What is a Keylogger? How to Detect Spyware on a Computer
Is your computer acting a little… off lately? Maybe your cursor jumps unexpectedly, your passwords stop working, or strange pop-ups appear out of nowhere. While it’s easy to brush off these occurrences as bugs or bad luck, they might actually point to something far more sinister — like someone secretly watching every keystroke you type.
What is a keylogger, and how does it work? A keylogger is a type of spyware designed to secretly record everything you type — passwords, messages, credit card numbers — and send that information to cybercriminals. According to SpyCloud’s report, 61% of data breaches in 2023 were related to malware, with infostealers (like keyloggers) playing a major role1.
In this article, I’ll break down exactly how keyloggers work. You’ll learn how to spot the warning signs, run effective scans, and remove spyware if it’s already there. Most importantly, I’ll show you how to prevent keyloggers from compromising your device in the first place, with practical tips anyone can follow — no tech expertise required.
Short on Time? Here are the Best Ways to Remove Keyloggers in 2026
- Run a full antivirus scan — Use trusted antivirus software to do a complete system scan. Most modern antivirus tools can detect and remove keyloggers automatically.
- Manually remove suspicious programs — Head to your list of installed programs and uninstall anything unfamiliar or that you didn’t intentionally install.
- Check your browser extensions — Keyloggers can sometimes sneak in through shady browser add-ons. Go through your extensions and remove anything you don’t recognize or trust.
- Install system updates — Make sure your operating system and all apps are up to date. Security patches often fix vulnerabilities that keyloggers exploit.
- Use system restore — If things still feel off, roll your system back to a point before the problems started. This can undo changes made by malware.
What Is a Keylogger and Why Is It Dangerous?
A keylogger (short for keystroke logger) is a sneaky type of software or device that secretly records everything you type. Whether you’re on a computer or phone, a keylogger can silently track your keystrokes, including passwords, credit card numbers, private messages, and other sensitive information. Some can even affect secondary devices connected via USB or charging cables. Keylogging and other device-based surveillance methods were present in 7% of federal cyberstalking cases in 20232.
What makes keyloggers especially dangerous is how quietly they operate. Most of them don’t trigger any obvious warnings — they silently run in the background, collecting data without you noticing. And in more advanced cases, keyloggers don’t just record what you type — they can also monitor how you type, including the timing, duration, and rhythm of each keystroke. This data can be used to build detailed user profiles or bypass behavioral authentication systems.
Here’s a summary of what makes them a serious threat to both individuals and businesses:
- They steal personal data. Keyloggers can grab your login info, banking details, and private conversations, which could lead to identity theft or financial fraud.
- They’re used for corporate spying. In businesses, attackers may use them to steal trade secrets, internal documents, or confidential emails.
- They invade your privacy. Beyond stealing data, keyloggers can monitor everything you do online, including your chats, searches, and more.
- They pave the way for bigger threats. The stolen data can be used in targeted phishing scams, ransomware attacks, or to gain access to important accounts and systems.
Is a Keylogger Malware or Spyware: What’s the Difference?
A keylogger is classified as malware if it’s installed on your device without your knowledge or consent — say, through a phishing email, shady download, or infected software. Its goal is to gain unauthorized access to your system and steal sensitive data like login credentials or financial information.
Spyware is a specific type of malware that focuses on secretly monitoring your activity. When a keylogger runs in the background without your awareness, quietly collecting your keystrokes and sending them to a third party, it's considered spyware. In many cases, keyloggers are both spyware and malware.
But not all keyloggers are malicious. Some keyloggers are used for legitimate reasons, such as:
- Parental controls. Parents may use them to monitor their children’s online activity for safety.
- Workplace monitoring. Employers might install them to track productivity or prevent data leaks. However, this raises ethical and privacy concerns, especially if employees aren’t informed.
Types of Keyloggers
Keyloggers come in many forms, but they all have the same goal: secretly capturing what you type. They’re generally divided into two main categories — software and hardware keyloggers — with a few variations that blend the two. Let’s break them down in a way that’s easy to understand.
