Best VPNs Reviewed By Experts: Top Services for 2024
- How to Choose the Best VPN for You
- Best VPN Services — Full Analysis (Updated 2024)
- ExpressVPN — Best VPN With the Fastest Speeds for Smooth Streaming
- CyberGhost — Dedicated Servers for Reliable Gaming, Streaming, and Torrenting
- Private Internet Access — Customizable App Settings Let You Balance Speed & Security
- NordVPN — Threat Protection for Enhanced Security Against Ads, Trackers, and Malware
- Surfshark — Unique Security Features and Antivirus Add-On to Protect You Online
- Quick Comparison Table: Best VPN Features
- Quick Guide: How to Set Up a VPN in 3 Easy Steps
- Research Methodology: How We Rank & Compare the Best VPNs
- Why You Need a VPN to Keep You Safe Online
- Are There Any Limitations to Using a VPN?
- What’s the Best VPN Service According to Reddit Reviews?
- FAQs About the Best VPN Services
- Get the Best VPN Service
ExpressVPN — The fastest VPN available. It's super secure, easy to use, great for streaming, and affordable. Get 49% off with this special discount.
Finding a great all-around VPN can feel impossible. Some VPNs have reliable servers for streaming but compromise on security, while others prioritize security over speed, making browsing frustrating. Even worse, there are untrustworthy VPNs that track your online movements or fail to encrypt your traffic.
To save you the hassle, our global team of cybersecurity experts has spent several years rigorously testing over 300 VPNs to determine which are the best overall.
Our top VPNs have extensive global server coverage and let you stream local content in Ultra HD or 4K. They also secure your connection without slowing you down and keep your online activity private. Some of them are even powerful enough to work in countries with strict internet censorship.
TLDR: Our top choice is ExpressVPN, thanks to its industry-leading security features and impressive speeds for streaming, torrenting, and gaming. But it also stands out for its strong commitment to keeping your online activity private.
You can try ExpressVPN risk-free thanks to its 30-day money-back guarantee. It offers 24/7 live chat with a responsive customer support team to assist you with any questions or concerns. If you’re not as impressed as we are, you can easily get a full refund. Editors' Note: ExpressVPN and this site are in the same ownership group.
Short on Time? Here Are the Best VPN Services in 2024
- Editor's ChoiceExpressVPN
Best overall VPN with fast speeds, strong security, and top-notch streaming capabilities.70% of our readers choose ExpressVPN - CyberGhost
Servers optimized for smooth streaming, fast torrenting, and lag-free gaming. - Private Internet Access
Tons of settings that you can customize to balance your speed and security. - NordVPN
Built-in Threat Protection feature blocks ads, trackers, and malicious websites. - Surfshark
Rotating IPs, CleanWeb, Camouflage mode, and more to protect your connection.
See 5 More of the Best VPN Services
Editors' Note: Intego, Private Internet Access, CyberGhost and ExpressVPN are owned by Kape Technologies, our parent company.
How to Choose the Best VPN for You
Choosing the right VPN involves more than just data and tests; it's about finding what fits your needs. While some are unquestionably better than others, the best VPN for you depends on your intended use and personal preferences.
Here’s a quick, 3-step guide to finding the top VPN for you.
- Identify your priorities. Security or entertainment? Some VPNs specialize in one over the other, though top ones balance both.
- Define your purpose. Identify your use case (privacy, streaming, gaming, torrenting, or a mix of them all) and how often you'll use the VPN. This focuses on your feature hunt.
- Set your budget. Decide your spending limit and whether you want to pay monthly or for a long-term plan. Top VPNs often run deals, but remember that a higher price doesn't always mean better service.
Keep an eye out for these features while you’re reading VPN reviews. In our experience, these are the most important to consider.
- Privacy and security. Opt for a no-logs VPN with verified privacy policies, 256-bit encryption, IP/DNS leak protection, and secure protocols like OpenVPN and WireGuard.
- Streaming. For optimal streaming, seek VPNs with large server networks in your country and fast speeds to stream in HD lag-free. Also, make sure they work reliably for your streaming accounts, like Netflix, Hulu, BBC iPlayer, or DAZN.
- Torrenting. Choose a VPN for torrenting that masks your IP, encrypts traffic, and offers P2P profiles. You’ll also need fast speeds, and you might want optional features like SOCKS5 proxies.
- Device compatibility. A good VPN should have native apps for multiple platforms and offer router or Smart DNS solutions for devices that don’t support VPNs. All of the VPNs in this list provide easy-to-install apps on their websites for popular devices like Windows, macOS, Android, iOS, Linux, routers, Fire Stick, and browsers.
- Suitable for your location. Consider if the VPN works well in your country, especially if you're in a region with privacy concerns or restrictive networks. Look for features like obfuscation to disguise VPN traffic. On the other hand, you might need a VPN to protect you’re data while you’re browsing, torrenting, or streaming, and not all VPNs work well with streaming or torrenting sites. If you need a VPN for China, India, UAE, UK, or the US, make sure that it works reliably there and works with local sites without a hitch.
Best VPN Services — Full Analysis (Updated 2024)
1. ExpressVPN — Best VPN With the Fastest Speeds for Smooth Streaming

Tested May 2024
| Best Feature | The fastest speeds we tested, ensuring you can stream, browse, game, and torrent without interruptions |
| Server Network | 3,000 servers in 105 countries give you fast worldwide connections |
| Simultaneous Device Connections | Up to 8, so you can protect your compatible devices under one subscription |
| Works With | Netflix, Disney+, Amazon Prime Video, BBC iPlayer, (HBO) Max, Hulu, Vudu, DAZN, and more |
ExpressVPN is the best all-around VPN our global team of VPN experts has tested. It has the fastest speeds on nearby and faraway connections and strong security. My UK-based colleague tests multiple servers consistently using its speed-optimized Lightway protocol. On average, it barely affects connection speeds. Local speeds slowed by only 5%, while some servers thousands of miles away only saw a 7% drop.
 For reference, many VPNs can drop your speeds by up to 80% on long-distance servers
For reference, many VPNs can drop your speeds by up to 80% on long-distance servers
Perfect for Streaming and User-Friendly With a Router App
ExpressVPN’s global server coverage ensures you’ll have reliable nearby connections for streaming your local content while preventing potential slowdowns caused by overcrowded servers.
Note that even though ExpressVPN and other services can hypothetically let you watch content that’s not licensed and available in your country, such action goes against most streaming platforms’ T&Cs. What’s more, it might even constitute copyright infringement, which the team and I don’t condone or support. We urge you to use a VPN responsibly and legally.
My global team and I tested it with 10+ Netflix libraries from their respective and licensed locations — we all had fast and smooth streaming. My US colleagues confirmed that it worked well for Hulu, Disney+, and Amazon Prime Video. When I tested it from the UK, it worked smoothly with Sky Go and BBC iPlayer, too.
It has a Smart DNS feature (MediaStreamer) that allows you to set it up for high-quality streaming on devices that don’t usually support VPNs, like gaming consoles and smart TVs. Keep in mind that Smart DNS doesn’t encrypt your traffic like a normal VPN connection, though.
ExpressVPN has native apps for the most popular devices and operating systems, so installation is easy. I especially liked that the browser extension offers full device protection — most services only offer proxy connections. My only complaint is that the Linux interface could be more user-friendly.
 I like how its app interfaces are almost identical between devices
I like how its app interfaces are almost identical between devices
ExpressVPN offers custom firmware and app for routers, too, simplifying setup without requiring manual installation.
