Differs From a Business VPN
5.0
Twingate operates on a zero-trust network, and uses application-level filters for user-identity-based authentication — not network-level. This means that whenever you access a resource, you’ll only be given access to that file, not the entire network. In case of a security breach, only that specific resource would be compromised.
The system administrator gives granular permissions, so that only specific groups of people or individuals can access a certain resource. This is a very helpful management tool, as one app allows you to control the entire network. It’s significantly more straightforward than trying to achieve this with a traditional VPN.
Authentication is achieved using SSO methods like Okta and Google. Not only is this a well-protected account but it allows for second factor authentication. Twingate uses native 2FA functionality so you can make use of this extra layer of safety even if your SSO doesn’t natively have it.
Your business resources are invisible with no internet-facing gateway, with the obvious exception of those who have access to the network. Split tunneling always ensures defined business traffic passes through Twingate, regardless of where you are — on hotel WiFi, a cafe, or at home.
I contacted Twingate to confirm the type of encryption used. While data is being transferred, it is secured via SSL/TLS. When the data is at rest, it is protected by Google cloud services featuring AES-256 encryption, with symmetric keys. Data keys are encrypted using a regularly changed master key, stored in a secure keystore.
You might miss certain features associated with standard business VPNs, like a kill-switch to ensure that everything goes through an encrypted tunnel without exception. With Twingate, it’s down to the business to decide what does. There might be a business need to routinely change IP addresses to certain locations, too.
Privacy — Collects Data but Separates Personal Traffic
5.0
Twingate does collect some of your information. Mostly this is standard information needed to set up your account, or for diagnostic purposes. Some of it is voluntary but the ways that Twingate might use it is spelled out clearly in the privacy policy.
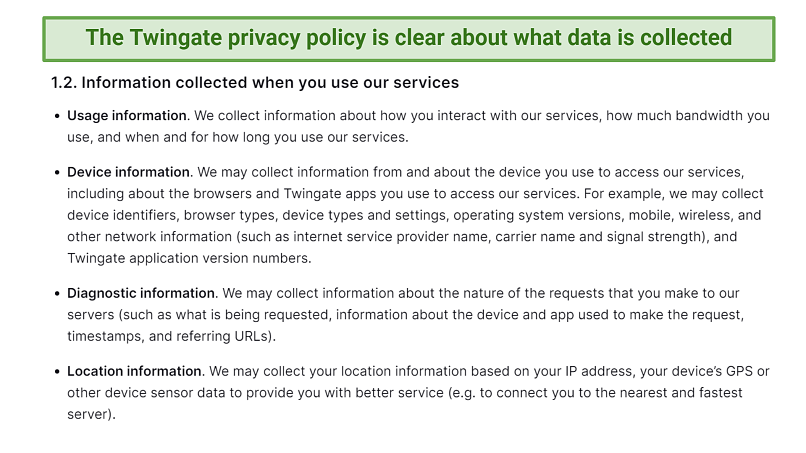 You can find the privacy policy easily and it spells out what happens to your data
You can find the privacy policy easily and it spells out what happens to your data
With its many integrations, it's important to note that Twingate will collect data from the third-party applications that you use in conjunction with it. However, it is not capable of reading data that is not routed through it, meaning it won't record your personal activities, like video calls or instant messages, which are not going through its network.
However, it is based in the US which is a member of the 5 Eyes Alliance. Although Twingate says it will fight any demands for your data, this does mean that your data could potentially be claimed by any member countries. If this is a concern, take a look at these standard VPNs with solid privacy policies.
Does Twingate Work in China? Yes
Twingate support confirmed that it will work in China. This is good news if you have employees located there that need to access essential business resources. It will be as if they’re in the office as usual.
Simultaneous Device Connections — Unlimited Depending on Offer
The basic offer allows up to Unlimited simultaneous device connections. This is per user, and allows up to 50 users. The business offer lets you increase the number of users to 150 though the device limit stays at 5.
However, if you need more than this you can choose the bespoke enterprise account which allows unlimited device connections (as well as unlimited users).
Device Compatibility — Works with all Major Platforms
Twingate works with all the most popular platforms, including Windows, Mac, Android, iOS, Linux, and Chrome OS.