1. Software Keyloggers
These are programs that sneak onto your device — usually when you download an infected file, open a malicious email attachment, or install shady apps. Once active, they record your keystrokes and can send the data straight to cybercriminals. Here are some common types:
- API-based keyloggers. These hook into the system’s APIs (application programming interfaces) to record keystrokes directly from the keyboard input layer.
- Form-grabbing keyloggers. Instead of capturing every keypress, these grab the information you submit in web forms — like usernames, passwords, and credit card numbers — before it gets encrypted.
- Memory-injection keyloggers. These inject malicious code into the memory of running applications, allowing them to hide in plain sight and avoid many traditional antivirus scans.
- Kernel-level keyloggers. They operate at the deepest layer of your system — the kernel. They have high-level access and are incredibly difficult to detect or remove.
2. Hardware Keyloggers
Hardware keyloggers are physical devices used to capture keystrokes by tapping into the connection between your keyboard and computer. Unlike software keyloggers, they require physical access to your device to be installed, which means the attacker needs to be near your computer at least once. Because they don't rely on software, they're often harder to detect. Common types include:
- USB keyloggers. Tiny devices plugged in between your keyboard and the USB port. They intercept and log every keystroke, storing the data on internal memory for later retrieval.
- Wireless keyboard sniffers. Devices that capture keystrokes by intercepting the wireless signals sent between a wireless keyboard and its receiver. They can operate from a short distance and don’t require a direct connection.
- Keyboard overlays. Thin, fake keyboards placed over real ones (especially in places like ATMs) to secretly capture keystrokes like PINs.
- Malicious USB or charging cables. These look and work like regular cables, but they’re secretly equipped with keylogging tech that activates when plugged into your device.
3. Remote Keyloggers
This is a type of software keylogger that doesn't just record data — it sends everything it captures to a remote server controlled by the attacker. These are often bundled with other malware, giving hackers the ability to spy on you and control your device from afar.
4. Hybrid Keyloggers
Some advanced keyloggers combine both hardware and software components to be even more effective. For example, a USB keylogger might also include software that encrypts the captured data and uploads it to a remote server automatically.
How to Detect Keyloggers
Keyloggers are sneaky by design, but there are ways to spot them — either by paying attention to odd behavior on your device or by using trusted security tools that can detect and remove them. The earlier you spot any signs that you’ve been hacked, the better your chances of stopping it before any serious damage is done.
Common Signs of a Keylogger Infection
If your device has been acting strange lately, it might be more than just a fluke. Here are some red flags to watch for:
- Performance issues. Notice lag while typing or using your mouse? Keyloggers run in the background and can slow your system down.
- Unknown processes. You might spot unfamiliar programs running in Task Manager (Windows) or Activity Monitor (macOS).
- Unauthorized settings changes. Things like browser settings, homepages, or installed extensions changing without your input could be a sign.
- Frequent crashes. Keylogger software can cause unexpected system instability.
- Unusual network activity. Since keyloggers often send your data to remote servers, they might cause a spike in outgoing network traffic.
How to Check for Keyloggers Manually
If you’re comfortable digging into your system a bit, here are a few things you can do yourself:
- Look at background processes. Open Task Manager or Activity Monitor and scan for anything you don’t recognize. If something looks suspicious, Google the process name to see if it's legit.
- Check installed programs. Head to your list of installed apps and uninstall anything you don’t remember adding or no longer use.
- Review startup programs. Some keyloggers set themselves to run every time your device boots up. Disabling unnecessary startup programs can help.
- Monitor network traffic. Tools like Wireshark or GlassWire can help you see if data is being sent from your device without your knowledge.
Keylogger Detection Tools
You don’t have to go it alone — there are plenty of trusted tools that can help you detect and remove keyloggers:
- Antivirus software. Many reputable antivirus tools include malware detection that can catch keyloggers.
- Anti-spyware programs. Tools like Malwarebytes are specifically designed to spot and eliminate spyware, including keyloggers.
- Firewalls. A good firewall can alert you to unusual data being sent from your computer, which might indicate keylogger activity.
- Dedicated keylogger detectors. There are even tools made just to detect keyloggers if you want an extra layer of protection, such as Zemana AntiLogger and SpyShelter.