It also supports P2P sharing across its entire network, making it easy to find a fast server. ExpressVPN only offers port forwarding through router setup, but split tunneling can help maximize your speeds while torrenting. I use it to encrypt only my BitTorrent traffic while everything else remains on my local network.
Robust Security and Privacy Protection
ExpressVPN’s security and privacy protection claims are upheld by industry-leading features and third-party audits. Its Lightway protocol, apps, and browser extensions have undergone several security audits to prove they’re watertight, and a 2022 audit by KPMG affirmed compliance with its no-logs policy.
Additional security and privacy features:
- Trustworthy privacy practices. It’s based in the British Virgin Islands and outside of the 14 Eyes Alliance jurisdiction. Plus, RAM-based servers (TrustedServer technology) wipe your data after every reboot.
- Military-grade encryption. It combines AES 256-bit encryption along with SHA512 hashing and a 4096-bit RSA key — making your data basically impossible to read. Plus, perfect forward secrecy ensures that even if your encryption key were discovered, it wouldn't compromise any past or future communications.
- No data leaks. Network Lock (ExpressVPN’s kill switch) prevents your data from being exposed if you suddenly lose the VPN connection. It also provides DNS/IP and WebRTC leak protection.
- Choice of protocols. Aside from Lightway, you also get access to OpenVPN — and IKEv2, but only on macOS.
- Threat Manager. ExpressVPN has a blocklist of sites that are known for tracking and malware, and it prevents your device from communicating with these shady servers. You can also easily customize it to block pop-up ads or adult sites.
- Password manager. ExpressVPN Keys, offered on its Android and iOS apps, lets you store unlimited passwords and can be used via its browser extension on your other devices. It also has a password generator to help you create secure passwords for your accounts.
Works in China and Offers Responsive Customer Care
ExpressVPN is one of the few VPNs that is known to work in China. It’s best to download it before entering the country, though. Only government-approved VPNs are legal there, so unofficial ones are often blocked. There are no public reports of tourists being fined for using one there, but it's important to educate yourself on VPN usage in China to understand the risks. We don’t condone breaking any country’s laws.
Despite China's strict internet censorship, ExpressVPN has been known to perform well within the country, even during past crackdowns on VPNs. It does this by providing obfuscation on every server.
You can try ExpressVPN for yourself risk-free thanks to its 30-day money-back guarantee. Claiming this was straightforward — I just used its 24/7 live chat feature to test its legitimacy. The agent asked a few questions about my experience and then instantly approved the refund. My money was back in my account 2 days later.
ExpressVPN is Best for…
- Overall versatility — ExpressVPN’s fast speeds, strong security, and reliability make it a one-stop shop for a broad range of online activities, including streaming, torrenting, gaming, and safe browsing.
ExpressVPN May Not Be Best for…
- Users on a budget — ExpressVPN is not the cheapest on my list (with plans starting from $6.67/month), but it does offer discounts on its site. I got 49% off when I signed up for a long-term plan.
2. CyberGhost — Dedicated Servers for Reliable Gaming, Streaming, and Torrenting
| Best Feature | Optimized servers for different countries and uses make it one of the easiest VPNs to use |
| Server Network | 11,690 servers in 100 countries, so you have lots of different IP options |
| Simultaneous Device Connections | Connect up to 7 devices at the same time and protect your connections |
| Works With | Netflix, Disney+, Amazon Prime Video, BBC iPlayer, (HBO) Max, Hulu, Vudu, and more |
CyberGhost is one of my favorite streaming VPNs, with specialty servers that are designed to give you fast and reliable connections for enjoying your favorite local content. Each of these is labeled according to the platform it works best with.
I’ve been testing its Netflix UK server in the UK for almost 3 years and have never experienced a sluggish connection. My international colleagues’ tests confirmed that CyberGhost’s streaming servers consistently work with their designated platforms within their respective licensed locations. This includes Disney+, Max, US Netflix, Amazon Prime Video, and much more.
 Simply search for the streaming platform you're looking for in the search bar
Simply search for the streaming platform you're looking for in the search bar
Its optimized servers for gaming and torrenting also provide a great experience. They have low ping and reliable speeds in gaming, as well as strong security and fast downloads for torrenting. While playing Call of Duty: Warzone online with its London gaming server from Glasgow, I encountered minimal lag with a consistent ping of just 32 ms.
Industry-Leading Privacy and Security
CyberGhost proves its dedication to protecting your data by offering a variety of unique privacy and security features. I know I’m always covered — whether I need protection on public WiFi, malware prevention, or extra privacy while working with sensitive data online.
Additional security and privacy features:
- Romanian base and NoSpy servers. Like ExpressVPN, CyberGhost’s headquarters are outside of the 14 Eyes Alliances’ jurisdiction. Here, it also has NoSpy servers, exclusively managed by CyberGhost employees, further minimizing data interception risks.
- Customizable protection. Its Block Content feature helps prevent ads, trackers, and malware. Plus, Smart Rules protects you on public WiFi by letting you customize how and when the app protects your traffic. Smart Rules also allows you to set “exceptions” to apps and sites (like split tunneling).
- Quality protocols. You get a choice of IKEv2, L2TP/ IPSec, OpenVPN, and WireGuard. Unfortunately, OpenVPN is not available for iOS or macOS, though.
- Dedicated IP option. You can get this for a small monthly fee — it’s a "personal" IP address that only you have access to, so you can avoid overcrowding and prevent sites from detecting it as a VPN connection. They’re available in the US, the UK, Canada, Germany, and France.
- Dependable privacy protection. Its no-logs policy was audited by Deloitte, who confirmed that your information is never stored. And like ExpressVPN, CyberGhost switched to diskless servers to ensure your data isn’t stored.
- Security essentials. You get 256-bit encryption plus perfect forward secrecy to keep hackers far away from your personal data. Plus, DNS/IP leak protection and a kill switch.
Easy-to-Use Apps and Speedy Connections
CyberGhost’s apps are sleek and easy to navigate — you can enable most features with just 1 click. It also has free browser extensions, but these are just proxies and aren’t available in every country. While it’s compatible with tons of popular operating systems (such as Windows, macOS, and Linux), Chromebook is not one of them.
 CyberGhost's streaming servers are also available on the iOS app, but it doesn't have torrenting or gaming servers
CyberGhost's streaming servers are also available on the iOS app, but it doesn't have torrenting or gaming servers
It’s fast, especially on its nearby connections. From the UK, I tested 3 nearby servers (in the UK, France, and Germany) and only lost about 16% on average. Its US servers were also fast, dropping no more than 38% from the baseline connection. This isn’t as fast as ExpressVPN, but considering some US servers are more than 9,000km from the UK, I was still impressed.
Affordable Plans and Extra-Long Guarantee
Its plans are affordable, starting at $2.19/month. Since testing a VPN out fully takes time, I opted to get CyberGhost with its 45-day money-back guarantee. This is available with all of the long-term plans (you get 14 days with its short-term plan). You can trust its refund policy — I made sure by testing it myself. Like ExpressVPN, it offers 24/7 live support, which I found to be friendly and knowledgeable.
CyberGhost is Best for…
- Entertainment — Its optimized servers make CyberGhost ideal for streaming, gaming, and torrenting. Plus, it has a Smart DNS feature, so you can stream on more devices.