Installation & Apps
8.0
Set-Up & Installation — IT Specialist Knowledge Recommended
Initial set-up requires a few extra steps from the account admin, firstly by choosing a sign-in method: Google, GitHub, Microsoft, or LinkedIn.
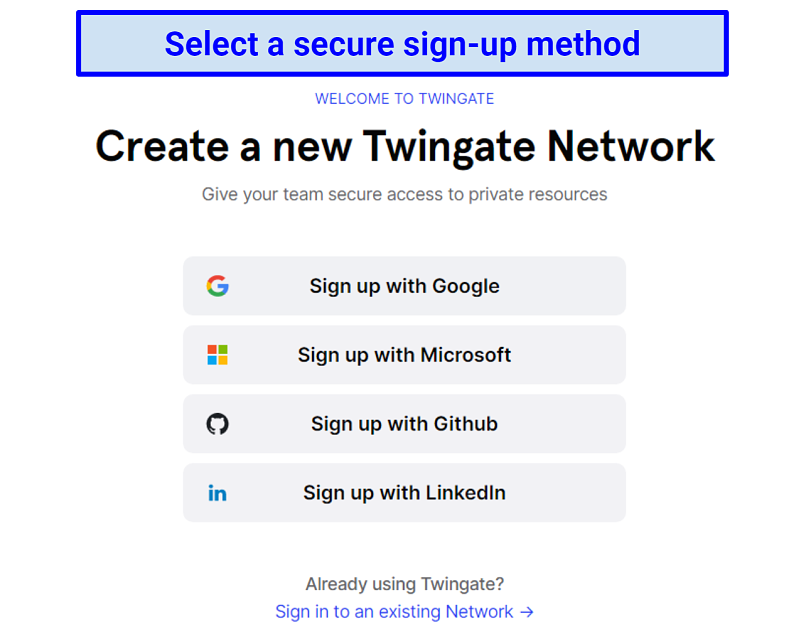 Chances are your business will be using one of these sign-in methods already
Chances are your business will be using one of these sign-in methods already
Next the domain name needs to be established. This will be the name new users log in with when they’re first getting connected to the network.

You can choose any domain name, so long as it’s not already taken
Once you sign up you are immediately redirected to a streamlined dashboard, where you are given the option to try the product, it even offers a calendar to set up a time. I had an automated message from customer support outlining what to do next.
I added my network (Google Cloud), and then set up the connector. The network administrator setting this up should have relatively high-level IT knowledge — the connector is deployed using command lines with Azure, Helm, or Docker. However, there are installation guides and support on hand if you need it.
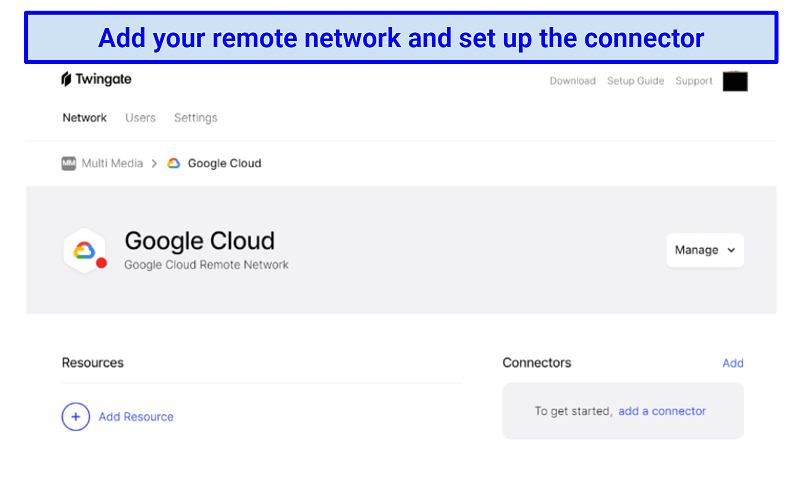 Some steps may require experienced IT personnel to complete the setup process
Some steps may require experienced IT personnel to complete the setup process
Then it’s just a case of adding your resources, and adding any new users via their email address. There is currently no port-level access, but this is all part of the approach of a super-secure zero-trust network. Whenever you access a business resource now, so long as it’s been defined it will be just as easy to access as if you were physically in the office (if you have one).