How to Remove a Keylogger
Think your device might be infected? Don’t panic — here are several methods covering how to safely remove a keylogger:
Method 1. Run a Full Antivirus Scan
This is your first line of defense.
Step 1. Boot your computer in Safe Mode
- Windows: Press Shift + Restart, then choose Troubleshoot > Advanced Options > Startup Settings.
- macOS: Hold Shift while your Mac starts up.
Step 2. Update your antivirus definitions
- Open your antivirus software. If you don’t have it, install a reputable antivirus like Malwarebytes, Bitdefender, or Norton.
- Find and run the update option to install the latest definitions.
Step 3. Perform a full system scan
- Choose Full Scan or Deep Scan.
- Let the scan run — it may take a few hours.
- Quarantine or remove anything flagged.
- Run a second scan to double-check the removal.
Method 2. Manually Remove Suspicious Programs
If you prefer a hands-on approach or want to double-check for anything missed by antivirus software:
For Windows
- Open Control Panel > Programs > Programs and Features.
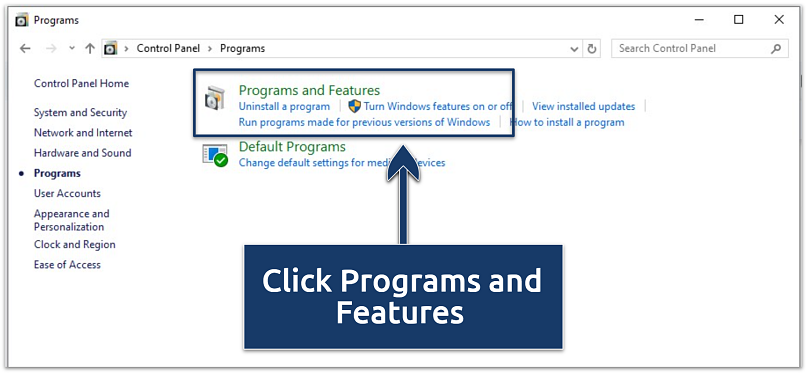 You can identify suspicious running programs from the control panel
You can identify suspicious running programs from the control panel - Sort by install date and look for recently added, unfamiliar programs (e.g., random character names, unknown publishers).
- Right-click any suspicious entries and click Uninstall.
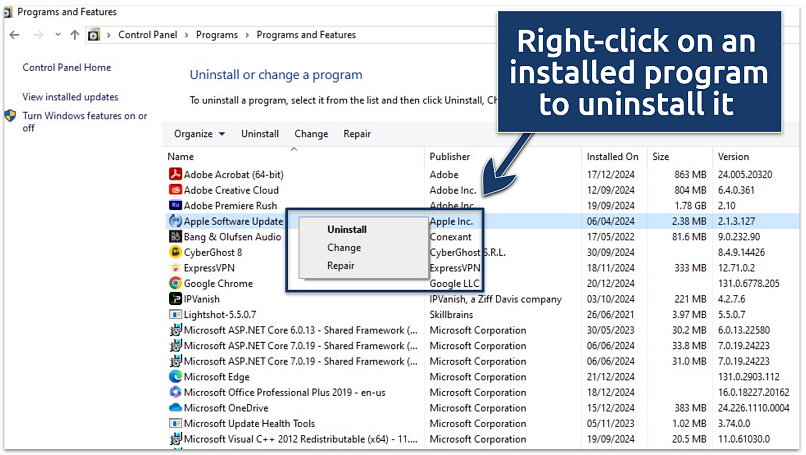 Keyloggers often auto-launch with your system to stay active
Keyloggers often auto-launch with your system to stay active - Press Ctrl + Shift + Esc to open Task Manager and check for odd processes. Look for tasks with unknown names or gibberish, triggers set to run at login or system startup, and unusual or empty authors.
 Do your reserach — you’ll often find forums or trusted sites that flag known malware
Do your reserach — you’ll often find forums or trusted sites that flag known malware - Go to the Startup tab and disable anything unfamiliar.