CyberGhost May Not Be Best for…
- Use in countries with strict censorship — CyberGhost doesn’t work in strictly censored countries like China and the UAE.
3. Private Internet Access — Customizable App Settings Let You Balance Speed & Security
| Best Feature | Tons of adjustable features at a low cost |
| Server Network | 29,650 servers in 91 countries, including in all US states |
| Simultaneous Device Connections | Unlimited, so you can use it on all devices simultaneously with just one subscription |
| Works With | Netflix, Disney+, Amazon Prime Video, BBC iPlayer, (HBO) Max, Hulu, Vudu, and more |
Private Internet Access (or PIA) offers exceptional security and customization for a low price. Plus, you get unlimited device connections, which makes it a really great deal.
Fully Customizable Security Features
You get full control to personalize your connection just how you like. You've got two popular VPN protocols to choose from: OpenVPN and WireGuard. For speedy streaming, I switched to WireGuard, which outperformed OpenVPN by 9% in our speed tests.
When it comes to my bank accounts, security is my top priority, so I use the highly secure OpenVPN protocol. Plus, I like that you can select your preferred level of encryption — either 128-bit or 256-bit. To keep my confidential info super safe, I always bump my encryption level up to 256-bit.
 You’ll find plenty more customization options (including MACE) by clicking the tabs in the left panel
You’ll find plenty more customization options (including MACE) by clicking the tabs in the left panel
Additional security and privacy features:
- Layers of security. PIA has a built-in ad and malware blocker called MACE. You can also enable Multi-Hop to route your connection through a SOCKS5 or Shadowsocks obfuscation proxy along with the VPN server. These features make PIA a good choice for use on restrictive WiFi networks or if you need extra security.
- NextGen servers. To eliminate the risk of third-party interference, PIA offers a selection of self-owned (colocated) servers in 3 global regions: North America, Europe, and Australia.
- Built with the basics. On top of military-grade encryption, you get leak protection and an adjustable kill switch that can protect you from leaks, even when the VPN is manually disabled. During my tests, PIA never leaked my IP or DNS address.
- Proxy browser extension. You can get its proxy extension for free for Chrome, Firefox, and Opera. It doesn’t encrypt your traffic like a VPN but can change your virtual location.
- Court-proven no-logs. Its no-logs policy has been court-proven multiple times; even when user data was demanded, PIA never had anything to show. This is reassuring since PIA is based in the US, which is the heart of the 14 Eyes Alliance.
Tons of Servers and Port Forwarding for Torrenting
With a vast network of 29,650 servers, PIA delivers impressive speeds. When I tested it from Glasgow, I only had a 6% drop when connected to nearby servers in the UK and France, while long-distance servers in the US, Australia, and Japan averaged a 45% speed loss.
PIA supports P2P sharing on all servers. And unlike ExpressVPN and CyberGhost, it provides port forwarding, so you can connect directly to seeders while enhancing your download speeds.
It has streaming-optimized servers in 8 different locations. These have proven much more reliable than its regular servers — I sometimes struggle to get fast or stable streaming with its normal connections. For Netflix UK and BBC iPlayer, I used its UK London Streaming connection since I’m based in the country. My US colleagues also confirmed its US East and West streaming servers work well with Netflix, Hulu, and Max.
Another unique feature that I really appreciate is that PIA has servers in all 50 US states. That ensures you’ll have a connection nearby, no matter which state you’re located in. In most cases, the closer the server, the speedier the connection.
 Many of PIA's advanced features, except split-tunneling are available on the iOS app
Many of PIA's advanced features, except split-tunneling are available on the iOS app
Great Customer Support and Resources
PIA’s apps are easy to install, and there’s also a Smart DNS feature. I particularly like that it offers a native GUI app for Linux. If you need help, you can contact customer support via live chat. Otherwise, there’s a huge knowledge base of FAQs, tutorials, and setup guides.
With plans starting at just $2.19/month, it’s one of the most affordable options on this list. All plans come with a trustworthy 30-day money-back guarantee so you can test PIA for free without risk. PIA offers a helpful 24/7 live chat feature to accelerate the refund process.
PIA is Best for…
- Flexibility — PIA’s adjustable security settings let you choose the security you need for your specific online activities — whether you’re torrenting, banking, or simply browsing.
PIA May Not Be Best for…
- VPN beginners — Its huge range of customization options can be overwhelming if you’re new to VPNs. On the other hand, this is great if you’re a tech nerd like me.
4. NordVPN — Threat Protection for Enhanced Security Against Ads, Trackers, and Malware
| Best Feature | Threat Protection uses a ton of customizable security settings to protect you from malware, ads, and trackers |
| Server Network | 6,348 servers in 111 countries make finding a nearby, fast server easy |
| Simultaneous Device Connections | Protect up to 10 devices at the same time |
| Works With | Netflix, Disney+, Amazon Prime Video, BBC iPlayer, (HBO) Max, Hulu, Vudu, and more |
NordVPN made my list of the best VPNs for its special security features, like Threat Protection and NordLynx, which is its proprietary protocol that’s built for speed and security.
Intuitive Features
Its Threat Protection feature blocks malicious sites, ads, and phishing attempts, even when the VPN isn’t connected to a server. It also scans and removes harmful files from your device. Every time I’ve tested NordVPN’s Threat Protection with ad-heavy websites, this feature eliminated all ads.
NordVPN's Dark Web Monitor notifies you if your VPN-linked email address is compromised on the dark web. The Meshnet feature facilitates encrypted connections to various devices. For example, you can access folders on your home computer from your laptop while traveling.
Additional security and privacy features:
- Specialty security servers. NordVPN’s Double VPN (multi-hop) and Obfuscated servers make it harder for prying eyes to intercept your data, which can also help you overcome certain firewalls. There are also Onion over VPN servers, so you can connect safely to Tor without having to download the Tor browser.
- Assured privacy protection. It’s a little concerning that NordVPN stores your username and last connection date for 15 minutes after each session. However, its no-logs policy has been verified 3 times — most recently by Deloitte (2022), which found NordVPN to be 100% compliant. It also uses RAM-based servers and is based in privacy-friendly Panama.
- Security essentials and more. NordVPN includes a kill switch with 2 settings (for the internet and apps, or both), 256-bit encryption, and DNS/IP leak protection. Plus, it runs its own DNS servers to keep your online activity from being traced back to you.
- Three different protocols. In addition to its proprietary NordLynx protocol, you also get access to OpenVPN and IKEv2/IPsec.
Solid Streaming and Torrenting VPN
NordVPN’s built-in SmartPlay feature makes it reliable for streaming. When my team and I tested it, it consistently worked with the streaming platforms licensed for our respective countries, including Netflix (in 5 countries), BBC iPlayer, Max, and Hulu. It also offers a Smart DNS feature that you can use on streaming devices that don’t support VPN apps.
For an additional monthly fee, you can get a dedicated IP from a choice of 15 server locations. Because this address will be unique to you, it’s less likely to produce slow or unstable connections that could be caused by a shared IP.
There’s a collection of P2P-optimized servers in various countries. And if you connect to a server that doesn’t support torrenting, you’ll automatically be redirected to one that does (in Canada or the Netherlands).
Its speed-optimized NordLynx protocol lets you stream and download smoothly. Nearby servers are fast — from my location in Glasgow, I had an average loss of just 8% on nearby servers. With 3 long-distance servers, the average speed loss came to 25%, which is also impressive.
Easy to Use and Solid Money-Back Guarantee
My team and I tested all of its apps (desktop, mobile, Linux, streaming devices, and more) — it took just a couple of minutes to install each one.
 I also really like that NordVPN's iOS app lets you add a widget to your home screen for a quicker connection
I also really like that NordVPN's iOS app lets you add a widget to your home screen for a quicker connection
All subscriptions come with a 30-day money-back guarantee, which proved trustworthy when I tested it out.
NordVPN is Best for…
- Streaming and torrenting — With its effective ad/malware blocker, fast speeds, SmartPlay, and P2P-optimized servers, it’s fully equipped for these activities. You can also speed up download times using split tunneling or its SOCKS5 proxy connection.
NordVPN May Not Be Best for…
- Great customer support — Although NordVPN offers 24/7 chat support, I don’t like that you have to sign in to your account before you can access it. I also found it frustrating how long I had to spend with the bot before getting transferred to a live agent.
5. Surfshark — Unique Security Features and Antivirus Add-On to Protect You Online
| Best Feature | Tons of advanced and unique security features to play around with |
| Server Network | 3,200 servers in 100 countries for plenty of connection options |
| Simultaneous Device Connections | You can install the VPN on all your compatible devices without having to log out to make space for others |
| Works With | Netflix, Disney+, Amazon Prime Video, BBC iPlayer, (HBO) Max, Hulu, Vudu, and more |
Surfshark offers some of the most advanced security features in the industry and, like PIA, unlimited device connections, although it’s not as cheap.
Advanced Security Features and Antivirus
Surfshark’s NoBorders feature helps you to use it on restrictive networks. When it detects that you’re using a problematic or unstable network, it provides you with a list of the best servers that will still work for you. On top of that, Camouflage mode obfuscates your traffic. Unfortunately, despite all of this, Surfshark doesn’t work in China.
 Enabling NoBorders narrows your server list down to those that can overcome network firewalls or VPN blocks
Enabling NoBorders narrows your server list down to those that can overcome network firewalls or VPN blocks
By signing up for Surfshark One, you can access its Antivirus, Alert, and Search features. Antivirus safeguards your devices against viruses and malware, offers regular scans to detect and remove harmful files, and secures your identity by blocking unauthorized camera access from apps. I really like that you can get all your online protection under 1 account.
Alert notifies you when your email, passwords, or credit card information appears on a leaked database. Also, Search is a private search engine that lets you browse the web without sponsored pages of personalized results based on your search history. Just like the VPN, the Surfshark One features are all really intuitive and easy to use.
Additional security and privacy features:
- CleanWeb. Surfshark’s CleanWeb prevents ads, trackers, malware, phishing attempts — and even those annoying cookie consent pop-ups.
- Rotating IP. This feature changes your IP address every 5–10 minutes without changing your selected location, providing more online privacy.
- Dedicated IP. Surfshark offers dedicated IP addresses for the UK, US, Germany, and the Netherlands.
- Bypasser. This is a split tunneling feature that allows you to select certain websites and apps to communicate with your device while blocking all others.
- Military-grade security. Surfshark lets you choose between WireGuard, OpenVPN, and IKEv2. It also uses 256-bit encryption paired with perfect forward secrecy, a kill switch, and DNS/IP leak protection.
- GPS override (Android only). This automatically matches your phone’s GPS location to the VPN server location you’re connected to. That way, you can block apps that don’t need your location from tracking you.
Fast Speeds and Reliable Streaming
When my team and I tested its streaming abilities, Surfshark consistently worked with just about every platform licensed for our respective countries. It's also a good torrenting VPN with its robust security features and Bypasser feature (split tunneling) to boost speeds. Plus, it supports torrenting on all of its servers.
I use its Fastest location feature whenever I need the best speeds for streaming and gaming. During our testing, we got 237.70 Mbps on a nearby server, which was only 4% less than the starting speed. Long-distance connections are decent — they never dropped more than 35% on average.
 Surfshark also lets you pause your connection for a certain amount of time, in case you forget to reconnect
Surfshark also lets you pause your connection for a certain amount of time, in case you forget to reconnect
Solid Privacy and Refund Policies
Despite Surfshark’s base in the Netherlands — a member of the 9 Eyes Alliance, its RAM-based servers and no-logs policy ensure that your data is kept private. Its compliance with its no-logs policy also passed an independent audit by Deloitte in 2022.
Surfshark lets you try it risk-free for 30 days with its money-back guarantee.
Surfshark is Best for…
- Unique security features — Not many VPNs offer features like GPS override and customizable Multi-Hop connections, just to name a few.
Surfshark May Not Be Best for…
- Short-term users — Surfshark’s 1-month plan is quite expensive compared to its competitors, so it’s not ideal in terms of affordability if you need a VPN for a shorter period.
6. IPVanish — Completely Self-Owned Network for Ultimate Privacy
| Best Feature | IPVanish doesn’t rent servers from third parties but owns its entire network |
| Server Network | 2,400 servers in 90 countries with 40,000+ unique IP addresses |
| Simultaneous Device Connections | Unlimited to use on all your compatible devices simultaneously |
| Works With | Netflix, Disney+, BBC iPlayer, (HBO) Max, Vudu, and more |
IPVanish is a great VPN offering all the security essentials, but what makes it stand out is its commitment to privacy. Many VPNs rent their servers from third parties, but IPVanish owns each and every one of its servers, removing any risk of third-party meddling.
On the other hand, IPVanish is based in the US — but its strict no-logs policy has been audited by Leviathan Security Group to confirm it won’t record or store your data.
Intuitive with a Native App for Fire Stick
It’s simple with few customizable settings, but that’s what makes IPVanish so user-friendly. Each server is displayed with its ping rate and load percentage. I personally appreciate this feature for finding a low-latency server for gaming on my PC.
 Servers with lower ping and user load are best for maintaining fast speeds
Servers with lower ping and user load are best for maintaining fast speeds
One unique feature is that IPVanish has a native app for Gen2 Fire TV Stick and newer. It was incredibly easy to set up, too. All you have to do to set it up is download the app directly from the Amazon Appstore to your Fire device, and you’re ready to go.
Our speed tests showed mixed results with IPVanish. Long-distance servers in the US, India, and Japan dropped speeds between 5% to 80%, while nearby servers in Europe averaged a speed loss of around just 11%.
Additional security features:
- Security essentials. With IPVanish, you get the basics like 256-bit encryption, a kill switch, and IP/DNS leak protection. Plus, it has some bonus features, including split tunneling and an ad/malware blocker (Threat Protection).
- Scramble. If you’re on a restrictive network that blocks VPNs, you can use this feature to obfuscate your traffic and hide the fact that you’re using a VPN.
- Four protocols. WireGuard, IKEv2, OpenVPN, and IPSec are all supported by IPVanish.
24/7 Customer Support and Solid Guarantee
IPVanish is one of the very few VPNs that offers support over the phone. I really appreciate this when you need real-time help setting up the VPN on certain devices. For example, setting up IPVanish on a router can get complicated, so it’s useful to have direct support to talk you through it.
 You can also use IPVanish's map to connect to the server you want
You can also use IPVanish's map to connect to the server you want
It offers a 30-day money-back guarantee, so you can sign up for IPVanish with peace of mind.
IPVanish is Best for…
- Torrenting — All of IPVanish’s self-owned servers support torrenting. It also has a SOCKS5 proxy connection to speed up download times.