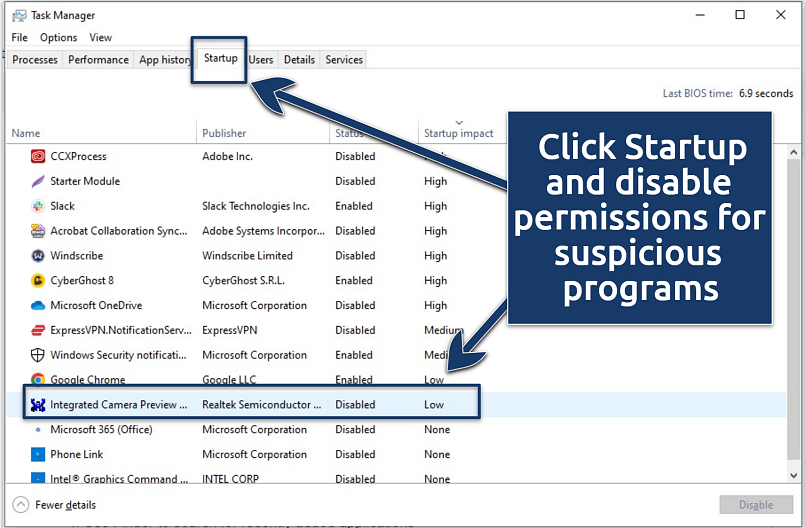 For security reasons and better performance, give startup permissions to only high-priority tasks
For security reasons and better performance, give startup permissions to only high-priority tasks
For macOS
- Open the Applications folder and look for suspicious apps.
- Check System Preferences > Users & Groups > Login Items.
- Use Activity Monitor to scan for unfamiliar processes.
- Delete shady apps by dragging them to Trash, then empty it and restart your system.
Method 3. Check Your Browser Extensions
Some malicious extensions can log keystrokes or compromise your data.
- Open your browser’s Extensions or Add-ons menu.
- Remove anything you don’t recognize or no longer use.
- Check access permissions for the ones you keep.
- Make sure all extensions are up to date.
Method 4. Install System Updates
Security patches can fix vulnerabilities that keyloggers may exploit.
For Windows
- Go to Settings > Update & Security.
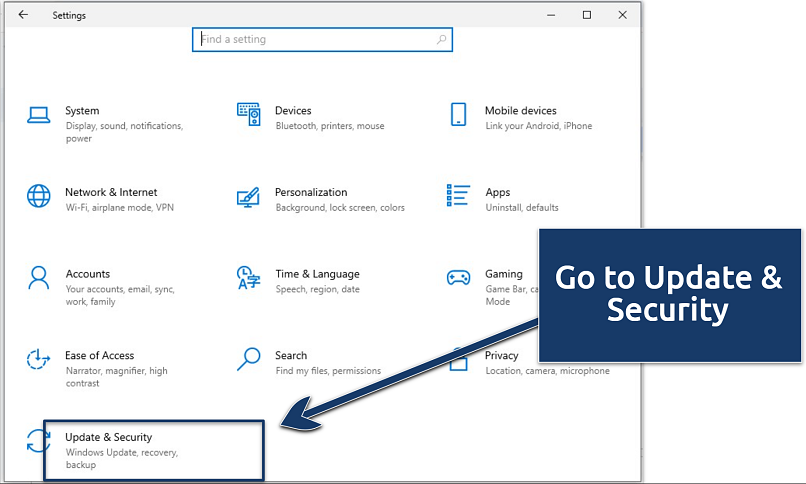 You can allow automatic updates so that your system is always up to date
You can allow automatic updates so that your system is always up to date - Click Check for updates and install everything available.