IPVanish May Not Be Best for…
- Streaming — Our tester in the US found IPVanish’s servers were reliable for most regional sites, like Netflix US and Max. However, some of its servers weren’t so dependable for watching Hulu or Prime Video. Plus, some servers located in faraway states produced major slowdowns, which isn’t great for streaming.
7. PrivateVPN — Solid VPN With a Small but Reliable Network
| Best Feature | Dependable for streaming and security, ideal for first-time VPN users |
| Server Network | 200 servers in 63 countries that offer reliable connections |
| Simultaneous Device Connections | Protect up to 10 devices at the same time |
| Works With | Netflix, Disney+, Amazon Prime Video, BBC iPlayer, (HBO) Max, Hulu, Vudu, and more |
PrivateVPN has a relatively small network. However, it turns this into a virtue by ensuring you can depend on its servers for reliable streaming and other online activities.
My team and I tested PrivateVPN’s servers in the US, the UK, Italy, and Australia to see how it performs with popular streaming platforms available in our locations. It gave us lag-free, smooth streaming on our regional sites, including Netflix, Sling TV, BBC iPlayer, and more.
 Its London server gave me a speedy connection, despite being quite far from my location in Glasgow
Its London server gave me a speedy connection, despite being quite far from my location in Glasgow
In our speed tests, PrivateVPN proved quick on nearby servers, with a reasonable speed drop on distant ones (55% on average). No matter which server I used, it was still fast enough for seamless browsing and HD streaming.
Strict No-Logs VPN That Works in China
PrivateVPN is based in Sweden — although it’s headquartered within the 14-Eyes jurisdiction, it follows a strict no-logs policy.
To further protect your privacy, it also has a Stealth VPN mode designed to work on restrictive networks that block VPNs and use DPI to probe your connection. PrivateVPN’s Stealth VPN has been known to work in China, too.
Additional Security Features
- Advanced View settings. PrivateVPN offers a kill switch and IPv6 and DNS leak protection, which can all be enabled in Advanced View.
- Five protocols. It uses AES 256-bit encryption and a choice of AnyConnect, IKEv2, IPSec, OpenVPN, and WireGuard protocols.
- Port forwarding and SOCKS5. These two settings are particularly useful for optimizing torrenting speeds.
Simple Apps and a Money-Back Guarantee
It has user-friendly apps for most devices and operating systems. It offers a handy proxy extension for Chrome but not for any other browsers at the moment. Luckily, the full VPN app will protect your data, no matter which browser you use. There’s also no Smart DNS feature, but you can set up PrivateVPN on a router to use it with devices like smart TVs, gaming consoles, and some streaming devices.
 Just click the large on/off button to connect to your most recent server location
Just click the large on/off button to connect to your most recent server location
Its 30-day money-back guarantee gives you plenty of time to make sure it’s the right choice for you. PrivateVPN also offers 24/7 live chat to help answer any questions you have in a timely manner.
PrivateVPN is Best for…
- VPN beginners — It offers a Simple View that hides all PrivateVPN’s more complicated security features and lets you connect to a server with 1 click.
PrivateVPN May Not Be Best for…
- Access to a large network — While its connections are reliable and have decent speeds, its small network might not cover every location you need access to.
8. Proton VPN — No Frills VPN That's User-Friendly and Ideal for Beginners
| Best Feature | Easy to use but high-performing VPN suitable for users of all experience levels |
| Server Network | 4,898 servers in 91 countries, including safe Secure Core options |
| Simultaneous Device Connections | You can use it on up to 10 devices simultaneously, which is generous |
| Works With | Netflix, Disney+, Amazon Prime Video, BBC iPlayer, (HBO) Max, Hulu, Vudu, and more |
Proton VPN is a beginner-friendly VPN provider. It has intuitive apps, so you don’t need to spend time getting used to them.
Its speeds are pretty impressive and allow for a smooth streaming experience. During our tests, we consistently experienced fast speeds with ProtonVPN’s VPN Accelerator feature enabled. The most our UK-based tester ever lost was 36% from a server all the way in Australia.
Special Secure Core Servers and Based in Switzerland
It’s based in privacy-friendly Switzerland and follows a no-logs policy. Also, it has its own unique Secure Core servers located in countries with favorable privacy laws (Iceland, Switzerland, and Sweden). You can route your traffic through a Secure Core server first and then another VPN server before it reaches its destination.
 The only downside is that routing through 2 servers slows your connection significantly
The only downside is that routing through 2 servers slows your connection significantly
Additional Security Features
- Reputable protocols. Proton VPN supports OpenVPN, IKEv2, WireGuard, and Stealth, but not every app offers all of these protocols.
- Perfect Forward Secrecy. This is paired with military-grade encryption to prevent cybercriminals from accessing your data.
- NetShield. Blocks ads, malware, and trackers before they ever reach your device.
Useful Features and a Limited Free Plan
Proton VPN allows you to personalize your connections. For example, you can choose one of its many P2P-optimized servers, the protocol you want, and label a “torrenting” connection for whenever you want to download files.
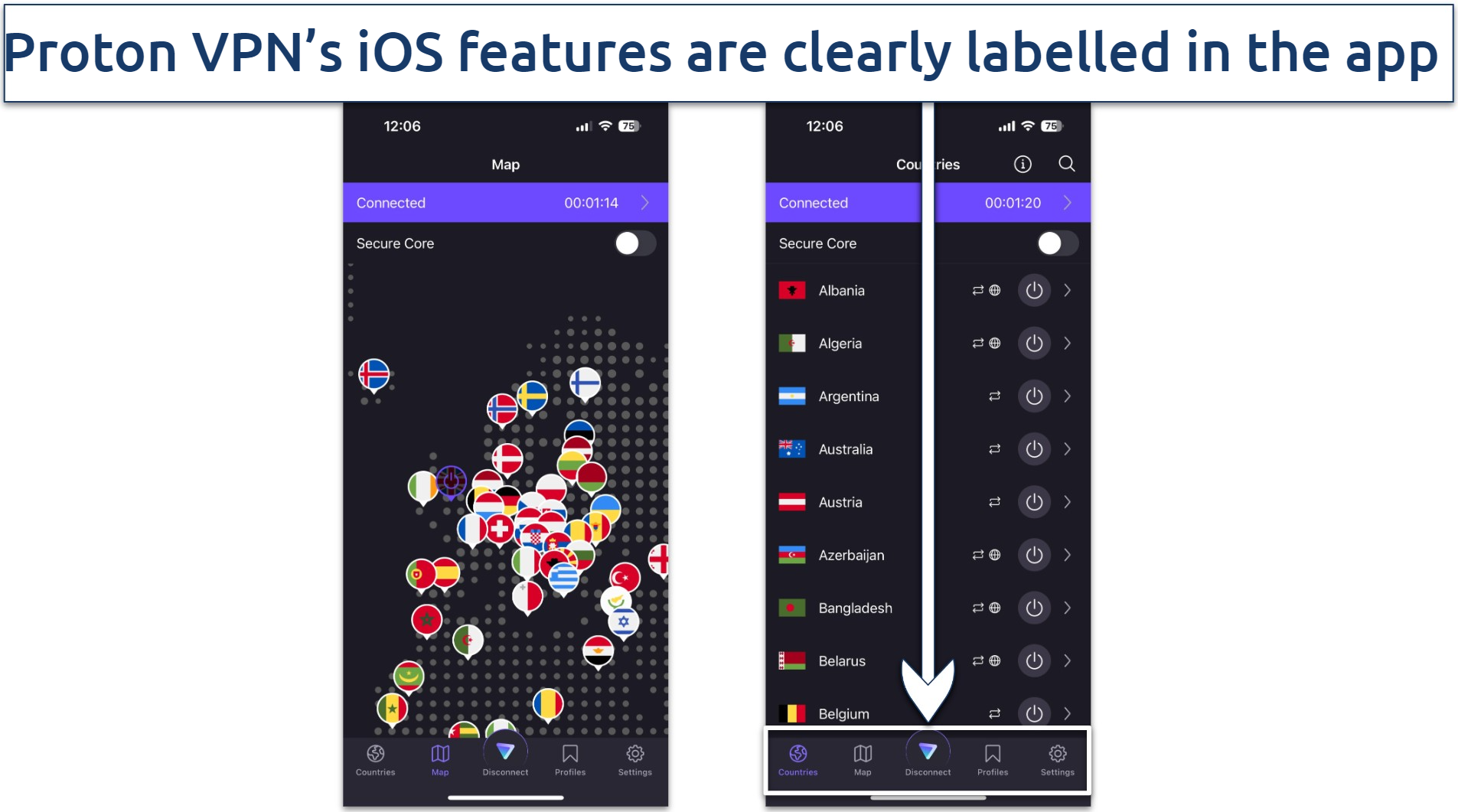 The iOS app also shows a country map to easily find the location you're looking for
The iOS app also shows a country map to easily find the location you're looking for
Almost all of Proton VPN’s servers are torrent-friendly, too. P2P servers are marked by a small icon next to the server name, but, unfortunately, it’s easy for your eyes to scan past these as the UI is a little crowded.
You can give Proton VPN a try using its free version — it has unlimited data and no ads. But the free plan doesn’t support torrenting and is not fast or reliable enough for streaming. It also doesn’t come with 24/7 live chat, like the paid plans.
It’s router-compatible, but like PrivateVPN, it doesn’t offer a Smart DNS feature. You can bundle Proton VPN with its encrypted email, calendar, and/or cloud services for an extra fee. It’s also possible to try risk-free, thanks to its 30-day money-back guarantee.
Proton VPN is Best for…
- Smooth, ad-free browsing — It offers full-VPN browser extensions (Firefox and Chrome) and its NetShield feature, which make Proton VPN great for secure and ad-free browsing.
Proton VPN May Not Be Best for…
- Affordability — Proton VPN is one of the priciest VPNs on this list, even with its long-term plans, which start at $4.49/month.
9. Hotspot Shield — Strong Security That Doesn’t Slow You Down
| Best Feature | Hydra protocol delivers consistently fast speeds for seamless use |
| Server Network | Safe and reliable network of 1,800 servers in 80 countries, |
| Simultaneous Device Connections | You can protect only 10 devices simultaneously |
| Works With | Netflix, Disney+, BBC iPlayer, (HBO) Max, Hulu, Vudu, and more |
Hotspot Shield’s proprietary protocol, called Hydra, prevents the major slowdowns that are caused by encryption.
Our speed tester in the UK reported an 11% drop on average on local servers with the Hydra protocol. Even distant servers in Japan, Australia, and the US maintained an average speed of 161.55 Mbps (just 37% slower than the baseline connection). Its fast servers are ideal for activities like HD/UHD streaming and quick torrenting.
 While there was a bigger drop on long-distance servers, it didn't make a difference to my browsing experience
While there was a bigger drop on long-distance servers, it didn't make a difference to my browsing experience
When my colleague tested it from the US, Hotspot Shield was smooth and reliable with most streaming apps, like Netflix and Disney+, but not Amazon Prime Video. It doesn’t offer Smart DNS, although setup on routers allows use on smart TVs or consoles. I quickly installed it on my ASUS router to stream on Apple TV.
Security Essentials
On top of its Hydra protocol, you get the choice of 4 VPN protocols, all of which provide 256-bit encryption: OpenVPN, SSTP, IPSec, and L2TP. One downside is that it doesn’t offer advanced features that let it work on heavily restrictive networks that block VPNs or other websites. But you can depend on it to protect your data while you browse, stream, and torrent.
Additional Security Features
- Leak prevention. DNS/IP leak protection and a kill switch to help keep your information hidden under any circumstances.
- Built-in malware and phishing protection. This feature is automatically enabled to protect you and your devices.
Limited Free Plan and an Extended Refund Period
Hotspot Shield’s paid plans are on the pricier side. There’s also a free version, but it’s quite limited. For example, it only gives you access to 5 server locations across Singapore, the UK, and the US. If you want to try Hotspot Shield risk-free, it comes with a generous 45-day money-back guarantee.
Hotspot Shield is Best for…
- Streaming and torrenting — Its speed-optimized Hydra protocol, reliable HD streaming abilities, and P2P support all make this VPN a good choice for these activities.
Hotspot Shield May Not Be Best for…
- Super privacy-conscious users — it’s based in the US and has a vague privacy policy, but after a bit of digging, I learned that while it temporarily records your IP address to prevent fraud, it’s immediately encrypted and then deleted after your VPN session ends.
10. hide.me — Unique Stealth Guard Feature Protects You on Specified Apps
| Best Feature | Stealth Guard feature lets you customize your VPN connection |
| Server Network | 2,400 servers in 89 countries, including servers optimized for streaming |
| Simultaneous Device Connections | Use it on 10 devices at the same time |
| Works With | Netflix, Disney+, Amazon Prime Video, BBC iPlayer, (HBO) Max, Hulu, Vudu, and more |
hide.me’s Stealth Guard feature allows you to specify which apps should only run over a VPN connection. If the VPN disconnects, the apps automatically stop, preventing data leakage over an unsecured connection. It's essentially a kill switch combined with split tunneling.
You can also customize how hide.me reacts to secure, unsecure, and ethernet connections. When it detects one of these networks, you can set it to ask you if you want to connect, enable the VPN, disable the VPN, or ignore the network.
 I appreciate the provided explanations to help you better understand each app feature
I appreciate the provided explanations to help you better understand each app feature
Additional security features:
- Data leak protection. hide.me incorporates DNS/IP leak protection and a kill switch, preserving your online privacy under all circumstances.
- Zero logs. Your online activity is never stored, recorded, or shared. hide.me is also based in Malaysia, where there are no data-retention laws.
- Encryption and strong protocols. hide.me supports SoftEther, WireGuard, OpenVPN, IKEv2, and SSTP and uses 256-bit encryption.
Streaming and Torrenting-Friendly
hide.me’s Bolt feature bypasses network congestion and reduces latency for a faster, smoother, and more reliable connection. P2P is supported across all servers, ensuring speedy and uncrowded torrenting.
It works reliably and provides decent speeds for high-quality streaming. Plus, it is adaptable for smart TVs and consoles through router setup. I managed to stream my regional Netflix library in HD on my Apple TV after setting it up on my router.
Free Version and a Money-Back Guarantee
You can try out a free version of hide.me, which offers 8 server locations and unlimited data. With a restricted network, capped speeds, and unreliable streaming, its capabilities are pretty limited, though. As a better alternative, you can test its unlimited premium version risk-free with its 30-day money-back guarantee.
hide.me is Best for…
- Reliable streaming and safe torrenting — When the team and I tested it, hide.me worked with every platform licensed for our respective countries that we tried it with. It had fast speeds for lag-free streaming and quick downloads. Plus, its strong security features protect your data while torrenting.
hide.me May Not Be Best for…
- Fast long-distance connections — Overall, hide.me is pretty fast with nearby connections. However, our UK-based speed tester recorded an average speed loss of 78% with its servers in Australia and Japan, which is pretty significant.