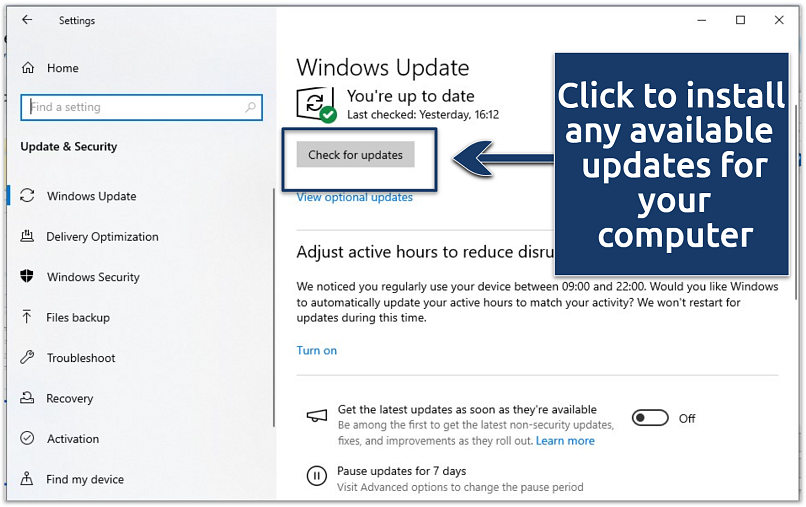 Built-in Microsoft Defender antivirus should be frequently updated to identify the latest threats
Built-in Microsoft Defender antivirus should be frequently updated to identify the latest threats - Restart when prompted and run Windows Defender after updating.
For macOS
- Go to Apple menu > System Preferences > Software Update.
- Install all available updates.
- Enable automatic updates, then restart your Mac.
Method 5. Use System Restore
You can roll your system back to a point before the infection.
For Windows
- Open Control Panel, click the arrow button next to it, and select All Control Panel Items.
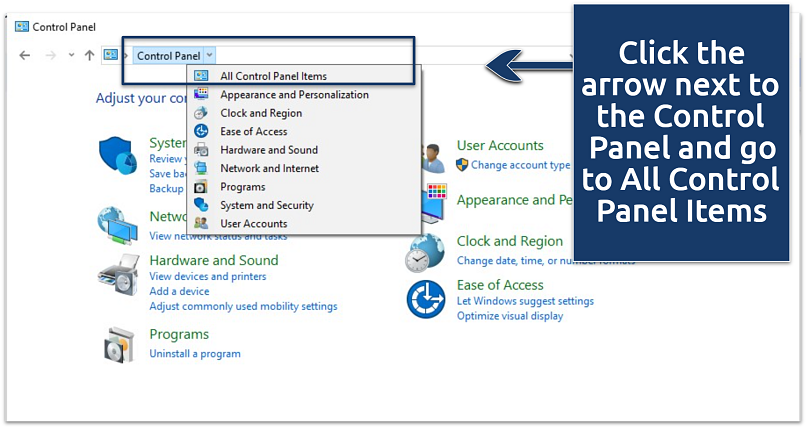 This gives you access to the classic view with all Windows settings
This gives you access to the classic view with all Windows settings - Scroll down to Recovery.
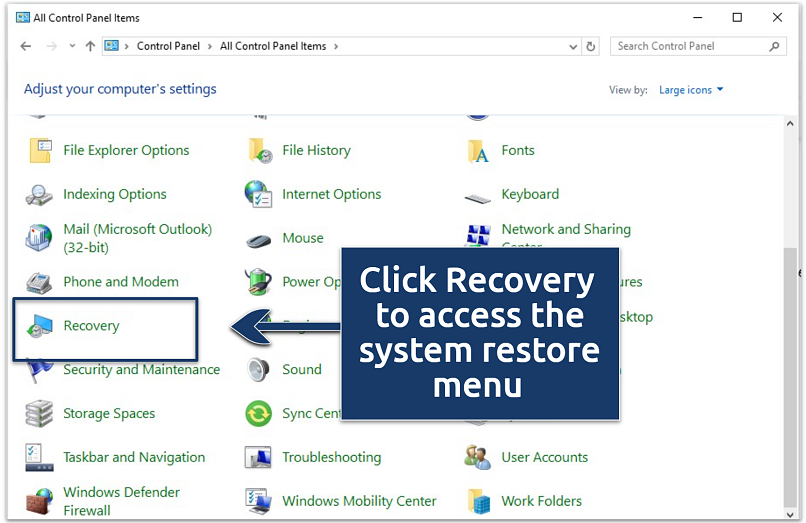 This is where Windows stores tools for fixing system issues
This is where Windows stores tools for fixing system issues - Select Open System Restore.