Editors' Note: Intego, Private Internet Access, CyberGhost and ExpressVPN are owned by Kape Technologies, our parent company.
Quick Comparison Table: Best VPN Features
VPNs can vary a great deal as far as the features they provide. This can make some VPNs better suited for certain activities than others.
A large server network is beneficial for easily finding a speedy nearby server while preventing user overload. At the same time, fast speeds are important for keeping your online activities running smoothly — slow VPNs can cause buffering or lag.
If you’re a big Netflix fan, look for a VPN that works reliably with your country’s library. If privacy is of bigger concern, choose a VPN with an independently-audited no-log policy. For those looking to use a VPN in censored countries, make sure the VPN has been tested to ensure it works in heavily restricted regions like China.
Use the table below to compare some key features of the best VPNs.
Quick Guide: How to Set Up a VPN in 3 Easy Steps
- Download a VPN. I recommend ExpressVPN since it’s fast, secure, and reliable no matter what you need a VPN for.
- Connect to a server. Visit the VPN’s official website and install the appropriate VPN app for your device.
- Start browsing. Pick a server — those closest to you should be the fastest.
Editors' Note: ExpressVPN and this site are in the same ownership group.
Research Methodology: How We Rank & Compare the Best VPNs
With hundreds of VPNs all claiming to be the best, how do you choose the right one? It’s not realistic to research every VPN out there… unless you have a global team of experts ready to put them to the test. That’s exactly what we did to create the ranking above — and all our other reviews and lists.
We analyze each VPN based on a variety of factors, with a special focus on a few key aspects. These factors include, from most to least important:
- Privacy and logging Policy — we thoroughly read through each VPN’s privacy policies and keep an eagle eye on any changes that may occur over time. We analyze the logging policies to ensure the VPN doesn’t store any identifiable information, and our top 5 VPNs’ logging policies have all been independently audited by third parties.
- Speeds — our team tests each VPN’s speeds weekly to see how they perform at short and long distances and to ensure these speeds are consistent and accurate.
- Security features — we ensure each VPN offers the essentials, like 256-bit encryption, leak protection, and a kill switch. All of the VPNs undergo leak testing, which we consistently perform on multiple servers across the globe.
- Streaming — my international team and I tested each VPN with the popular streaming sites in each of our locations (where each platform is licensed). We ensured that you can secure your connections with the VPN without it compromising the speeds and reliability of your streaming.
- Compatible with a range of devices — as well as making sure that the VPN you choose is compatible with the devices you want to use it on, make sure the device’s app isn’t lacking any features. For example, some VPNs don’t offer a kill switch or split tunneling on all devices.
- Ease of use — we check that each VPN is user-friendly enough for all levels, with apps for easy installation, simple server connection, and feature descriptions (in the site or within the app).
- Customer support — our team tests each VPN’s customer service to ensure you’ll get informed answers to your questions, one way or another. We ask questions via live chat to see the response times and check that their site provides a database of information you can refer to.
- Torrenting — we’ve tested each VPN with torrenting to see how fast they are, whether their ad blockers are effective (if offered), and if they flag potential malware before it can infect your device. Plus, regular leak testing reveals whether your IP address would be visible during torrenting.
- Value for money and money-back guarantee — we ensured that our top VPNs are feature-rich and perform to a high standard so you can be confident that you’re getting the most for your money. We also made sure the VPNs we choose offer trustworthy money-back guarantees so that you can get a refund if the VPN isn’t right for you.
Why You Need a VPN to Keep You Safe Online
A VPN lets you tap into a global network of private servers. When you establish a connection with a VPN server in any country, it encrypts your online traffic and reroutes it via this location. You’ll also use that server’s IP address, so your original IP isn’t visible.
This enhances your online privacy and secures your connection against threats such as snooping, hacking, and other cyberattacks.
VPNs offer tons of benefits and applications, which vary depending on the specific features they offer. Generally, here are some of the most common ways you can use a VPN:
- Safeguard your data against cybercrime. The best VPNs encrypt your traffic with a 256-bit AES algorithm — the same encryption governments, banks, and militaries use. They also use trusted VPN protocols to scramble traffic, helping to keep your browsing private, whether you're connected to your home network or an unsecured, public WiFi hotspot.
- Keep your IP address private. A VPN connection hides your IP address, which stops anyone from tracing your activity back to you. This shields you from hackers and helps circumvent ISP throttling (where your speeds are slowed because you use a lot of data, like if you torrent). For absolute privacy, you can use a VPN with the secure Tor browser.
- Securely torrent files. P2P sharing poses risks due to illegal or unethical practices, and it can leave you vulnerable to hackers or malware. Using a VPN while torrenting can protect you from the latter kind of risks, helping to protect your devices and personal data. The team at vpnMentor does not endorse illegal torrenting. Always ensure your downloads are copyright-free!
- Safely play online games. VPNs provide protection against DDoS attacks that some competitive gamers use to disrupt your home network. The best VPNs have low-latency servers that are optimal for games like Call of Duty: Warzone and Valorant.
Are There Any Limitations to Using a VPN?
Of course. VPNs are your online superheroes, boosting security, privacy, and digital freedom, but remember, every superhero has its kryptonite. Even the best VPNs on the market won’t tackle the following:
- Full-blown virus and malware defense. Trustworthy antivirus software remains your best bet, even with VPNs having malware-blocking tools.
- Internet speed enhancement. A VPN won't turbocharge your net speed unless your ISP is stealthily throttling your connection. And since VPNs encrypt your data and route it through a server, they will almost always slow down your speeds.
- Complete anonymity. VPNs give your privacy a boost but don't make you entirely untraceable. Browser fingerprinting, tracking scripts, and traffic analysis can still keep tabs on your online activity. Also, if the VPN stores logs and happens to be in the 14-Eyes jurisdiction, you run the risk of your data being handed to government agencies.
- VPN blocks. Some websites and services can detect and block traffic from VPNs to stop people from accessing it from unlicensed regions. This means you might not always be able to watch certain content, even if you’re accessing it from your own country while connected to a VPN for privacy.
- Legal license for illicit activities. Remember, VPNs don't green-light illegal activities, such as torrenting copyrighted stuff or visiting sites prohibited in your location. Your actions online should always respect the law.
What’s the Best VPN Service According to Reddit Reviews?
As with most topics on Reddit, reviews on the top VPNs are mixed. However, during my research, I found that ExpressVPN emerges as the best VPN among Redditors for its reliable streaming and torrenting, along with providing consistently fast speeds. Moreover, its security features, including an independently audited no-logs policy, make it a safe option.
Other popular VPNs, like NordVPN, CyberGhost, Surfshark, and PIA, are also often recommended by Redditors, but ExpressVPN’s consistent performance makes it stand out.
Redditors consistently highlight ExpressVPN's ability to maintain high speeds without significantly affecting the internet connection — a huge advantage for users who engage in high-bandwidth activities. It also has a large global server network, so you can almost always find a local server to connect to, no matter where you are.
While its pricing is on the higher side, the value it provides, especially with its frequent discounts and money-back guarantee, tends to justify the cost for most users.
FAQs About the Best VPN Services
Which VPN has the fastest speeds?