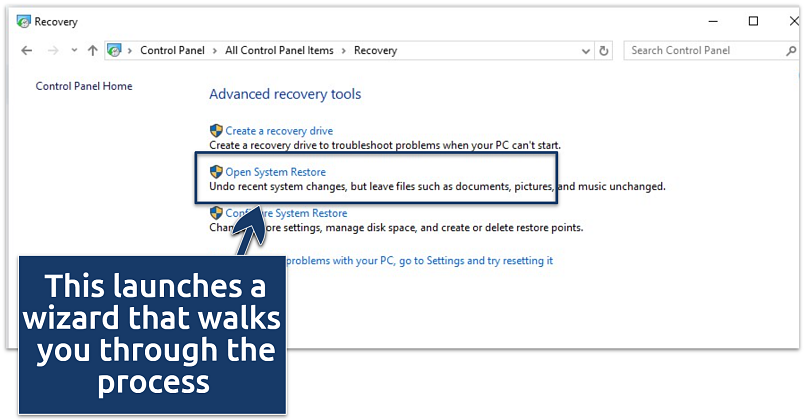 You won’t lose your documents or downloads, but recently installed apps may be removed
You won’t lose your documents or downloads, but recently installed apps may be removed - Confirm you want to restore the system's files and settings.
- Click Choose a different restore point.
- Select a date before the keylogger infection.
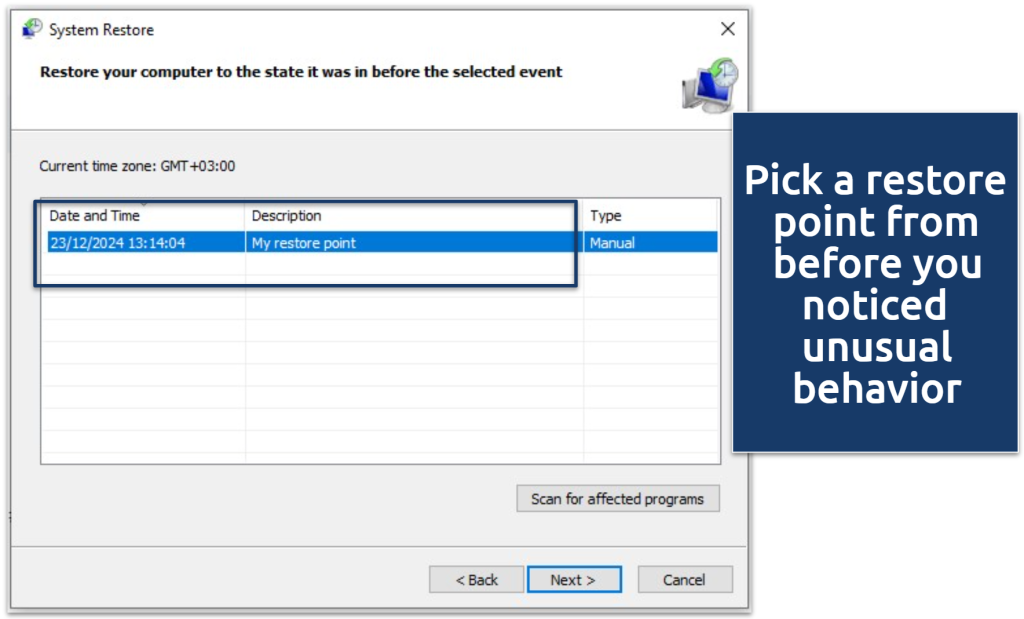 Click “Scan for affected programs” before confirming to see which apps and drivers will be rolled back or removed
Click “Scan for affected programs” before confirming to see which apps and drivers will be rolled back or removed - Confirm and begin the restore process.
- Allow the system to restart.
- Verify system functionality after restoration.
For macOS
Step 1. Boot into macOS Recovery Mode
For Intel Macs:
- Shut down your Mac completely.
- Turn it back on and immediately press and hold Command (⌘) + R.
- Release the keys when the Apple logo or spinning globe appears.
For Apple Silicon (M1/M2/M3) Macs:
- Shut down your Mac.
- Press and hold the power button until you see Loading startup options.
- Click Options > Continue.
Step 2. In the macOS Utilities window, choose Restore From Time Machine Backup and click Continue. Connect your Time Machine backup drive if it isn’t already plugged in.
Step 3. Choose the backup source. Select the disk that contains your Time Machine backups (usually an external drive). Click Continue.
Step 4. Select a backup date. You’ll see a list of available backups. Choose a restore point from before you noticed any suspicious behavior or unusual performance. Click Continue.
Step 5. Choose the destination disk. Select your Mac’s main internal drive (usually called Macintosh HD) as the location to restore. Click Restore to begin.
Step 6. Wait for the restore to complete. The restoration process may take 30 minutes to several hours depending on your backup size and drive speed. Make sure your Mac stays plugged in and do not interrupt the process.
Step 7: Restart and verify your system.
- Once the process finishes, your Mac will restart.
- Check that the suspicious behavior is gone.
- Run a full antivirus/malware scan, and inspect your Applications, Login Items, and Activity Monitor for anything unusual.
- Change your passwords, especially for email, banking, or cloud services you’ve accessed recently.
Method 6. Clean OS Reinstallation
Reinstalling your operating system is one of the most effective ways to remove persistent keyloggers or malware. This method erases your current system files and starts fresh, eliminating most infections. However, it also deletes everything on your drive, so proceed carefully and follow these steps:
Step 1. Back up important files
- Copy your essential documents, photos, and other personal files to an external hard drive or cloud storage.
- Do not back up programs, installers, or full system images, as these could carry malware with them.
- Double-check your backup to make sure nothing important is missing.
Step 2. Create bootable installation media
For Windows:
- Download the Media Creation Tool from Microsoft’s official website.
- Follow the instructions to create a bootable USB drive with a fresh copy of Windows.
For macOS:
- Use macOS Recovery (built into the system) or create a bootable USB installer via Terminal with the createinstallmedia command.
- You’ll need a clean copy of macOS and a USB drive with at least 16GB of space.
Step 3. Prepare for the clean installation
- Disconnect from the internet to prevent early malware contact during setup.
- Insert your bootable USB or DVD into the computer.
- Have any required product keys, serial numbers, or activation info ready.
- If using Windows, back up drivers for rare or older hardware, just in case.
Step 4. Boot from the installation media. Restart your computer and boot from the USB/DVD.
Windows: Enter the BIOS/UEFI menu (usually by pressing F2, F12, Delete, or Esc during startup), and set the USB as the first boot device.
macOS: Hold the Option key during startup and select the USB drive as the startup disk.
Step 5. Perform the clean installation. Follow the on-screen prompts to begin installing the OS. When prompted about where to install:
Windows: Choose Custom: Install Windows only (advanced).
macOS: Open Disk Utility, select your main drive, and click Erase.
Step 6. Complete setup and post-installation security. Once the installation is complete:
- Do not reconnect external drives or restore files yet.
- Install antivirus software immediately.
- Apply all available system updates.
- Before reconnecting external drives or restoring data, scan them with antivirus software.
- Restore only personal files. Do not restore old system images, program backups, or apps unless you are sure they are clean.
- Change all your passwords from this clean system, especially for email, financial services, and cloud accounts.
Step 7. In case of persistent malware (rootkit or firmware-level threats). If the keylogger or malware returns even after a clean OS reinstall, it may be embedded deeper than the operating system.
- Rootkits are a type of malware that hides in core system processes, often at the kernel level, making them difficult to detect or remove.
- BIOS/UEFI malware can infect your system firmware and load even before your OS starts.
In these rare cases:
- Re-flash your BIOS/UEFI with a clean version from the hardware manufacturer.
- Replace the hard drive and perform the clean installation on the new drive.
- Always install from trusted offline installation media.
Method 7. Seek Professional Help
If none of the above methods work — or you're unsure how to proceed — consult a cybersecurity expert to help you remove persistent infections and secure your system.
How to Prevent Keylogging
Preventing cyber attacks, including keylogger infections, requires a combination of best practices, vigilant behavior, and reliable cybersecurity tools to safeguard your devices.
- Install antivirus and anti-spyware software. Use robust antivirus and security software to block keylogger installations. Enable real-time protection and keep the software updated.
- Avoid suspicious links and downloads. Be cautious about clicking on unknown links in emails or on websites. Only download software from trusted sources to avoid installing malware on your device.