Our number 1 rated VPN consistently comes out on top in our speed tests. But it’s important to note that the fastest VPN for us might not be for you. A VPN’s speed results will vary depending on your location to its nearest server, how crowded the server is, your base connection, and tons of other factors.
That being said, over the years we’ve been working with our top VPN provider, it has consistently given us the fastest upload/download speeds and the lowest lag and ping rates. This means that you can use it to stream in high quality without buffering, download torrents quickly, and game online without slow connections tripping you up.
What is the best VPN for Android and iOS?
Each of the VPNs on this list offers feature-rich and high-performing mobile apps. They all offer reliable performance, user-friendly interfaces, and robust security features. These top VPNs offer dedicated apps designed specifically for mobile, ensuring seamless ease of use.
When selecting a VPN for mobile devices, prioritize providers with strong encryption standards, automatic kill switches, and a strict no-logs policy to safeguard your data. Additionally, look for services offering a wide range of server locations to minimize latency.
However, individual preferences and needs may vary, so consider factors like additional features such as ad-blocking or split tunneling to find the best fit for your needs.
Are VPNs legal?
In the vast majority of countries, it’s completely legal to use a VPN. VPNs themselves are legitimate tools that promote privacy, security, and internet freedom. Their primary functions (encrypting data and ensuring privacy) are 100% acceptable under most legal systems.
There are a few places where VPNs are forbidden or occupy a legal gray area, like China, Iraq, Iran, Russia, Belarus, Turkey, Oman, and the UAE. If you’re located in a country with internet censorship, you should check to see what the local laws are regarding VPNs.
Sometimes people use VPNs for illegal purposes, which we don’t condone under any circumstances. For instance, you could theoretically use a VPN to obtain an IP address in a region outside of your location and hypothetically access content that’s not normally available to you. Keep in mind that this goes against most streaming platforms’ T&Cs and can constitute copyright infringement. Remember: anything that would be against the law without a VPN is still against the law with a VPN and should always be avoided.
Are VPNs safe?
Reputable, trustworthy VPNs are completely safe to use. In fact, they’re designed to make your online experience even safer by shielding you from potential threats like hacking or surveillance. Do keep in mind that some VPNs have shady privacy practices, weak security, or outdated software, which can all leave you vulnerable. So, it’s best to do your research before downloading and even using a virus detection tool, especially if you’re looking at free VPNs.
It’s also your responsibility to make sure that what you’re doing online doesn’t violate any laws or local regulations. You may be putting yourself at risk if:
- You’re located in a country where the government only allows certain VPNs, and you use one that’s not officially approved.
- You download or watch copyrighted content with a VPN (or without a VPN, for that matter).
Which VPN is best for torrenting?
The best VPNs for torrenting typically offer fast and reliable connections, robust security, and a strict no-logs policy. Look for providers with specialized servers optimized for P2P file sharing to ensure smooth torrenting experiences. Additionally, strong encryption and DNS leak protection are crucial for maintaining privacy while torrenting. It's advisable to avoid VPNs with bandwidth caps or those known to throttle P2P traffic.
What is the best VPN for Netflix?
All of the VPNs that made this list are excellent choices for Netflix. Although, they vary in terms of how many Netflix libraries they work with and streaming speeds. You need a VPN that works well with your country’s Netflix catalog and doesn’t reduce your streaming quality.
Keep in mind that even though a VPN can hypothetically let you access Netflix libraries from abroad, such action goes against the platform’s T&Cs and could even amount to copyright infringement. The team and I strongly advise you to use a VPN responsibly.
Depending on how fast your baseline connection is, you may need a really fast VPN so you don’t experience buffering. You may also want to consider whether the VPN has a Smart DNS feature or router compatibility so you can stream Netflix on more devices (like game consoles and smart TVs.)
Can a VPN track you online?
Technically, it’s possible for a VPN to track you — but the best ones won’t. When you use a VPN, you’re protecting your data and personal information from third parties like your ISP, hackers, advertisers, and the government, but the VPN itself still has access to everything. This is why VPNs have no-logs policies that promise they’ll never record or store your data.
Some VPNs also use technology like RAM-based servers to minimize the chance of your data ever falling into the wrong hands. These servers are wiped every time they reboot, so all your information is automatically erased.
Which VPN is best for China, India, and the UAE?
The best VPNs for China, India, and the UAE are those with advanced obfuscation techniques and servers in nearby countries. These VPNs are better equipped to work well in countries with strict censorship measures.
Additionally, choose a VPN with strong encryption and a history of successfully working reliably in countries with strict censorship and on restricted networks.
However, make sure you stay informed about the legal and regulatory environment surrounding VPN usage in these countries. You should also be aware that accessing banned content or circumventing government censorship may carry legal consequences in some jurisdictions. The team at vpnMentor and I don’t condone using a VPN for illegal purposes.
What are the best VPNs to use at school?
All of the VPNs in this list are well-equipped for use at school. They all offer reliable security features you can use at school (or on similar networks such as in a workplace or public WiFi network). In addition, the VPNs in this list are fast enough for any school-related activity — whether you download a podcast for research or do a quiz. VPNs that offer advanced features, such as obfuscation, are best for overcoming VPN-blocking firewalls (like those that are sometimes used on public school networks).
Are VPNs worth the cost?
The VPNs in this list are all worth the cost for those willing to keep themselves safe online. While the prices vary, they’re all affordable options, and we’ve ensured they all perform well. Some of them even cost just a bit more than $2 per month. So, you’ll be paying less than the price of a takeout coffee each month to secure your online data, stay safe online, and protect your digital freedom.
In general, long-term subscriptions tend to be cheaper overall than short-term plans; the longer your commitment, the lower your monthly price.
The best VPNs also offer money-back guarantees, which means that if you change your mind after subscribing, you can ask for a refund within a certain period (usually 30 days). This doesn’t change the price, but it does give you some added peace of mind in case you’re unsure about the expense.
If you’re ready to make a purchase, head to our coupons page for exclusive discounts on top VPNs.
Are there free VPNs?
There are free VPNs available, but our tests show that premium VPNs always outperform them.
That’s because free VPNs rarely have the resources to invest as heavily in security, performance, and reliability as their premium competitor or counterparts. They work well for basic browsing but not much more. They’re not super reliable with streaming platforms, and their congested servers meant our torrents suffered from significant download speed slowdowns.
That’s not to say that there aren’t any good free VPNs out there. There are, and these are usually so-called “freemium” VPNs. This just means that they’re free versions of premium software, so they might contain ads. However, the best freemium VPNs are funded by the company’s income from premium users, so you’ll just have to deal with data and bandwidth caps. They’re not equivalent to a paid service, but they’re a decent alternative.
Bear in mind the old adage: “If you’re not paying for a product, you are the product.” Every free VPN we’ve recommended here is reliable and safe to use, but not all are. We came across tons of free VPNs that pay their bills by selling your data to advertisers. And, we even found some that are barely-disguised scams or malware delivery systems.
Get the Best VPN Service
Finding the perfect VPN can be time-consuming and overwhelming. Some excel in streaming yet fall short in security; others prioritize privacy but compromise on speed. To save you the effort, our team rigorously tested over 300 VPN services to identify the best.
Our top pick is ExpressVPN — it stands out for its robust security, impressive speeds, and commitment to privacy. Better yet, you can test ExpressVPN out completely risk-free since it offers a trustworthy money-back guarantee. If you find it’s not the VPN for you, claiming your refund is a piece of cake.