- Enable two-factor authentication (2FA). Adding 2FA to your critical accounts provides an extra layer of security, making it much harder for keyloggers to compromise you fully. Even if a hacker manages to steal your password, they’ll still need a second form of verification — like a code, a biometric scan, or a security key — to access your account. Many of these methods work on the same device, but they still raise the bar significantly for attackers.
- Use virtual keyboards. By using virtual keyboards instead of physical keyboards, you can reduce the risk of keylogging on sensitive transactions where keystrokes can be easily captured and used to steal your information.
- Be cautious with public WiFi. Avoid accessing sensitive accounts on public WiFi, as you can be an easy target for hackers. Alternatively, use a VPN to encrypt your data on these networks.
- Monitor device activity. Check your device regularly for unusual processes or unauthorized setting changes that may indicate the presence of a keylogger.
- Inspect hardware. Periodically check for unfamiliar devices connected to your keyboard or USB ports.
- Use secure password managers. Store and autofill passwords online securely, minimizing direct keystroke entry.
- Keep software and systems updated. Keystroke malware can be delivered through zero-day exploits, which makes them particularly stealthy and difficult to detect early. That’s why it’s essential to keep your operating system, browsers, and apps updated — patches often close the security gaps that keyloggers and other malware rely on.
FAQs on Keylogging
Can keyloggers infect my phone?
Yes, keyloggers can infect both Android and iOS phones. Mobile keyloggers often disguise themselves as legitimate apps and can record everything you type, including passwords and messages. They typically gain access through malicious app downloads, phishing links, or compromised public WiFi networks. To protect yourself, only download apps from official stores, keep your operating system updated, and avoid clicking suspicious links.
Can keyloggers steal my bank account information?
Yes, keyloggers can capture your banking credentials and financial information. When you type your bank account numbers, passwords, or credit card details, keyloggers record these keystrokes and send them to cybercriminals. They can even capture screenshots during banking sessions. To protect your financial information, use two-factor authentication and virtual keyboards for banking websites and regularly scan your device for malware.
Do I need special software to detect keyloggers?
Most modern antivirus programs can detect keyloggers effectively. However, dedicated anti-keylogging software provides additional specialized detection features and real-time keystroke encryption. They can identify suspicious keyboard monitoring activities and protect against advanced keylogging techniques that a standard antivirus might miss.
Will resetting my computer remove a keylogger?
A complete factory reset will remove most software-based keyloggers from your computer. However, if the infection goes deep into the reset partition, you may have to reinstall the OS and create new partitions. After resetting or reinstalling, it's crucial to restore files from clean backups only and immediately install security software. Also, hardware keyloggers (physical devices connected between the keyboard and computer) will remain unaffected even if you reset.
How old is keylogging?
Keylogging dates back to the 1970s, when it was first used in typewriter monitoring systems. During the Cold War, Soviet intelligence planted keyloggers in IBM Selectric typewriters at US embassies, transmitting keystrokes via radio signals — an early example of keylogging for espionage.
The first software-based keyloggers appeared in the 1980s, used mainly to monitor employee productivity. Today, keyloggers have evolved into sophisticated tools that can capture keystrokes, screenshots, clipboard data, and even activity on smartphones.
What antivirus can detect keyloggers?
Trusted antivirus programs like Bitdefender, Kaspersky, Norton, McAfee, and Windows Defender can detect and remove most keyloggers. These tools use a mix of signature-based detection and behavior analysis to identify keylogging activity, even if it’s hidden deep within your system. Some security suites also offer real-time protection and anti-spyware features that are especially effective against stealthy keyloggers.
To stay protected, make sure your antivirus is always updated — new keylogger variants appear frequently, and outdated software may not catch the latest threats.
Conclusion
Keyloggers can silently steal sensitive information without leaving obvious traces. They can be deployed through malicious software, compromised hardware, or social engineering tactics, causing damage to individuals and businesses alike.
With the proper knowledge and proactive measures, you can significantly reduce the risk of falling victim to keyloggers. Remember, cybersecurity is an ongoing effort, so staying informed is also crucial to protecting against the latest threats.





Please, comment on how to improve this article. Your feedback matters!